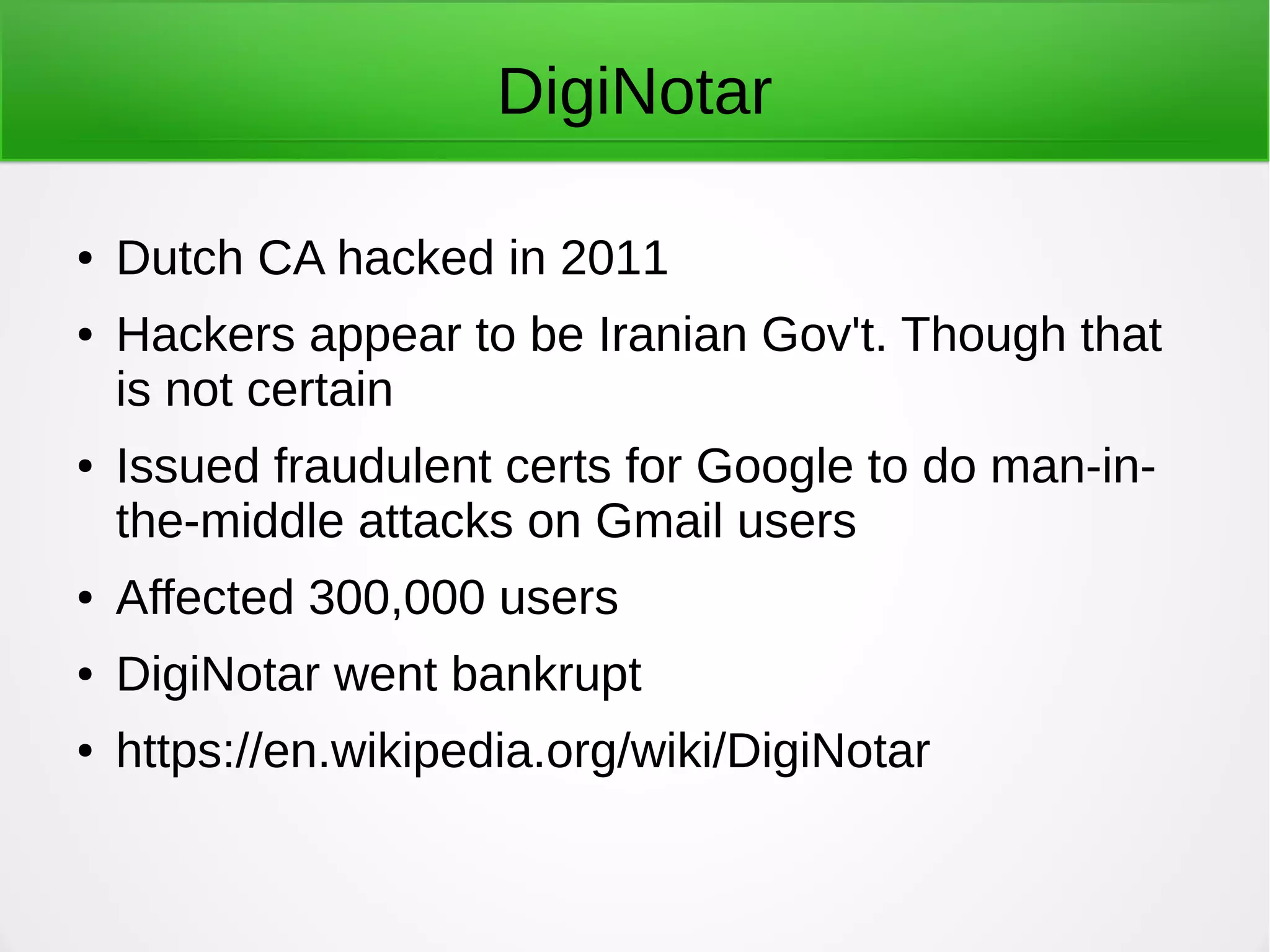
SSL certificates use public key encryption to verify secure connections between clients and servers. Issues arise from the hierarchical trust model where root certificate authorities can sign other certificates, and some authorities have had their private keys compromised, allowing fake certificates to be generated. Alternative approaches like Certificate Transparency aim to increase transparency and accountability over the certificate issuance and validation process.