Stack Frame Protection
•
0 likes•508 views
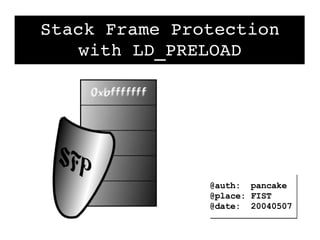
Stack Frame Protection with LD_PRELOAD [1] Buffer overflows are caused by exploiting the stack frame, which stores local variable and return pointer information. Methods to protect the stack frame include compiler patches, runtime security using ptrace, and library-based security loaded with LD_PRELOAD. [2] The author created a library called LibSFP that can be loaded with LD_PRELOAD to securely replace vulnerable functions like strcpy and prevent buffer overflows. It works by measuring the current stack frame size and limiting calls to this size. [3] LibSFP stores a magic value in malloc chunk headers to distinguish global and chunked variables, and protects variables in the stack
Report
Share
Report
Share
Download to read offline
Recommended
Threads - Why Can't You Just Play Nicely With Your Memory?

Many Cores with Java, Session Three: Threads - Why Can't You Just Play Nicely With Your Memory? moves on to start to think about concurrent code on two core. Some fundemental strategies are introduced briefly - non-blocking and locking.
Concurrent/ parallel programming

Concurrent programming allows running multiple tasks simultaneously through processes and threads. It describes running tasks in a time-shared manner on a single CPU core or truly in parallel across multiple CPU cores. Concurrent programs have different execution paths that run simultaneously. Concurrency means tasks happen within the same timeframe with dependencies, while parallelism means tasks happen simultaneously without dependencies. Concurrency challenges include shared resources, race conditions, deadlocks, priority inversions and starvation due to lack of proper synchronization techniques like mutexes and semaphores. In iOS, Apple provides threads, Grand Central Dispatch, and other synchronization tools to support concurrent programming.
Threads - Why Can't You Just Play Nicely With Your Memory_

The document discusses parallelism and multi-core processors. It notes that pre-emptive operating systems provide an illusion of parallel processes even on single-core hardware through context switching. When moving to multi-core, caches may be shared between cores on the same chip but not between chips. Communication is faster on-chip than off-chip. Shared memory requires software strategies like mutual exclusion and non-blocking algorithms to ensure reasonable behavior. Locks and memory barriers like synchronized in Java are used to prevent reading stale data. Compare-and-swap is an algorithm that allows non-blocking updates to shared memory locations.
LLJVM: LLVM bitcode to JVM bytecode

LLJVM is a library that translates LLVM bitcode to JVM bytecode. It was originally created to optimize Python UDFs in PySpark by compiling them to bitcode using Numba and then translating that to run on JVMs. However, LLJVM currently only supports a limited set of LLVM instructions and data types. It focuses on translating simple Numba-generated bitcode and providing runtime support functions. Translating more complex UDFs could improve PySpark performance significantly by avoiding serialization overhead and allowing whole-stage codegen.
Java variables and classes

Introduction to Java Variables and Classes. Primitive and Non Primitive Variables. Boolean, char, Short, Int, Long, Float, and double data type. Definition of Class and Objects with Examples. Various components of Class and Constructors
RPC in Smalltalk

RPC allows calling methods on remote objects by marshalling parameters and unmarshalling return values. There are many challenges to RPC including unreliable networks, latency, security, and changing topologies. Smalltalk supports RPC through mechanisms like distributed events, value/reference passing, and marshaling objects to formats like JSON to enable communication across networks and between systems. Developing distributed systems requires strategies for handling issues like passing large objects efficiently and updating interfaces when remote objects change.
Metasploit Module Development

This document provides an overview of Metasploit module development. It discusses the prerequisites, introduces Metasploit and its architecture including the file system and libraries. It explains the Metasploit object model and modules, covering exploits, payloads, encoders, the module tree, and staged vs stageless payloads. It also discusses digging into an existing module to understand its parameters and methods.
Parallel programming

This document provides an overview of parallel programming concepts like parallelism, threads, and concurrency. It discusses the importance of parallel programming given increasing numbers of processor cores. Key concepts covered include parallelism versus multi-processing, tasks and threads, the Java thread classes and methods, threading in Swing applications, and the new Java ForkJoin framework for parallel divide-and-conquer tasks. Examples are provided of using threads, Runnables, and SwingWorkers in Java programs.
Recommended
Threads - Why Can't You Just Play Nicely With Your Memory?

Many Cores with Java, Session Three: Threads - Why Can't You Just Play Nicely With Your Memory? moves on to start to think about concurrent code on two core. Some fundemental strategies are introduced briefly - non-blocking and locking.
Concurrent/ parallel programming

Concurrent programming allows running multiple tasks simultaneously through processes and threads. It describes running tasks in a time-shared manner on a single CPU core or truly in parallel across multiple CPU cores. Concurrent programs have different execution paths that run simultaneously. Concurrency means tasks happen within the same timeframe with dependencies, while parallelism means tasks happen simultaneously without dependencies. Concurrency challenges include shared resources, race conditions, deadlocks, priority inversions and starvation due to lack of proper synchronization techniques like mutexes and semaphores. In iOS, Apple provides threads, Grand Central Dispatch, and other synchronization tools to support concurrent programming.
Threads - Why Can't You Just Play Nicely With Your Memory_

The document discusses parallelism and multi-core processors. It notes that pre-emptive operating systems provide an illusion of parallel processes even on single-core hardware through context switching. When moving to multi-core, caches may be shared between cores on the same chip but not between chips. Communication is faster on-chip than off-chip. Shared memory requires software strategies like mutual exclusion and non-blocking algorithms to ensure reasonable behavior. Locks and memory barriers like synchronized in Java are used to prevent reading stale data. Compare-and-swap is an algorithm that allows non-blocking updates to shared memory locations.
LLJVM: LLVM bitcode to JVM bytecode

LLJVM is a library that translates LLVM bitcode to JVM bytecode. It was originally created to optimize Python UDFs in PySpark by compiling them to bitcode using Numba and then translating that to run on JVMs. However, LLJVM currently only supports a limited set of LLVM instructions and data types. It focuses on translating simple Numba-generated bitcode and providing runtime support functions. Translating more complex UDFs could improve PySpark performance significantly by avoiding serialization overhead and allowing whole-stage codegen.
Java variables and classes

Introduction to Java Variables and Classes. Primitive and Non Primitive Variables. Boolean, char, Short, Int, Long, Float, and double data type. Definition of Class and Objects with Examples. Various components of Class and Constructors
RPC in Smalltalk

RPC allows calling methods on remote objects by marshalling parameters and unmarshalling return values. There are many challenges to RPC including unreliable networks, latency, security, and changing topologies. Smalltalk supports RPC through mechanisms like distributed events, value/reference passing, and marshaling objects to formats like JSON to enable communication across networks and between systems. Developing distributed systems requires strategies for handling issues like passing large objects efficiently and updating interfaces when remote objects change.
Metasploit Module Development

This document provides an overview of Metasploit module development. It discusses the prerequisites, introduces Metasploit and its architecture including the file system and libraries. It explains the Metasploit object model and modules, covering exploits, payloads, encoders, the module tree, and staged vs stageless payloads. It also discusses digging into an existing module to understand its parameters and methods.
Parallel programming

This document provides an overview of parallel programming concepts like parallelism, threads, and concurrency. It discusses the importance of parallel programming given increasing numbers of processor cores. Key concepts covered include parallelism versus multi-processing, tasks and threads, the Java thread classes and methods, threading in Swing applications, and the new Java ForkJoin framework for parallel divide-and-conquer tasks. Examples are provided of using threads, Runnables, and SwingWorkers in Java programs.
Dennis Benkert & Matthias Lübken - Patterns in a containerized world? - code....

