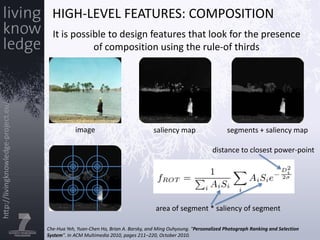
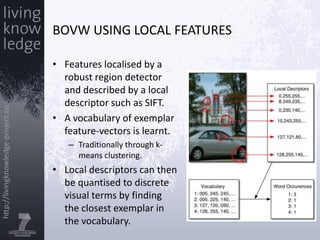
This document provides an introduction to extracting information from images. It discusses how images are represented digitally in computers and various techniques for extracting features from images, including lower-level features like color histograms and higher-level features like faces. Examples are given of feature extraction algorithms for faces and image composition. The document also discusses representing images using "bags of visual words" modeled after text analysis and introduces two open-source tools, OpenIMAJ and ImageTerrier, for image analysis.