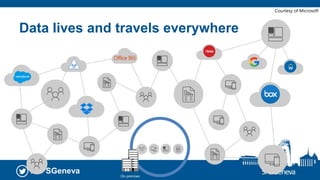
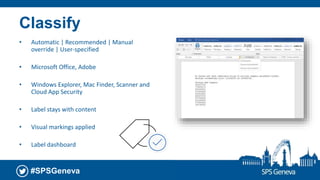
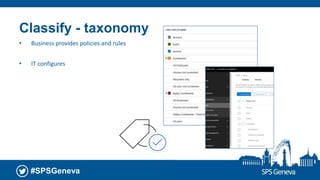
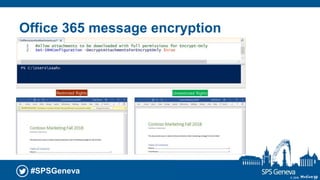
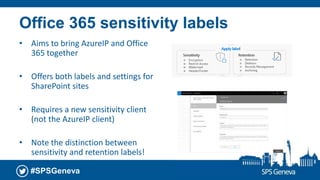
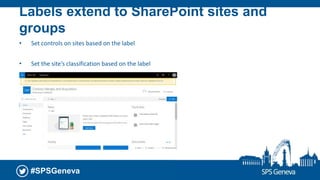
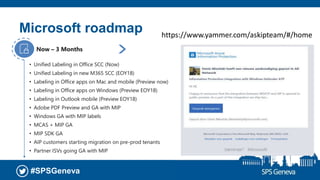
The document presents a session at the SPS Geneva event focused on Azure Information Protection and its integration with Office 365, highlighting goals including understanding data classification and Microsoft’s roadmap for information protection. It covers key features like document encryption, sensitivity labels, and compliance with regulations such as GDPR. The session emphasizes automation and protection of sensitive information across various platforms, showcasing tools for classifying and securing content.