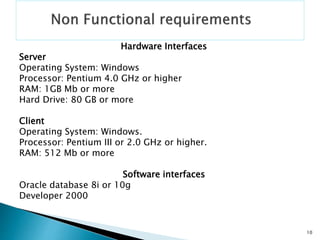
This document provides an overview of a presentation on software development methodologies for a library management system. It outlines the domain, actors, functional and non-functional requirements, use cases diagram, classes, class diagram, objects, and class/object relationships that will be discussed. The presentation will cover adding, updating, deleting articles and inquiring about members and articles. It will also discuss user authentication, searching and requesting articles, and checking accounts.