This slide deck introduces several container patterns for building modular and scalable container-based applications. It defines the concept of a modular container and describes pods as a group of closely related containers. It then outlines some common composite patterns including sidecars, ambassadors, adapters, and chains. The document is a work in progress seeking feedback to improve the defined patterns.
Embedded Recipes 2018 - Shared memory / telemetry - Yves-Marie Morgan

To exchange data between processes without the overhead of locking/syscall, shared memory can be used. libshdata/telemetry offers a lock free circular buffer with timestamped data chunks to handle some typical uses cases found in drones:
One process for flying stack, and one a more processes for video computing.
Video processing can access drone attitude precisely with the frame
Logging of all the telemetry exchanged in shared memory is easily written in a file or to a remote ground station
Also work in AMP configurations
IPv4aaS tutorial and hands-on

This document discusses various techniques for IPv6 transition and coexistence with IPv4, including:
- Dual-stack which allows simultaneous support of both IPv4 and IPv6.
- Tunnels which encapsulate IPv6 packets in IPv4 packets to provide IPv6 connectivity through IPv4 networks.
- Translation techniques like NAT64 which allow communication between IPv4-only and IPv6-only nodes.
what every web and app developer should know about multithreading

Multithreading allows executing multiple tasks simultaneously by splitting a program into multiple threads. It is useful for improving performance on web applications and when disk/network I/O is involved. However, threads introduce complexity as code and data may be accessed concurrently. Synchronization techniques like mutexes are needed to coordinate thread access and prevent race conditions from causing unpredictable behavior. Developers must carefully manage shared resources and avoid deadlocks when using multithreading.
Caffe + H2O - By Cyprien noel

This document proposes an in-memory file system to provide a unified abstraction for distributed computing across different devices and networks. It aims to simplify application integration and allow data to be directly placed on devices like GPUs. A prototype would use distributed mmap over Ethernet or InfiniBand to test the approach. The goal is to apply this to build a new distributed version of Caffe that could better leverage devices and frameworks like H2O through simplified pipelines rather than separate integrations.
NUMA and Java Databases

Talk given on state of NUMA with Java databases such as Cassandra and how it can improved / ameliorated, and compared with traditional storage engines.
Lecture2

1. The basic components of a parallel computer are processors, memory, and an interconnect network that connects the processors and memory.
2. Key processor terms include RISC, pipelining, and superscalar, which refer to instruction processing techniques. The network interconnect is characterized by latency, bandwidth, and topology.
3. Memory terms include cache, which sits between the CPU and main memory, as well as instruction cache, data cache, secondary cache, and translation lookaside buffer. Caches provide faster access to frequently used data and instructions.
Stefan Richter - Writing simple, readable and robust code: Examples in Java, ...

Stefan Richter gave a presentation on writing simple, readable, and robust code using examples in Java, Clojure, and Go. He discussed his programming experience and showed how Martin Fowler used Java to parse a fixed-length file format into objects. Richter then demonstrated how the same task could be accomplished more concisely in Common Lisp and Clojure using macros to define domain-specific languages. He argued that macros are a powerful feature of Lisp-like languages.
An End to Order (many cores with java, session two)

Session Two of Many Cores with Java, looking at parallelism within a single modern core. Discusses the links with
Bloc: a Modern Core for Highly Dynamic Graphics 

Title: Bloc: a Modern Core for Highly Dynamic Graphics
First Name: Stephane
Last Name: Ducasse
Type: Talk
Abstract: Bloc is the new generation core for Pharo graphics. Bloc is a complete rewrite from scratch of core classes and logic of Morphic. Bloc is developed by A. Plantec since a couple of years, it is the result of several iterations and based on the experience accumulated by Alain while designing Miro and Miro2 several years ago. Bloc is the basis for Brick the new widget sets developed by the University of Bern. In this presentation we will show the essence of the design of Bloc.
Bio: Stephane is directeur de recherche at Inria. He has more than 16 years of experience in software maintenance. He leads the RMoD (http://rmod.lille.inria.fr) team. He is expert in two domains: object-oriented language design and reengineering. He worked on traits, composable groups of methods, and this work got some impact. Traits have been introduced in Pharo, Perl, PHP and under a variant into Scala, Fortress of SUN Microsystems. He is also expert on software quality, program understanding, program visualizations, reengineering and metamodeling. He is one of the developer of Moose, an open-source software analysis platform http://www.moosetechnology.org/. He created http://www.synectique.eu/ a company building dedicated tools for advanced software analysis.
Pthread

This document provides an introduction to POSIX threads (Pthreads) programming. It discusses what threads are, how they differ from processes, and how Pthreads provide a standardized threading interface for UNIX systems. The key benefits of Pthreads for parallel programming are improved performance from overlapping CPU and I/O work and priority-based scheduling. Pthreads are well-suited for applications that can break work into independent tasks or respond to asynchronous events. The document outlines common threading models and emphasizes that programmers are responsible for synchronizing access to shared memory in multithreaded programs.
Java one2015 - Work With Hundreds of Hot Terabytes in JVMs

Presentation Summary: By leveraging on memory mapped files, the Chronicle Engine supports large maps that easily can exceed the size of your server’s RAM, thus allowing application developers to create huge JVM:s where data can be obtained quickly and with predictable latency. The Chronicle Engine can be synchronized with an underlying database using Speedment so that your in-memory maps will be “alive” and change whenever data changes in the underlying database. Speedment can also automatically derive domain models directly from the database so that you can start using the solution very quickly. Because the Java Maps are mapped onto files, the maps can also be shared instantly between several JVM:s and when you restart a JVM, it may start very quickly without having to reload data from the underlying database. The mapped files can be hundreds of terabytes which has been done in real world deployment cases.
Multithreading

The document discusses multithreading and how it can be used to exploit thread-level parallelism (TLP) in processors designed for instruction-level parallelism (ILP). There are two main approaches for multithreading - fine-grained and coarse-grained. Fine-grained switches threads every instruction while coarse-grained switches on long stalls. Simultaneous multithreading (SMT) allows a processor to issue instructions from multiple threads in the same cycle by treating instructions from different threads as independent. This converts TLP into additional ILP to better utilize the resources of superscalar and multicore processors.
Os

The document discusses threads in OCaml and their implementations. There are two implementations of threads available in OCaml - system threads which are built on operating system threads, and VM-level threads which perform time-sharing at the virtual machine level without using OS threads. While VM-level threads do not take advantage of multiple processors, they can be easier to program with than system threads for some applications.
Thread

Threads are lightweight processes that improve application performance through parallelism. Each thread has its own program counter and stack but shares other resources like memory with other threads in a process. Using threads provides advantages like lower overhead context switching compared to processes and allows parallel execution on multi-core systems. There are two types of threads - user level threads managed by libraries and kernel level threads supported by the OS kernel. Threads have a life cycle that includes states like new, ready, running, blocked, and terminated.
Userspace RCU library : what linear multiprocessor scalability means for your...

RCU is well-known at the kernel-level for providing a way to synchronize shared data structures in read-often, update-rarely scenarios.
The development of a RCU library at the userspace application level has been mainly driven by the need for efficient synchronization of userspace tracing control data structures.
IBM kindly agreed to allow distribution of RCU-related code in a LGPL library, which makes it available for everyone to use. This can have large impact on the design of highly scalable applications performing caching of frequent requests, like domain name servers, proxy and web servers.
This presentation will discuss about the class of applications which could benefit from using the userspace RCU library.
The userspace RCU library is available under the LGPL license at http://www.lttng.org/urcu .
Memcached And MySQL

Memcached is a high performance, distributed memory object caching system that stores data and objects in memory for fast access by applications. It uses a simple text-based protocol and handles hashing and serialization of objects. Memcached works by having applications like PHP first check memcached for cached objects, and if not found, retrieve the object from the database and store it in memcached for future requests.
Unba.se – San Diego Rust – march 2017 (abridged)

Daniel Norman presented his project unba.se, a Rust-powered distributed causal computing system. The project is still young with some functionality working intermittently. The code structure facilitates transport between slabs (data containers), with memos (immutable operations) transmitted between slabs. Contexts convert raw data into observations while enforcing consistency, and subjects represent data topics like records. The plan is to implement more functionality, determine how unba.se differs from IPFS, publish papers, and develop apps to demonstrate the system. Rust contributors are welcomed to help with the open source project.
Building Topology in NS3

This document discusses building a point-to-point topology simulation in NS-3. It describes:
1) Creating nodes using the Node class and NodeContainer helper.
2) Attaching NetDevices and channels using helpers like PointToPointHelper.
3) Installing the internet protocol stack on nodes with InternetStackHelper.
4) Assigning IP addresses to nodes with Ipv4AddressHelper.
5) Running applications like UdpEchoServer and UdpEchoClient on nodes using helpers.
6) Starting the simulation and destroying it after completion.
Type safe, versioned, and rewindable stream processing with Apache {Avro, K...

