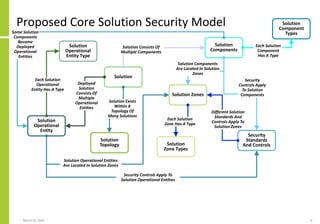
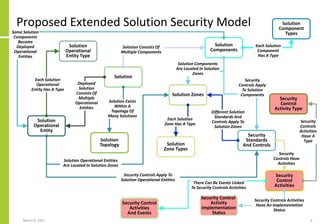
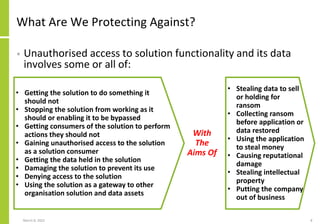
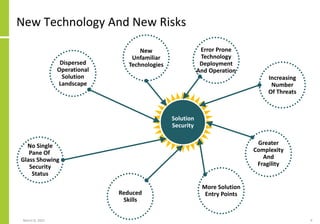
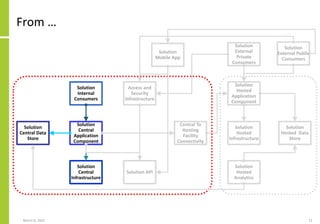
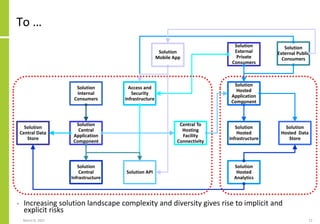
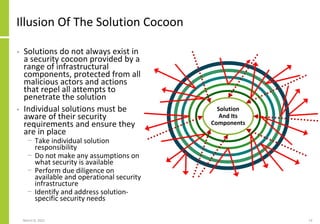
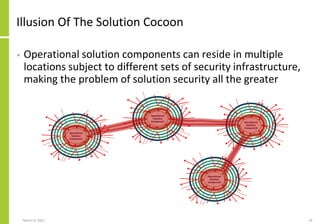
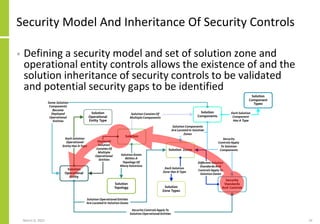
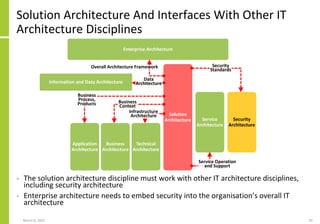
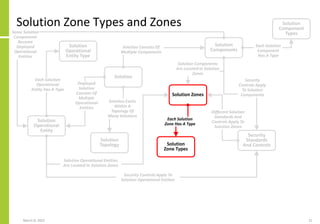
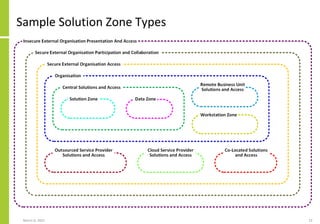
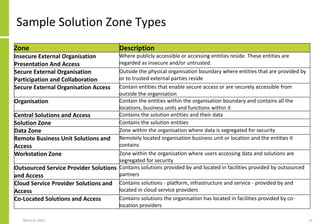
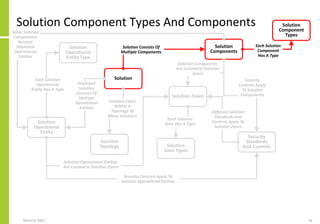
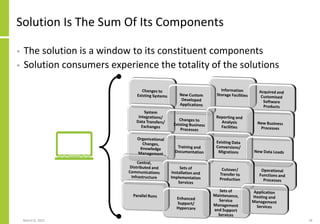
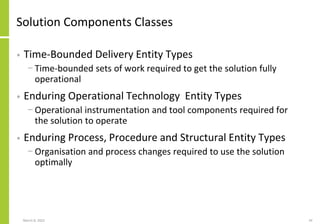
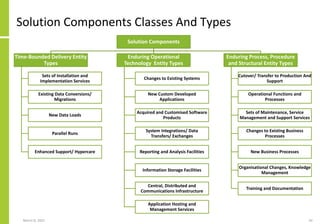
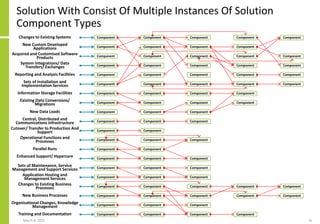
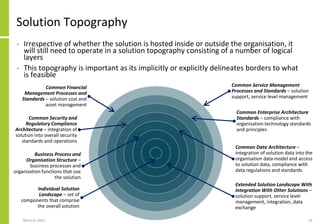
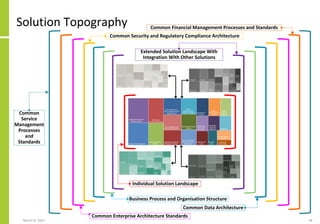
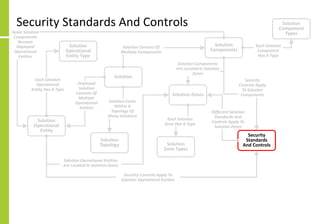
