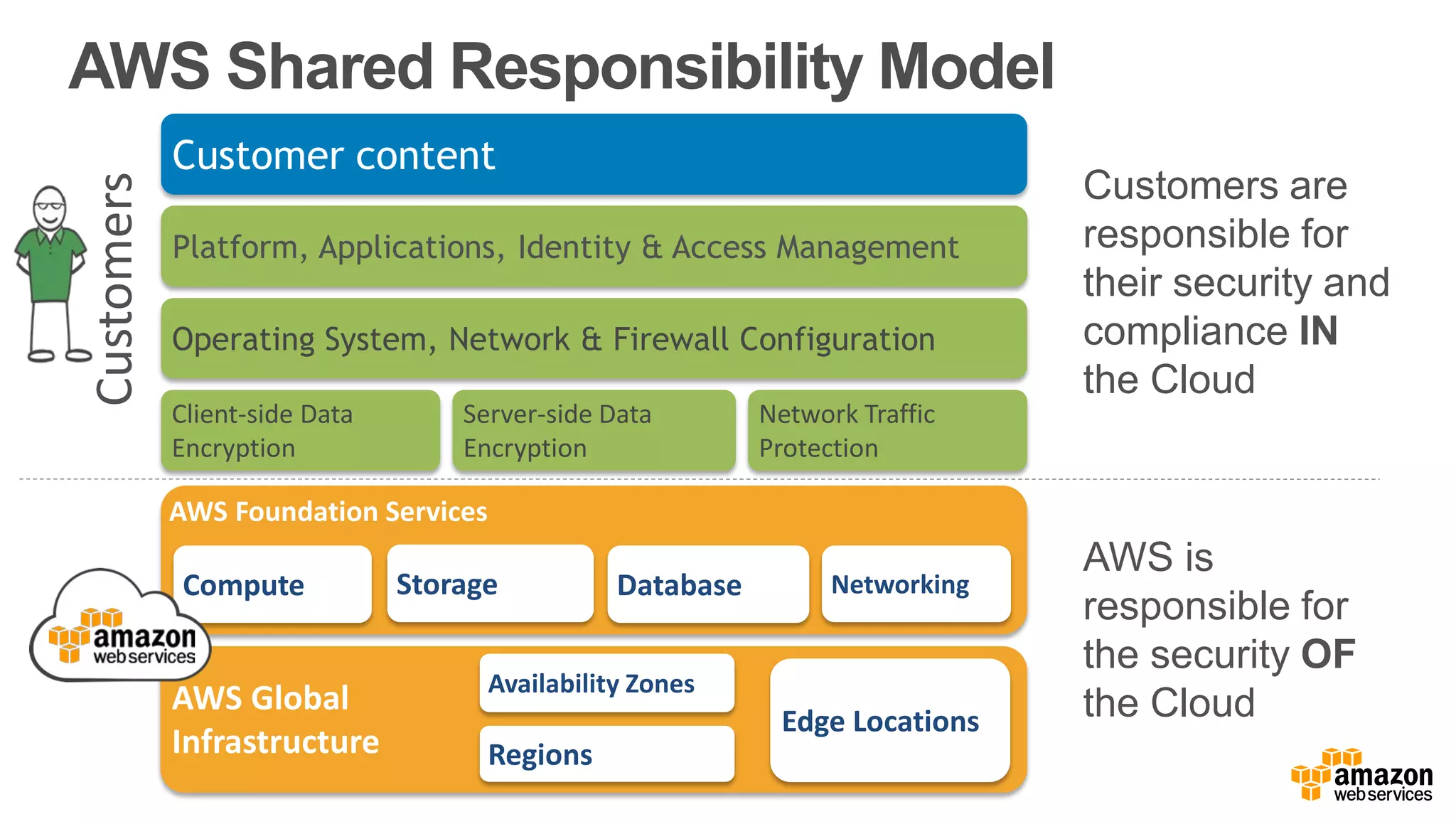
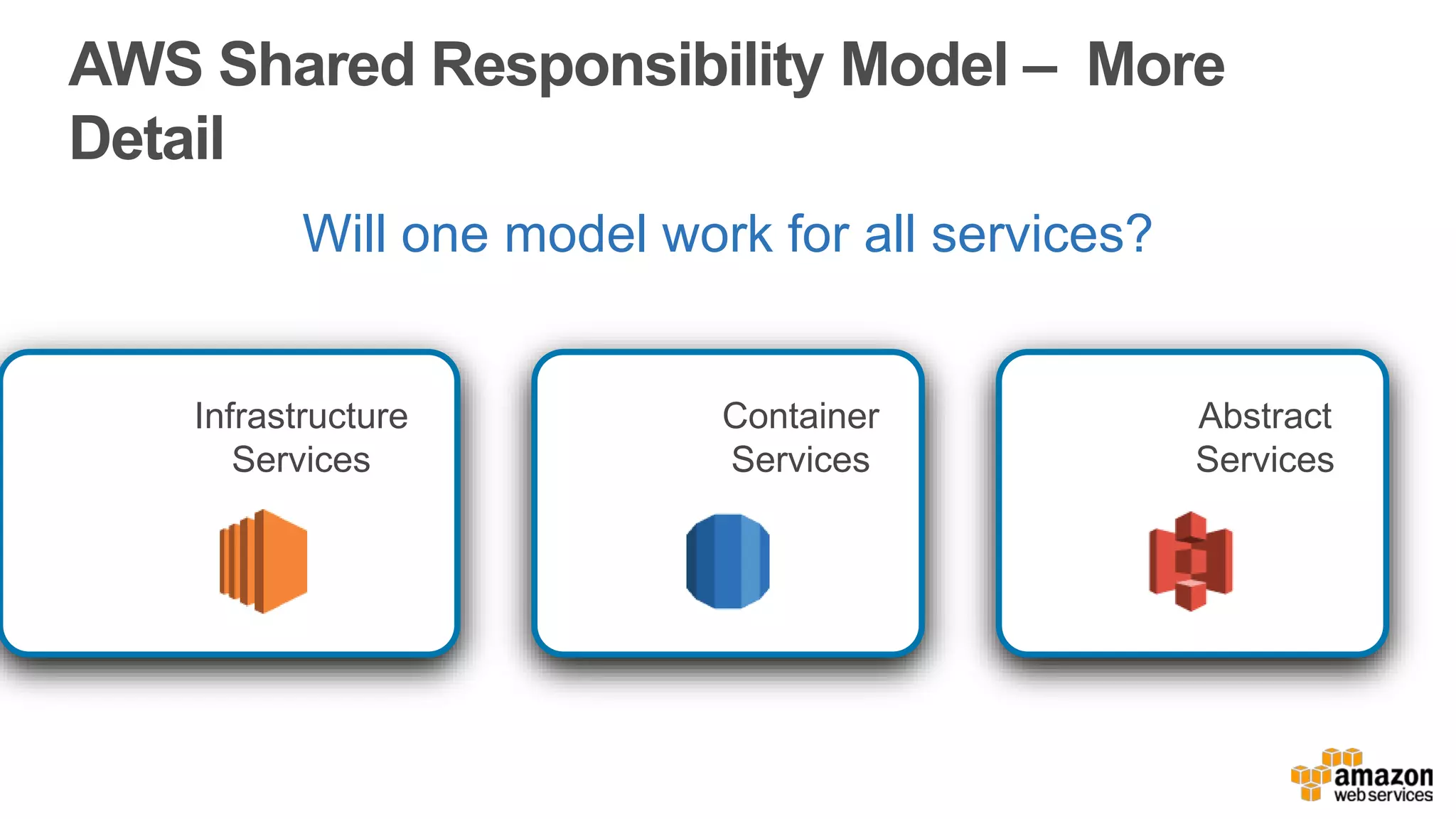
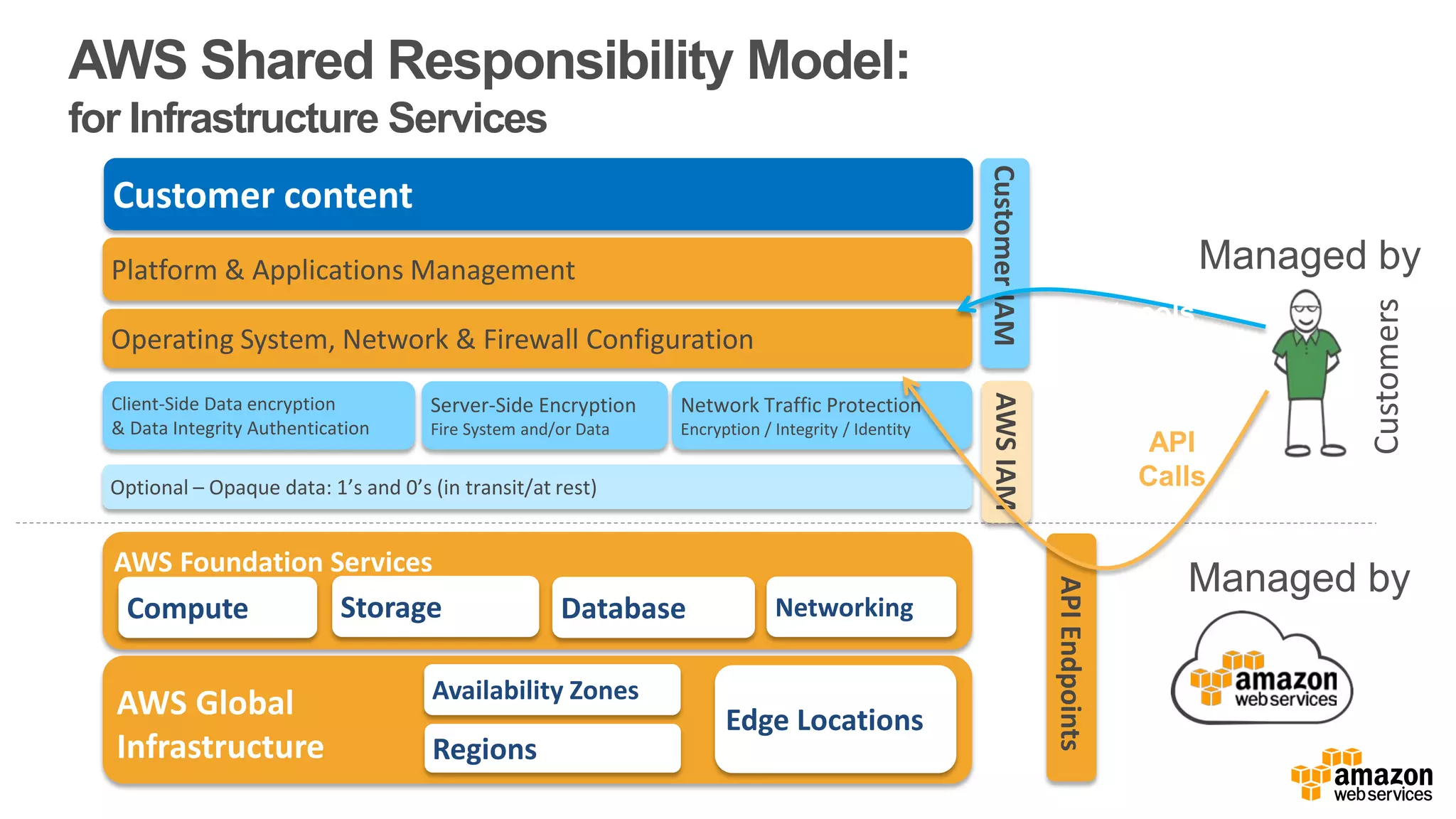
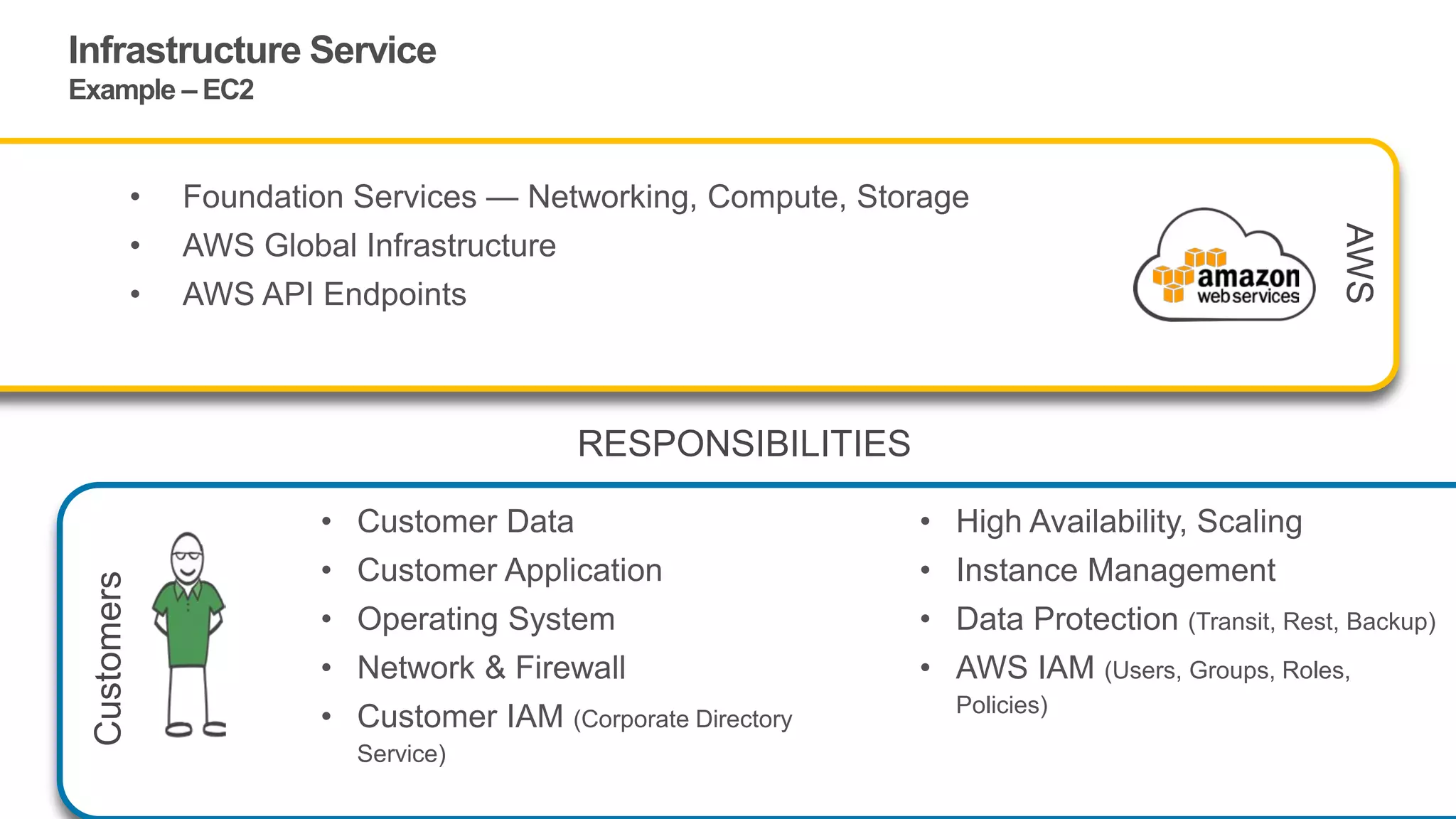