This document summarizes a talk on using Apache Kafka and Avro for stream processing at Mate1. It discusses:
1. How Mate1 was using message queues before to address latency and scalability issues, but wanted improvements in type safety, versioning, and being rewindable.
2. How they used Apache Avro for serialization to gain type safety when producing and consuming from Kafka topics.
3. How they developed a simple data format and integrated an Avro schema repository to allow for versioned schemas and backwards compatibility when schemas change.
4. How the integration allows for rewinding by mapping offsets to points in time, and rebuilding state after crashes by reprocessing data from a previous
The Stack Frame

The call stack is a data structure that stores information about active subroutines in a computer program. It keeps track of the point to which each subroutine should return control when finished. Subroutines can call other subroutines, resulting in information stacking up on the call stack. The call stack is composed of stack frames containing state information for each subroutine. Debuggers like GDB allow viewing the call stack to see how the program arrived at its current state.
How Functions Work

A function is a reusable block of code that can be called from different parts of a program. Functions accept parameters as input and may return a value. When a function is called, its parameters and local variables are stored on the stack. Each function call creates a stack frame that contains its parameters, local variables, and return address. This allows functions to maintain separate variable scopes while sharing the call stack.
More Related Content
What's hot
Dennis Benkert & Matthias Lübken - Patterns in a containerized world? - code....

This slide deck introduces several container patterns for building modular and scalable container-based applications. It defines the concept of a modular container and describes pods as a group of closely related containers. It then outlines some common composite patterns including sidecars, ambassadors, adapters, and chains. The document is a work in progress seeking feedback to improve the defined patterns.
Embedded Recipes 2018 - Shared memory / telemetry - Yves-Marie Morgan

To exchange data between processes without the overhead of locking/syscall, shared memory can be used. libshdata/telemetry offers a lock free circular buffer with timestamped data chunks to handle some typical uses cases found in drones:
One process for flying stack, and one a more processes for video computing.
Video processing can access drone attitude precisely with the frame
Logging of all the telemetry exchanged in shared memory is easily written in a file or to a remote ground station
Also work in AMP configurations
IPv4aaS tutorial and hands-on

This document discusses various techniques for IPv6 transition and coexistence with IPv4, including:
- Dual-stack which allows simultaneous support of both IPv4 and IPv6.
- Tunnels which encapsulate IPv6 packets in IPv4 packets to provide IPv6 connectivity through IPv4 networks.
- Translation techniques like NAT64 which allow communication between IPv4-only and IPv6-only nodes.
what every web and app developer should know about multithreading

Multithreading allows executing multiple tasks simultaneously by splitting a program into multiple threads. It is useful for improving performance on web applications and when disk/network I/O is involved. However, threads introduce complexity as code and data may be accessed concurrently. Synchronization techniques like mutexes are needed to coordinate thread access and prevent race conditions from causing unpredictable behavior. Developers must carefully manage shared resources and avoid deadlocks when using multithreading.
Caffe + H2O - By Cyprien noel

This document proposes an in-memory file system to provide a unified abstraction for distributed computing across different devices and networks. It aims to simplify application integration and allow data to be directly placed on devices like GPUs. A prototype would use distributed mmap over Ethernet or InfiniBand to test the approach. The goal is to apply this to build a new distributed version of Caffe that could better leverage devices and frameworks like H2O through simplified pipelines rather than separate integrations.
NUMA and Java Databases

Talk given on state of NUMA with Java databases such as Cassandra and how it can improved / ameliorated, and compared with traditional storage engines.
Lecture2

1. The basic components of a parallel computer are processors, memory, and an interconnect network that connects the processors and memory.
2. Key processor terms include RISC, pipelining, and superscalar, which refer to instruction processing techniques. The network interconnect is characterized by latency, bandwidth, and topology.
3. Memory terms include cache, which sits between the CPU and main memory, as well as instruction cache, data cache, secondary cache, and translation lookaside buffer. Caches provide faster access to frequently used data and instructions.
Stefan Richter - Writing simple, readable and robust code: Examples in Java, ...

Stefan Richter gave a presentation on writing simple, readable, and robust code using examples in Java, Clojure, and Go. He discussed his programming experience and showed how Martin Fowler used Java to parse a fixed-length file format into objects. Richter then demonstrated how the same task could be accomplished more concisely in Common Lisp and Clojure using macros to define domain-specific languages. He argued that macros are a powerful feature of Lisp-like languages.
An End to Order (many cores with java, session two)

Session Two of Many Cores with Java, looking at parallelism within a single modern core. Discusses the links with
Bloc: a Modern Core for Highly Dynamic Graphics 

Title: Bloc: a Modern Core for Highly Dynamic Graphics
First Name: Stephane
Last Name: Ducasse
Type: Talk
Abstract: Bloc is the new generation core for Pharo graphics. Bloc is a complete rewrite from scratch of core classes and logic of Morphic. Bloc is developed by A. Plantec since a couple of years, it is the result of several iterations and based on the experience accumulated by Alain while designing Miro and Miro2 several years ago. Bloc is the basis for Brick the new widget sets developed by the University of Bern. In this presentation we will show the essence of the design of Bloc.
Bio: Stephane is directeur de recherche at Inria. He has more than 16 years of experience in software maintenance. He leads the RMoD (http://rmod.lille.inria.fr) team. He is expert in two domains: object-oriented language design and reengineering. He worked on traits, composable groups of methods, and this work got some impact. Traits have been introduced in Pharo, Perl, PHP and under a variant into Scala, Fortress of SUN Microsystems. He is also expert on software quality, program understanding, program visualizations, reengineering and metamodeling. He is one of the developer of Moose, an open-source software analysis platform http://www.moosetechnology.org/. He created http://www.synectique.eu/ a company building dedicated tools for advanced software analysis.
Pthread

This document provides an introduction to POSIX threads (Pthreads) programming. It discusses what threads are, how they differ from processes, and how Pthreads provide a standardized threading interface for UNIX systems. The key benefits of Pthreads for parallel programming are improved performance from overlapping CPU and I/O work and priority-based scheduling. Pthreads are well-suited for applications that can break work into independent tasks or respond to asynchronous events. The document outlines common threading models and emphasizes that programmers are responsible for synchronizing access to shared memory in multithreaded programs.
Java one2015 - Work With Hundreds of Hot Terabytes in JVMs

Presentation Summary: By leveraging on memory mapped files, the Chronicle Engine supports large maps that easily can exceed the size of your server’s RAM, thus allowing application developers to create huge JVM:s where data can be obtained quickly and with predictable latency. The Chronicle Engine can be synchronized with an underlying database using Speedment so that your in-memory maps will be “alive” and change whenever data changes in the underlying database. Speedment can also automatically derive domain models directly from the database so that you can start using the solution very quickly. Because the Java Maps are mapped onto files, the maps can also be shared instantly between several JVM:s and when you restart a JVM, it may start very quickly without having to reload data from the underlying database. The mapped files can be hundreds of terabytes which has been done in real world deployment cases.
Multithreading

The document discusses multithreading and how it can be used to exploit thread-level parallelism (TLP) in processors designed for instruction-level parallelism (ILP). There are two main approaches for multithreading - fine-grained and coarse-grained. Fine-grained switches threads every instruction while coarse-grained switches on long stalls. Simultaneous multithreading (SMT) allows a processor to issue instructions from multiple threads in the same cycle by treating instructions from different threads as independent. This converts TLP into additional ILP to better utilize the resources of superscalar and multicore processors.
Os

The document discusses threads in OCaml and their implementations. There are two implementations of threads available in OCaml - system threads which are built on operating system threads, and VM-level threads which perform time-sharing at the virtual machine level without using OS threads. While VM-level threads do not take advantage of multiple processors, they can be easier to program with than system threads for some applications.
Thread

Threads are lightweight processes that improve application performance through parallelism. Each thread has its own program counter and stack but shares other resources like memory with other threads in a process. Using threads provides advantages like lower overhead context switching compared to processes and allows parallel execution on multi-core systems. There are two types of threads - user level threads managed by libraries and kernel level threads supported by the OS kernel. Threads have a life cycle that includes states like new, ready, running, blocked, and terminated.
Userspace RCU library : what linear multiprocessor scalability means for your...

