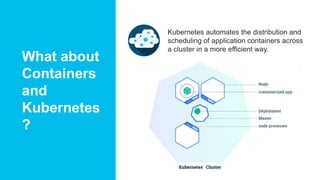
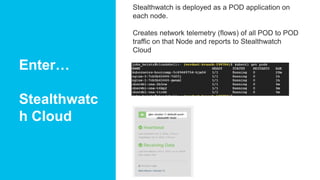
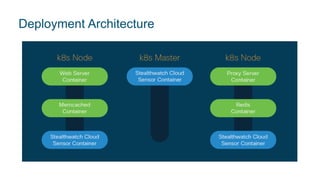
Jeff Moncrief discusses how Stealthwatch Cloud provides visibility, threat identification, and network compliance for Kubernetes environments. Stealthwatch is deployed as a POD application on each node to create network telemetry of all POD to POD traffic and report it to Stealthwatch Cloud, giving complete visibility into traffic in the Kubernetes cluster. The solution deploys as a Pod and integrates with the node-level network layer to provide visibility, baselining, and anomaly detection into container and pod communications.