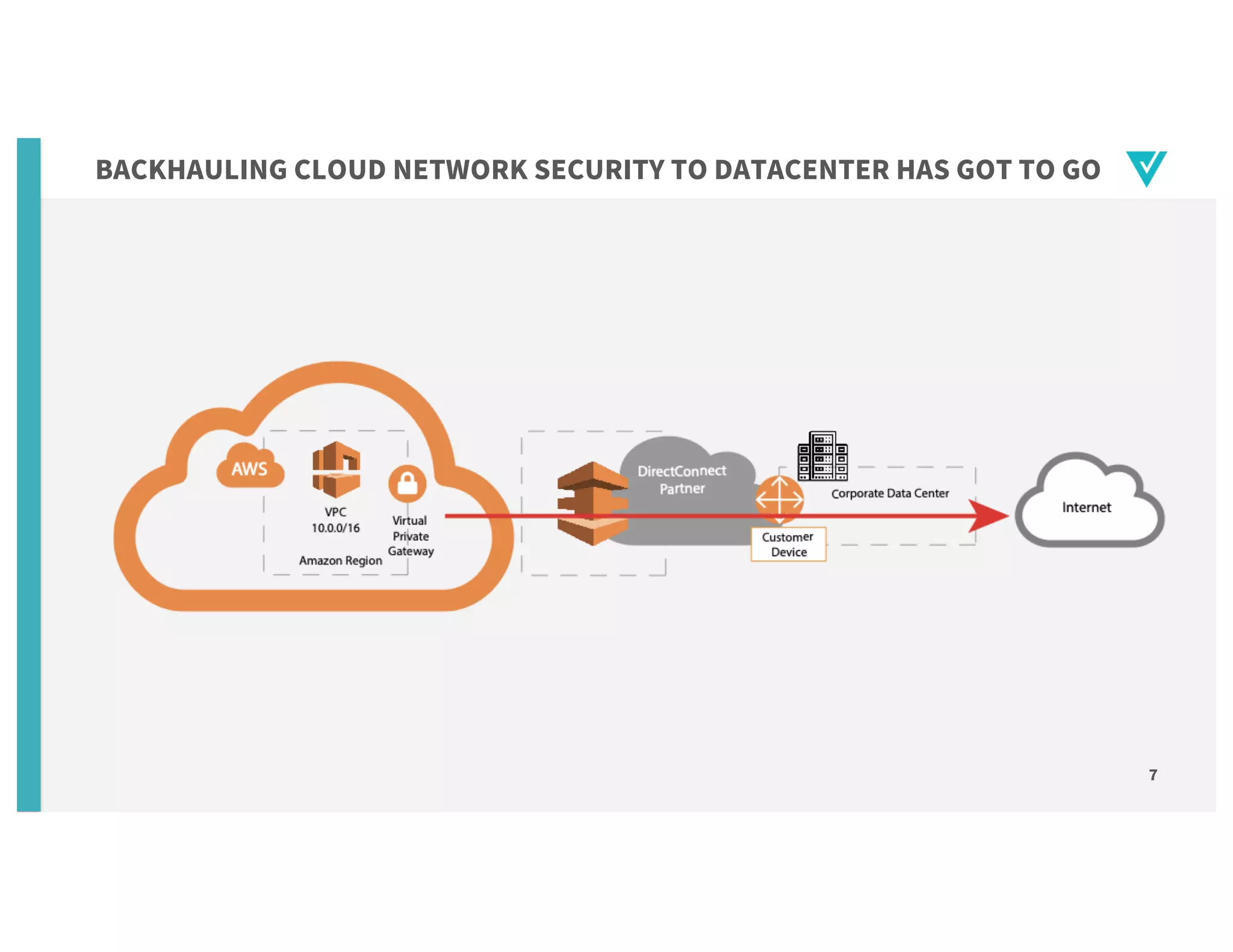
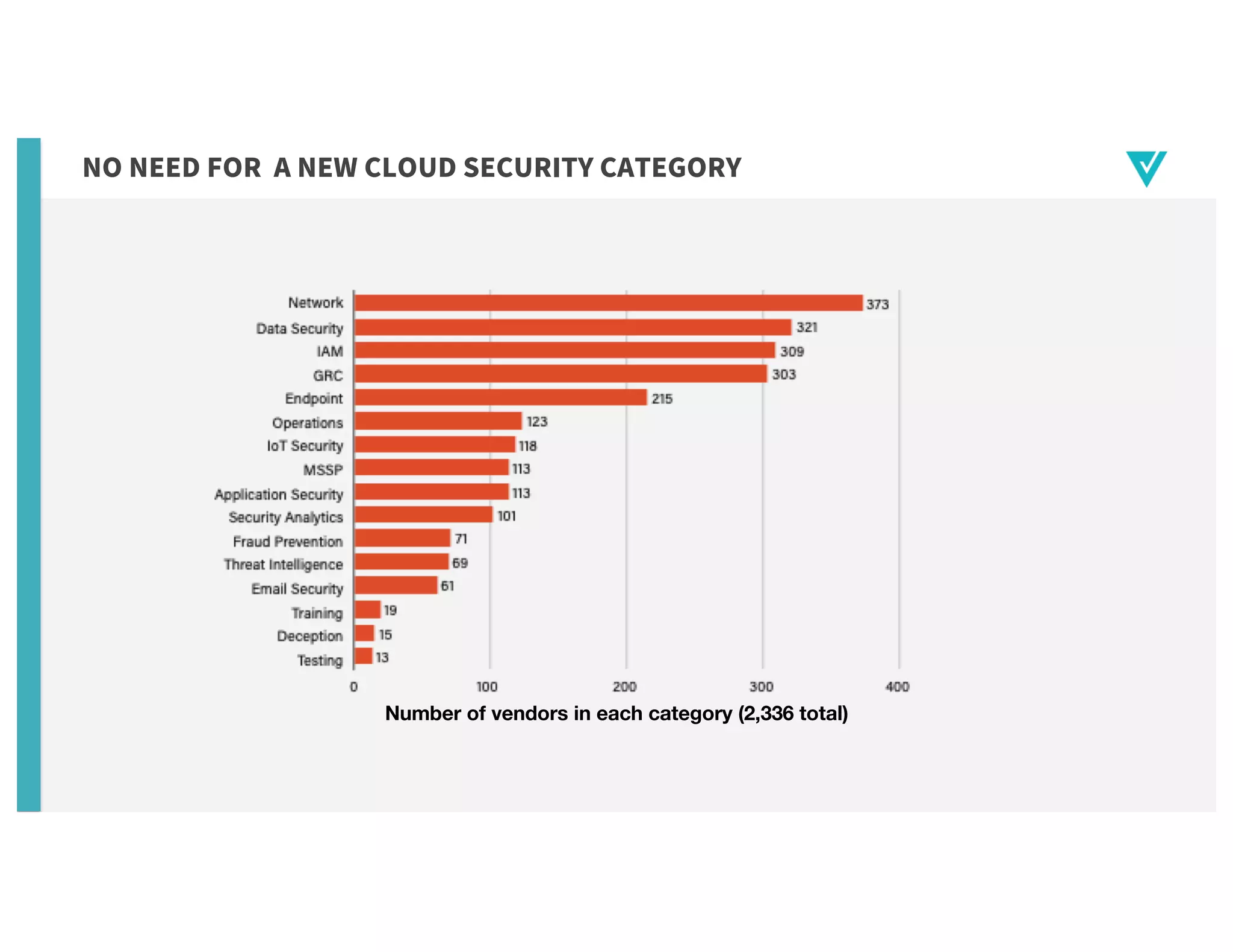
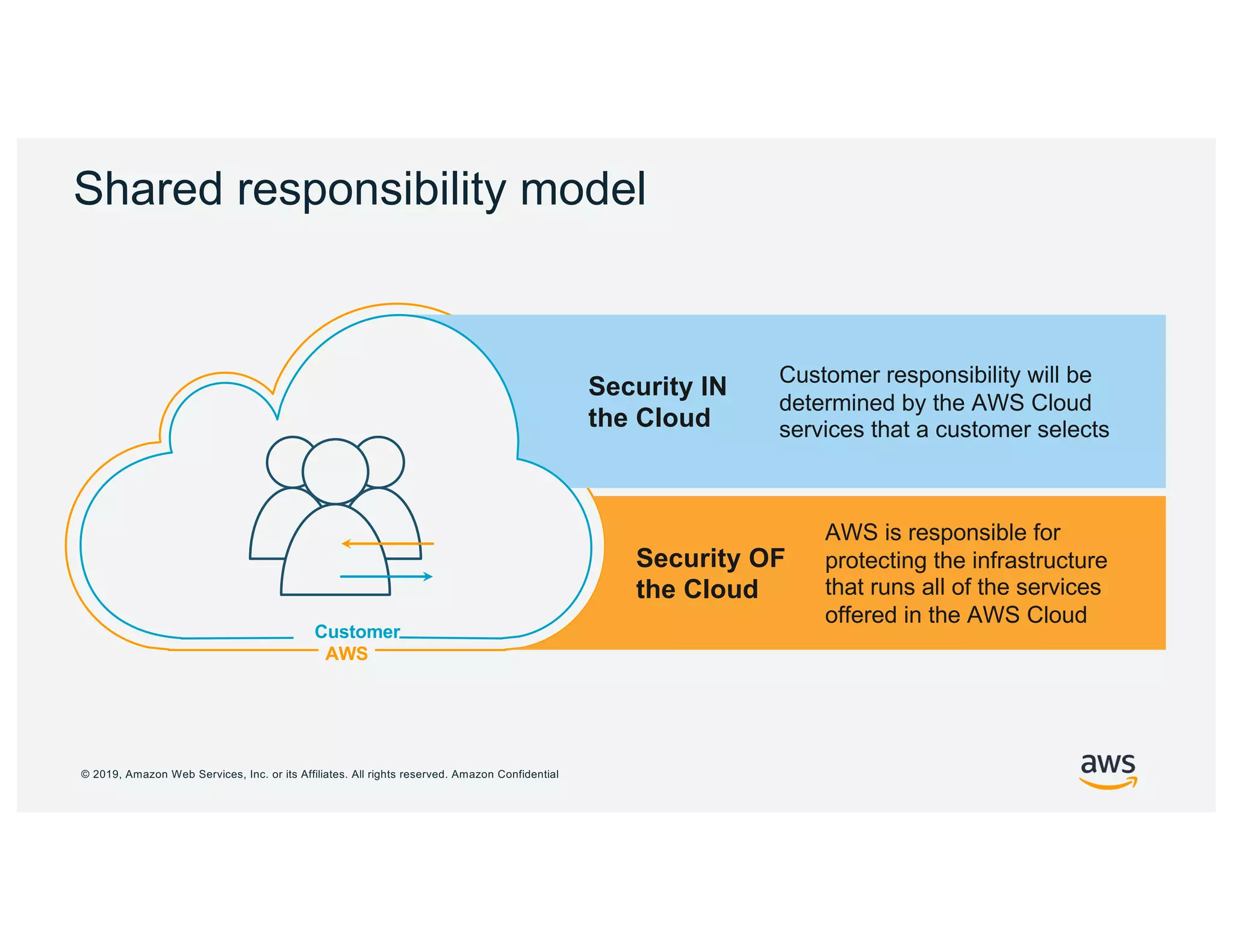
