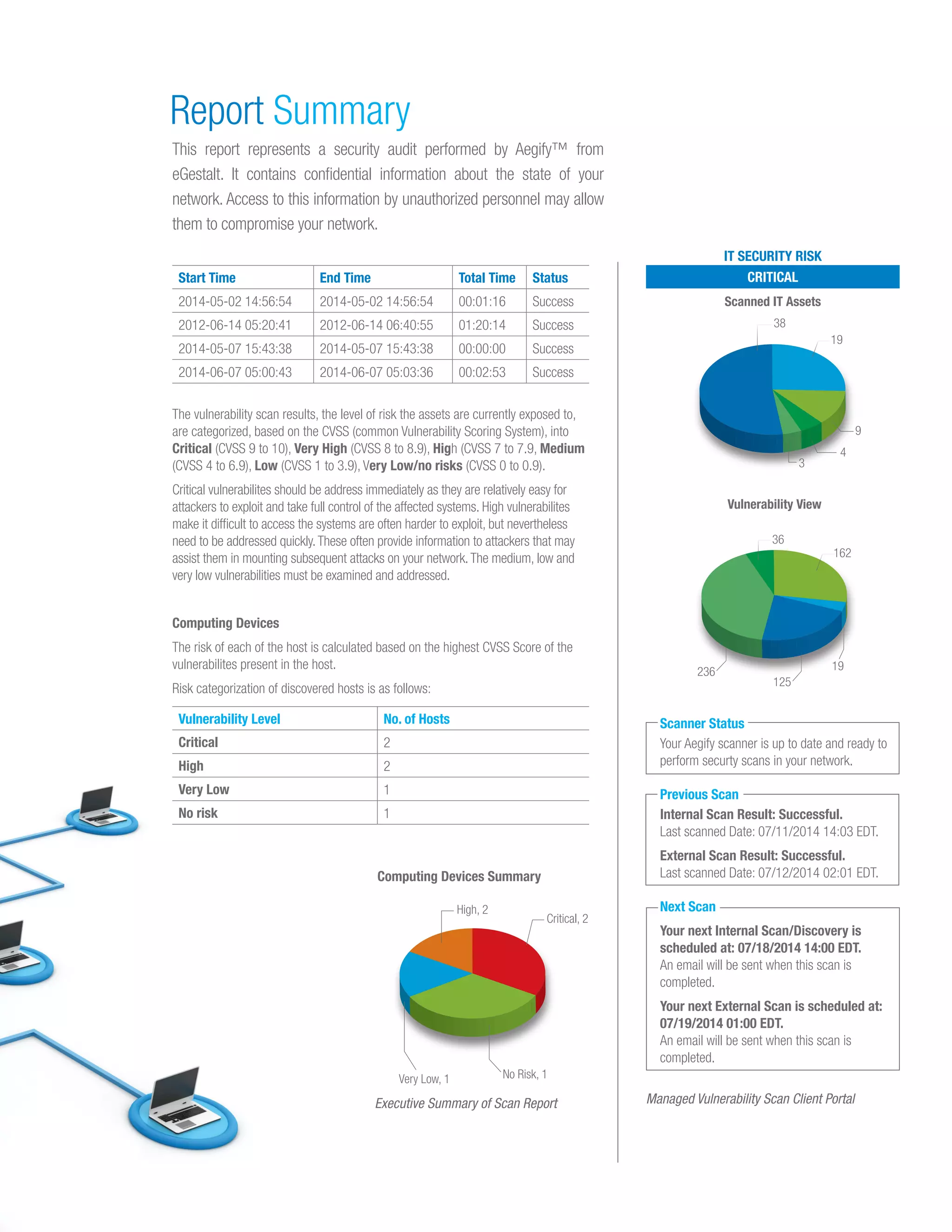
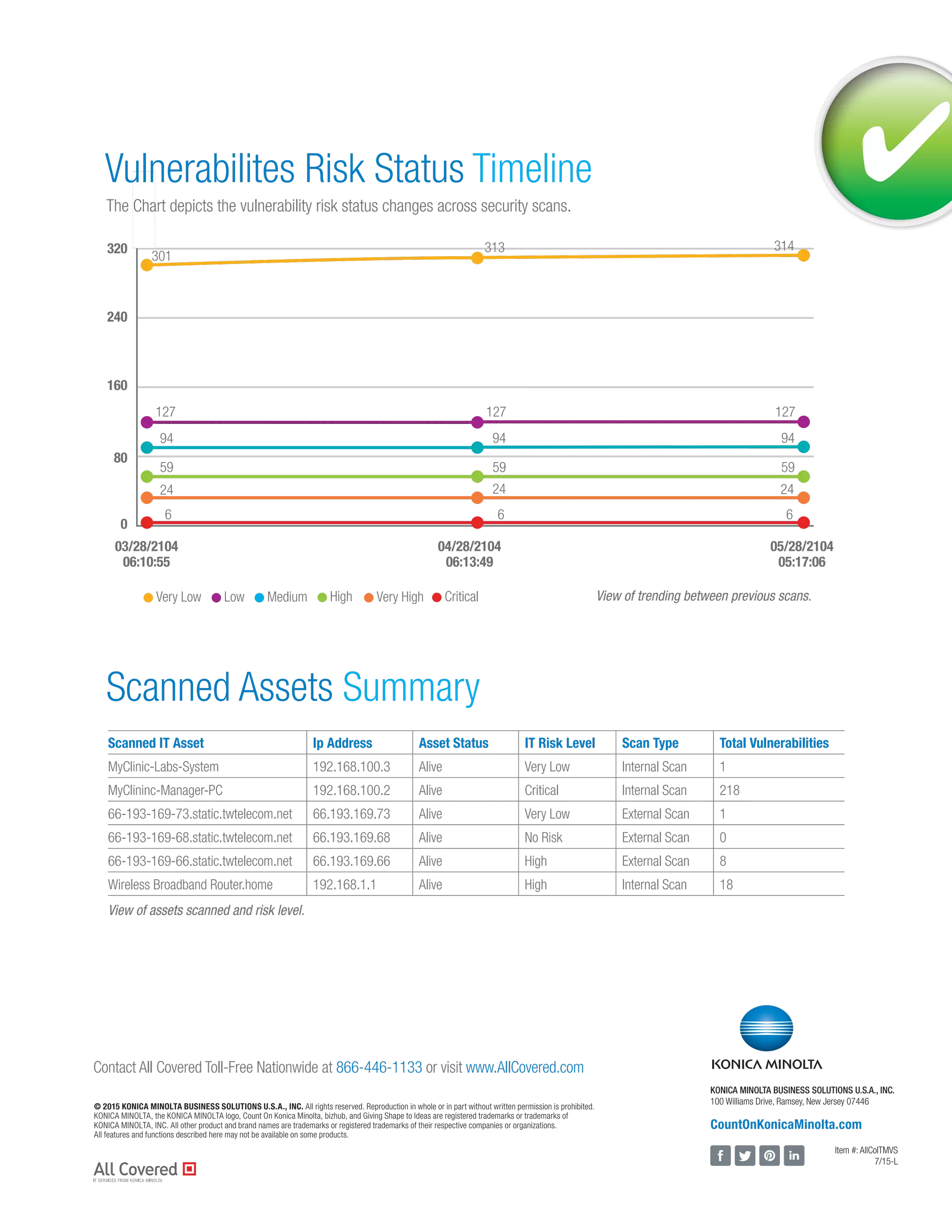
All Covered's managed vulnerability scan service offers comprehensive vulnerability assessments for networks and applications, both on-premise and in the cloud. It includes internal and external scanning, asset discovery, and detailed reporting with remediation recommendations. The service helps organizations maintain a current understanding of their security posture and meet regulatory compliance requirements.