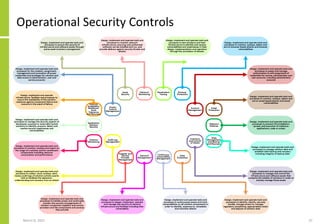
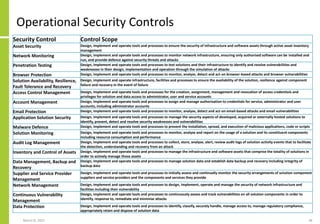
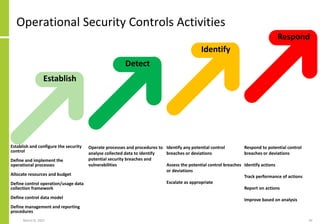
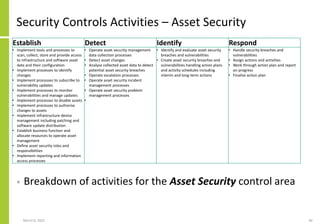
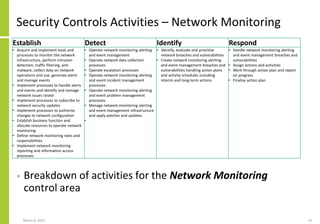
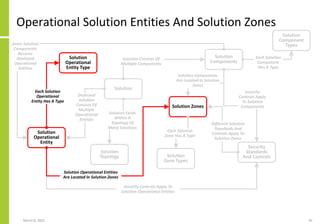
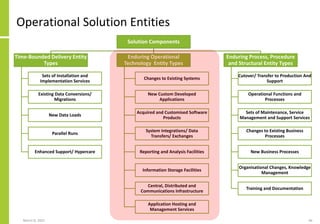
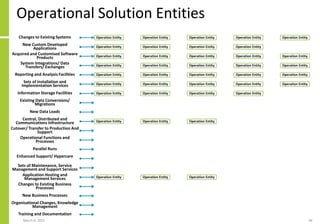
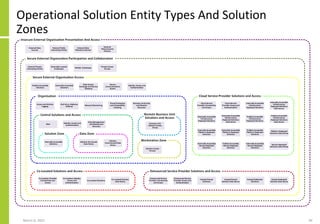
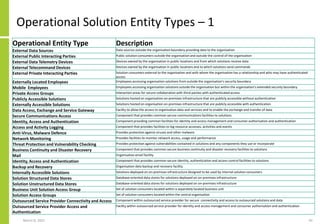
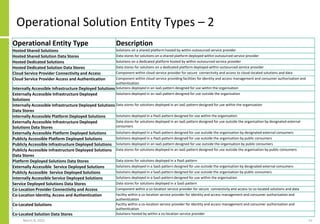
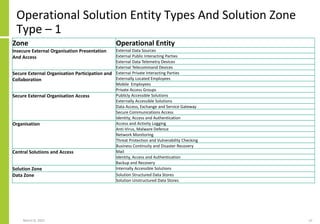
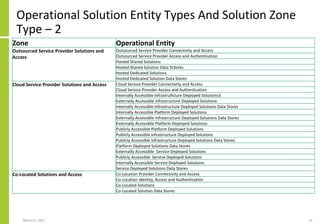
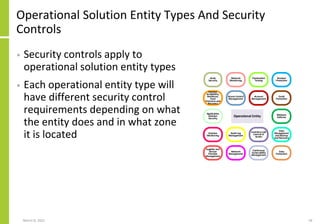
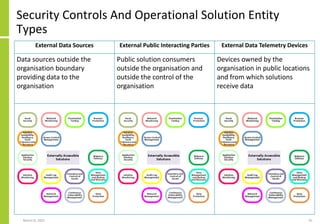
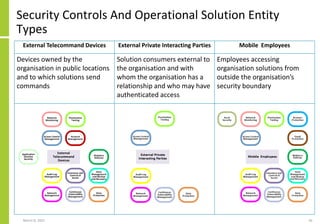
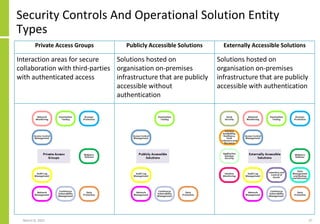
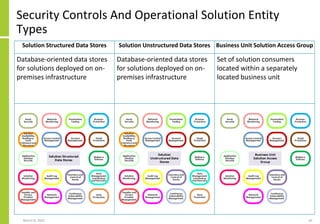
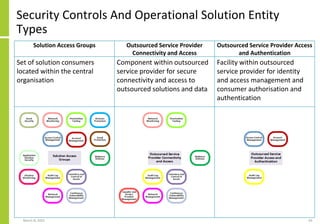
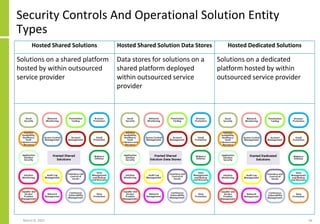
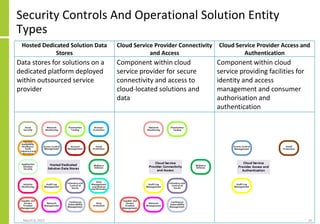
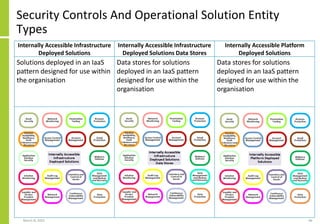