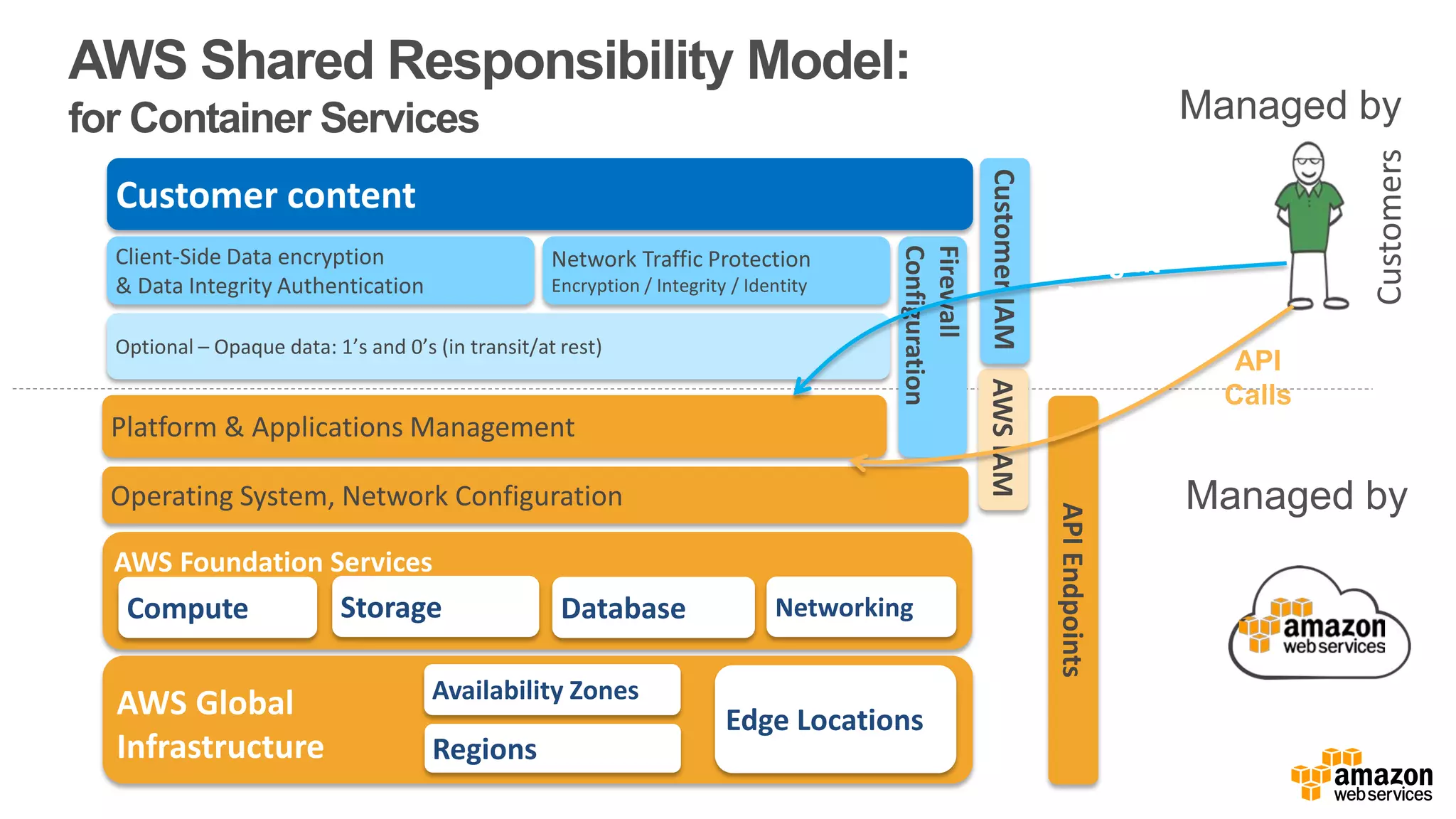
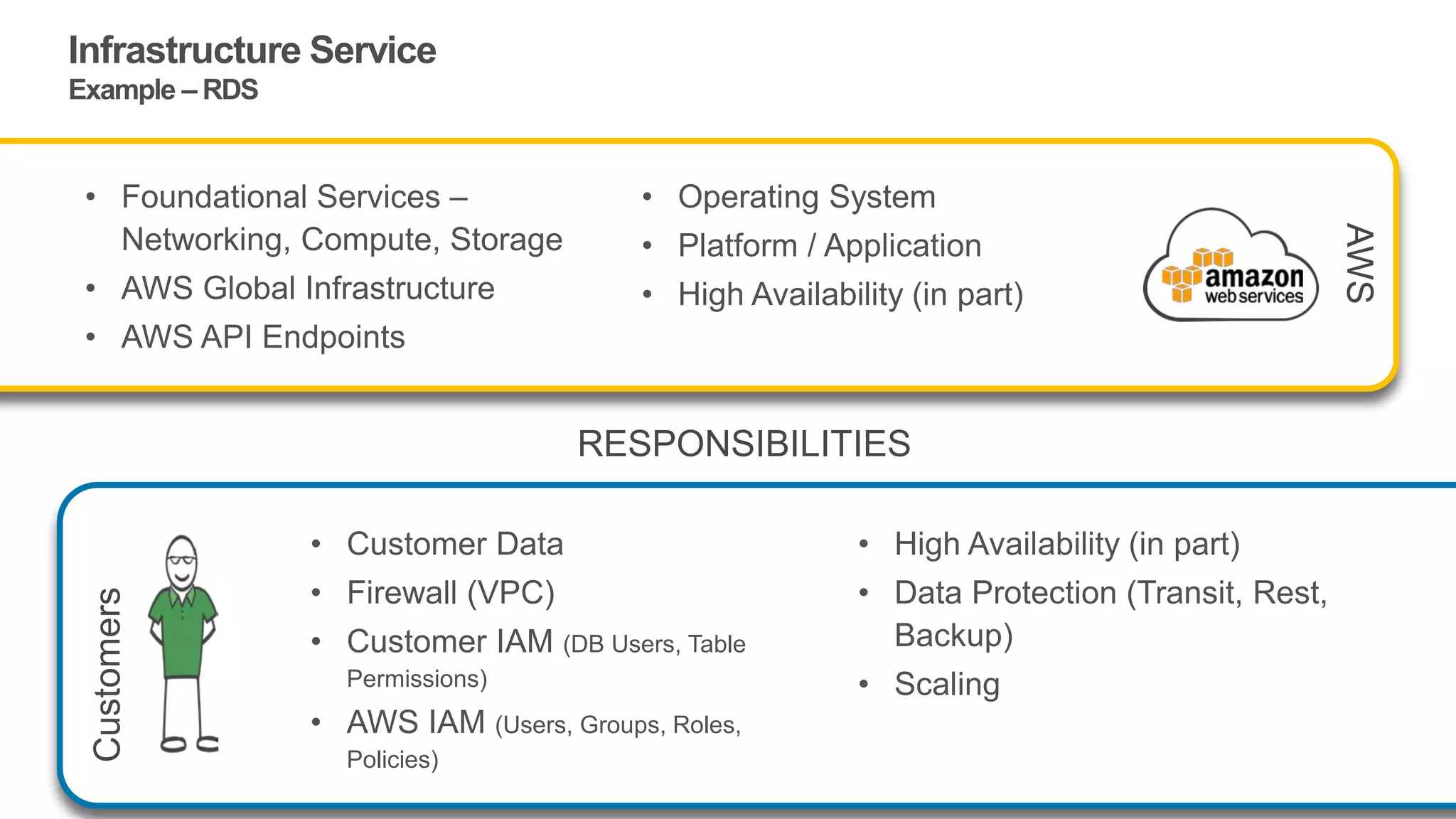
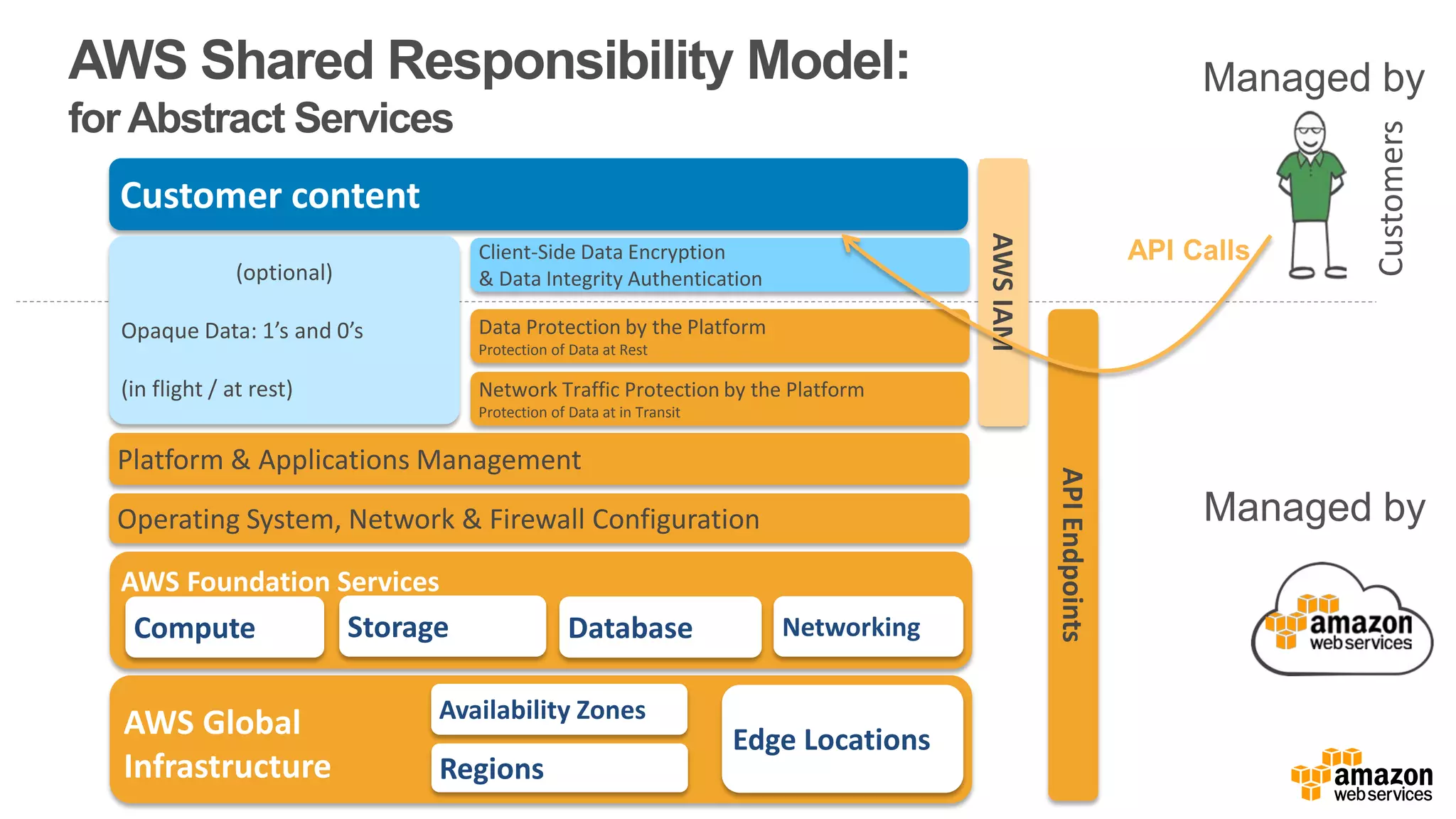
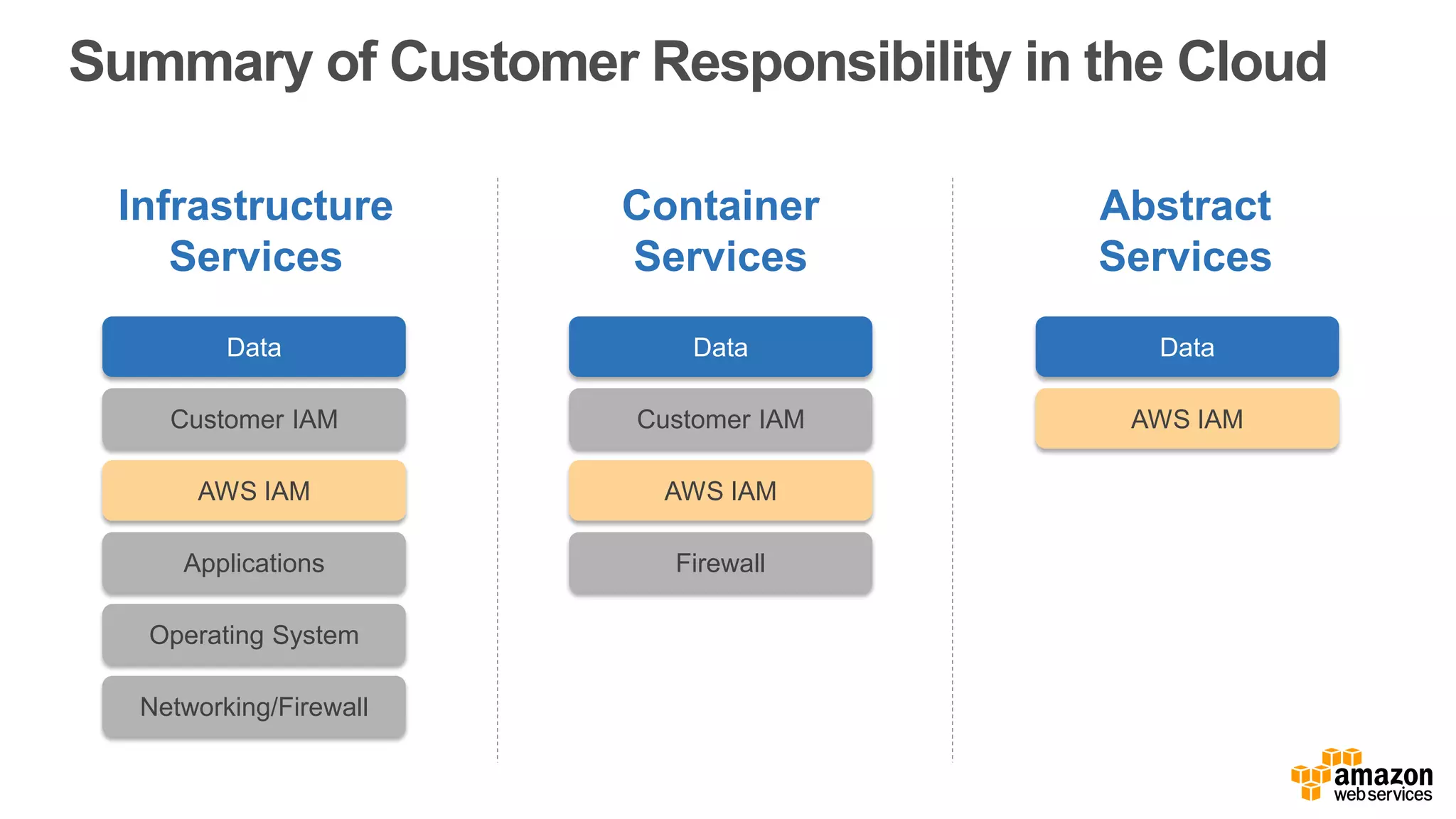
