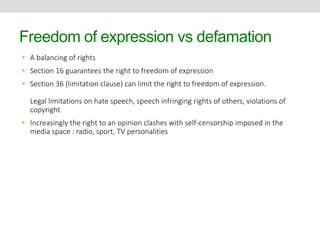
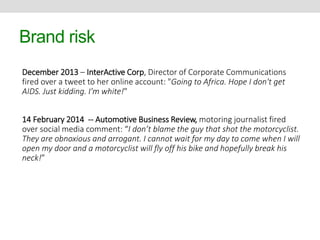
This document discusses social media risks and related laws. It covers how conversations on social media can become publications with legal implications. Some key topics discussed include privacy risks from sharing personal information and companies monitoring employees' social media, intellectual property risks like copyright infringement, and defamation risks from making untrue statements about others. The document also examines how various laws like privacy acts, harassment laws, and intellectual property laws apply in the social media context.





















![Legal developments
• South African case law
• Sedick and Another v Krisray (Pty) Ltd (2011) 8 BALR 879 (CCMA); and
• Fredericks v Jo Barkett Fashions [2011] JOL 27923 (CCMA)
• Media Workers Association of SA obo Mvemve v Kathorus Community Radio (2010) 31 ILJ
2217 (CCMA)
However, normal rules of substantive and procedural fairness do apply
• Smith v Partners in Sexual Health (non-profit) (2011) 32 ILJ 1470 (CCMA)
• LRA : employers may not prevent an employee from exercising rights it confers
• The National Labour Relations Board regards SM policies as potentially chilling on
employees’ rights to engage in activity to improve working conditions
• In August the FPB announced it will be considering “mechanisms” to regulate online
and new media content by 2017.](https://image.slidesharecdn.com/socialmediapresentation-141017034203-conversion-gate01/85/Social-Media-Legal-Risk-26-320.jpg)