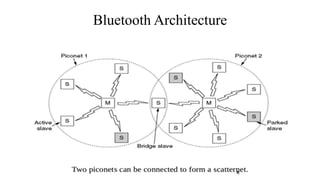
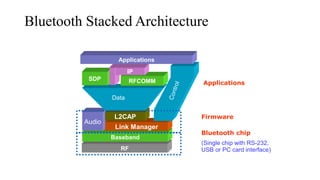
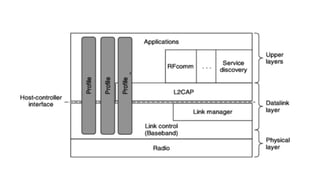
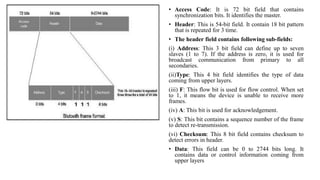
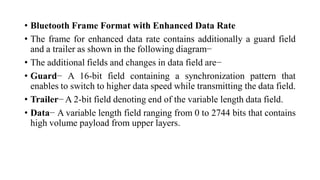
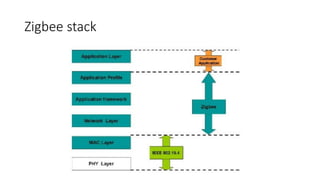
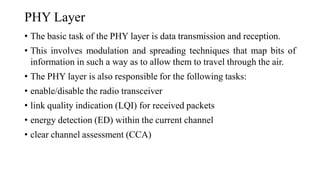
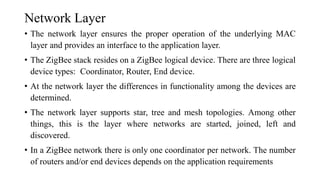
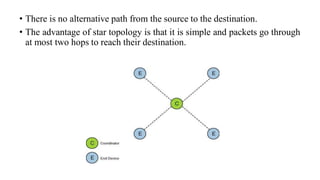
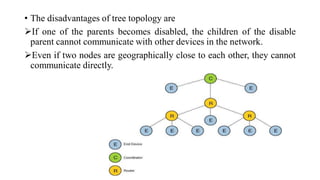
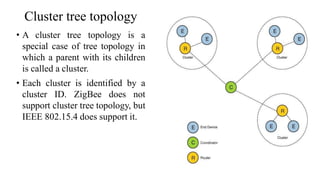
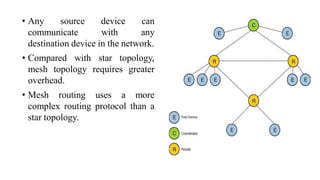
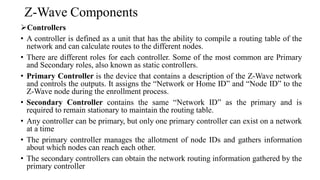
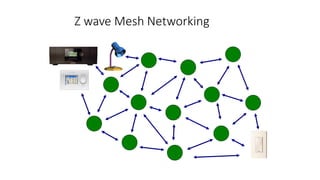
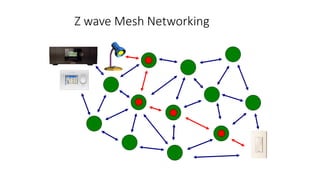
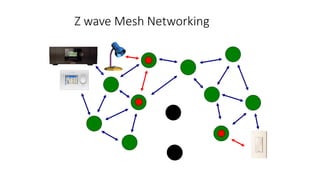
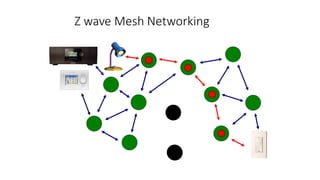
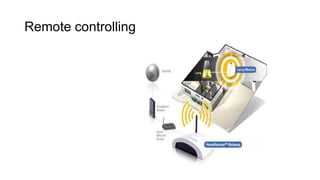
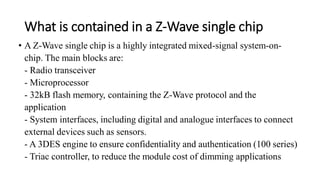
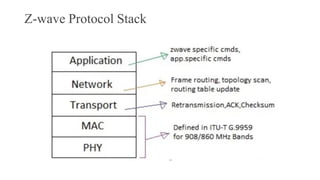
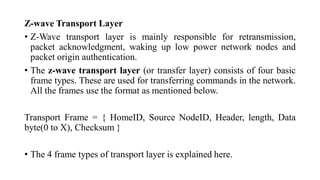
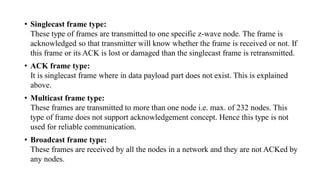
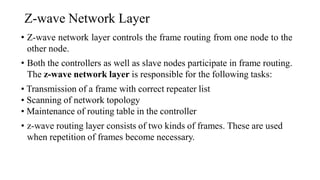
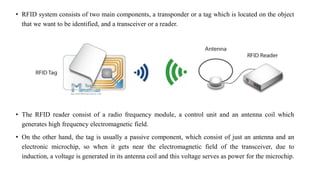
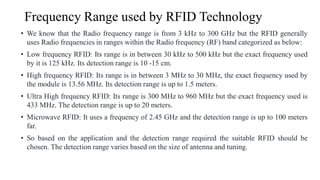
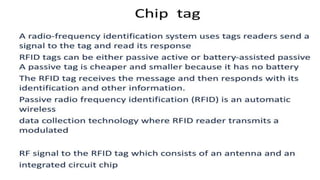
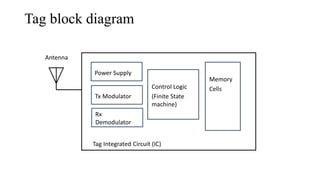
This document summarizes Bluetooth technology and its architecture. It discusses how Bluetooth enables wireless communication between electronic devices through short-range ad hoc networks called piconets. A piconet can have up to 8 devices connected to a single master device within a 10 meter range. Multiple piconets can be combined to form a scatternet, allowing devices to communicate across piconets. The document then describes the seven layers of the Bluetooth architecture and protocol stack, including the radio layer, baseband layer, link manager protocol, host controller interface, logical link control and adaptation protocol, RFCOMM, and service discovery protocol.