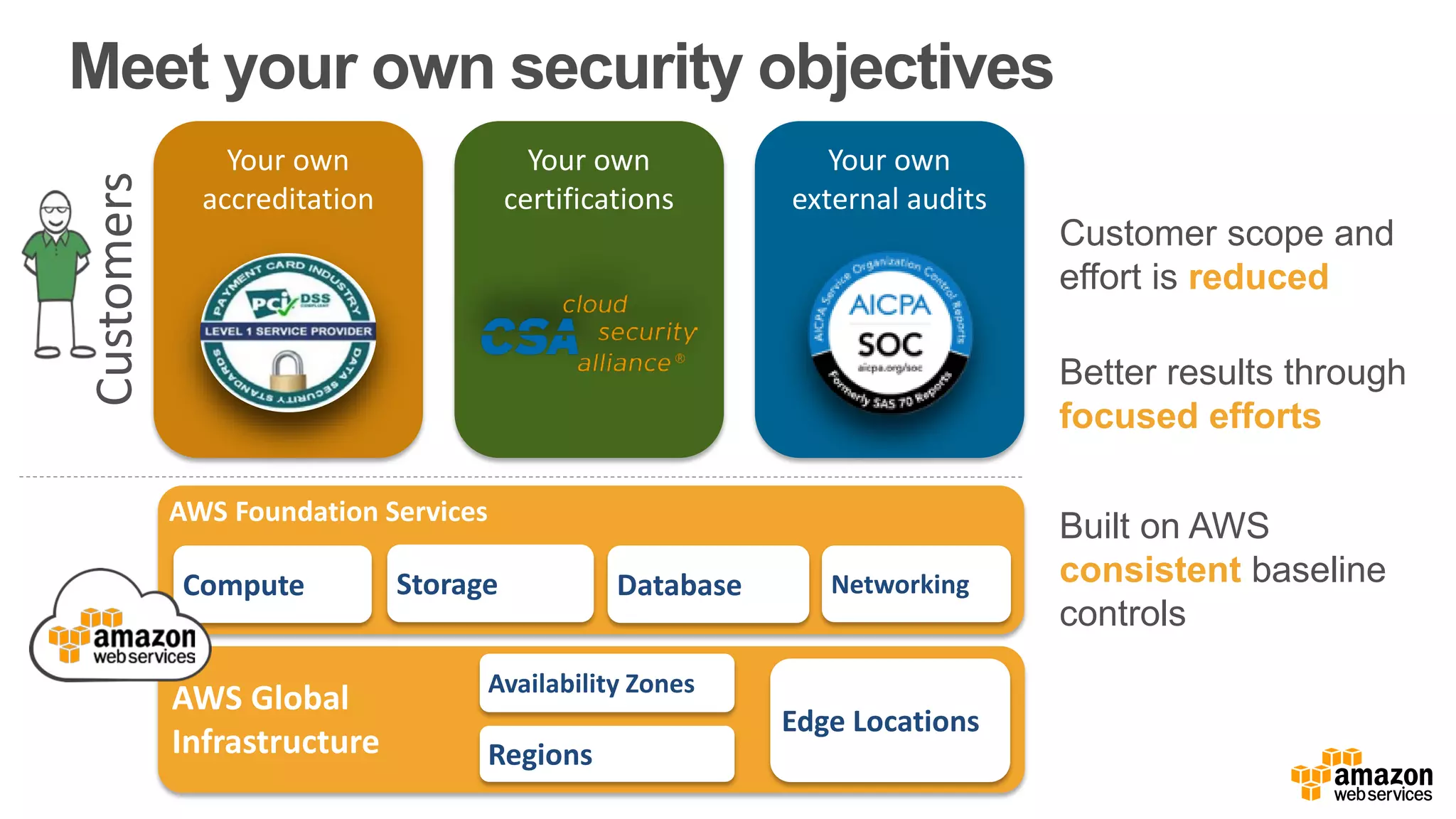
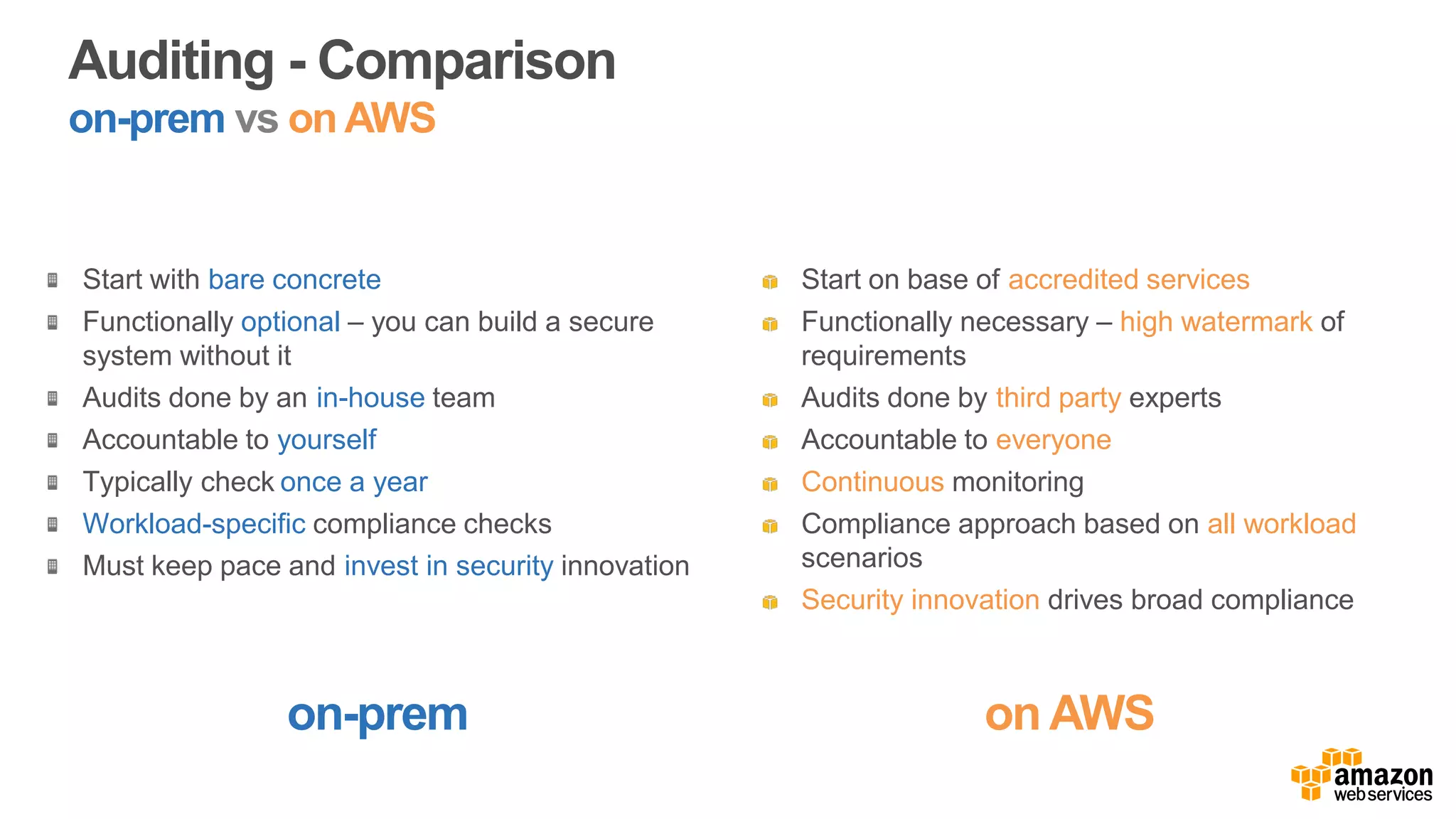
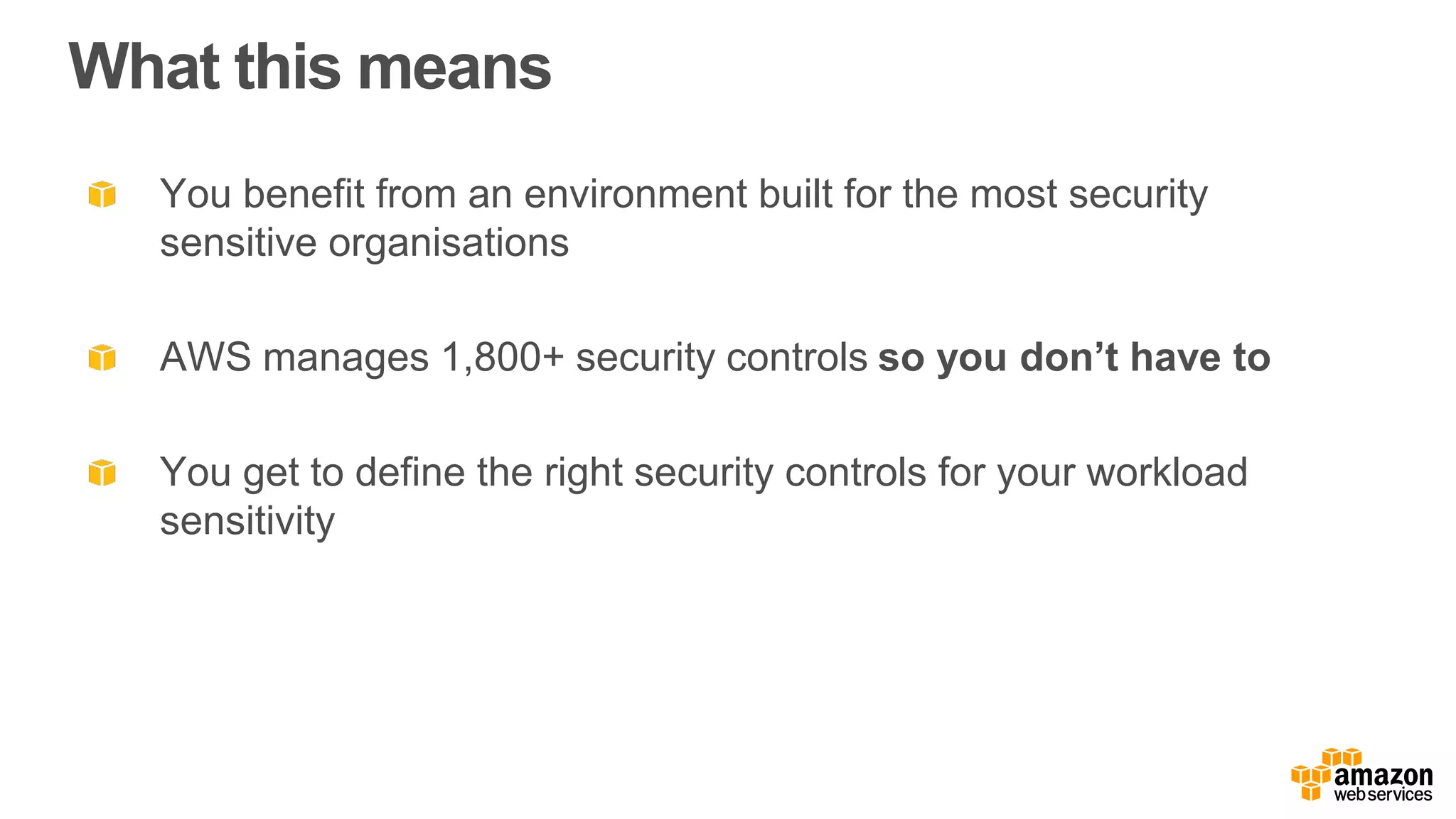
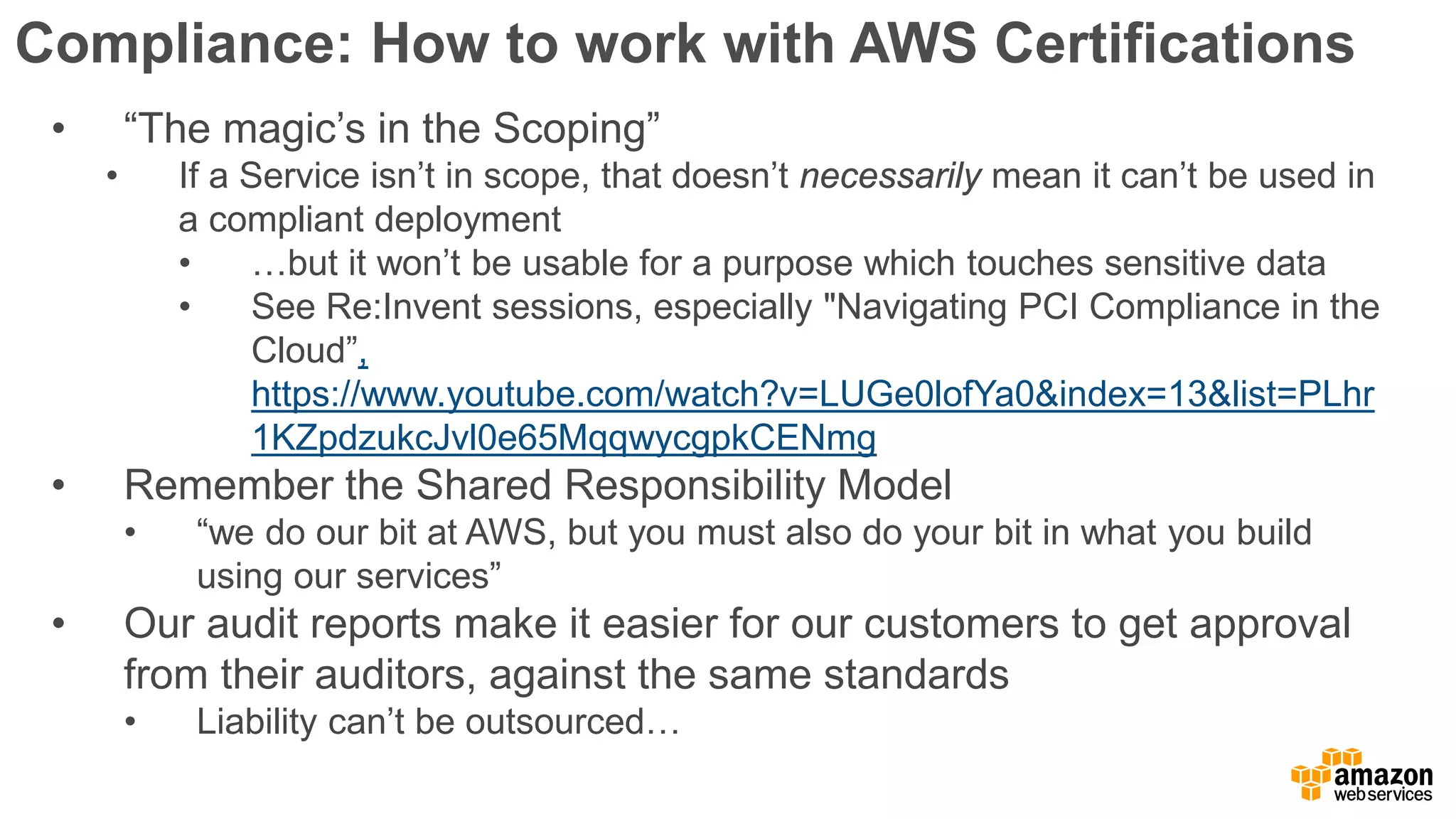
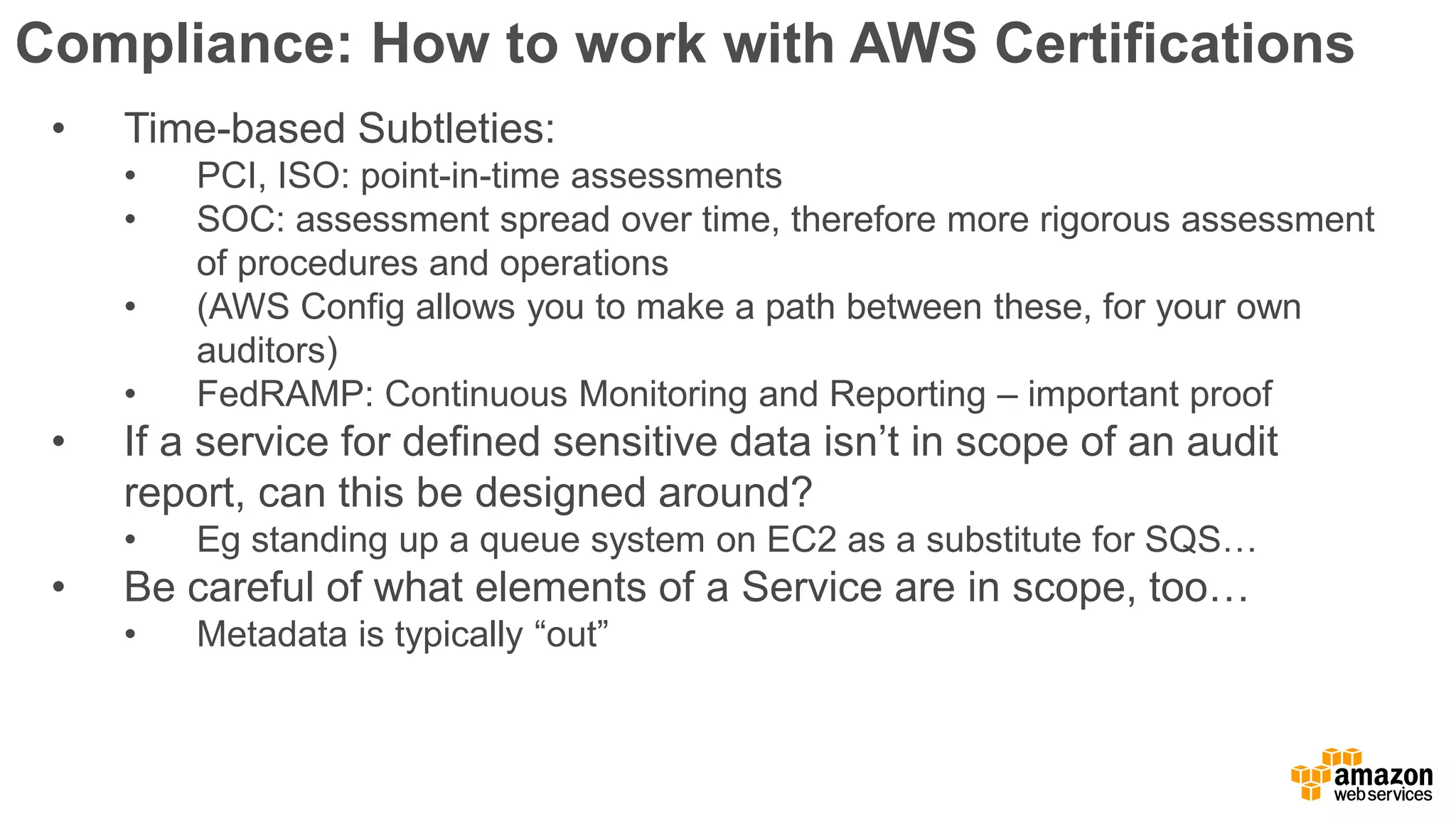