RCU is well-known at the kernel-level for providing a way to synchronize shared data structures in read-often, update-rarely scenarios.
The development of a RCU library at the userspace application level has been mainly driven by the need for efficient synchronization of userspace tracing control data structures.
IBM kindly agreed to allow distribution of RCU-related code in a LGPL library, which makes it available for everyone to use. This can have large impact on the design of highly scalable applications performing caching of frequent requests, like domain name servers, proxy and web servers.
This presentation will discuss about the class of applications which could benefit from using the userspace RCU library.
The userspace RCU library is available under the LGPL license at http://www.lttng.org/urcu .
Memcached And MySQL

Memcached is a high performance, distributed memory object caching system that stores data and objects in memory for fast access by applications. It uses a simple text-based protocol and handles hashing and serialization of objects. Memcached works by having applications like PHP first check memcached for cached objects, and if not found, retrieve the object from the database and store it in memcached for future requests.
Unba.se – San Diego Rust – march 2017 (abridged)

Daniel Norman presented his project unba.se, a Rust-powered distributed causal computing system. The project is still young with some functionality working intermittently. The code structure facilitates transport between slabs (data containers), with memos (immutable operations) transmitted between slabs. Contexts convert raw data into observations while enforcing consistency, and subjects represent data topics like records. The plan is to implement more functionality, determine how unba.se differs from IPFS, publish papers, and develop apps to demonstrate the system. Rust contributors are welcomed to help with the open source project.
Building Topology in NS3

This document discusses building a point-to-point topology simulation in NS-3. It describes:
1) Creating nodes using the Node class and NodeContainer helper.
2) Attaching NetDevices and channels using helpers like PointToPointHelper.
3) Installing the internet protocol stack on nodes with InternetStackHelper.
4) Assigning IP addresses to nodes with Ipv4AddressHelper.
5) Running applications like UdpEchoServer and UdpEchoClient on nodes using helpers.
6) Starting the simulation and destroying it after completion.
Type safe, versioned, and rewindable stream processing with Apache {Avro, K...

This document summarizes a talk on using Apache Kafka and Avro for stream processing at Mate1. It discusses:
1. How Mate1 was using message queues before to address latency and scalability issues, but wanted improvements in type safety, versioning, and being rewindable.
2. How they used Apache Avro for serialization to gain type safety when producing and consuming from Kafka topics.
3. How they developed a simple data format and integrated an Avro schema repository to allow for versioned schemas and backwards compatibility when schemas change.
4. How the integration allows for rewinding by mapping offsets to points in time, and rebuilding state after crashes by reprocessing data from a previous
What's hot (20)
Dennis Benkert & Matthias Lübken - Patterns in a containerized world? - code....

Dennis Benkert & Matthias Lübken - Patterns in a containerized world? - code....
Embedded Recipes 2018 - Shared memory / telemetry - Yves-Marie Morgan

Embedded Recipes 2018 - Shared memory / telemetry - Yves-Marie Morgan
what every web and app developer should know about multithreading

what every web and app developer should know about multithreading
Stefan Richter - Writing simple, readable and robust code: Examples in Java, ...

Stefan Richter - Writing simple, readable and robust code: Examples in Java, ...
An End to Order (many cores with java, session two)

An End to Order (many cores with java, session two)
Java one2015 - Work With Hundreds of Hot Terabytes in JVMs

Java one2015 - Work With Hundreds of Hot Terabytes in JVMs
Userspace RCU library : what linear multiprocessor scalability means for your...

Userspace RCU library : what linear multiprocessor scalability means for your...
Type safe, versioned, and rewindable stream processing with Apache {Avro, K...

Type safe, versioned, and rewindable stream processing with Apache {Avro, K...
Viewers also liked
The Stack Frame

The call stack is a data structure that stores information about active subroutines in a computer program. It keeps track of the point to which each subroutine should return control when finished. Subroutines can call other subroutines, resulting in information stacking up on the call stack. The call stack is composed of stack frames containing state information for each subroutine. Debuggers like GDB allow viewing the call stack to see how the program arrived at its current state.
How Functions Work

A function is a reusable block of code that can be called from different parts of a program. Functions accept parameters as input and may return a value. When a function is called, its parameters and local variables are stored on the stack. Each function call creates a stack frame that contains its parameters, local variables, and return address. This allows functions to maintain separate variable scopes while sharing the call stack.
CILK/CILK++ and Reducers

The document discusses CILK and CILK++, parallel programming languages that allow spawning concurrent tasks. It covers the key language features like spawn and sync, provides examples of Fibonacci implementations, and describes the work stealing runtime system that dynamically schedules tasks across processors. The runtime uses a decentralized work stealing approach where idle processors steal tasks from other processors' task queues to balance workload.
Task based Programming with OmpSs and its Application

Charla de la Dra. Rosa M. Badia Sala del Barcelona Supercomputing Center impartida el 4 de Noviembre en la Facultad de Informática
[若渴計畫]64-bit Linux Return-Oriented Programming![[若渴計畫]64-bit Linux Return-Oriented Programming](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[若渴計畫]64-bit Linux Return-Oriented Programming](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
參考http://crypto.stanford.edu/~blynn/rop/ 學習了64-bit Linux Return-Oriented Programming,在這過程中看到一些linux command的用法和stack的知識學習.並與大家分享
Numbers and Values in Objective-C and C Programming

This document discusses different types of numbers used in programming including integers like char, short, int, long, and long long. It also covers floating point numbers like float and double. Additionally, it covers printf formatting, integer and floating point math operations, and the math library for trigonometric functions.
Authoring tools worksheet

The document discusses different concepts for organizing multimedia elements and events along a timeline, as icons, or as pages in a book or cards in a stack. It lists some authoring tools that use these concepts, including Flash, Director, Authorware, and Icon for timeline and icon concepts, and HyperCard, SuperCard, and Toolbook for book/card concepts.
Wk1to4

The document discusses several topics related to computer architecture and assembly language programming:
1. It describes the von Neumann architecture model and key components like the ALU, control unit, and memory.
2. It summarizes Moore's Law and how increasing transistor density has allowed for higher performance chips over time.
3. It provides an overview of some early Intel processors like the 8086 and techniques used to increase processor speed like pipelining.
4. It includes brief explanations of common assembly language concepts like registers, memory addressing, and arithmetic and logical instructions.
02 - Introduction to the cdecl ABI and the x86 stack

* Brief description of the x86 ASI and cdecl ABI
* Data and code segregation
* Into cdecl
* The stack frame
Python Yield

The document discusses yield in Python and how it allows functions to act as generators by using the yield keyword instead of return, enabling generator functions to control execution by yielding values and resuming at the point after each yield. It explains how generators are created and how yield allows suspending and resuming execution of generator functions to implement features like coroutines, trampolines to avoid recursion limits, and the with statement in Python.
2장. Runtime Data Areas

Java Performance Fundamental 세미나 교재입니다
2장은 JVM의 메모리 구조인 Runtime Data Areas에 대한 설명을 하고 있습니다. 크게는4개의 모듈로 나누어 지는 Runtime Data Areas를 부분 별로 자세히 다루고 있습니다. 그리고 나서 우리가 프로그램을 수행할 때 Runtime Data Areas에서는 어떻게 데이터들이 움직이는 지를 간단한 예제를 통해 알아보고자 합니다.
* Runtime Data Areas의 구조
* PC Register
* Java Virtual Machine Stacks
* Native Method Stack
* Method Area
* Java Heap
* Runtime Data Areas Simulation
Smashing The Stack

The document discusses stack-based buffer overflows. It explains that stack-based overflows can overwrite local variables, function pointers, or return addresses on the stack. Overwriting a return address allows an attacker to change the flow of execution to code of their choice, usually a shellcode-containing buffer. The document provides an example of a stack-based overflow overwriting a return address, which would cause execution to jump to the attacker's buffer after the function returns.
Functions in Objective-C and C Programming