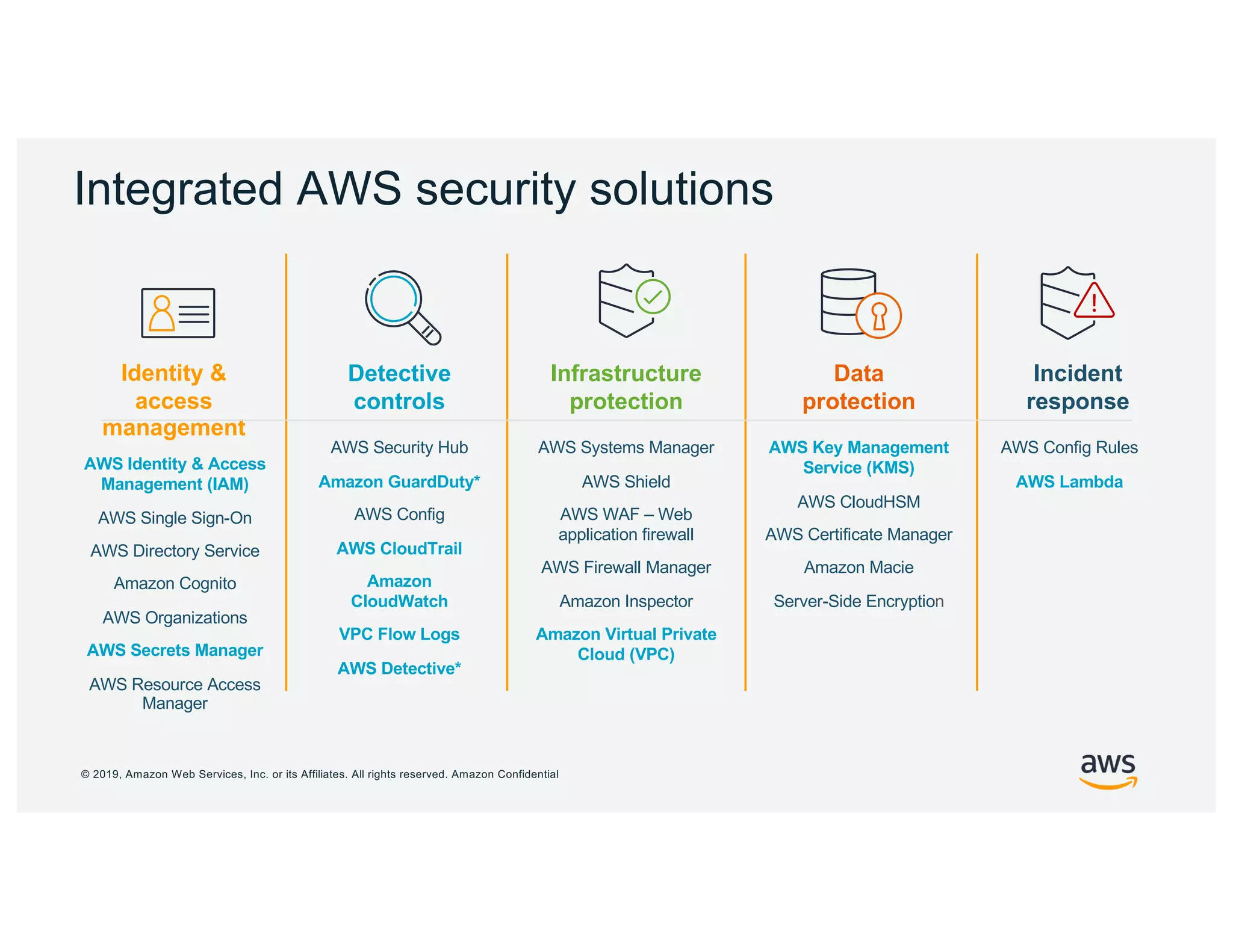
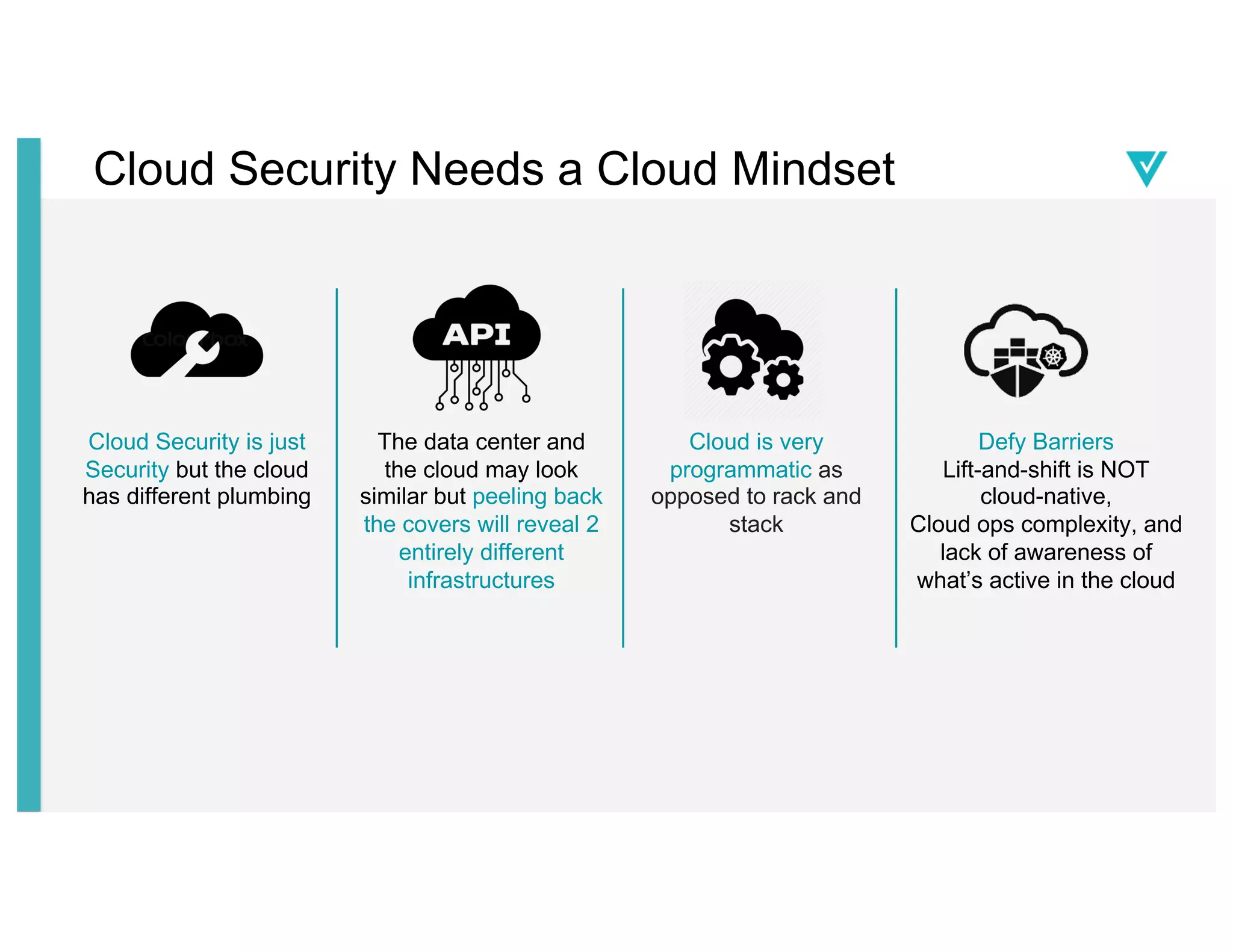
