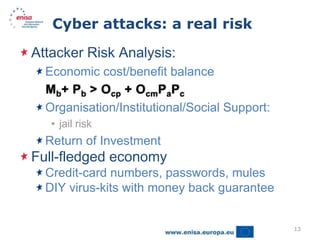
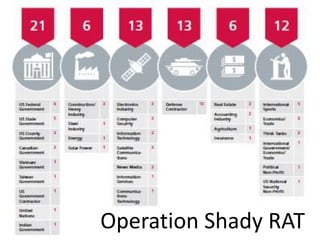
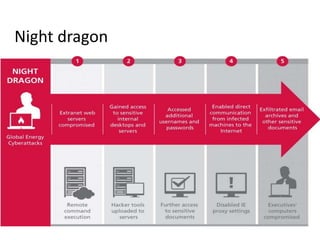
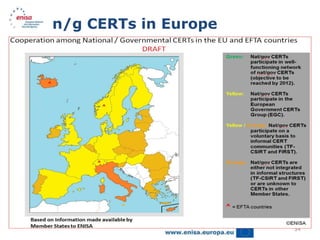
This document discusses cybercrime risks in Europe. It provides an overview of ENISA's activities related to facilitating cooperation against cybercrime, developing guidance on new and emerging technologies, and promoting privacy and trust online. Specific contributions from ENISA include developing best practices for cooperation between computer emergency response teams (CERTs) and law enforcement agencies. ENISA also organizes annual workshops for CERTs to share information and hosts a clearinghouse of incident response tools. A proposed new EU Directive aims to more effectively address large-scale cyber attacks by criminalizing certain hacking tools and their use.