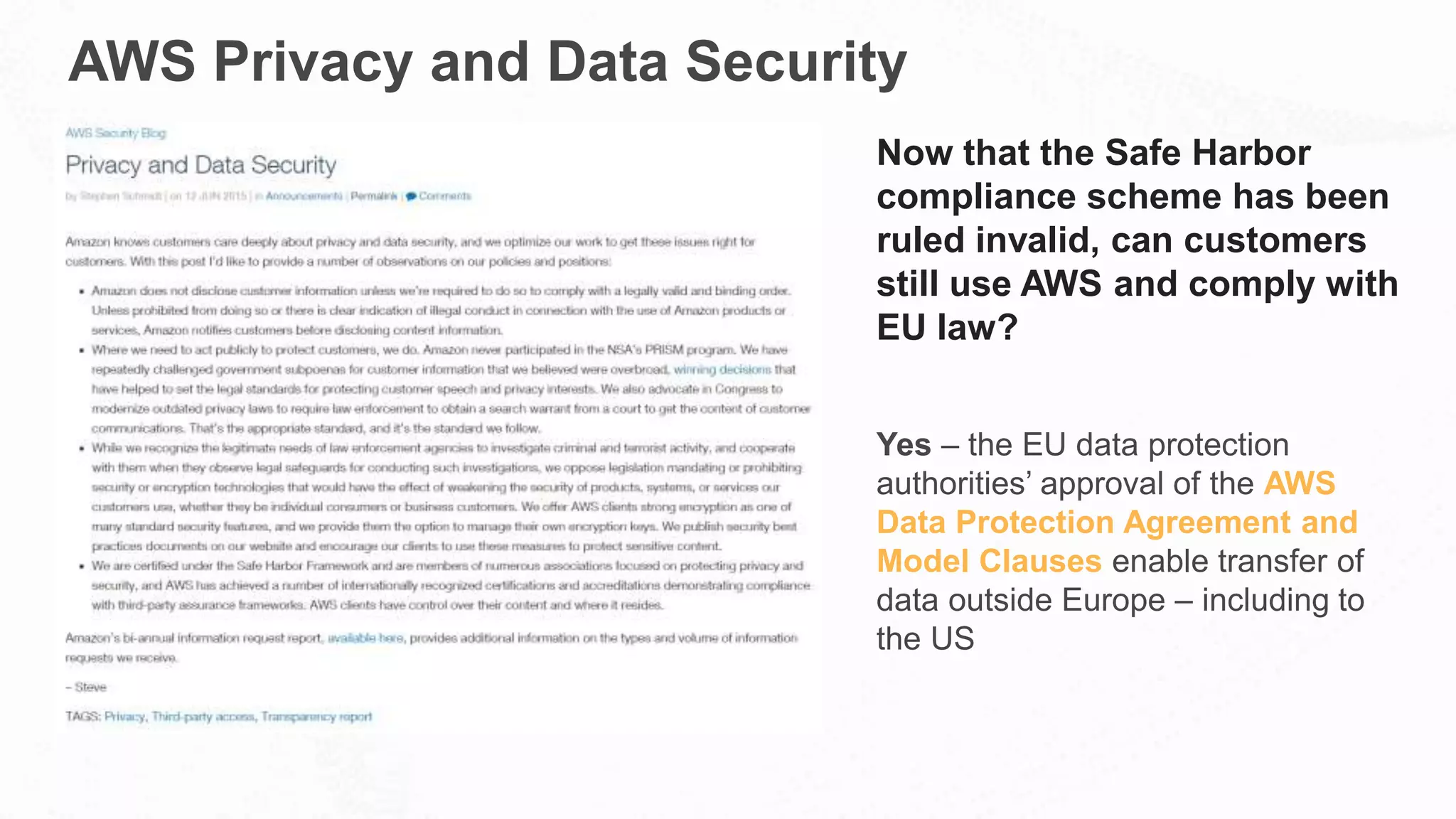
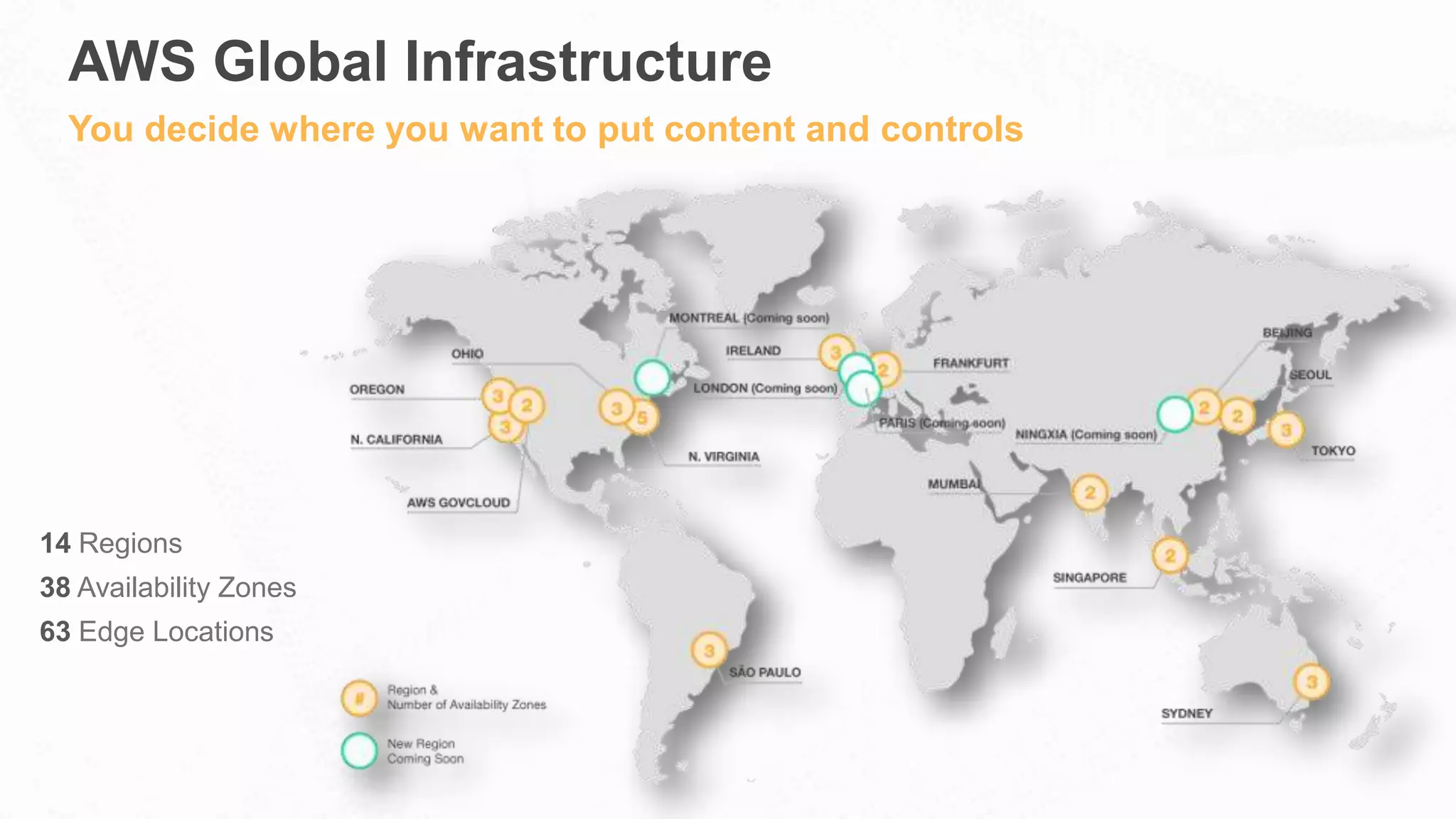
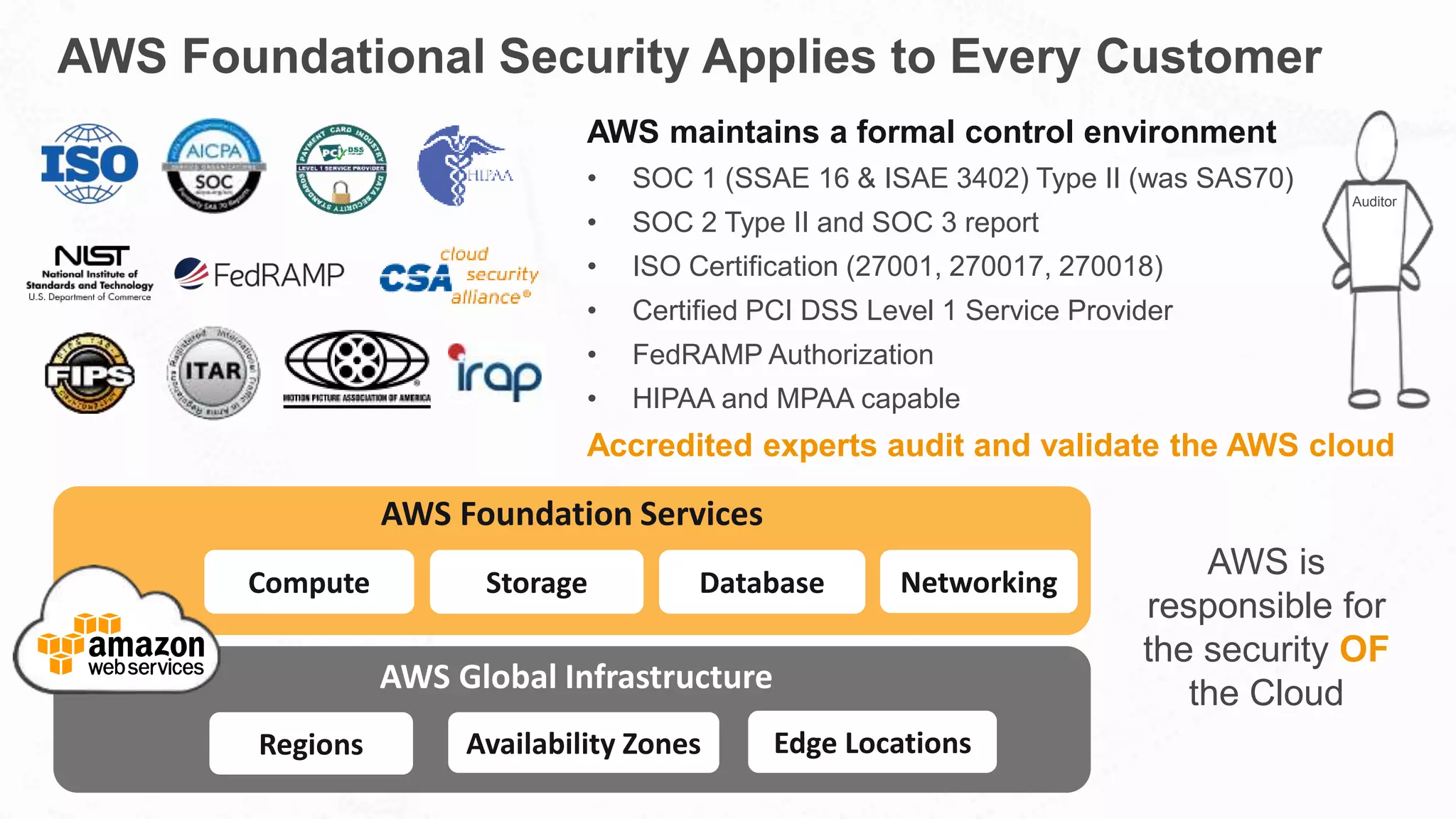
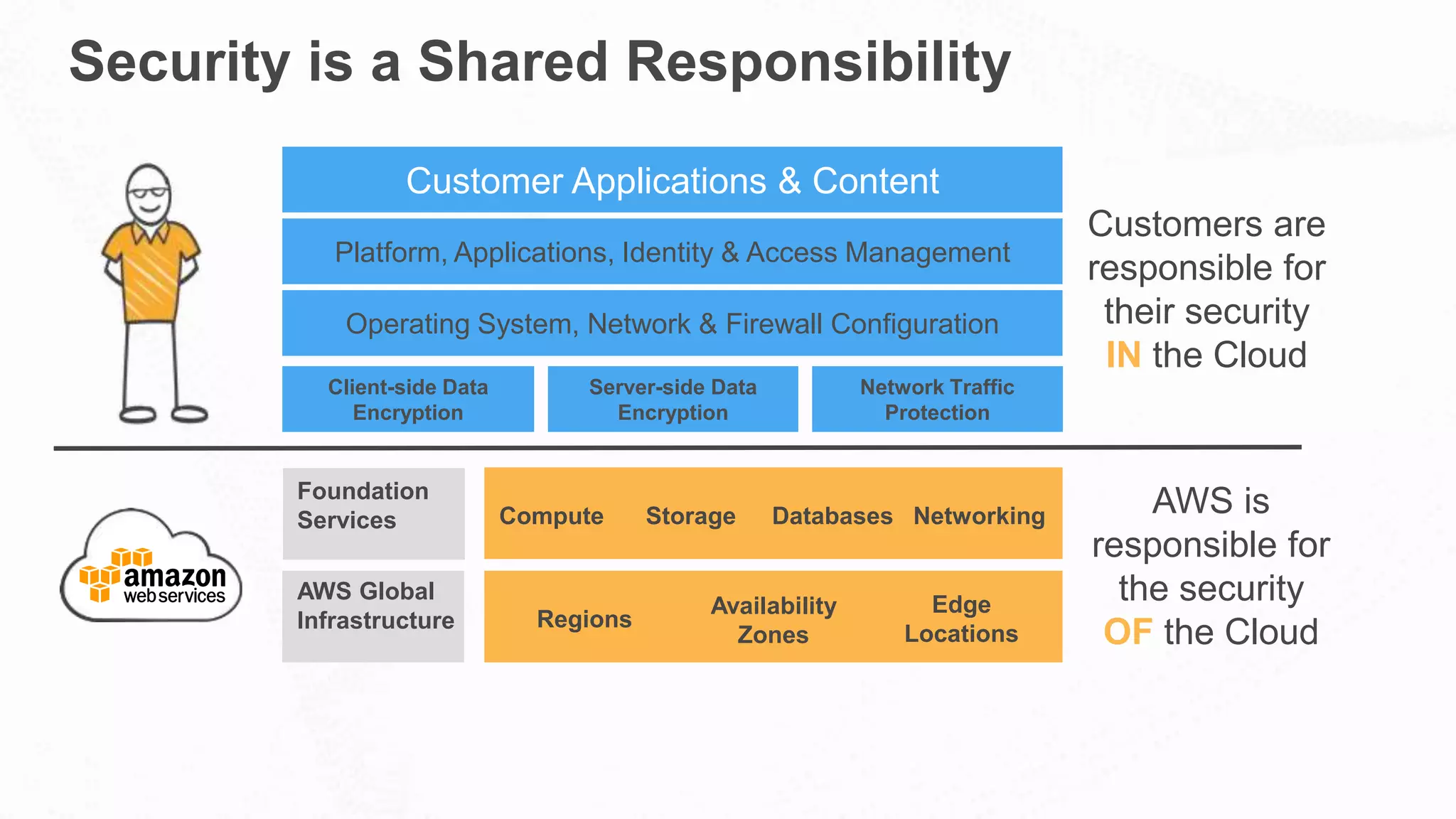
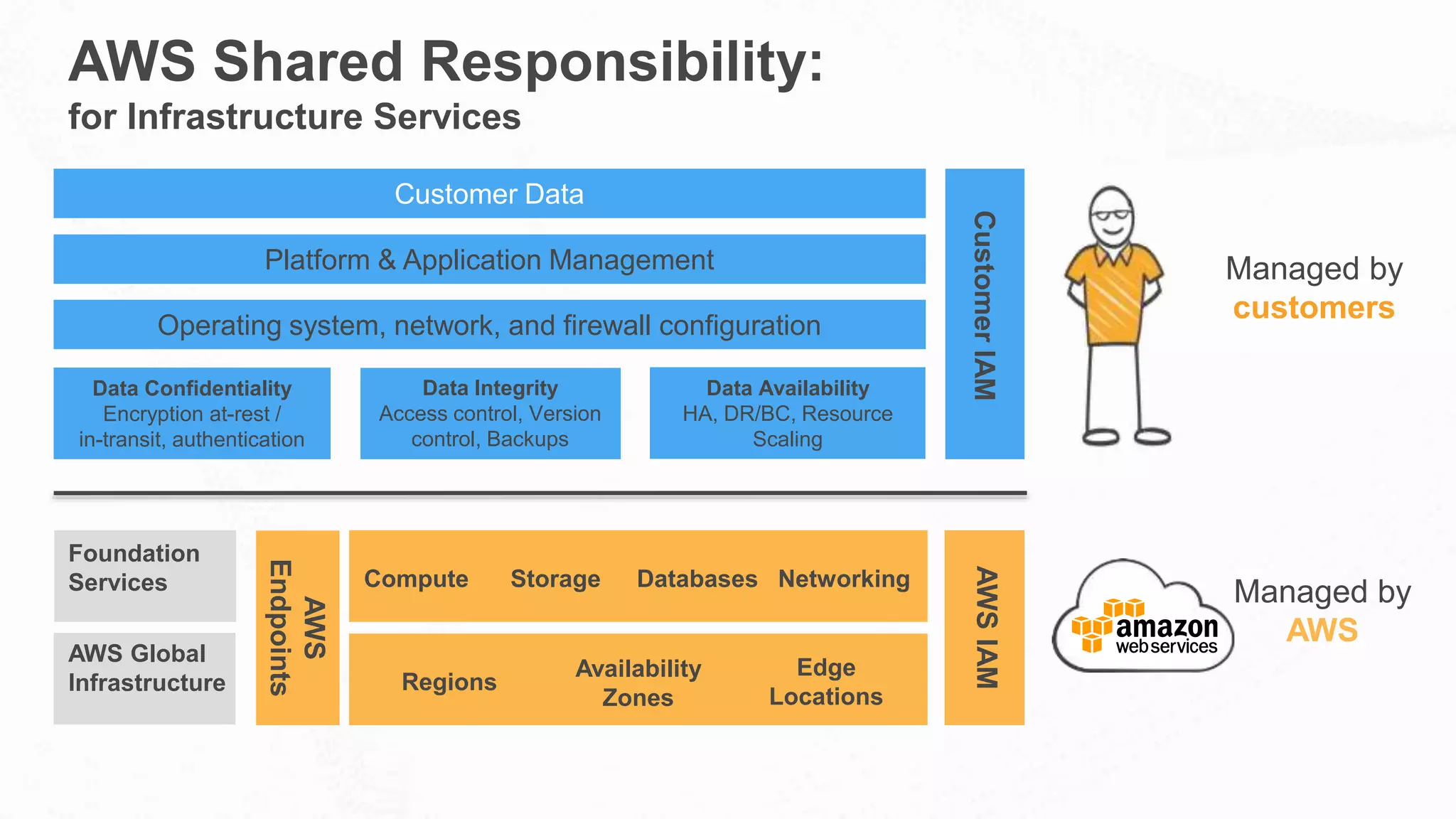
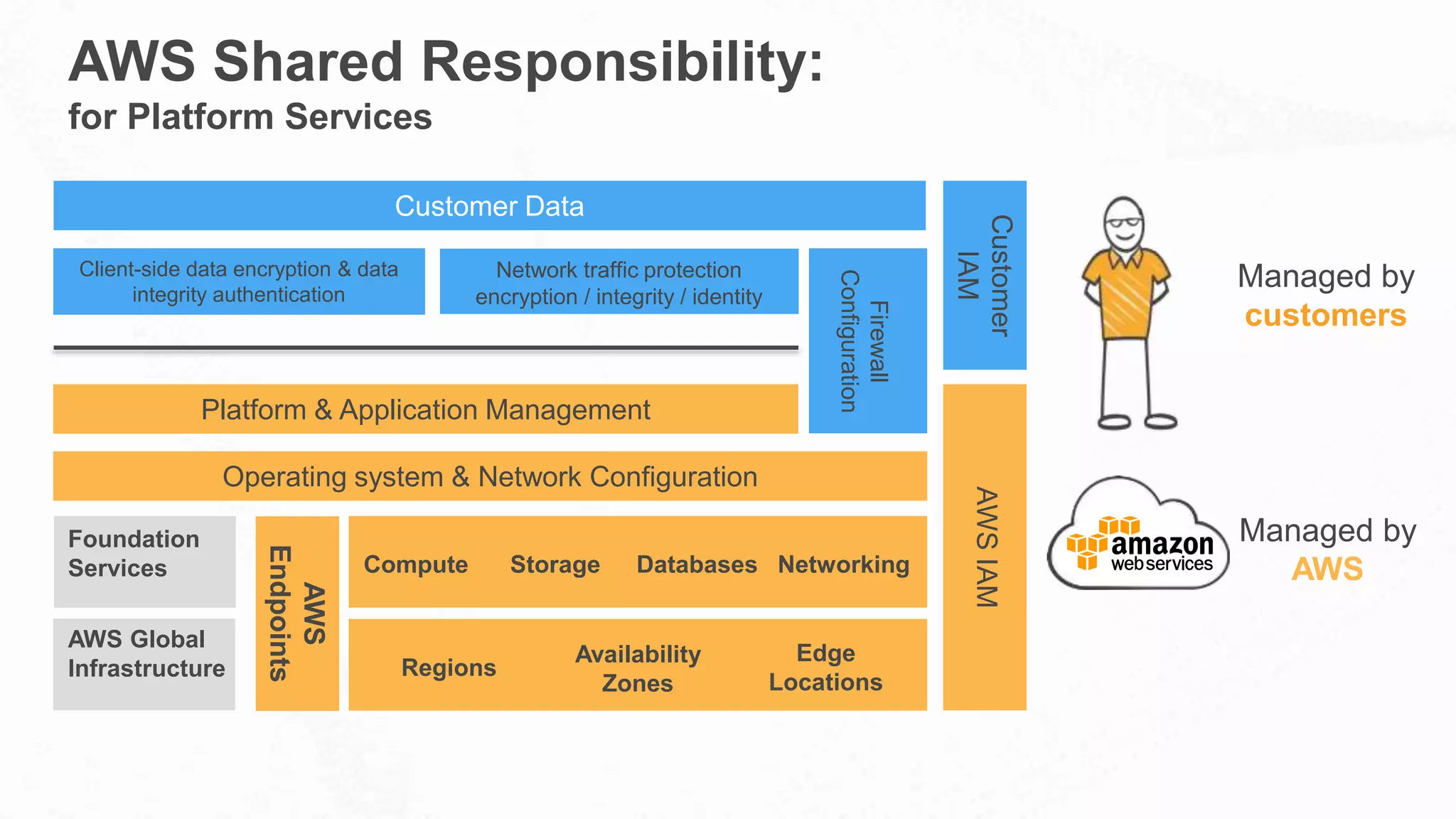
