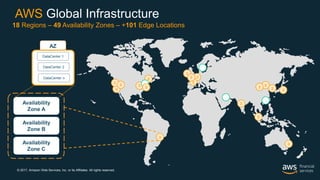
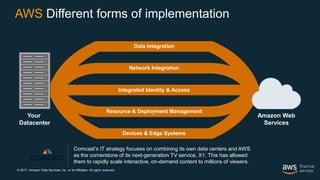
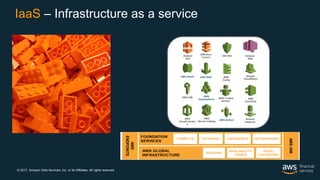
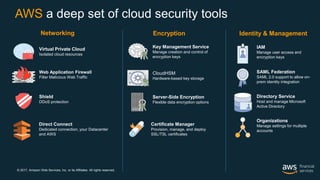
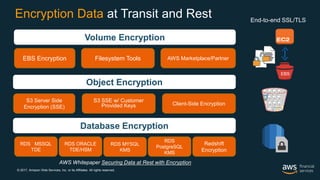
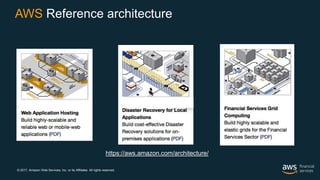
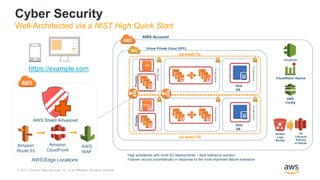
This document outlines the security and compliance capabilities of Amazon Web Services (AWS), highlighting its global infrastructure with 18 regions and 49 availability zones. It details various services and tools for data protection, identity access control, and compliance measures, emphasizing customers' control over their content and privacy. Additionally, it presents AWS’s commitment to maintaining secure cloud environments through independent audits and advanced security features.