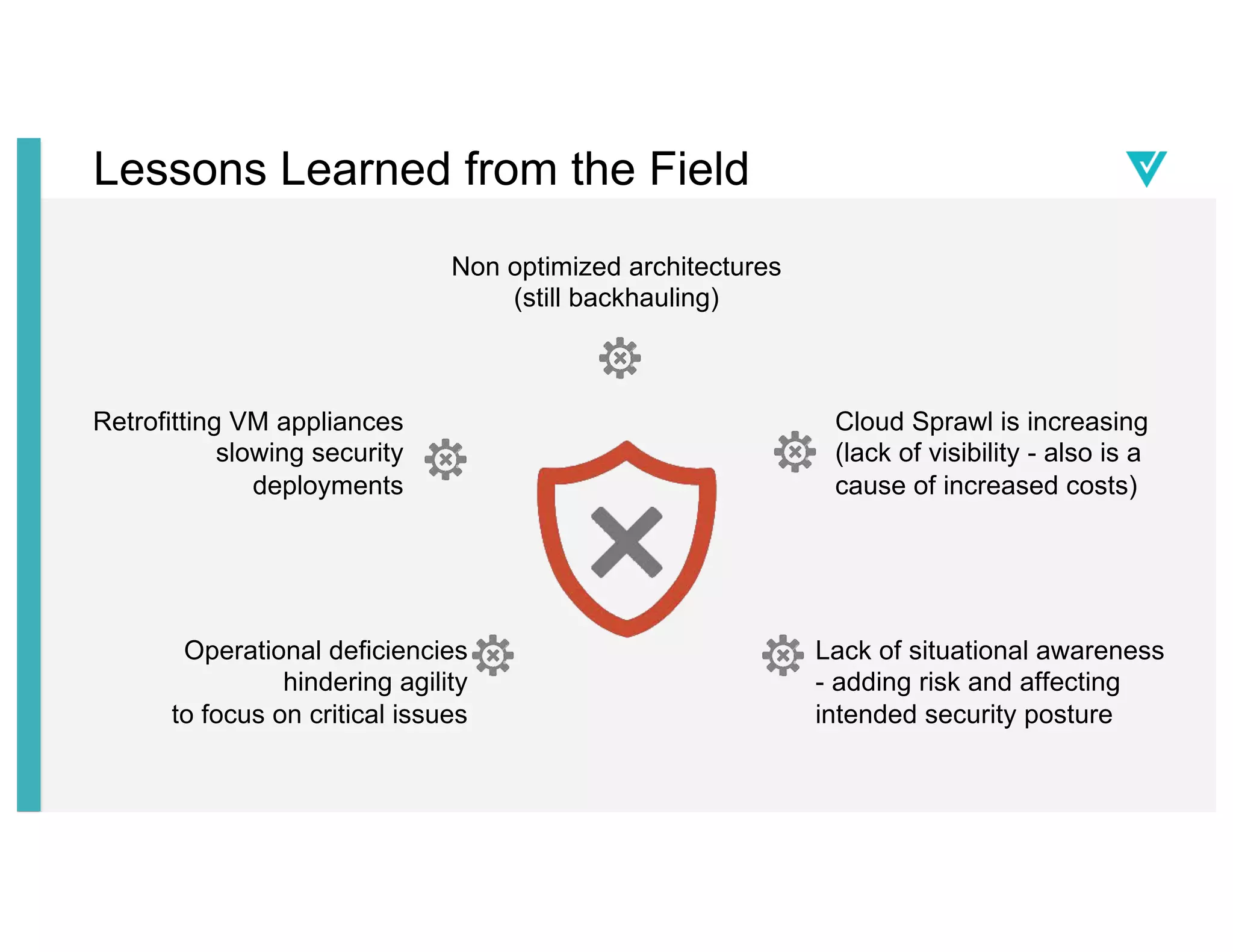
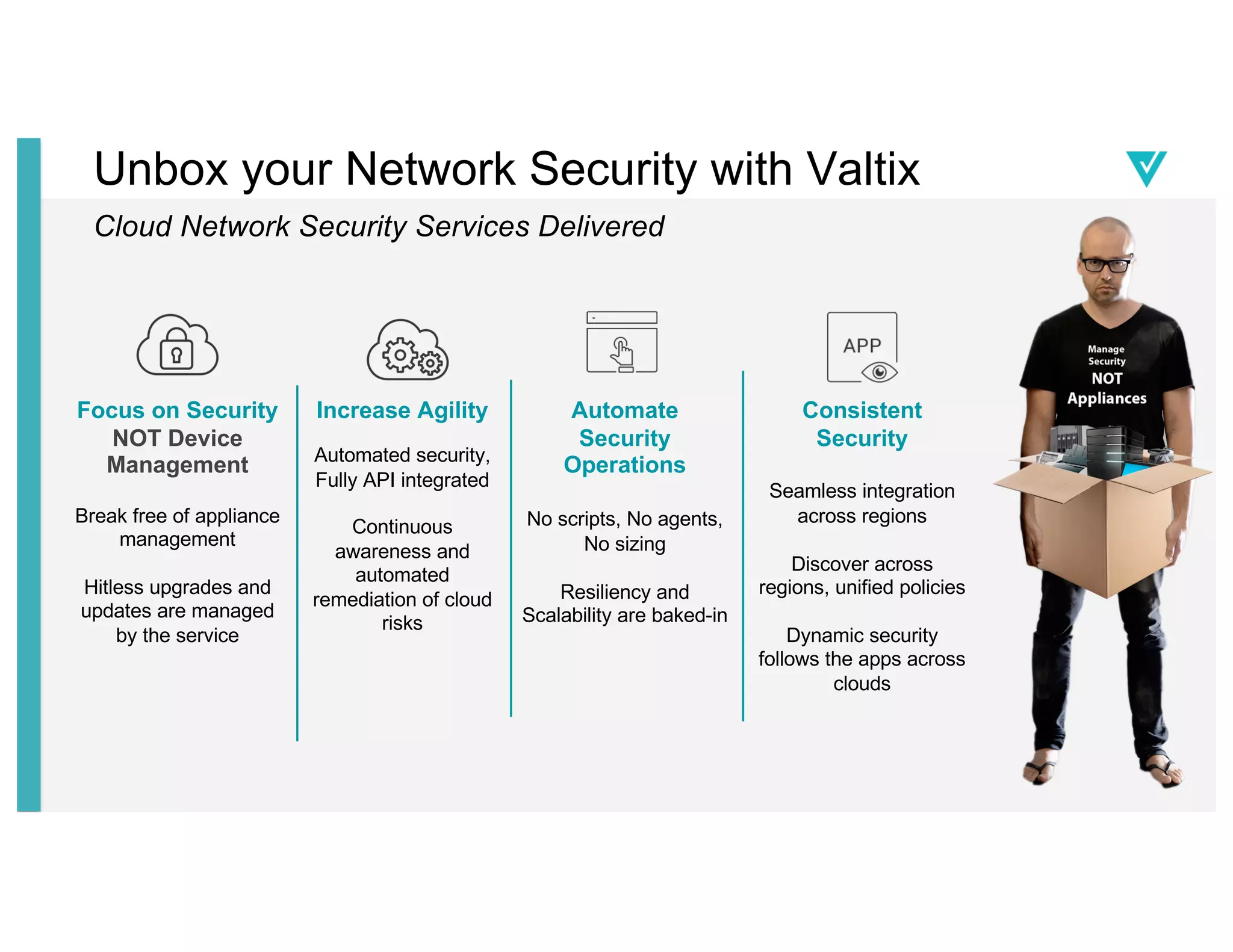
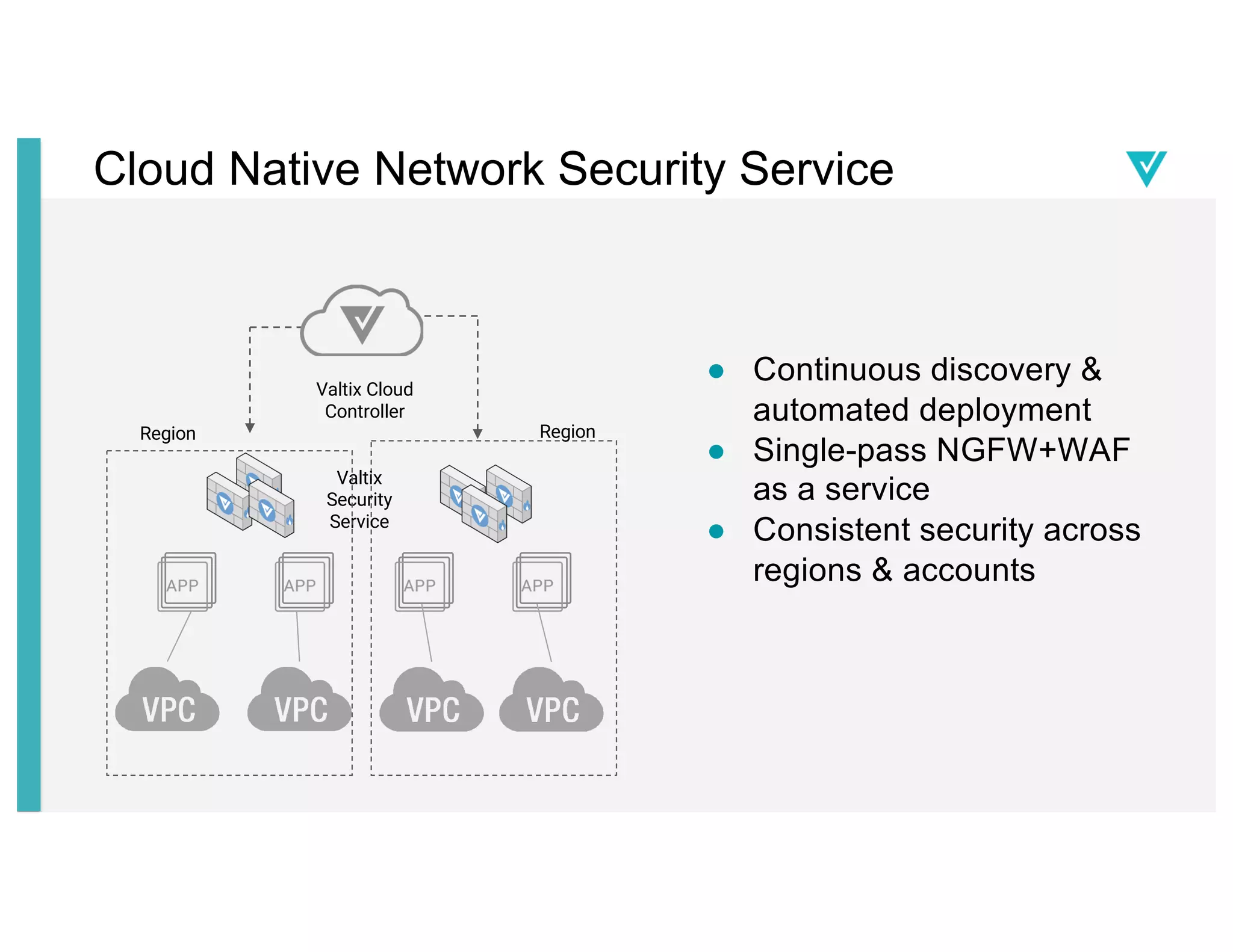
