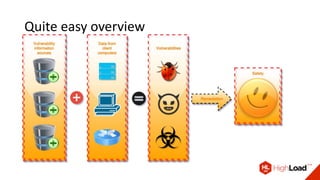
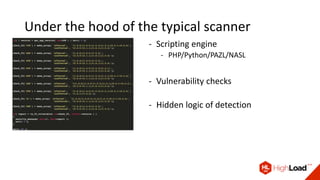
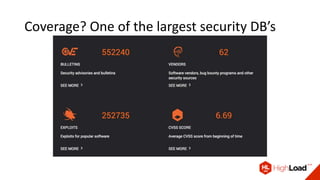
- Vulners is a vulnerability intelligence platform that aggregates data from over 60 sources and provides a fast search engine and APIs for accessing this data.
- It aims to standardize vulnerability data into a unified model to make it more useful for security tools and analytics. This includes normalizing vendor security advisories, exploits, and other informational resources.
- In addition to search, it offers features like vulnerability scanning via APIs, email/RSS subscriptions, and a Telegram bot to provide customized vulnerability awareness services for users. All of its features and data are free to use.


















![Advanced queries
- Any complex query
- title:httpd type:centos order:published last 15 days cvss.score:[7 TO 10]
- Sortable by any field of the model (type, CVSS, dates, reporter, etc)
- Apache Lucene syntax (AND, OR and so on)
- Exploit search by sources and CVE’s
- cvelist:CVE-2014-0160 type:exploitdb
- sourceData:.bash_profile
- sourceData:"magic bytes”](https://image.slidesharecdn.com/vulnerabilityintelligencewithvulners-161108120846/85/Vulnerability-intelligence-with-vulners-com-26-320.jpg)