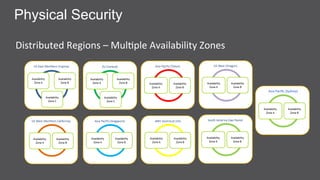
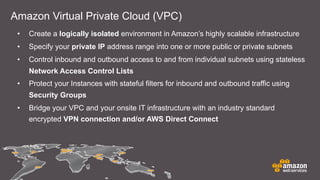
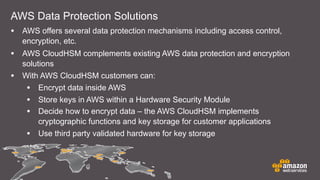
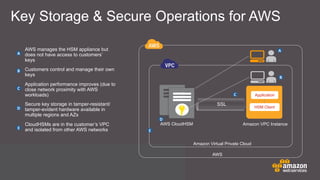
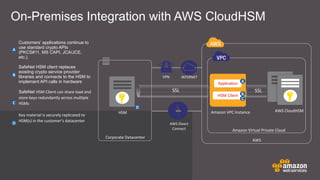
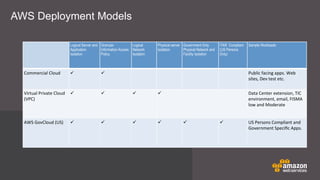
The document discusses cloud security features offered by AWS, including universal access to security capabilities for all customers, visibility into infrastructure, auditing capabilities, transparency through certifications, and a shared responsibility model between AWS and customers. It provides details on several security and compliance control objectives focused on areas like security organization, user access, logical security, data handling, physical security, change management, and incident handling. Finally, it discusses specific AWS security services and features like CloudHSM for key management and different deployment models.