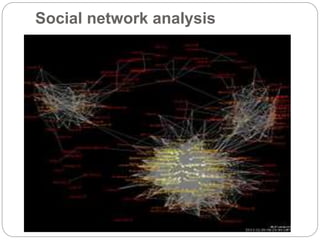
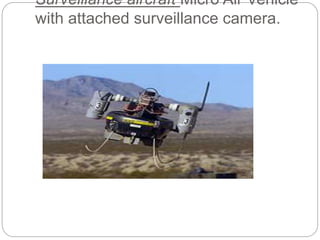
Surveillance involves monitoring behavior or activities to influence, manage or protect people. It can involve observation from a distance using electronic equipment like CCTV cameras or intercepting electronic communications. There are many types of surveillance including computer, phone, CCTV, social media analysis, biometrics, aerial, data mining and human operatives. Surveillance is used by governments for security purposes and criminal groups to plan crimes. New technologies like facial recognition, GPS tracking and drones enable additional forms of surveillance.