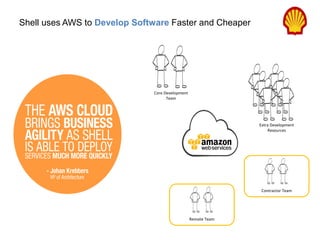
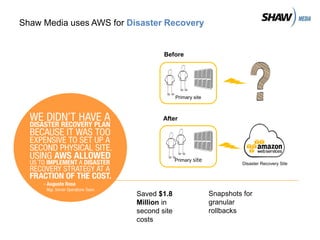
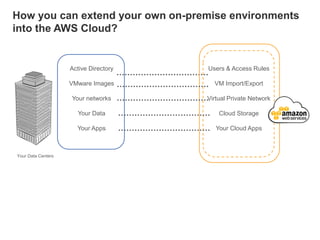
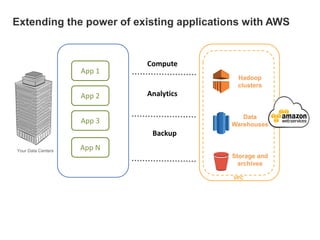
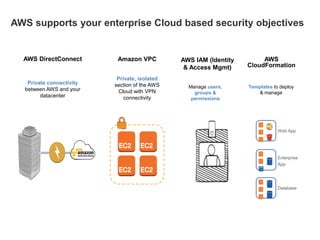
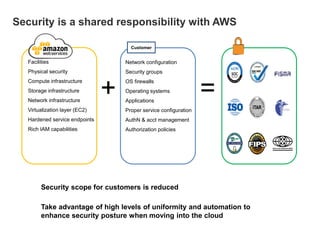
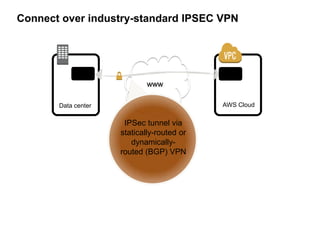
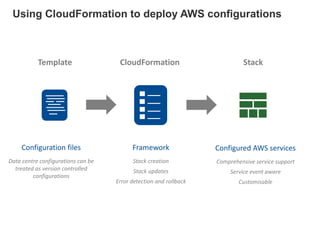
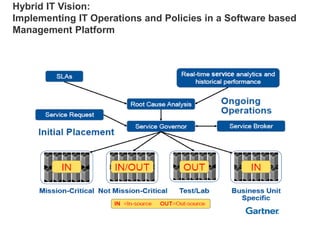
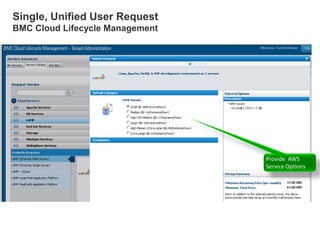
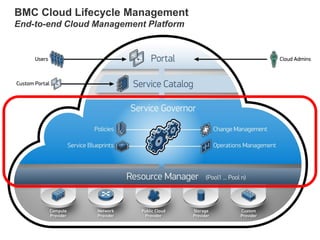
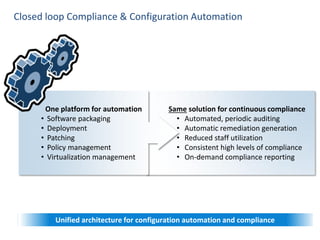
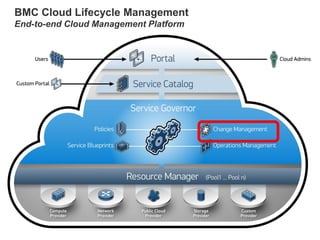
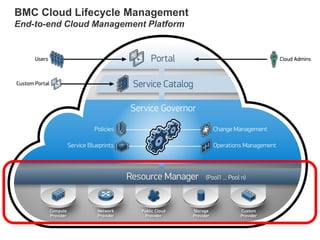
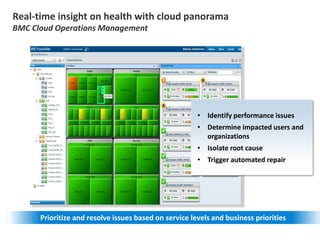
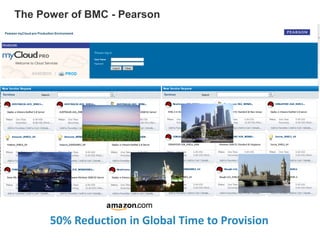
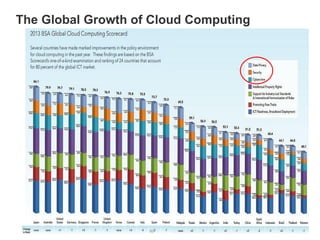
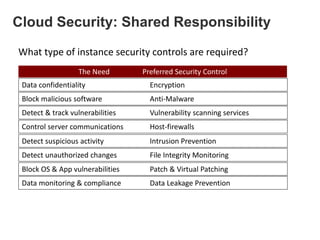
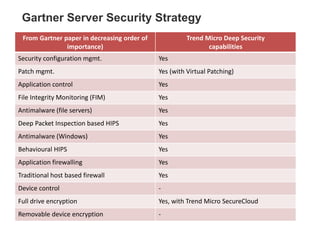
Hybrid Cloud & the Enterprise
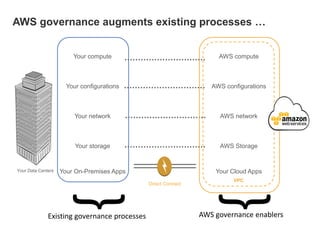
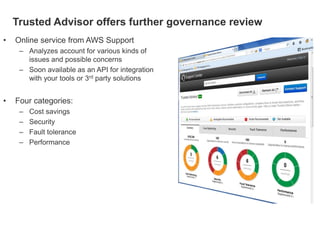
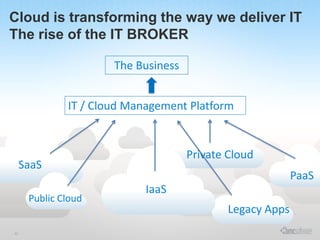
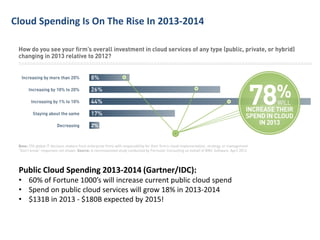
This document discusses how enterprises are extending their infrastructure into the cloud using hybrid cloud solutions. It provides examples of how various companies such as Shell, S&P Capital IQ, and Lionsgate are using Amazon Web Services (AWS) to augment their on-premises infrastructure. The presentation discusses how AWS enables hybrid environments through services like Virtual Private Clouds and identity and access management. It also discusses how enterprises can achieve security, control and governance when building hybrid cloud solutions with AWS and enterprise management platforms from partners like BMC.