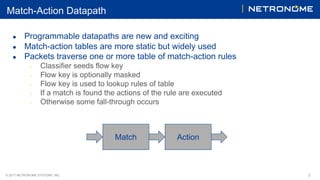
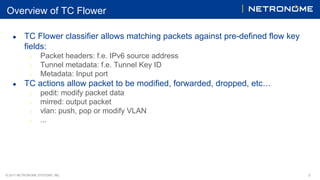
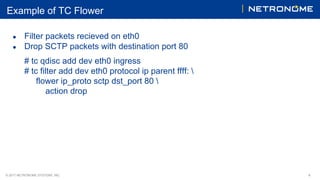
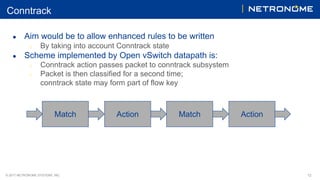
The document discusses the 'tc flower' classifier, which enables packet matching against predefined flow key fields and includes various actions for packet handling. It highlights the motivations for hardware offload to enhance throughput and CPU efficiency, as well as the history of such offloads in the Linux kernel. Examples of configuring hardware offload policies and using tc flower are provided, showcasing its functionality and enhancements with additional match capabilities.