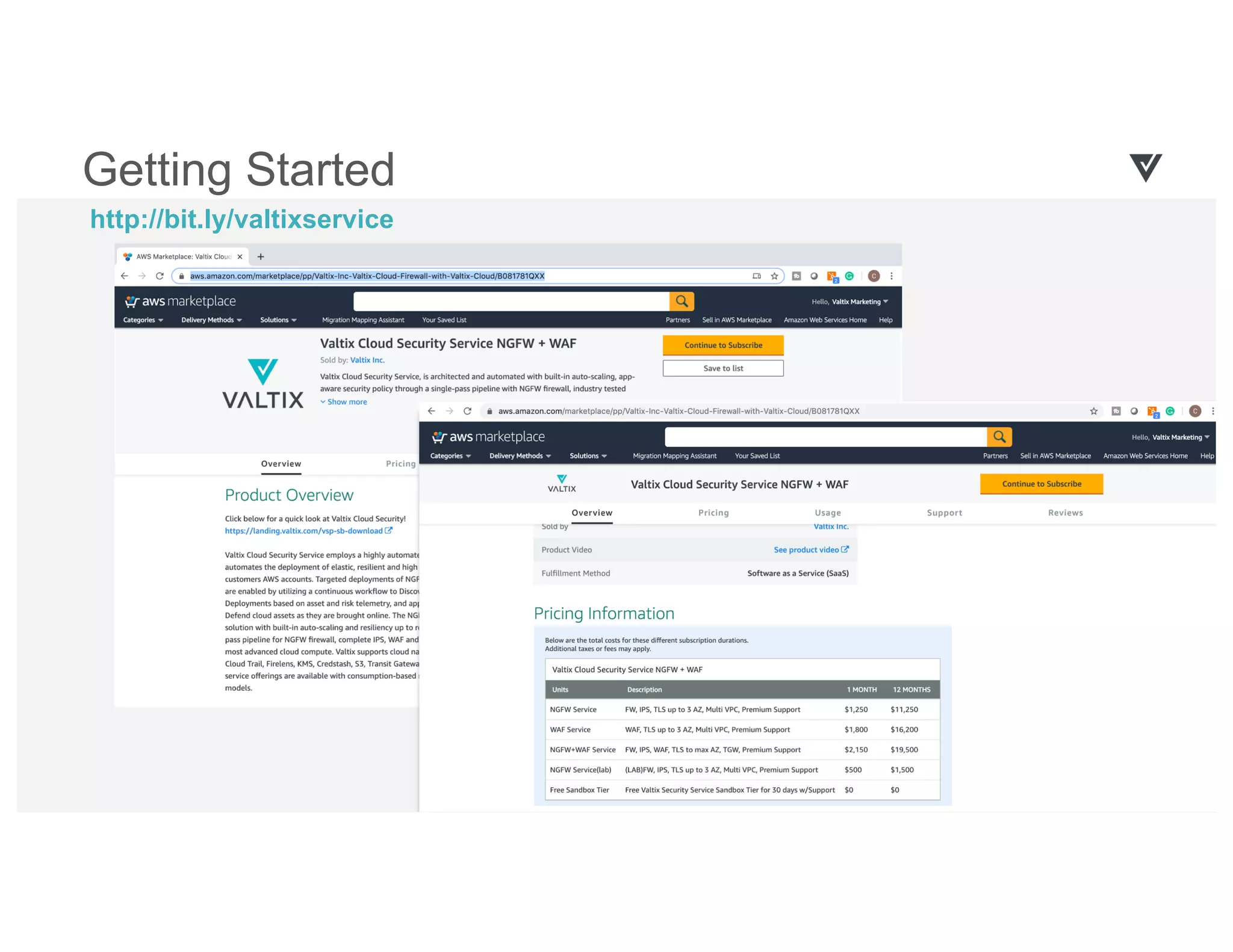
The document discusses cloud network security trends and practices as presented in a webinar led by Richard Stiennon and other experts from Amazon Web Services. It emphasizes the evolution of security models with digital transformation in cloud environments, the need for automation and visibility, and the unique challenges posed by cloud infrastructure. Key takeaways include the importance of adopting cloud-native security solutions and the benefits of using AWS services for comprehensive security management.