Course Link: http://skl.sh/11kA0im
Website: http://iPhoneDev.tv
Learn about functions which allow you to organize your code into chunks. Functions allow you to delegate work between different blocks of code.
Introduction to Linux Exploit Development

The document provides an introduction to Linux exploit development. It discusses the speaker's background and certifications. It then covers compiling a simple "Hello World" program in C and examining the resulting executable file format and memory layout. The presentation examines the stack and how functions, arguments, and return addresses are managed using stack frames and instructions like PUSH, POP, CALL, and RET. It demonstrates the prologue and epilogue sections of a function that save and restore registers and stack pointers.
Exploit techniques and mitigation

This document discusses various exploit techniques such as stack overflow, heap overflow, and return oriented programming that leverage application vulnerabilities. It also covers mitigation techniques including stack protection, safeSEH, heap protection, data execution prevention, and address space layout randomization. The document recommends automated malware protection solutions that can protect against zero-day attacks as the most effective approach compared to anti-virus blacklists or sandboxing solutions.
Introduction to pointers and memory management in C

The document is an introduction to pointers and memory management in C. It discusses computer memory, how variables and function calls are implemented, and introduces pointers as a way to overcome limitations of passing arguments by value. It covers pointer arithmetic, arrays, and dynamic memory allocation using malloc and free. The goal is to help understand concepts and techniques while noting caveats.
Addressing 

This document discusses different addressing modes and instruction formats. It covers several addressing modes including immediate, direct, indirect, register, register indirect, displacement, stack, and relative addressing. It also discusses the instruction formats of different processors including PDP-8, PDP-10, PDP-11, VAX, Pentium, and PowerPC with details on opcode, operands, addressing modes, instruction length and allocation of bits.
Reversing & Malware Analysis Training Part 4 - Assembly Programming Basics

This presentation is part of our Reverse Engineering & Malware Analysis Training program.
For more details refer our Security Training page
http://securityxploded.com/security-training.php
Low Level Exploits

This document discusses various low-level exploits, beginning with creating shellcode by extracting opcodes from a compiled C program. It then covers stack-based buffer overflows, including return-to-stack exploits and return-to-libc. Next it discusses heap overflows using the unlink technique, integer overflows, and format string vulnerabilities. The document provides code examples and explanations of the techniques.
Viewers also liked (20)
Task based Programming with OmpSs and its Application

Task based Programming with OmpSs and its Application
Numbers and Values in Objective-C and C Programming

Numbers and Values in Objective-C and C Programming
02 - Introduction to the cdecl ABI and the x86 stack

02 - Introduction to the cdecl ABI and the x86 stack
Introduction to pointers and memory management in C

Introduction to pointers and memory management in C
Reversing & Malware Analysis Training Part 4 - Assembly Programming Basics

Reversing & Malware Analysis Training Part 4 - Assembly Programming Basics
Similar to Stack Frame Protection
Pune-Cocoa: Blocks and GCD

Blocks is a cool concept and is very much needed for performance improvements and responsiveness. GCD helps run blocks effortlessly by scheduling on a desired queue, priority and lots more.
gcdtmp

Grand Central Dispatch (GCD) was created by Apple to make it easier to write concurrent code for multi-core systems. It shifts thread and task management from apps to the operating system. Units of work are described as blocks of code, while queues organize blocks based on execution needs. GCD has a multi-core engine that assigns blocks from app queues to OS-managed threads, removing the need for apps to directly use threads. Blocks are lightweight anonymous functions that can capture state and be passed between queues and threads for asynchronous execution. Common queues include the main queue for UI updates and global queues for general-purpose work.
High-Performance Networking Using eBPF, XDP, and io_uring

Bryan McCoid discusses using eBPF, XDP, and io_uring for high performance networking. XDP allows programs to process packets in the kernel without loading modules. AF_XDP sockets use eBPF to route packets between kernel and userspace via ring buffers. McCoid is building a Rust runtime called Glommio to interface with these techniques. The runtime integrates with io_uring and allows multiple design patterns for receiving packets from AF_XDP sockets.
Quick introduction to Java Garbage Collector (JVM GC)

The document discusses the Java Virtual Machine (JVM) and garbage collection. It describes the JVM memory areas like the heap, stack, method area and PC registers. It explains garbage collection techniques like minor and major GC used for young and old generation memory. The document also discusses different garbage collectors like serial, parallel, CMS and G1 collectors and how they perform compaction to reduce heap fragmentation. Tools for monitoring heap usage like jconsole and Websphere resource analyzer are also mentioned.
Memory compiler tutorial – TSMC 40nm technology

This chapter contains information for memory compilers available in STDL80 cell library. These are
complete compilers that consist of various generators to satisfy the requirements of the circuit at hand. Each
of the final building block, the physical layout, will be implemented as a stand-alone, densely packed,
pitch-matched array. Using this complex layout generator and adopting state-of-the-art logic and circuit
design technique, these memory cells can realize extreme density and performance. In each layout
generator, we added an option which makes the aspect ratio of the physical layout selectable so that the
ASIC designers can choose the aspect ratio according to the convenience of the chip level layout.
Memory model

This document discusses memory ordering and synchronization in multithreaded programs. It begins with background on mutexes, semaphores, and their differences. It then discusses problems that can occur with locking-based synchronization methods like mutexes, such as deadlocks, priority inversion, and performance issues. Alternative lock-free programming techniques using atomic operations are presented as a way to synchronize access without locks. Finally, memory ordering, consistency models, barriers, and their implementations in compilers, Linux kernels, and ARM architectures are covered in detail.
Attack on the Core

Kernel vulnerabilities was commonly used to obtain admin privileges, and main rule was to stay in kernel as small time as possible! But nowdays even when you get admin / root then current operating systems are sometimes too restrictive. And that made kernel exploitation nice vector for installing to kernel mode!
In this talk we will examine steps from CPL3 to CPL0, including some nice tricks, and we end up with developing kernel mode drivers.
Advanced Arm Exploitation

1. The document outlines an agenda for a workshop on advanced ARM exploitation. The agenda includes introductions to memory corruption, buffer overflows, format string exploitation, and techniques for bypassing exploit mitigations like DEP using return-oriented programming (ROP).
2. Practical demonstrations are provided on topics like visualizing stack corruption from buffer overflows, overwriting the instruction pointer to hijack execution, injecting and executing shellcode payloads, reading and writing arbitrary memory with format strings, and creating ROP chains to bypass DEP.
3. The speakers are introduced as security researchers and instructors specializing in areas like exploit development, malware, rootkits, and reverse engineering. Attendees are encouraged to contact
Ice Age melting down: Intel features considered usefull!

Decades history of kernel exploitation, however still most used techniques are such as ROP. Software based approaches comes finally challenge this technique, one more successful than the others. Those approaches usually trying to solve far more than ROP only problem, and need to handle not only security but almost more importantly performance issues. Another common attacker vector for redirecting control flow is stack what comes from design of today’s architectures, and once again some software approaches lately tackling this as well. Although this software based methods are piece of nice work and effective to big extent, new game changing approach seems coming to the light. Methodology closing this attack vector coming right from hardware - intel. We will compare this way to its software alternatives, how one interleaving another and how they can benefit from each other to challenge attacker by breaking his most fundamental technologies. However same time we go further, to challenge those approaches and show that even with those technologies in place attackers is not yet in the corner.
Performance optimization techniques for Java code

The presentation covers the the basics of performance optimizations for real-world Java code. It starts with a theoretical overview of the concepts followed by several live demos
showing how performance bottlenecks can be diagnosed and eliminated. The demos include some non-trivial multi-threaded examples
inspired by real-world applications.
Open Source Storage at Scale: Ceph @ GRNET

Presentation held at GRNET Digital Technology Symposium on November 5-6, 2018 at the Stavros Niarchos Foundation Cultural Center, Athens, Greece.
• Introduction to Ceph and its internals
• Presentation of GRNET's Ceph deployments (technical specs, operations)
• Usecases: ESA Copernicus, ~okeanos, ViMa
Linux kernel development_ch9-10_20120410