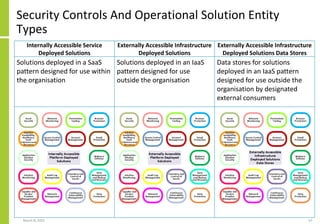
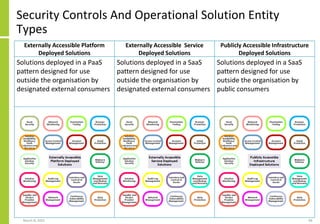
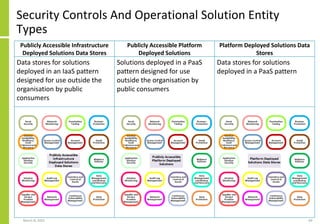
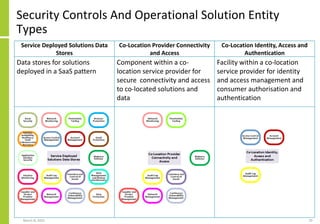
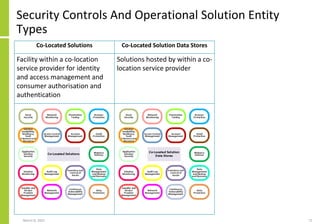
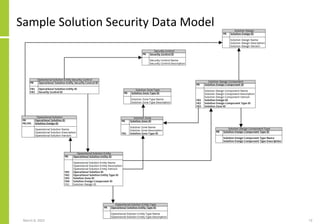
The document proposes a core and extended model for embedding security within technology solutions. The core model maps out solution components, zones, standards and controls. It shows how solutions consist of multiple components located in zones, with different standards applying. The extended model adds details on security control activities and events. Solution security is described as a "wicked problem" with no clear solution. New technologies introduce new risks to solutions across dispersed landscapes. The document outlines types of solution zones and common component types that make up solutions.