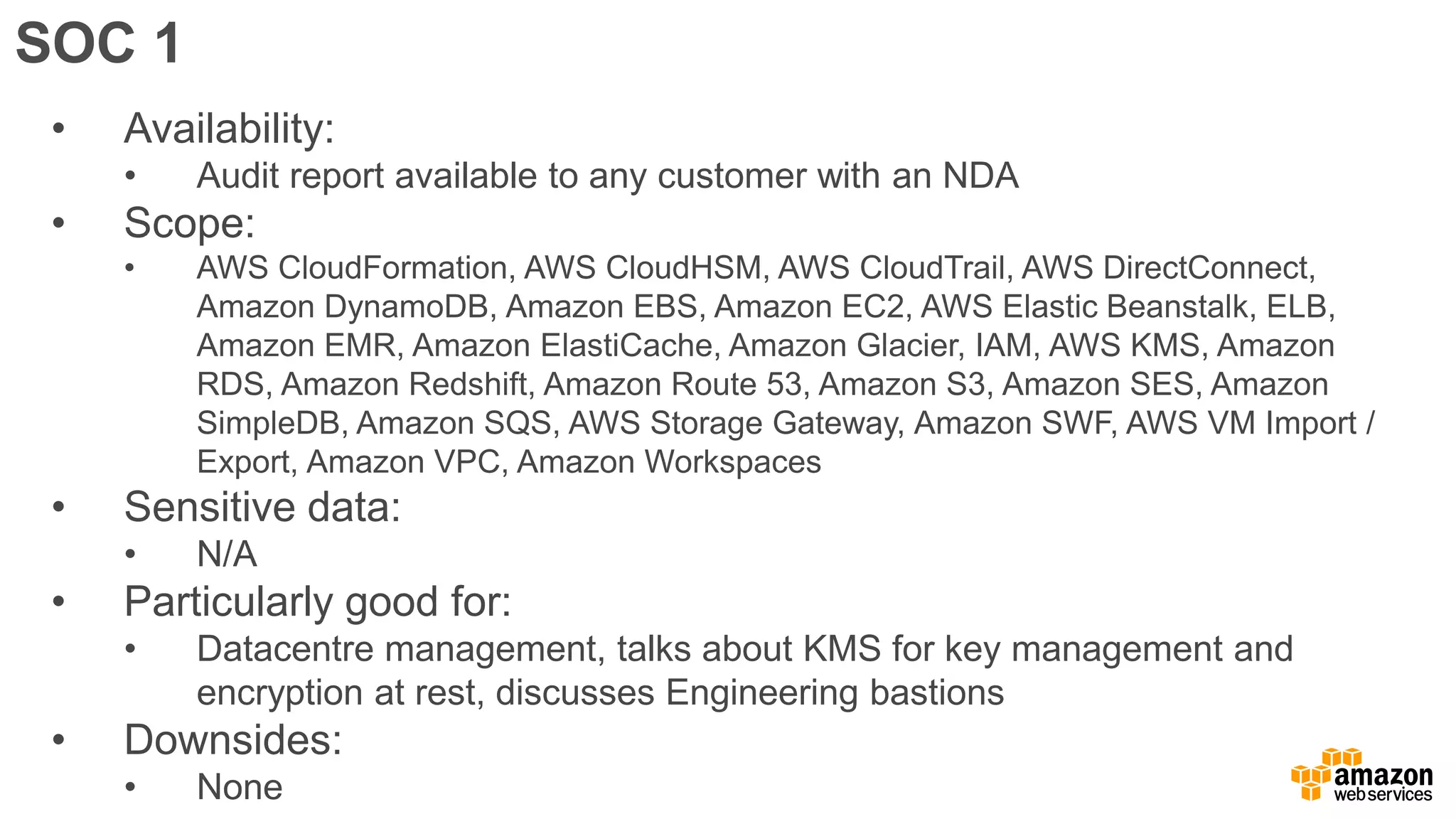
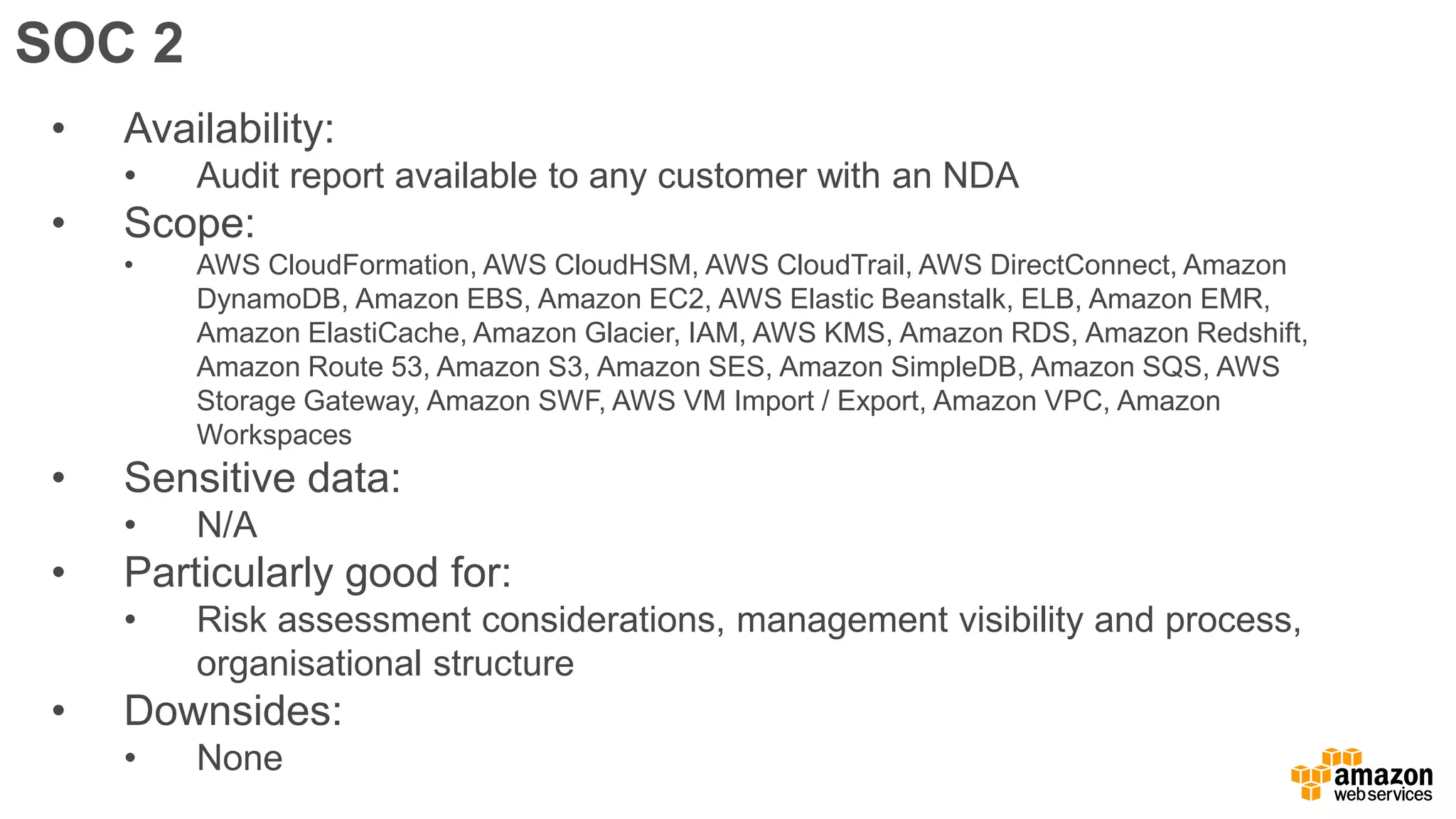
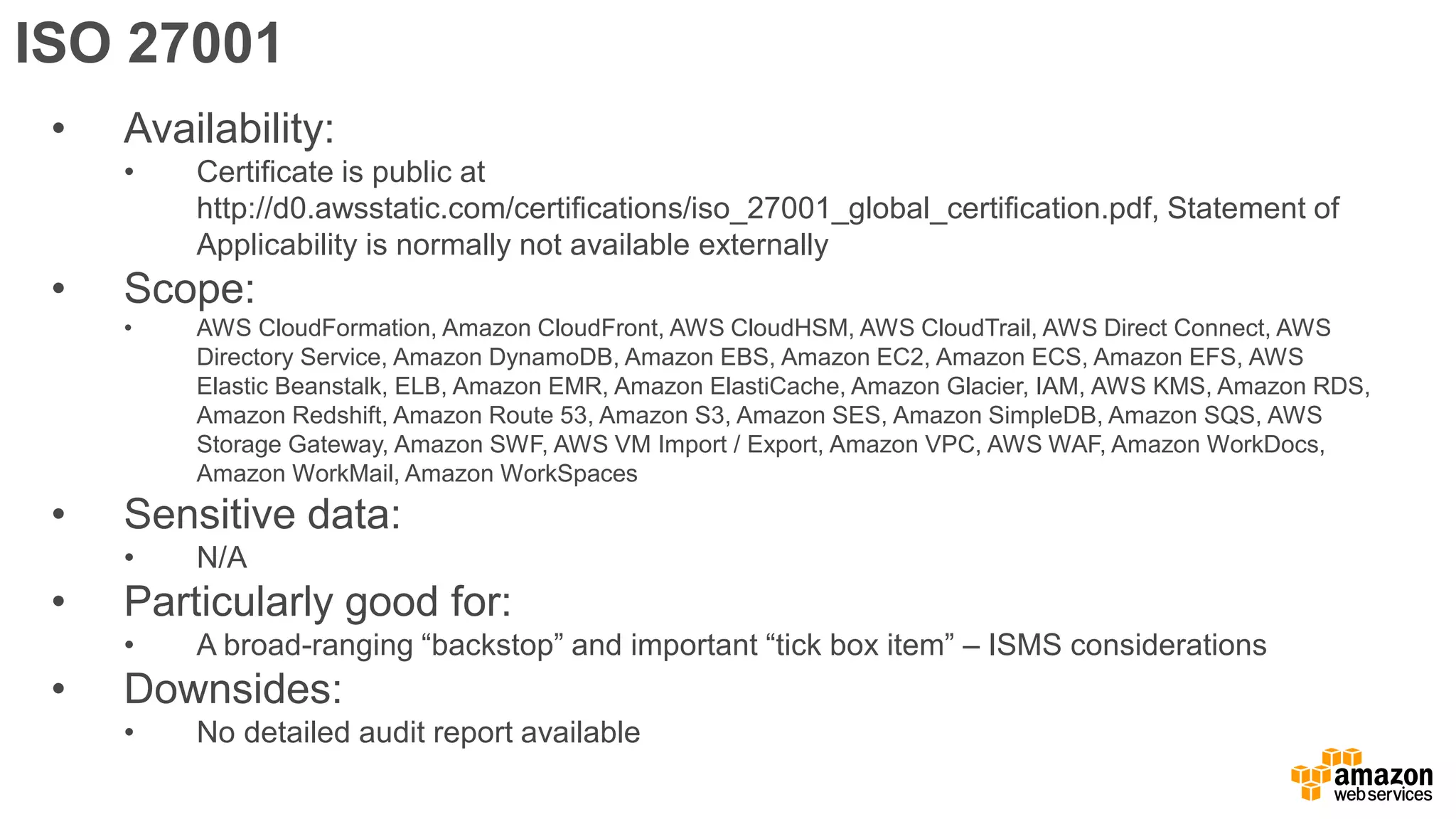
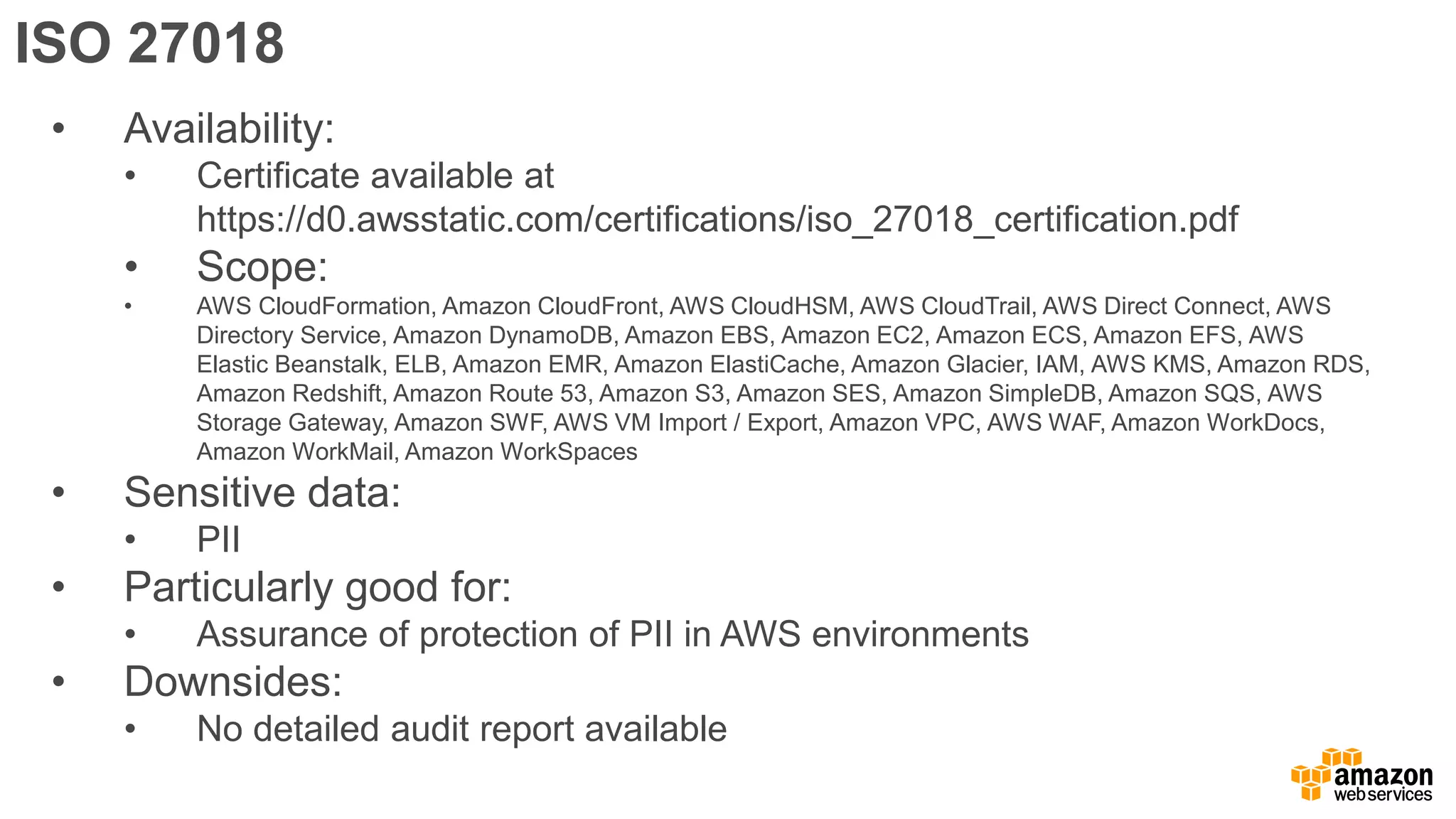
