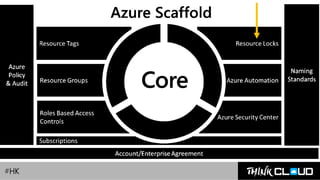
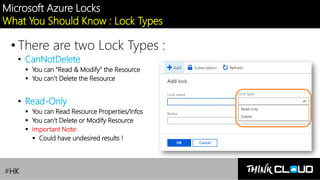
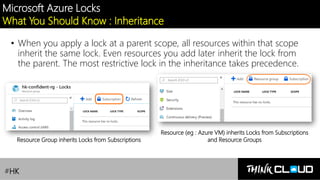
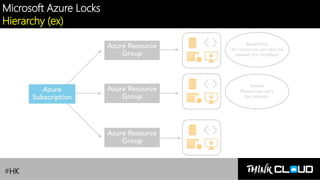
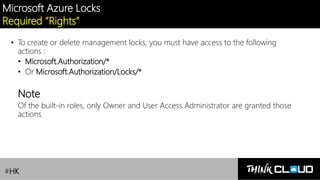
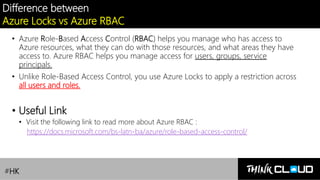
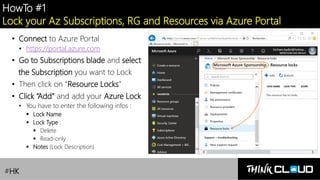
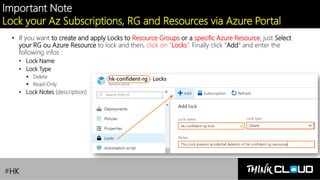
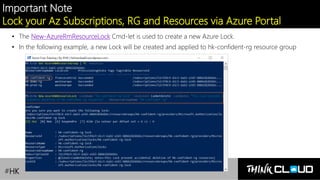
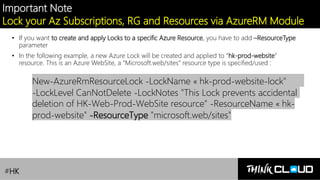
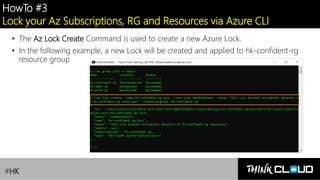
This document provides an overview of Azure locks, highlighting their importance in governance by protecting subscriptions, resource groups, and resources from accidental deletion. It explains the types of locks (cannot delete and read-only), their inheritance properties, and the necessary permissions for implementation, contrasting them with Azure RBAC which manages user access. Additionally, it offers guidance on creating and applying locks using various tools like the Azure portal, PowerShell, and Azure CLI.