Kernel synchronization methods are required to prevent race conditions when shared resources are accessed concurrently by multiple threads. The Linux kernel supports various synchronization primitives including atomic operations, spin locks, semaphores, mutexes, completion variables, and the big kernel lock. Each method has advantages and limitations depending on whether the resource can be accessed in interrupt context or while sleeping. Locking schemes must prevent deadlocks and ensure scalability to work effectively in multi-processor and preemptible kernel environments.
Linux kernel development chapter 10

Kernel synchronization methods are required to prevent race conditions when shared resources are accessed concurrently by multiple threads. The Linux kernel supports various synchronization primitives including atomic operations, spin locks, semaphores, mutexes, completion variables, and the big kernel lock. Each method has advantages and limitations depending on whether the resource can be accessed in interrupt context or while sleeping. More complex schemes like reader-writer locks and sequential locks also provide alternatives to binary locks.
Open arkcompiler

- OpenArkCompiler supports multiple languages and aims to optimize cross-language calls and improve efficiency.
- It includes components for compiling, optimization passes on its intermediate representation Maple, and backend code generation.
- The founder Zhou Zhide has decades of experience in compiler design and led the development of several compilers including Open64.
Ippevent : openshift Introduction

This document provides an introduction to Docker and Openshift including discussions around infrastructure, storage, monitoring, metrics, logs, backup, and security considerations. It describes the recommended infrastructure for a 3 node Openshift cluster including masters, etcd, and nodes. It also discusses strategies for storage, monitoring both internal pod status and external infrastructure metrics, collecting and managing logs, backups, and security features within Openshift like limiting resource usage and isolating projects.
Back to the CORE

In order to harden kernel exploitation as much as possible was introduced variety of features including KASLR, SMEP and sometimes also SMAP.
Even those are powerful techniques their effectiveness rely on their cooperation, environment and their implementation.
We will present new and some not so new exploitation techniques, show ideas behind breaking trough before mentioned security features and why it is possible, and we will take a look at pool spraying on x64 as well.
Polyglot and Functional Programming (OSCON 2012)

The document discusses introducing polyglot and functional programming concepts to Java developers. It explains that while Java is a powerful language, other JVM languages can offer advantages like more rapid development, concise coding, and taking advantage of non-object oriented and dynamic approaches. It provides examples of using functional concepts like map and filter to more declaratively operate on collections of data in a Java program. The document suggests exposing developers to these concepts through libraries and by experimenting with other JVM languages.
Performance Optimization of SPH Algorithms for Multi/Many-Core Architectures

In the framework of the Intel Parallel Computing Centre at the Research Campus Garching in Munich, our group at LRZ presents recent results on performance optimization of Gadget-3, a widely used community code for computational astrophysics. We identify and isolate a sample code kernel, which is representative of a typical Smoothed Particle Hydrodynamics (SPH) algorithm and focus on threading parallelism optimization, change of the data layout into Structure of Arrays (SoA), compiler auto-vectorization and algorithmic improvements in the particle sorting. We measure lower execution time and improved threading scalability both on Intel Xeon (2.6× on Ivy Bridge) and Xeon Phi (13.7× on Knights Corner) systems. First tests on second generation Xeon Phi (Knights Landing) demonstrate the portability of the devised optimization solutions to upcoming architectures.
1 Introduction to JAVA.pptx

This document provides an introduction to Java and Object-Oriented Programming (OOP) concepts. It defines key OOPs concepts like objects, classes, abstraction, encapsulation, inheritance, and polymorphism. It also discusses the features of Java like being simple, object-oriented, platform independent, secure, robust, portable, and high-performance. The document then provides examples of where Java is used including desktop applications, web applications, enterprise applications, mobile applications, and more.
So you want to liberate your data?

The document provides an overview of MongoDB, including how it stores data as documents in collections rather than rows in tables. It discusses how to query, update, and index MongoDB. The document also covers deployment options like replica sets for high availability and sharding for horizontal scaling. It notes some things to be aware of like the default lack of durability for inserts and updates.
Similar to Stack Frame Protection (20)
High-Performance Networking Using eBPF, XDP, and io_uring

High-Performance Networking Using eBPF, XDP, and io_uring
Quick introduction to Java Garbage Collector (JVM GC)

Quick introduction to Java Garbage Collector (JVM GC)
Ice Age melting down: Intel features considered usefull!

Ice Age melting down: Intel features considered usefull!
Performance Optimization of SPH Algorithms for Multi/Many-Core Architectures

Performance Optimization of SPH Algorithms for Multi/Many-Core Architectures
More from Conferencias FIST
Seguridad en Open Solaris

Este documento presenta información sobre la seguridad en OpenSolaris. Cubre temas como la minimización y el bastionado del sistema, los controles de acceso a archivos, los perfiles y roles de privilegios, los filtros de red y firewalls, la virtualización con zonas y contenedores, y las herramientas de auditoría.
Seguridad en Entornos Web Open Source

Este documento presenta una introducción a la seguridad en entornos web de código abierto. Explica conceptos clave como arquitecturas web bicapa y multicapa, autenticación básica mediante servicios de directorio LDAP, autenticación con control de acceso utilizando servicios SSO como Sibboleth y CAS, y autenticación fuerte a través de infraestructuras PKI implementadas con soluciones de código abierto como OpenCA y EJBCA. Además, proporciona detalles técnicos sobre estas soluciones de autentic
Spanish Honeynet Project

El documento presenta el Proyecto Honeynet Español. Explica brevemente qué son los honeynets, el Proyecto Honeynet original y sus objetivos. Luego describe el Proyecto Honeynet Español, incluyendo sus miembros, recursos y proyectos futuros como expandir el uso de honeynets para áreas como el spam y las redes Wi-Fi.
Seguridad en Windows Mobile

El documento resume los mecanismos de seguridad de Bluetooth como salto de frecuencias, emparejamiento, autenticación y autorización, y explica cómo estos pueden ser vulnerados mediante técnicas como sniffing, PIN cracking y BD_ADDR spoofing. También describe vectores de ataque como la vulnerabilidad de Directory Traversal en HTC que permite el acceso no autorizado a archivos.
SAP Security

The document discusses security risks in SAP systems and how cryptographic solutions can address them. It describes how technologies like secure single sign-on (SSO), encryption of data communications through Secure Network Communication (SNC), and digital signatures of documents through SAP's Secure Signature Framework (SSF) can authenticate users, encrypt data transmissions, and digitally sign files. The presentation provides examples of how these cryptographic methods have been implemented for SAP systems to facilitate secure access, communications, and document signing.
Que es Seguridad

El documento discute las definiciones comunes de seguridad de la información y sus limitaciones. Explora cinco puntos de vista diferentes (militar, seguros, académico, tecnologías de la información y legislativo) y cuatro ámbitos (información abstracta, sistemas de información, redes e internet, y organizaciones). También analiza cuatro definiciones populares de seguridad y los desafíos en definirla debido a la complejidad de los sistemas de información.
Network Access Protection

The document announces the FIST Conference to be held in Madrid, Spain in February and March 2009. It provides the conference website and notes that the conference is supported by Creative Commons under an Attribution-NoDerivs license, which allows copying and sharing of the work while requiring attribution and prohibiting derivatives. The conference will feature speaker David Carrasco in late February or early March 2009.
Las Evidencias Digitales en la Informática Forense

Este documento describe los principios básicos de la informática forense, incluyendo la definición, ámbito de actuación, objetivos del proceso, principios, normas fundamentales, evidencias digitales y su validez jurídica. Explica que la informática forense se encarga de investigar sistemas informáticos para hechos con relevancia jurídica y desarrolla técnicas para ubicar, reproducir y analizar evidencias digitales con fines legales. También cubre temas como la importancia de preservar la evidencia original, establecer
Evolución y situación actual de la seguridad en redes WiFi

Este documento resume la evolución y vulnerabilidades de la seguridad en redes Wi-Fi. Explica las vulnerabilidades iniciales en los estándares 802.11 y WEP, como los ataques de Fluhrer-Mantin-Shamir y Airbugh. También describe herramientas para realizar ataques prácticos como Airjack y BSD-Airtools. Finalmente, resume los sistemas posteriores como 802.1x, WPA y 802.11i que intentaron mejorar la seguridad.
El Information Security Forum

