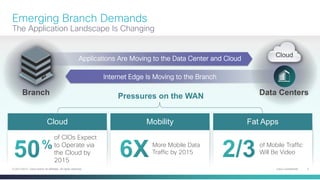
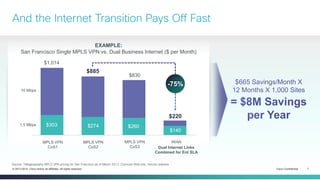
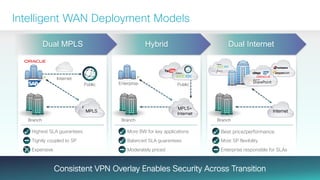
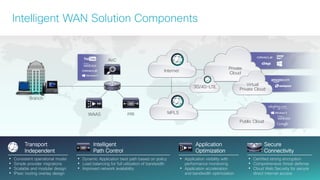
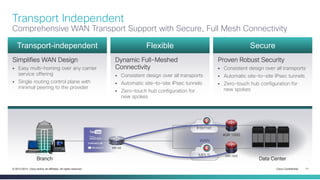
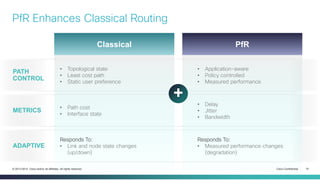
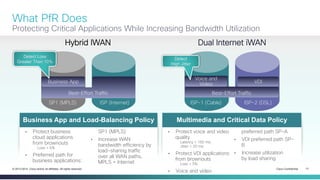
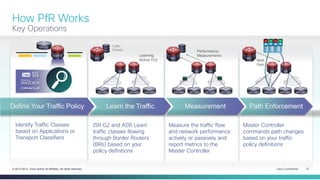
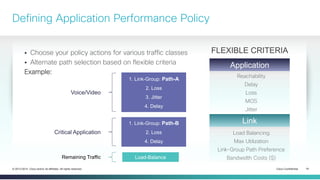
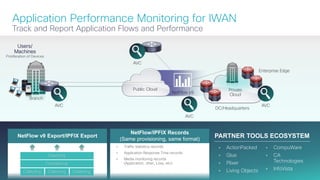
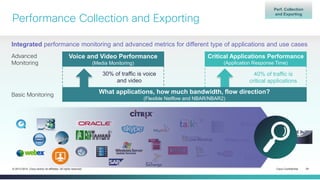
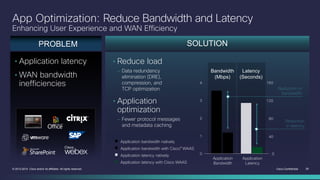
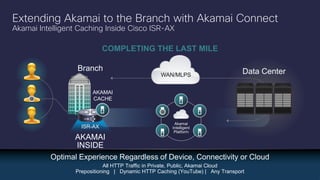
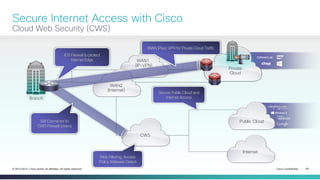
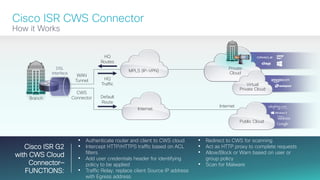
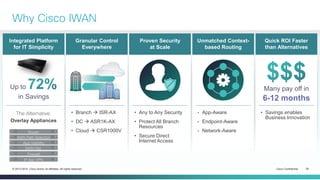
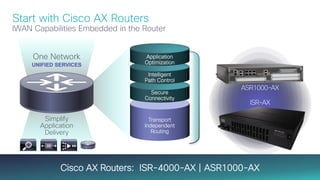
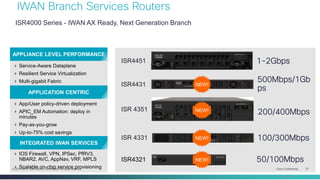
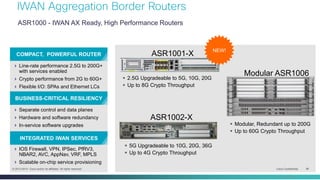
The document provides a technical overview of Cisco's Intelligent WAN (iWAN) solutions, focusing on its deployment models, application optimization, and secure connectivity. iWAN addresses the evolving demands of branch networks by offering a transport-independent design and advanced path control for improved application performance and security. It emphasizes cost savings and operational simplicity through integrated management tools and comprehensive monitoring capabilities.