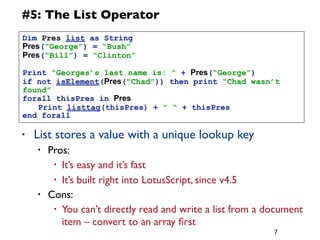
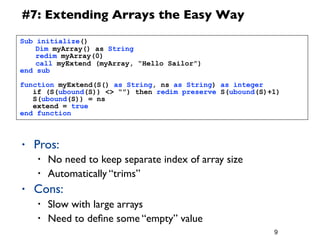
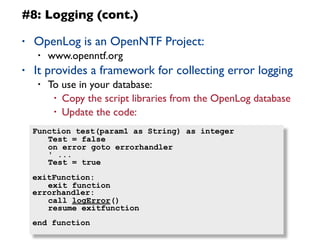
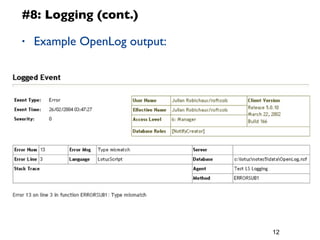
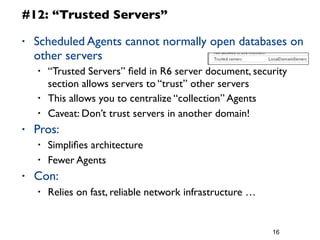
The document provides a 12 step guide to writing effective LotusScript code. The steps include how to code for maintenance, testing code often and completely, spending time planning before coding, using defensive coding practices, leveraging built-in data types like Lists and NotesDateTime, and using logging and error handling techniques. Following the guide is intended to help produce code that is easier to maintain, has fewer bugs, and higher performance.