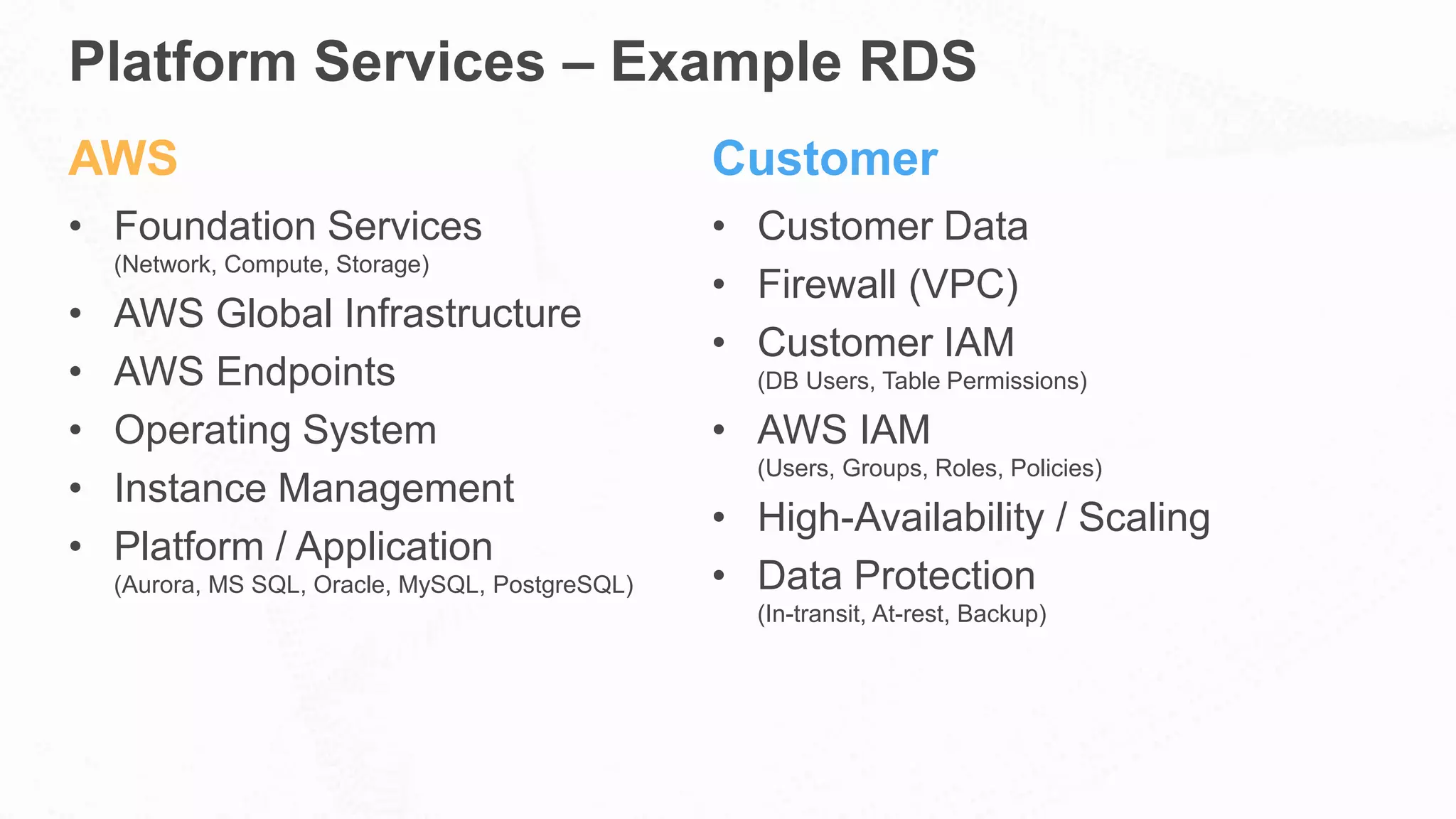
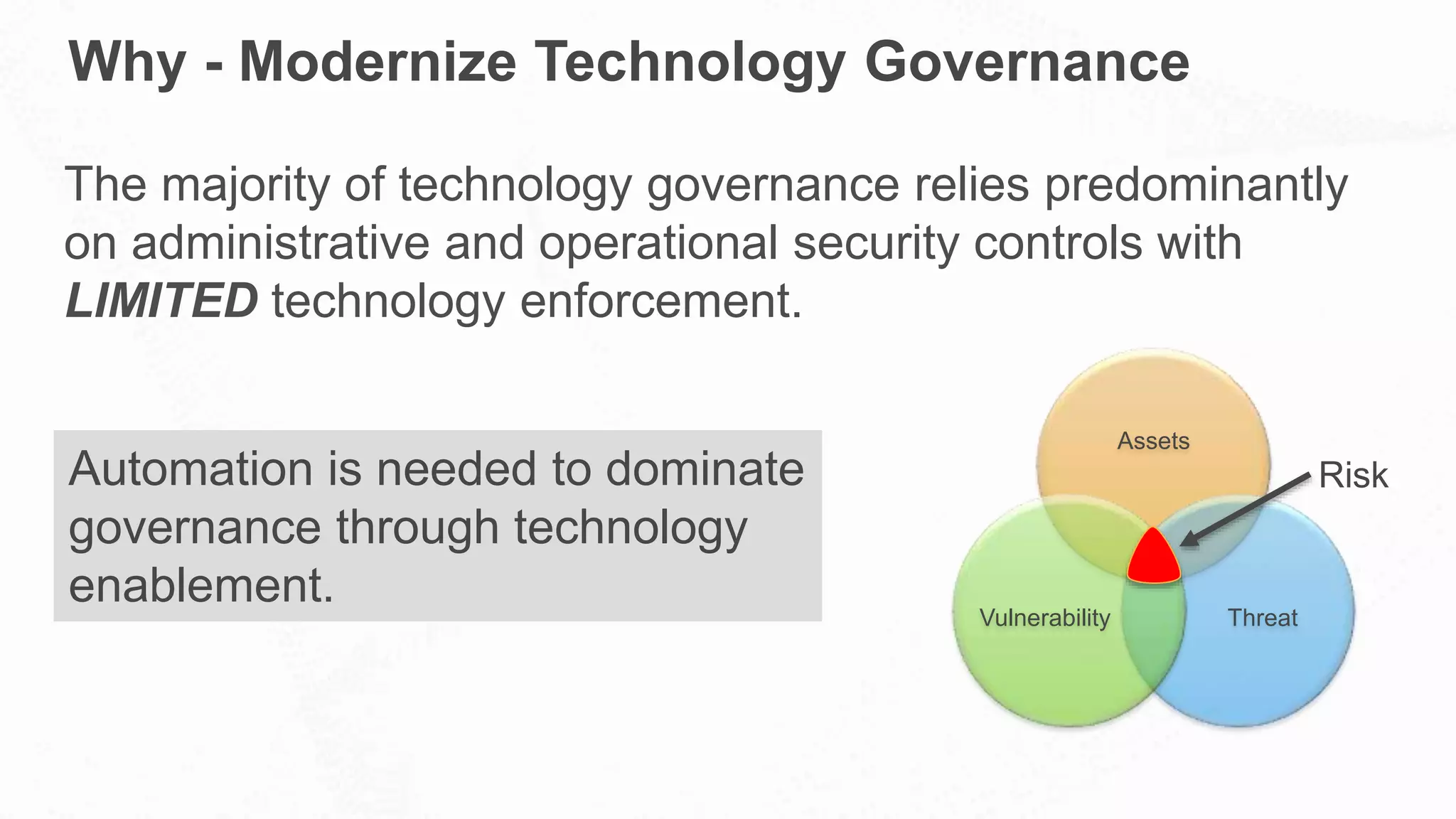
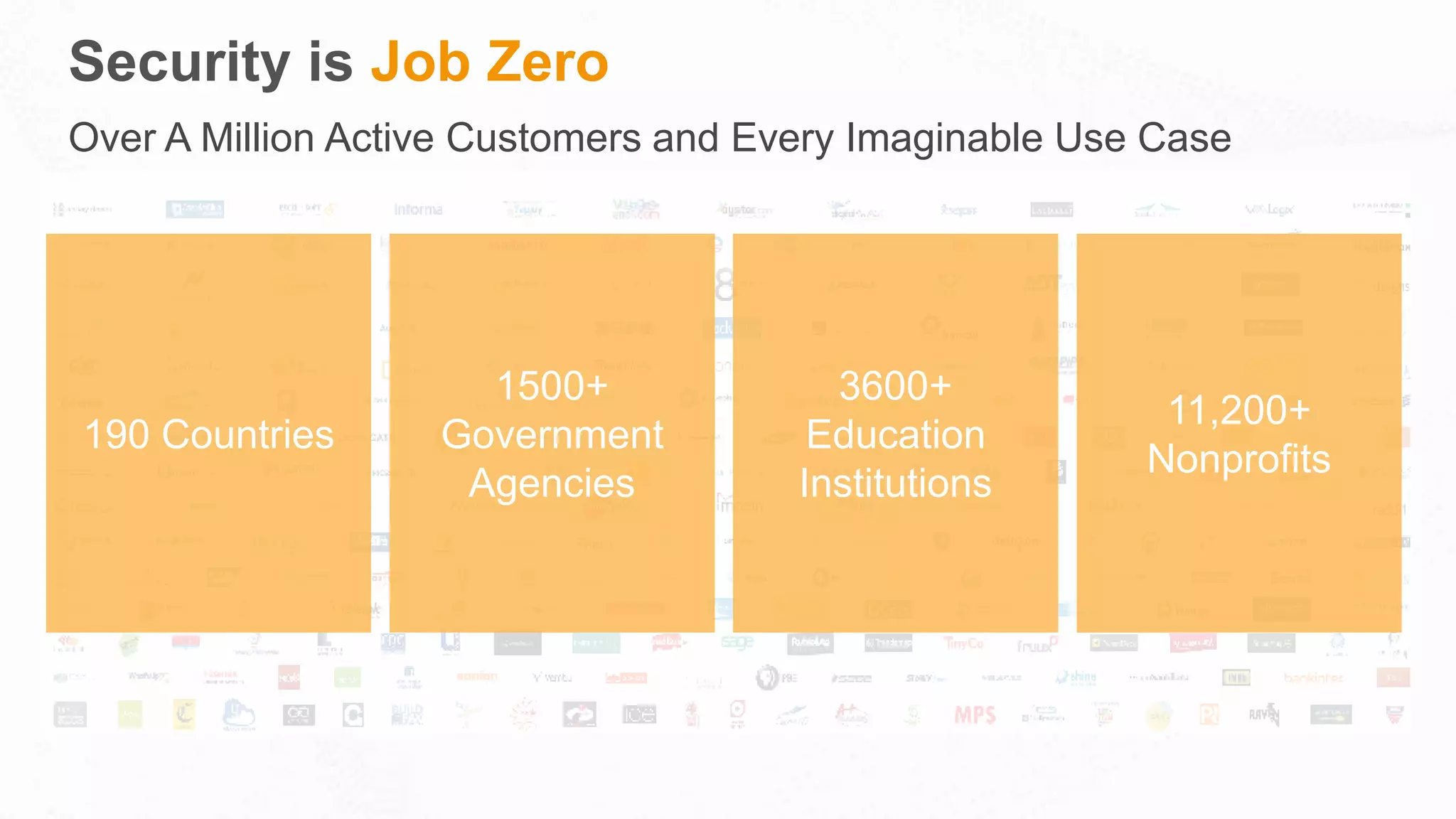
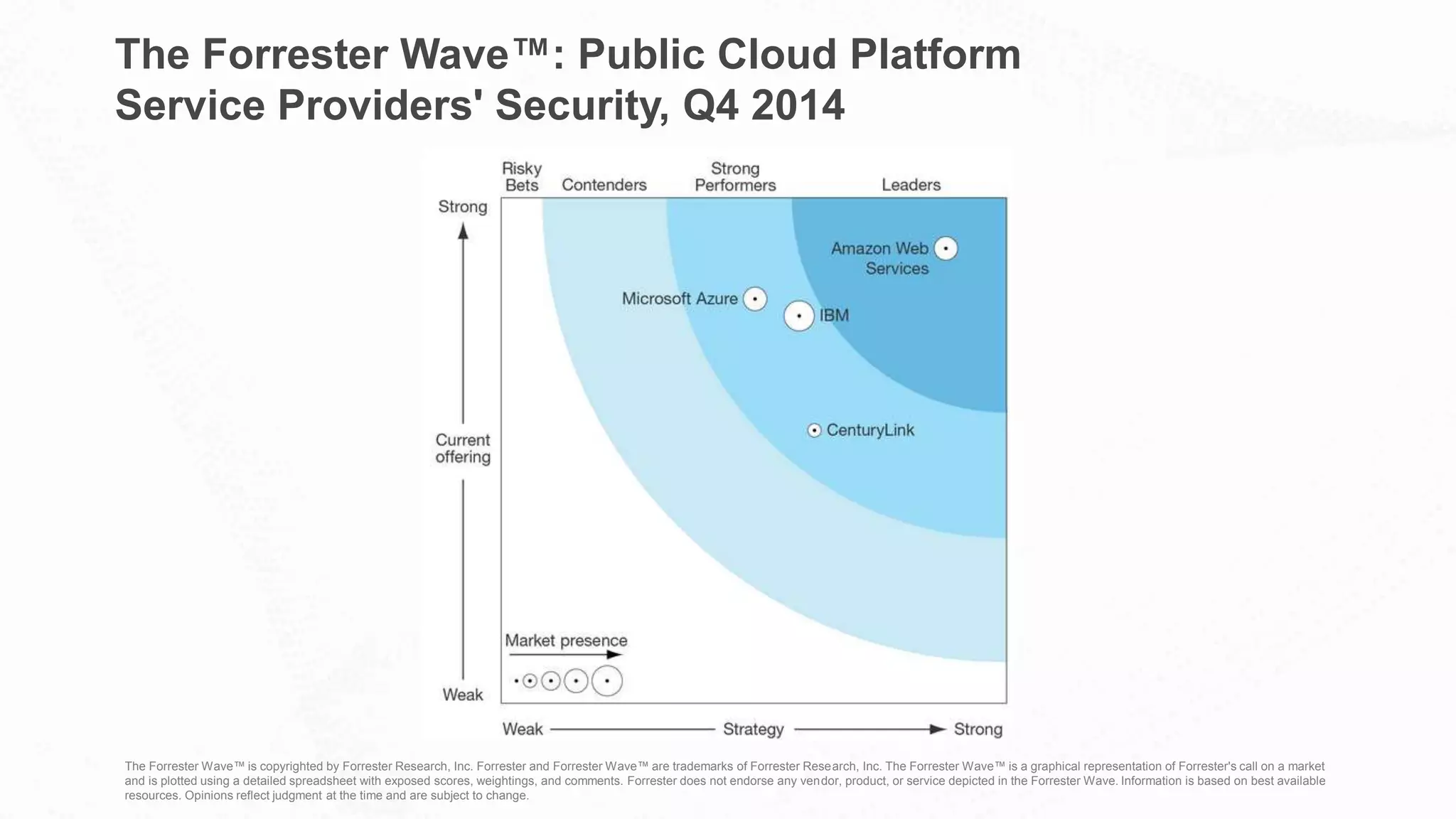
The document outlines AWS's commitment to security