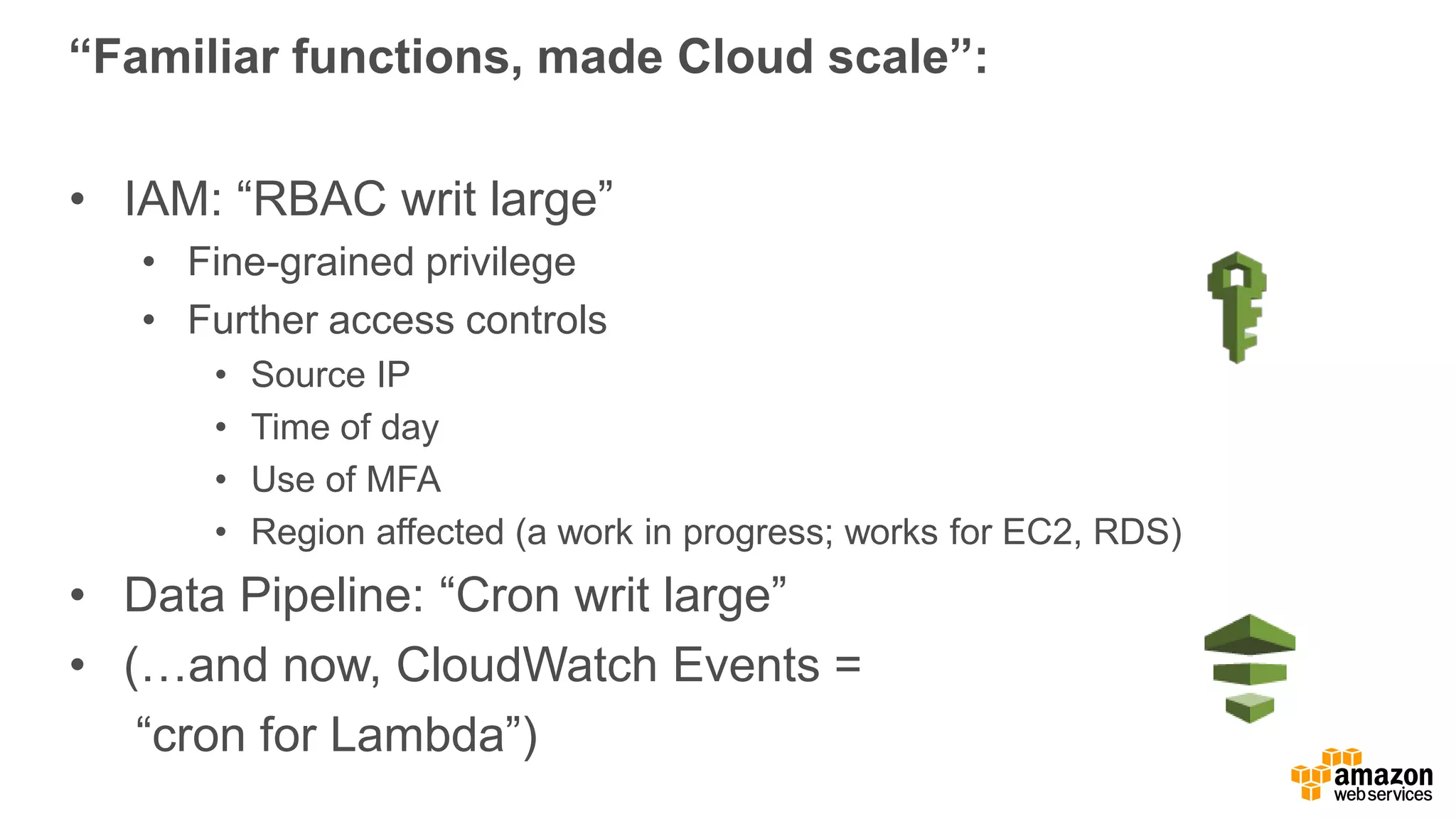
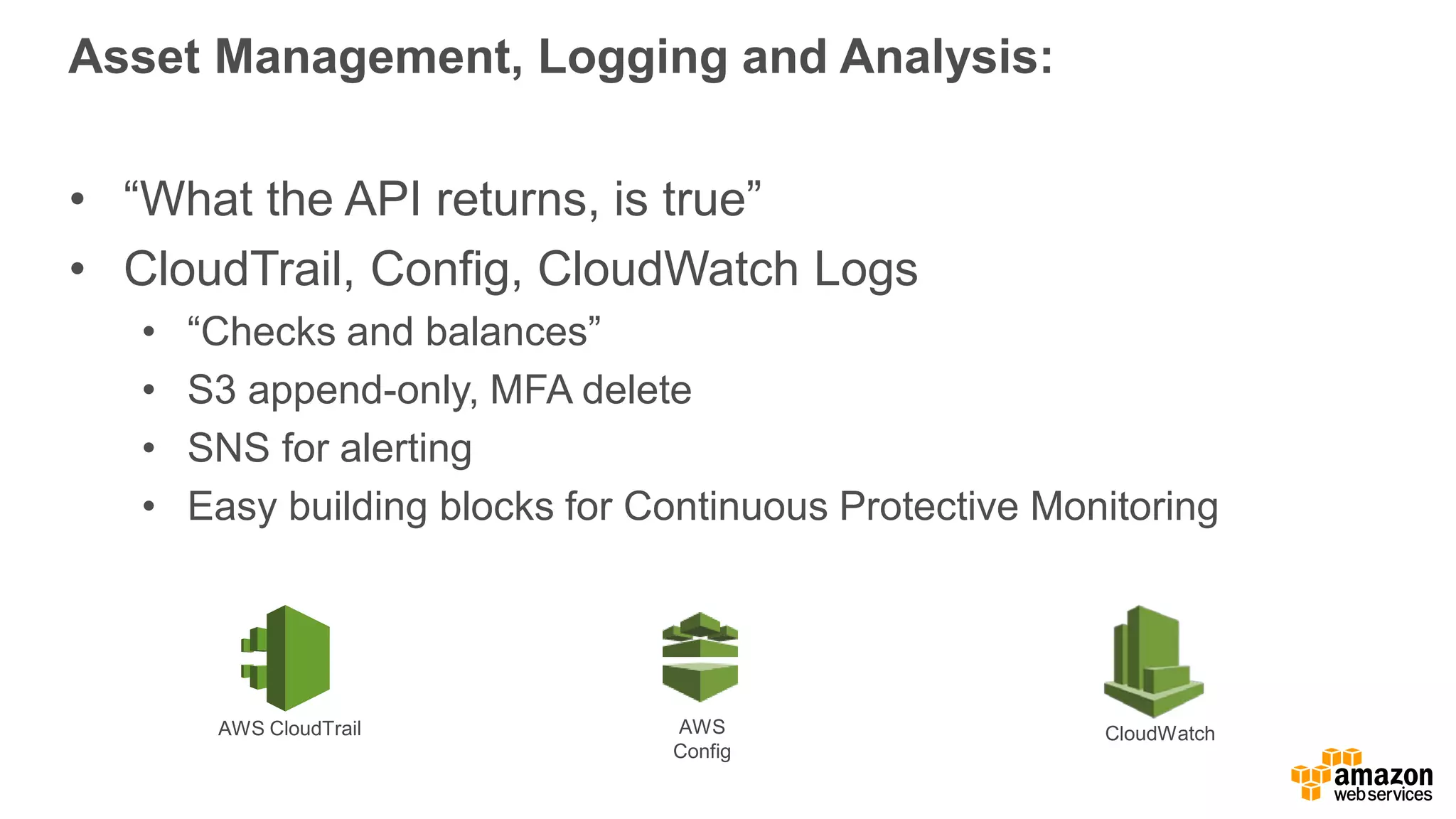
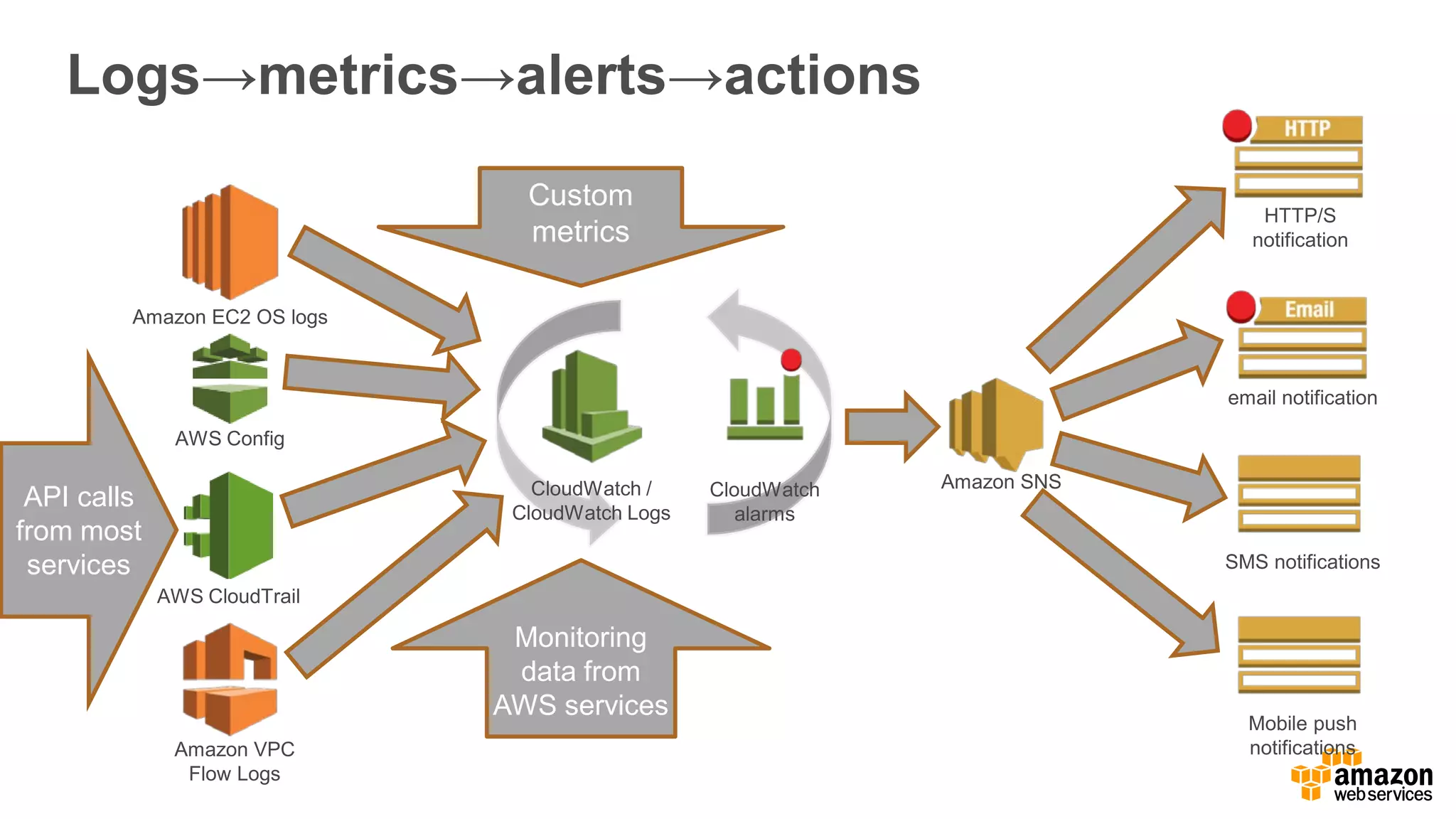
The document discusses information security in AWS, detailing the shared responsibility model between AWS and its customers, where AWS secures the cloud infrastructure while customers must secure their data and applications. It covers AWS foundational services, compliance requirements, and the various certifications available, emphasizing the importance of audits, risk management, and innovative security practices. The document also provides a summary of responsibilities in managing infrastructure, data protection, and regulatory compliance in a cloud environment.