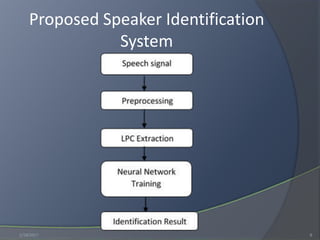
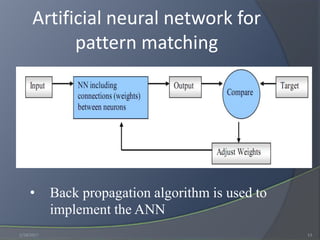
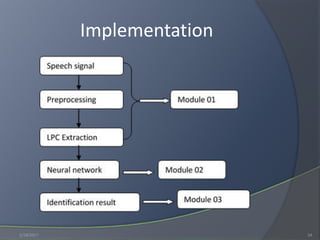
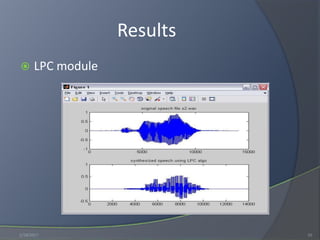
This document discusses speaker identification and authentication methods. It presents an overview of authentication approaches like tokens, knowledge, and biometrics. It then reviews literature on speech recognition paradigms and approaches. The methodology section proposes a speaker identification system that preprocesses voice files, extracts LPC features, and uses an artificial neural network for pattern matching. Results show the system achieves around 84% correct identification accuracy on 88 samples. Recommendations include interconnecting LPC and neural network modules, enabling text-independent identification, increasing the number of users and accuracy, and enabling cross-platform development.