Este documento resume una presentación sobre el Information Security Forum (ISF). El ISF es una asociación internacional de más de 300 organizaciones que se dedica a resolver problemas clave relacionados con la gestión de riesgos de la información. El ISF desarrolla herramientas y servicios prácticos orientados al negocio, como encuestas de situación, un estándar de mejores prácticas y una extranet segura para sus miembros. La presentación describe los productos y servicios del ISF, incluidos sus programas de trabajo, encuestas y está
Criptografia Cuántica

El documento describe la criptografía cuántica y el protocolo BB84 para distribución cuántica de claves. Explica cómo los ordenadores cuánticos podrían romper los sistemas criptográficos actuales y cómo la distribución cuántica de claves utiliza los principios de la mecánica cuántica como la superposición y el enredo para generar claves criptográficas de forma segura.
Inseguridad en Redes Wireless

Este documento trata sobre la seguridad en redes WiFi. Explica que el cifrado WEP y WPA son vulnerables a ataques, mientras que WPA2 es más seguro. Recomienda usar WPA2 o WPA con contraseñas largas y complejas, y también implementar autenticación 802.1X/EAP. Finalmente, proporciona consejos sobre defensa en profundidad y contramedidas para mejorar la seguridad de las redes WiFi.
Mas allá de la Concienciación

El documento trata sobre la importancia de la concienciación en seguridad de la información. Explica que es necesario informar, formar y motivar a los empleados sobre buenas prácticas, cumplimiento de políticas y peligros. También destaca la necesidad de gestionar la responsabilidad, medir el comportamiento y aplicar el principio de necesidad de conocer, separación de funciones y supervisión.
Security Metrics

This document provides a summary of a presentation on security management metrics. It discusses defining metrics that can be quantitatively measured and interpreted over time. Good metrics are specific, measurable, actionable, relevant, and timely. The presentation provides examples of different types of metrics like activity, scope, availability, and efficiency. It also discusses using metrics to assess security management capability levels from undefined to optimized. Metrics should be specified and can be represented visually over time. The goal of metrics is to support informed security management decisions.
PKI Interoperability

The document summarizes Raúl Guerra Jiménez's presentation on PKI interoperability at the FIST Conference in September 2005 in Madrid. It discusses the basics of public key infrastructure (PKI) including concepts like digital certificates, certification authorities, cross-certification, and certificate revocation. It also provides examples of PKI applications in areas like internet security, remote access, virtual private networks, and securing intranets and applications.
Wifislax 3.1

WiFiSlax es una distribución Linux live CD orientada a la auditoría de seguridad inalámbrica. Incluye herramientas como Kismet, aircrack y aircrack-ng para auditoría WiFi, así como herramientas Bluetooth como BlueZ y aplicaciones para ataques como Bluebug y Bluesnarf. El objetivo es facilitar el uso de Linux para seguridad inalámbrica y concienciar sobre los riesgos de WEP y otras redes inseguras.
Network Forensics

The document summarizes a presentation on network forensics and lessons learned from the July 2007 London attacks. The presentation covered early adoption of firewalls and DMZs, intrusion prevention systems, the use of fingerprints and DNA in forensics, the 2004 Madrid train bombings and 2005 London bombings. It discussed the police investigation into the London attacks including identifying suspects from CCTV footage and a practice run captured on video. The presentation proposed the use of network monitoring tools as a forensic technique and discussed challenges of detecting slow scan attacks and those using random ports or covert channels.
Riesgo y Vulnerabilidades en el Desarrollo

1) El documento habla sobre los riesgos y vulnerabilidades en el desarrollo web y ofrece soluciones en PHP. 2) Recomienda definir condiciones de ejecución seguras para las bases de datos, controlar el acceso al código y procesar los datos de entrada. 3) Explica formas de mejorar la seguridad del servidor web, lenguaje de programación y sistema gestor de bases de datos.
Security Maturity Model

The document introduces the Security Maturity Model (SMM) which describes an organization's security maturity based on factors such as security responsibilities, organization, practices, policies, access control, audits, and security investment management. It outlines 5 levels of security maturity for organizations from initial/ad hoc (Level 1) to optimum/embedded (Level 5). Levels 3-5 involve defined, managed, and quantitative security practices and responsibilities. The SMM also describes a Security Norms Framework for developing flexible and domain-specific security policies, norms, standards and procedures.
More from Conferencias FIST (20)
Las Evidencias Digitales en la Informática Forense

Las Evidencias Digitales en la Informática Forense
Evolución y situación actual de la seguridad en redes WiFi

Evolución y situación actual de la seguridad en redes WiFi
Recently uploaded
20240609 QFM020 Irresponsible AI Reading List May 2024

Everything I found interesting about the irresponsible use of machine intelligence in May 2024
Full-RAG: A modern architecture for hyper-personalization

Mike Del Balso, CEO & Co-Founder at Tecton, presents "Full RAG," a novel approach to AI recommendation systems, aiming to push beyond the limitations of traditional models through a deep integration of contextual insights and real-time data, leveraging the Retrieval-Augmented Generation architecture. This talk will outline Full RAG's potential to significantly enhance personalization, address engineering challenges such as data management and model training, and introduce data enrichment with reranking as a key solution. Attendees will gain crucial insights into the importance of hyperpersonalization in AI, the capabilities of Full RAG for advanced personalization, and strategies for managing complex data integrations for deploying cutting-edge AI solutions.
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
TrustArc Webinar - 2024 Global Privacy Survey

How does your privacy program stack up against your peers? What challenges are privacy teams tackling and prioritizing in 2024?
In the fifth annual Global Privacy Benchmarks Survey, we asked over 1,800 global privacy professionals and business executives to share their perspectives on the current state of privacy inside and outside of their organizations. This year’s report focused on emerging areas of importance for privacy and compliance professionals, including considerations and implications of Artificial Intelligence (AI) technologies, building brand trust, and different approaches for achieving higher privacy competence scores.
See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar will review:
- The top 10 privacy insights from the fifth annual Global Privacy Benchmarks Survey
- The top challenges for privacy leaders, practitioners, and organizations in 2024
- Key themes to consider in developing and maintaining your privacy program
Things to Consider When Choosing a Website Developer for your Website | FODUU

Choosing the right website developer is crucial for your business. This article covers essential factors to consider, including experience, portfolio, technical skills, communication, pricing, reputation & reviews, cost and budget considerations and post-launch support. Make an informed decision to ensure your website meets your business goals.
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
Best 20 SEO Techniques To Improve Website Visibility In SERP

Boost your website's visibility with proven SEO techniques! Our latest blog dives into essential strategies to enhance your online presence, increase traffic, and rank higher on search engines. From keyword optimization to quality content creation, learn how to make your site stand out in the crowded digital landscape. Discover actionable tips and expert insights to elevate your SEO game.
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for life science domain, where you retriever information from biomedical knowledge graphs using LLMs to increase the accuracy and performance of generated answers
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
“I’m still / I’m still / Chaining from the Block”

“An Outlook of the Ongoing and Future Relationship between Blockchain Technologies and Process-aware Information Systems.” Invited talk at the joint workshop on Blockchain for Information Systems (BC4IS) and Blockchain for Trusted Data Sharing (B4TDS), co-located with with the 36th International Conference on Advanced Information Systems Engineering (CAiSE), 3 June 2024, Limassol, Cyprus.
Uni Systems Copilot event_05062024_C.Vlachos.pdf

