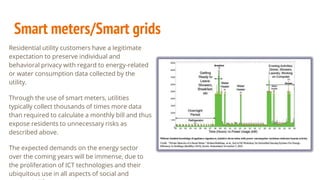
Surveillance technologies can be used to monitor individuals and groups. Some key surveillance technologies discussed in the document include: automated license plate readers, body cameras, CCTV cameras, cell-site simulators, drones, facial recognition software, social media monitoring software, smart meters/grids, and stalkerware monitoring programs. Many of these technologies raise privacy and civil liberties concerns, and some have been shown to disproportionately target or misidentify certain groups.












![Biometric surveillance technology
The U.S. military has used iris scanning
devices to identify detainees in Iraq and
Afghanistan.
The New York City Police Department was
among the first police departments to begin
using iris recognition.
On June 25, 2019, the U.S. Department of
Homeland Security (DHS) and ICE released a
Privacy Impact Assessment (PIA) on Rapid
DNA Operational Use [.pdf], stating that:
...Rapid DNA testing to establish a biological
parent-child relationship can be conducted in
approximately 90 minutes without human
review, unless there is an inconclusive result.
https://www.eff.org/deeplinks/2019/08/ices-rapid-dna-testing-
migrants-border-yet-another-iteration-family-separation](https://image.slidesharecdn.com/surveillancetechnologiesaprimer-200604160948/85/Surveillance-technologies-a-primer-16-320.jpg)