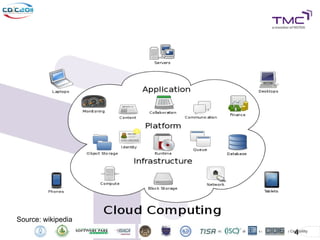
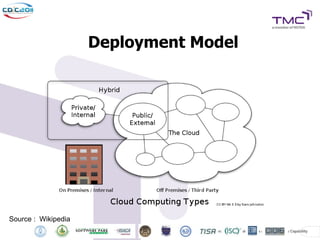
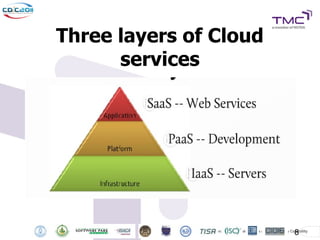
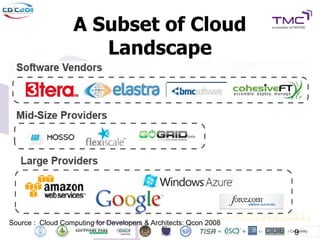
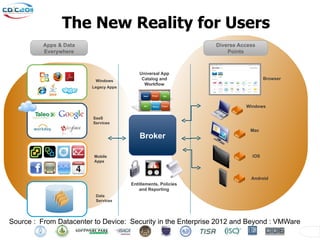
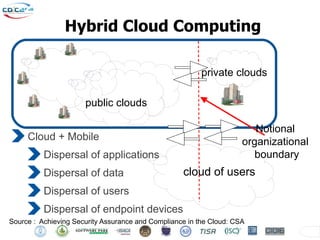
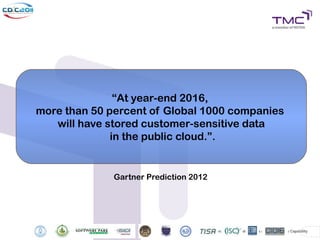
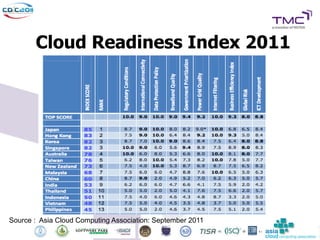
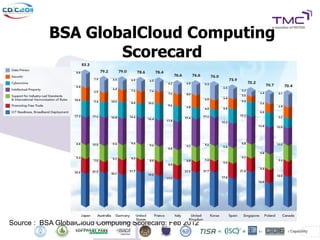
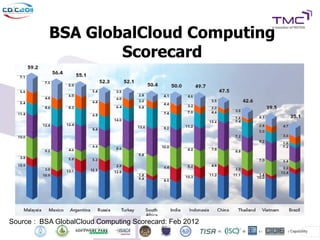
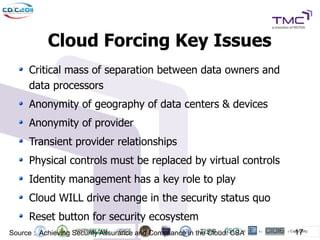
The Cyber Defense Initiative Conference 2011 discussed privacy and security challenges in the digital age, focusing on the impact of cloud computing on data management and security. Notably, it highlighted that over 50% of Global 1000 companies will store sensitive data in the public cloud by 2016, alongside key issues of governance, compliance, and the need for improved security measures. The document underlines the evolving relationship between data owners and providers amid increasing reliance on cloud services.