Unlocking Productivity: Leveraging the Potential of Copilot in Microsoft 365, a presentation by Christoforos Vlachos, Senior Solutions Manager – Modern Workplace, Uni Systems
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-und-domino-lizenzkostenreduzierung-in-der-welt-von-dlau/
DLAU und die Lizenzen nach dem CCB- und CCX-Modell sind für viele in der HCL-Community seit letztem Jahr ein heißes Thema. Als Notes- oder Domino-Kunde haben Sie vielleicht mit unerwartet hohen Benutzerzahlen und Lizenzgebühren zu kämpfen. Sie fragen sich vielleicht, wie diese neue Art der Lizenzierung funktioniert und welchen Nutzen sie Ihnen bringt. Vor allem wollen Sie sicherlich Ihr Budget einhalten und Kosten sparen, wo immer möglich. Das verstehen wir und wir möchten Ihnen dabei helfen!
Wir erklären Ihnen, wie Sie häufige Konfigurationsprobleme lösen können, die dazu führen können, dass mehr Benutzer gezählt werden als nötig, und wie Sie überflüssige oder ungenutzte Konten identifizieren und entfernen können, um Geld zu sparen. Es gibt auch einige Ansätze, die zu unnötigen Ausgaben führen können, z. B. wenn ein Personendokument anstelle eines Mail-Ins für geteilte Mailboxen verwendet wird. Wir zeigen Ihnen solche Fälle und deren Lösungen. Und natürlich erklären wir Ihnen das neue Lizenzmodell.
Nehmen Sie an diesem Webinar teil, bei dem HCL-Ambassador Marc Thomas und Gastredner Franz Walder Ihnen diese neue Welt näherbringen. Es vermittelt Ihnen die Tools und das Know-how, um den Überblick zu bewahren. Sie werden in der Lage sein, Ihre Kosten durch eine optimierte Domino-Konfiguration zu reduzieren und auch in Zukunft gering zu halten.
Diese Themen werden behandelt
- Reduzierung der Lizenzkosten durch Auffinden und Beheben von Fehlkonfigurationen und überflüssigen Konten
- Wie funktionieren CCB- und CCX-Lizenzen wirklich?
- Verstehen des DLAU-Tools und wie man es am besten nutzt
- Tipps für häufige Problembereiche, wie z. B. Team-Postfächer, Funktions-/Testbenutzer usw.
- Praxisbeispiele und Best Practices zum sofortigen Umsetzen
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

ABSTRACT: A prima vista, un mattoncino Lego e la backdoor XZ potrebbero avere in comune il fatto di essere entrambi blocchi di costruzione, o dipendenze di progetti creativi e software. La realtà è che un mattoncino Lego e il caso della backdoor XZ hanno molto di più di tutto ciò in comune.
Partecipate alla presentazione per immergervi in una storia di interoperabilità, standard e formati aperti, per poi discutere del ruolo importante che i contributori hanno in una comunità open source sostenibile.
BIO: Sostenitrice del software libero e dei formati standard e aperti. È stata un membro attivo dei progetti Fedora e openSUSE e ha co-fondato l'Associazione LibreItalia dove è stata coinvolta in diversi eventi, migrazioni e formazione relativi a LibreOffice. In precedenza ha lavorato a migrazioni e corsi di formazione su LibreOffice per diverse amministrazioni pubbliche e privati. Da gennaio 2020 lavora in SUSE come Software Release Engineer per Uyuni e SUSE Manager e quando non segue la sua passione per i computer e per Geeko coltiva la sua curiosità per l'astronomia (da cui deriva il suo nickname deneb_alpha).
CAKE: Sharing Slices of Confidential Data on Blockchain

Presented at the CAiSE 2024 Forum, Intelligent Information Systems, June 6th, Limassol, Cyprus.
Synopsis: Cooperative information systems typically involve various entities in a collaborative process within a distributed environment. Blockchain technology offers a mechanism for automating such processes, even when only partial trust exists among participants. The data stored on the blockchain is replicated across all nodes in the network, ensuring accessibility to all participants. While this aspect facilitates traceability, integrity, and persistence, it poses challenges for adopting public blockchains in enterprise settings due to confidentiality issues. In this paper, we present a software tool named Control Access via Key Encryption (CAKE), designed to ensure data confidentiality in scenarios involving public blockchains. After outlining its core components and functionalities, we showcase the application of CAKE in the context of a real-world cyber-security project within the logistics domain.
Paper: https://doi.org/10.1007/978-3-031-61000-4_16
Essentials of Automations: The Art of Triggers and Actions in FME

In this second installment of our Essentials of Automations webinar series, we’ll explore the landscape of triggers and actions, guiding you through the nuances of authoring and adapting workspaces for seamless automations. Gain an understanding of the full spectrum of triggers and actions available in FME, empowering you to enhance your workspaces for efficient automation.
We’ll kick things off by showcasing the most commonly used event-based triggers, introducing you to various automation workflows like manual triggers, schedules, directory watchers, and more. Plus, see how these elements play out in real scenarios.
Whether you’re tweaking your current setup or building from the ground up, this session will arm you with the tools and insights needed to transform your FME usage into a powerhouse of productivity. Join us to discover effective strategies that simplify complex processes, enhancing your productivity and transforming your data management practices with FME. Let’s turn complexity into clarity and make your workspaces work wonders!
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Recently uploaded (20)
20240609 QFM020 Irresponsible AI Reading List May 2024

20240609 QFM020 Irresponsible AI Reading List May 2024
Full-RAG: A modern architecture for hyper-personalization

Full-RAG: A modern architecture for hyper-personalization
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
Things to Consider When Choosing a Website Developer for your Website | FODUU

Things to Consider When Choosing a Website Developer for your Website | FODUU
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
Best 20 SEO Techniques To Improve Website Visibility In SERP

Best 20 SEO Techniques To Improve Website Visibility In SERP
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for Life Science to increase LLM accuracy
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

Cosa hanno in comune un mattoncino Lego e la backdoor XZ?
CAKE: Sharing Slices of Confidential Data on Blockchain

CAKE: Sharing Slices of Confidential Data on Blockchain
Essentials of Automations: The Art of Triggers and Actions in FME

Essentials of Automations: The Art of Triggers and Actions in FME
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Stack Frame Protection
- 1. Stack Frame Protection with LD_PRELOAD @auth: pancake @place: FIST @date: 20040507
- 2. Outlook ● Buffer overflows and stack basics; ● Protection methods; ● Target on preload; ● LibSFP {aka my testing lib}; ● Internal work; ● Few code examples; ● Links and EOF;
- 3. Buffer overflows basics ● The first cause of insecurity; ● Every function is closed into an stack frame. ● The stack frame saves information about local variables and return pointer. ● Programmers must focus in secure code, not just external security.
- 4. Protection methods ● Development stage. – Patches to Gcc that uses canary-based methods to ensure the SF integrity. – Use lint to clean insecure function calls. ● Runtime – Ptrace-based security. 3x slower, but the most secure. – Library-based security. Faster and protects almost basic bugs.
- 5. Preload method ● Dynamically load of a library with LD_PRELOAD or ld.so.conf by ld.so; ● Replacement for the most buggy function symbols by secure ones (strcpy, memcpy, strlen, ...); ● Exists some libraries that do that: – Libsafe – secure libc functions. – Libformat - secure format strings. ● Main problem: non-portable.
- 6. LibSFP ● I decide to write a libformat/libsafe replacement. ● Target on: – UNIX-OSes portability (GNU,*BSD,...) – Architecture portability (endian, stack) – Open, active development. It's GPLd. ● Actually its development is stopped. But i'll be happy to receive contributions and follow the project.
- 7. Internal work ● Basically it's a library that rewrites every symbol. ● Cross all stack frames layers until find the current one. ● Measures the current SF size and limits calls to this size. ● Library can be configured at runtime – Offset: Change overflow margins. – Action: alert, ignore, force CoreDump...
- 8. Internal work ● There are 3 kind of variables: – Local – stored in the stack frame. (easy to protect). – Global – stored in Heap. (difficult to know the limits). – Malloc – stored in Heap space with chunk header information. (the assigned space limits could be read from chunk headers). ● Malloc techniques: – LibSFP stores a magic value into the chunk header to separate global variables from chunked ones. – Chunks are memory-aligned, it means that size isn't exact.
- 9. Internal work ● There are 3 kind of variables: – Local – stored in the stack frame. (easy to protect). – Global – stored in Heap. (difficult to know the limits). – Malloc – stored in Heap space with chunk header information. (the assigned space limits could be read from chunk headers). ● Malloc techniques: – LibSFP stores a magic value into the chunk header to separate global variables from chunked ones. – Chunks are memory-aligned, it means that size isn't exact.
- 10. Few examples Now it's the moment for going to the terminal and show some examples...
- 11. Links and EOF ● Libsafe – http://www.research.avayalabs.com/project/libsafe/ ● Immunix Gcc StackGuard – http://www.cse.ogi.edu/DISC/projects/immunix/StackGuard/ ● Libsfp isn't released yet, but if I receive interest I would probably upload into: – http://www.nopcode.org/ – http://pancake.host.sk/altres/src/
