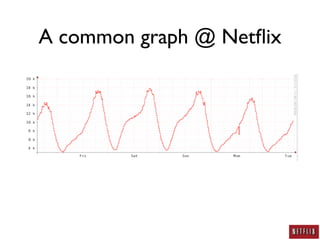
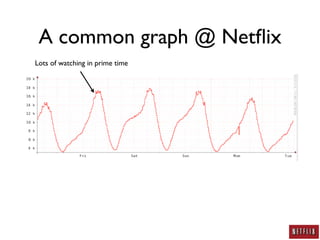
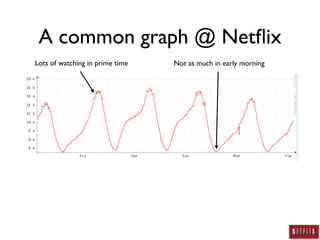
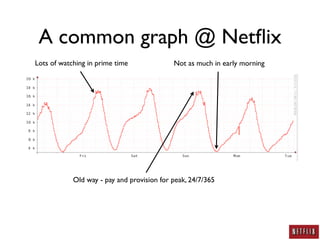
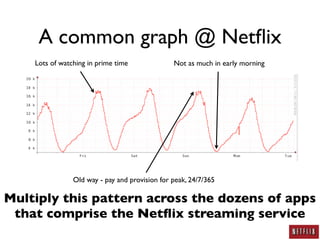
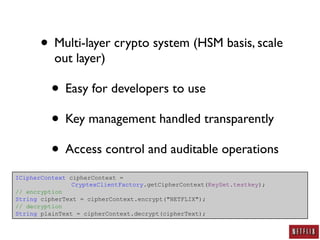
This document summarizes Jason Chan's presentation on real world cloud application security lessons learned from running large scale systems at Netflix. Some key points include:
- Netflix has migrated nearly 99% of its infrastructure to the public cloud to take advantage of scalability and reduce costs of "undifferentiated heavy lifting".
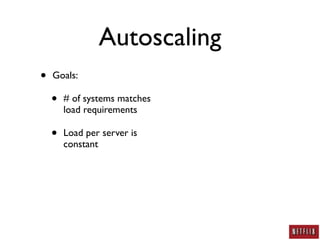
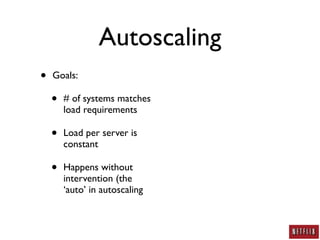
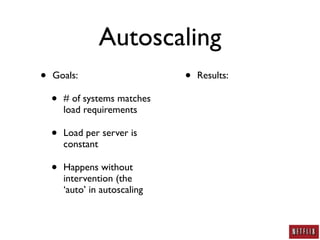
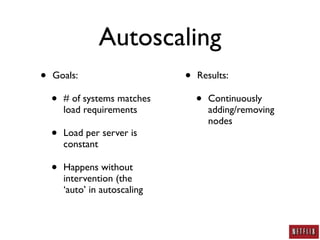
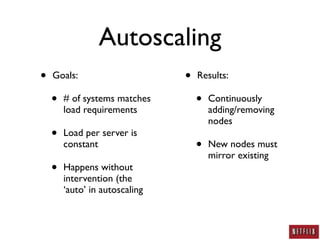
- Netflix uses autoscaling to dynamically scale the number of systems based on load, allowing servers to match load requirements and reducing costs.
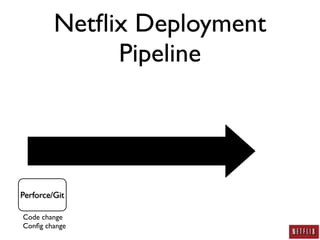
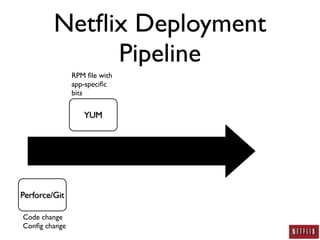
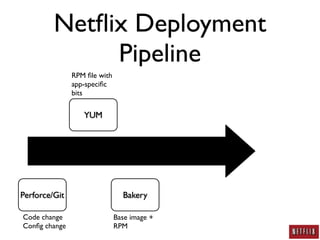
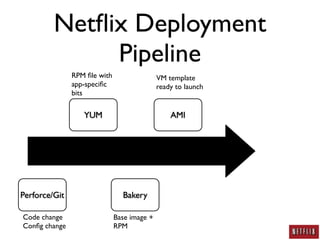
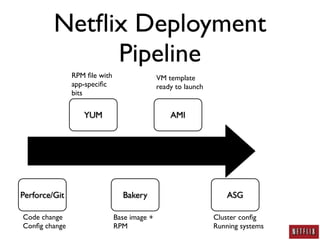
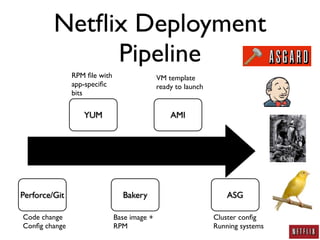
- Netflix developed a deployment pipeline to easily deploy code and configuration changes across thousands of systems without making changes to existing systems.
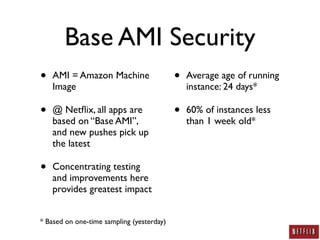
- Security practices had to adapt to the cloud model, including managing vulnerabilities at the base AMI level, integrating security tools into the development pipeline, and standard