and compliance, highlighting its shared responsibility model where both AWS and customers are accountable for different aspects of security. It provides examples of various industries utilizing AWS for secure solutions and compliance adherence, alongside certifications and frameworks supporting their security measures. Additionally, it discusses the importance of modernizing technology governance through a security-by-design approach to efficiently manage and protect sensitive data.





![Certifications / Attestations Laws / Regulations / Privacy Alignments / Frameworks
DoD SRG DNB [Netherlands] CIS
FedRAMP EAR CLIA
FIPS EU Model Clauses CJIS
IRAP EU Data Protection Directive CMS EDGE
ISO 9001 FERPA CMSR
ISO 27001 GLBA CSA
ISO 27017 HIPAA FDA
ISO 27018 HITECH FedRAMP TIC
MLPS Level 3 IRS 1075 FISC
MTCS ITAR FISMA
PCI DSS Level 1 My Number Act [Japan] G-Cloud
SEC Rule 17-a-4(f) Privacy Act [Australia] GxP (FDA CFR 21 Part 11)
SOC 1 Privacy Act [New Zealand] IT Grundschutz
SOC 2 PDPA - 2010 [Malaysia] MITA 3.0
SOC 3 PDPA - 2012 [Singapore] MPAA
UK Cyber Essentials U.K. DPA - 1988 NERC
VPAT / Section 508 NIST
EU-US Privacy Shield PHR
Spanish DPA Authorization UK Cloud Security Principles
Comprehensive Security and Compliance](https://image.slidesharecdn.com/alertlogic-cloud-security-summit-dallas-161025210108/75/Modernizing-Technology-Governance-8-2048.jpg)