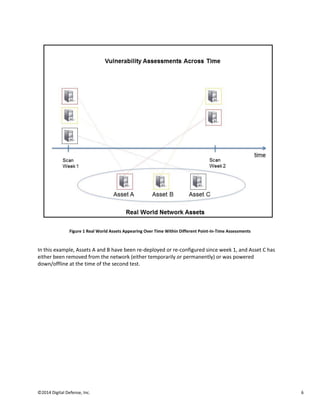
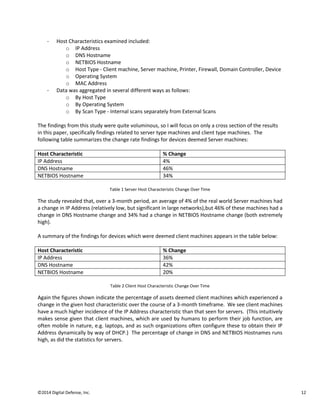
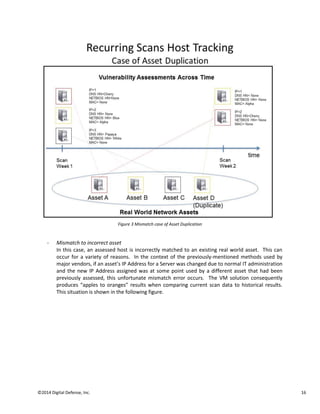
Vulnerability management solutions are flawed due to a lack of advanced network endpoint correlation capabilities. This introduces inaccuracies that leave enterprises at high risk. Most solutions only track 3-5 host characteristics for reconciliation over time, but networks experience around 40% "churn", meaning the characteristics change frequently. This limited tracking leads to misleading scan results, an inaccurate security posture view, and vulnerabilities being missed. Advanced reconciliation is needed to properly relate hosts over multiple scans and manage risk levels across time.