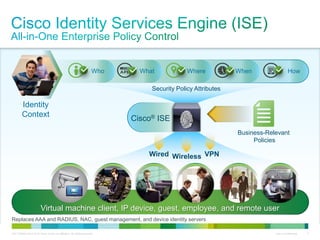
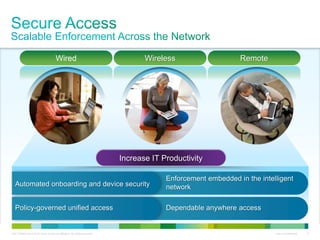
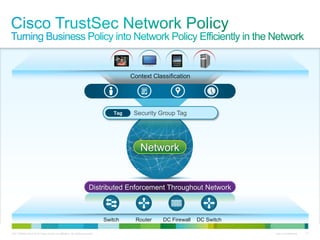
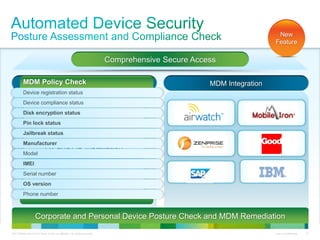
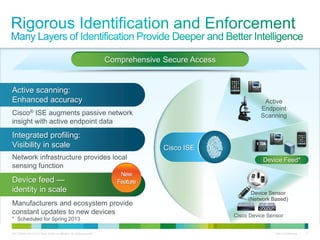
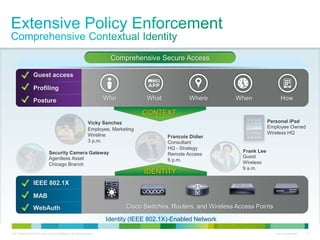
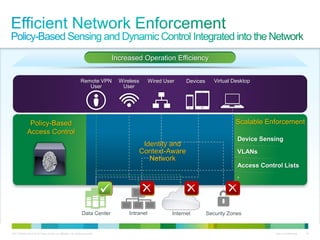
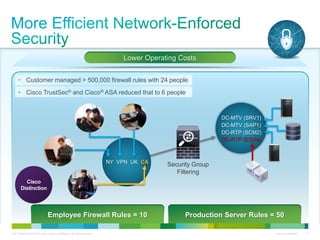
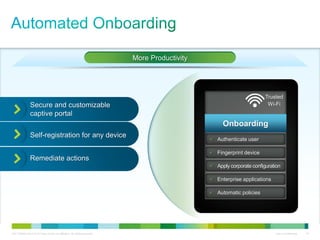
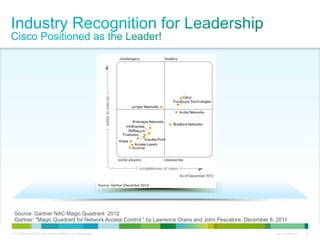
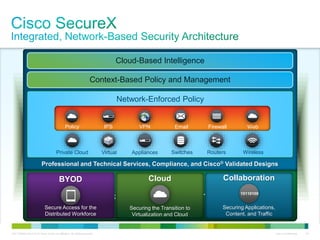
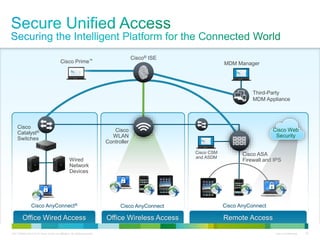
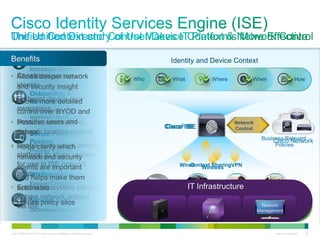
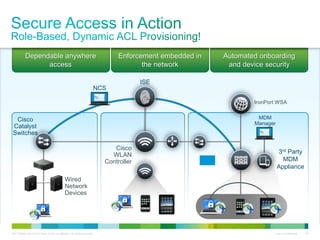
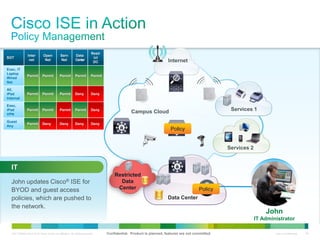
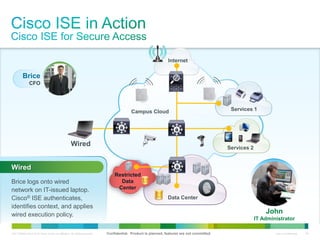
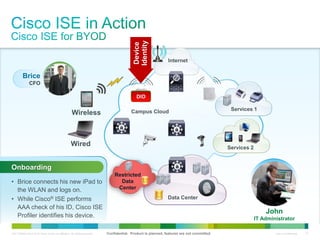
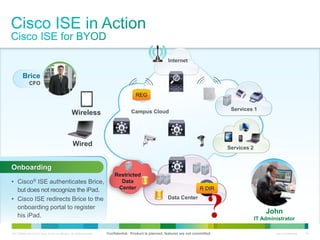
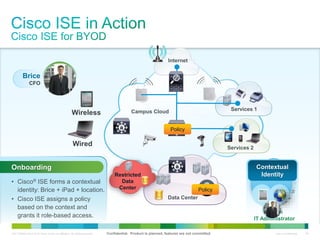
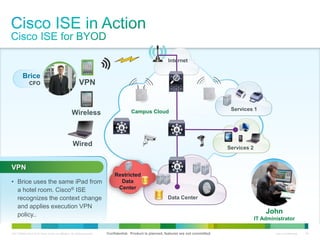
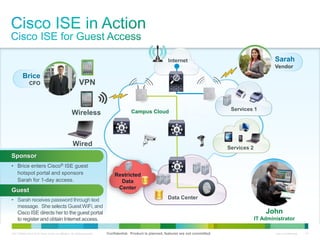
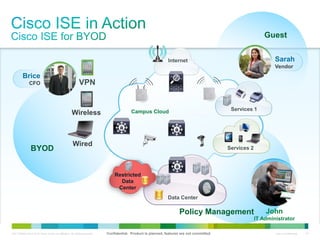
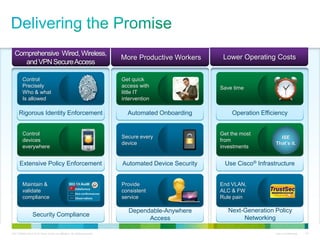
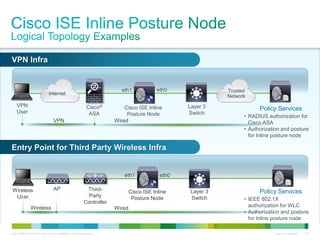
Cisco ISE provides comprehensive secure access through device profiling, posture assessment, and contextual identity to apply appropriate network access policies. It centrally manages policy enforcement on wired, wireless and VPN networks to increase security, productivity and operational efficiency. Cisco ISE automates user onboarding and ensures compliant devices receive network access while improperly postured devices are remediated.