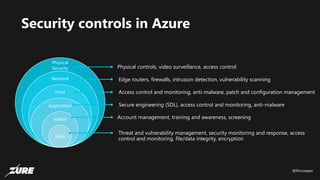
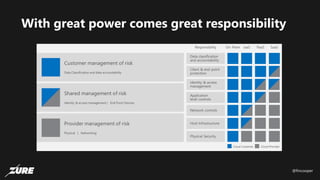
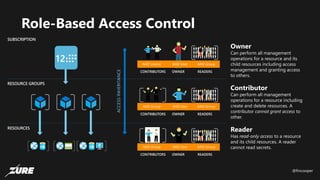
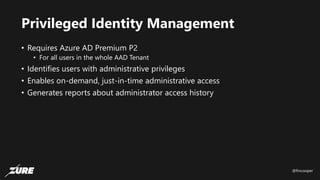
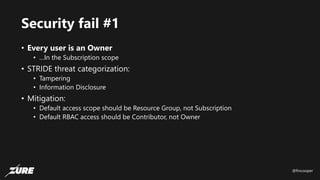
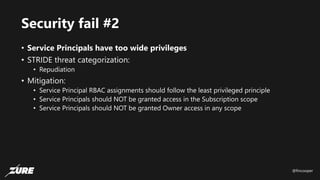
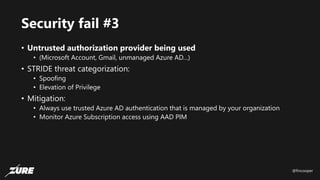
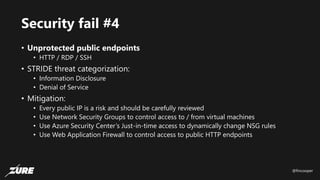
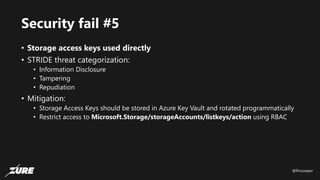
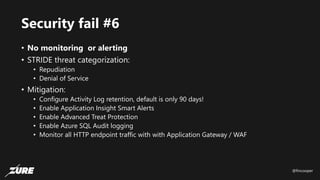
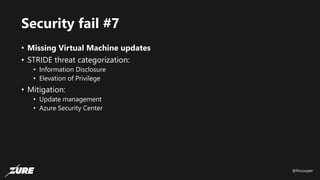
The document discusses top Azure security fails and how to avoid them. It begins by introducing the speaker and their experience with Azure security. It then covers common security controls in Azure and the concept of role-based access control (RBAC). The document identifies seven common security fails including giving all users owner permissions, overprivileged service principals, untrusted authentication providers, unprotected public endpoints, misused storage access keys, lack of monitoring and alerting, and missing virtual machine updates. It demonstrates how to avoid these fails using tools like Azure Security Center and the Secure DevOps kit for Azure.