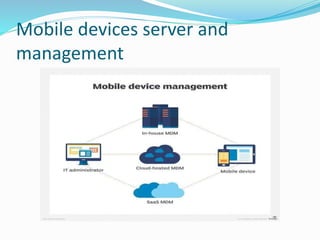
The document discusses various topics related to data synchronization in mobile computing systems. It defines data synchronization as maintaining availability and consistency of data across distributed systems. It describes different types of synchronization including two-way synchronization between devices, server-alerted synchronization, one-way server-initiated synchronization, and client-initiated refresh synchronization. It also discusses synchronization software, protocols, mobile device servers, management, file systems, and security considerations.