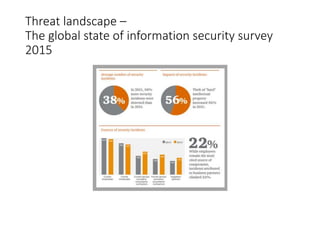
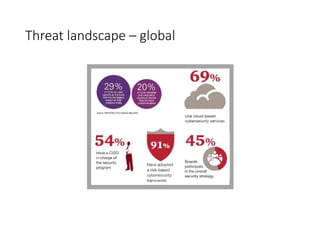
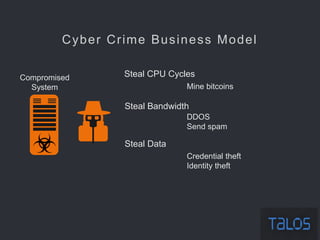
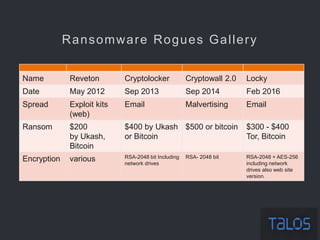
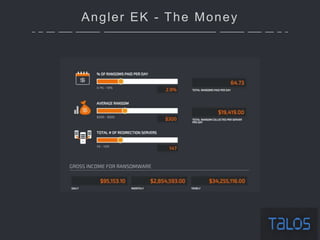
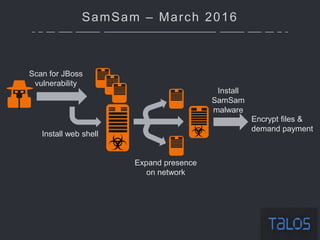
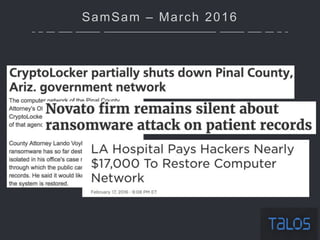
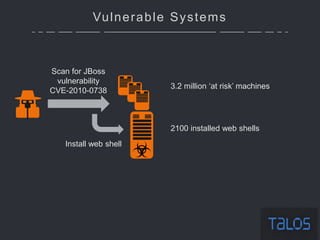
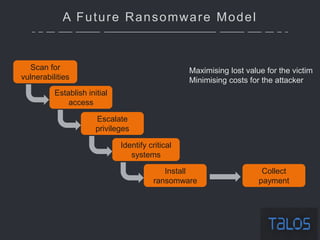
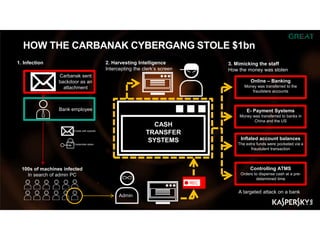
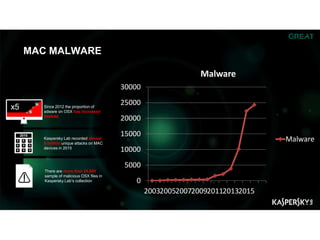
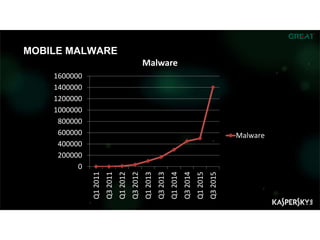
The document summarizes an ICSA Technology Conference focused on cyber security that was held on Friday, November 4, 2017. The conference included chair remarks, discussions on building business confidence in cyber security, the evolving cyber threat landscape, ransomware and cyber extortion, and how to respond to a cyber security breach. Speakers addressed questions organizations have about current cyber risk levels and how to understand and address cyber threats through practical measures.