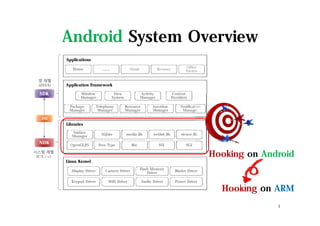
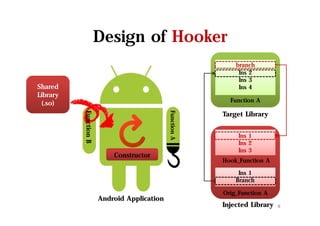
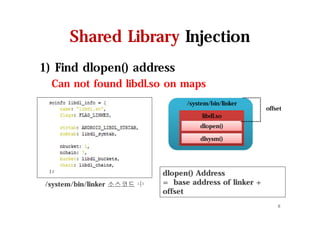
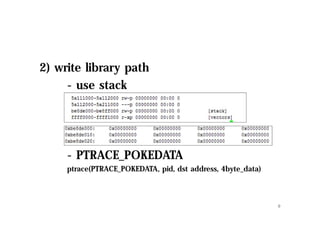
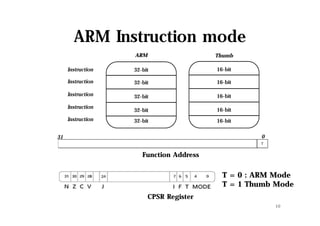
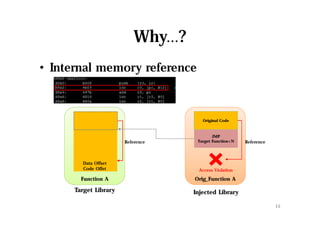
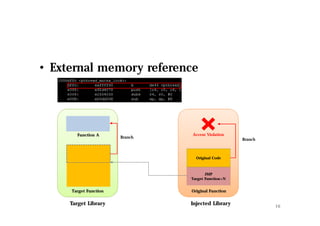
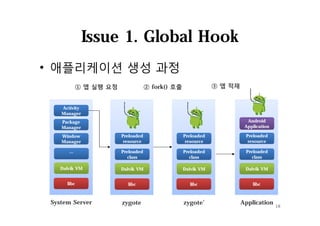
The document discusses hooking techniques in Android systems, specifically focusing on ARM architecture and shared library injection. It outlines the steps for finding, modifying, and using hooks in target libraries and applications, including the use of ptrace and dlopen for library injection. The presentation also covers the process of application creation in Android and provides details on function hooking and its implementation.




![3) Call dlopen() ß Thumb
Debugger Application
Backup Register
Values
Set Breakpoint at Next Instruction
Change Register
Values• pc = dlopen() addr
• r0 = stack addr
• r1 = 0
• lr = next instruction’s
addr (pc)
Restore Registers Values,
Remove Breakpoint
Debugger Applicatio
n
Backup Register
Values
Overwrite Code at Next Instruction
Change Register
Values• pc = pc+4
• r0 = stack addr
• r1 = 0
• lr = next instruction’s
addr (pc)
Restore Registers Values,
Restore Code ,
Remove Breakpoint
• break
• ldr pc, [pc, #0]
• 0x0
• dlopen() address
Thumb 모드 ARM 모드
11](https://image.slidesharecdn.com/2014codeengnconference10hookingonandroid-140713113701-phpapp02/85/2014-CodeEngn-Conference-10-Hooking-on-Android-11-320.jpg)
![4) result
Useage : injector [pid] [Library Full Path]
12
끝](https://image.slidesharecdn.com/2014codeengnconference10hookingonandroid-140713113701-phpapp02/85/2014-CodeEngn-Conference-10-Hooking-on-Android-12-320.jpg)

![2) Install Hooker
14
Target Library
Injected Library
LDR PC, [PC]
Function A
NOP
Hook_FunctionA Addr
Ins 4
Ins 1
Ins 2
Ins 1
Ins 2
Ins 3
Branch
Hook_Function A
Orig_Function A
Target Library
Injected Library
Function A
Push {r5}
add r5, pc, #4
ldr r5, {r5}
bx r5
Hook_FunctionA Addr
Ins 7
pop {r5}
Ins 1
Ins 2
Ins 1
Ins 6
Branch
Hook_Function A
Orig_Function A
ARM->ARM Thumb->ARM](https://image.slidesharecdn.com/2014codeengnconference10hookingonandroid-140713113701-phpapp02/85/2014-CodeEngn-Conference-10-Hooking-on-Android-14-320.jpg)
![Solution
• 귀찮으니 그냥 복사하자…
17
Target Library
Injected Library
LDR PC, [PC]
Function A
NOP
Hook_FunctionA Addr
Ins 4
Ins 1
Ins 2
Hook_Function A
Copied Target Library
Function A
Ins 1
Ins 2
Ins 3
Ins 4
Function Pointer](https://image.slidesharecdn.com/2014codeengnconference10hookingonandroid-140713113701-phpapp02/85/2014-CodeEngn-Conference-10-Hooking-on-Android-17-320.jpg)

![How to use
• download : http://bananapayload.org
20
[library path] [Name / Offset] [Function Type]
/system/lib/libc.so malloc void *malloc(size_t size)
/system/lib/test.so 0x400 void sub400(int, int)
./ genLibrarySource [define File] [output path]
Define Format
Source Code
Edit Source & Edit makefile & make library
Useage : injector [pid] [Library Full Path] Hook Success](https://image.slidesharecdn.com/2014codeengnconference10hookingonandroid-140713113701-phpapp02/85/2014-CodeEngn-Conference-10-Hooking-on-Android-20-320.jpg)

