This document discusses improving security by addressing issues with random number generation and timing attacks. It proposes using a random delay at the network interface level to obscure timing signals and prevent timing attacks. It also suggests revisiting an old technique called TrueRand that uses differences between a CPU's clock and other clocks/timers as a source of entropy for random number generation. The document advocates a pragmatic approach of deploying imperfect but effective defenses rather than insisting on perfection.








![The Proposed Fix
Any time values need to compared in a security
critical context, compare them in constant time (so
that there‟s no correlation between what‟s
compared, and how long it takes)
public static boolean isEqual(byte[] a, byte[] b) {
if (a.length != b.length) { return false; }
int result = 0;
for (int i = 0; i < a.length; i++) {
result |= a[i] ^ b[i]
}
return result == 0;
}
Looks good, right?](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-11-320.jpg)


![What Could Go Wrong?
“All timing noise can be averaged out eventually, so a global random
delay can‟t work”
Pretty much all password comparisons are done with non-constant time
compares, so I guess all passwords are vulnerable?
Here‟s some SSH 0day
sys_auth_passwd(Authctxt *authctxt, const char
*password){…
/* Encrypt the candidate password using the proper
salt. */
encrypted_password = xcrypt(password,
(pw_password[0] && pw_password[1]) ? pw_password :
"xx");
return (strcmp(encrypted_password, pw_password) == 0);
Strcmp is not constant time. So, you just offline brute force for
passwords that have certain characters and see how far you get.
It is highly unlikely that the above “attack” actually works
Nanosecond differentials are too small to recover
Maybe not locally…hmmm…](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-14-320.jpg)







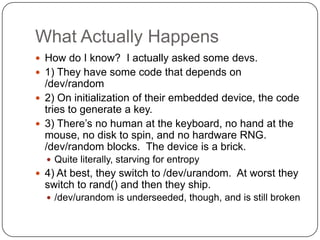

![TrueRand: An Old Hack [0]
Why do we like measuring keyboard and mice?
Humans and computers are not synchronized
Humans do not operate on nanosecond clocks like
computers do
Human is slow clock, CPU is fast clock
Any system with two clocks, has a Hardware
Random Number Generator
Even if the error is one part per million, that‟s a bit
per second per megahertz
The error is generally much larger than a part per
million, just from thermal noise
(Not just thermal noise)](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-25-320.jpg)
![TrueRand: An Old Hack [1]
What TrueRand (from Matt Blaze and D.P. Mitchell, in
1996) does
Run the CPU in a tight loop (count++);
Every 16ms, fire an interrupt
On interrupt, shuffle the count variable, and integrate it into a
buffer
The entropy comes in here – timer is slow clock, CPU is
fast clock
After 11 shuffles, return the buffer as an integer
Hash two buffers together using sha1, return only the
first byte
It ain‟t bad. But it‟s disowned.
That‟s too bad, because it would have prevented (at
least) 1/200 keys from being broken.](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-26-320.jpg)

![DakaRand 1.0 [0]
An update to the old model
Multiple generators
Sleepers: Measure usleep with
CLOCK_MONOTONIC
CLOCK_REALTIME
RDTSC (on X86 platforms)
CPU counter – there are equivalents for ARM, MIPS
Incrementer: See how many times we can
increment an integer within a certain time period
(100% CPU)](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-28-320.jpg)
![DakaRand 1.0 [1]
RTC: Measure interrupts from the realtime clock
using CLOCK_MONOTONIC (dedicated IRQ!)
128hz
8192hz
Threads: Measure the status of an integer
modulated by a runaway thread (100% CPU)
Anyone who thinks computers are completely deterministic
creations has never written threaded code ;)
Two Threads, One Int (one adds, one subtracts, main polls)
Two Threads, Two ints (both add, main compares)
One Thread, One Int (one adds, main polls)
Possible addition: Noisier functions than add](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-29-320.jpg)








![We have to stop injection
vulnerabilities
They‟re killing us
They‟re not l33t
They‟re totally effective
They‟re the vast majority of vulnerabilities ever
written and discovered
We haven‟t actually fixed them
If we did fix them, they wouldn‟t still be costing
billions of dollars
[Yes, we‟re going to revisit Interpolique…it‟s OK,
we‟re going to bash it too]](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-41-320.jpg)




![Look at this. It matters.
+[,+[-[>+>+<<-]>[<+>-]+>>++++++++[<-------->-]<-[< [-
]>>>+[<+<+>>-] <[>+<-]<[<++>>>+[<+<->>-]<[>+<-
]]>[<]<]>>[-]<<<[[- ]<[>>+>+<<<-]>> [<<+>>-
]>>++++++++[<-------->-]<->>++++[<++++ ++++>-]<-
<[>>>+<<[ >+>[-]<<-]>[<+>-
]>[<<<<<+>>>>++++[<++++++++>-]>-]< <-<-]>[<<<<[-
]>>>>[<<<<->>>>-]]<<++++[<<++++++++>>-]<<-
[>>+>+<<<-]>>[<<+ >>-]+>>+++++[<----->-]<-[<[-
]>>>+[<+<->>-]<[>+ <-]<[<++>>>+[<+<+ >>-]<[>+<-
]]>[<]<]>>[-]<<<[[-]<<[>>+>+<<<-]> >[<<+>>-]+>------------
[<[-]>>>+[<+<->>-]<[>+<-]<[<++>>>+[<+<+>>-]< [>+<-
]]>[<]<]>>[-]< <<<<------------->>[[-]+++++[<<+++++>>-
]<<+>> ]<[>++++[<<+++++++ +>>-]<-]>]<[-
]++++++++[<++++++++>-]<+>]<.[ -]+>>+<]>[[-]<]<]](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-47-320.jpg)


![Interpolique [0]
Released in 2010 at HOPE
Concept for eliminating injection attacks while
retaining “dangerous” (but developer preferred)
coding styles
Both SQLi and XSS
Basic idea
“SELECT * FROM foo where x=$x and y=$y”
Humans can pretty easily see the separation between
code and data. Data begins with $. Code does not.
The language throws that data away and just smashes
strings together.
Does it have to?](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-51-320.jpg)
![Interpolique [1]
The original approach for Interpolique
First, use an alternate syntax to identify the desired
variables
“SELECT * FROM foo where x=^^x and y=^^y”
Then, create a function that returns the code we‟d have
liked the developer to write.
$stmt = $conn->prepare(“SELECT * FROM foo where x=? and
y=?”);
$stmt->bind_param(“ss”, $x, $y);
$stmt->execute();
Finally, evaluate the generated code
eval(b(“SELECT * FROM foo where x=^^x and y=^^y”);
Eval is, surprisingly, the only way to retrieve the values of $x
and $y from inside the function b().](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-52-320.jpg)




















![More Detail
Candidate collection
For each IP, incrementing the first byte
first, (1.1.1.1, 2.1.1.1, 3.1.1.1…), send a TCP SYN
on the required port (23 for telnet, 3389 for RDP)
In a separate window, log TCP SYN|ACKs with
tcpdump
tcpdump –w log 'tcp[tcpflags] = (tcp-syn|tcp-ack)'
Scanrand was being buggy, this maximized logging
Candidate Inspection
Telnet Encryption – nmap team whipped up a quick
check, so I just fed the IP list to it
Very few found](https://image.slidesharecdn.com/blackops2012-120805184348-phpapp02/85/Black-ops-2012-75-320.jpg)