Embed presentation
Downloaded 10 times
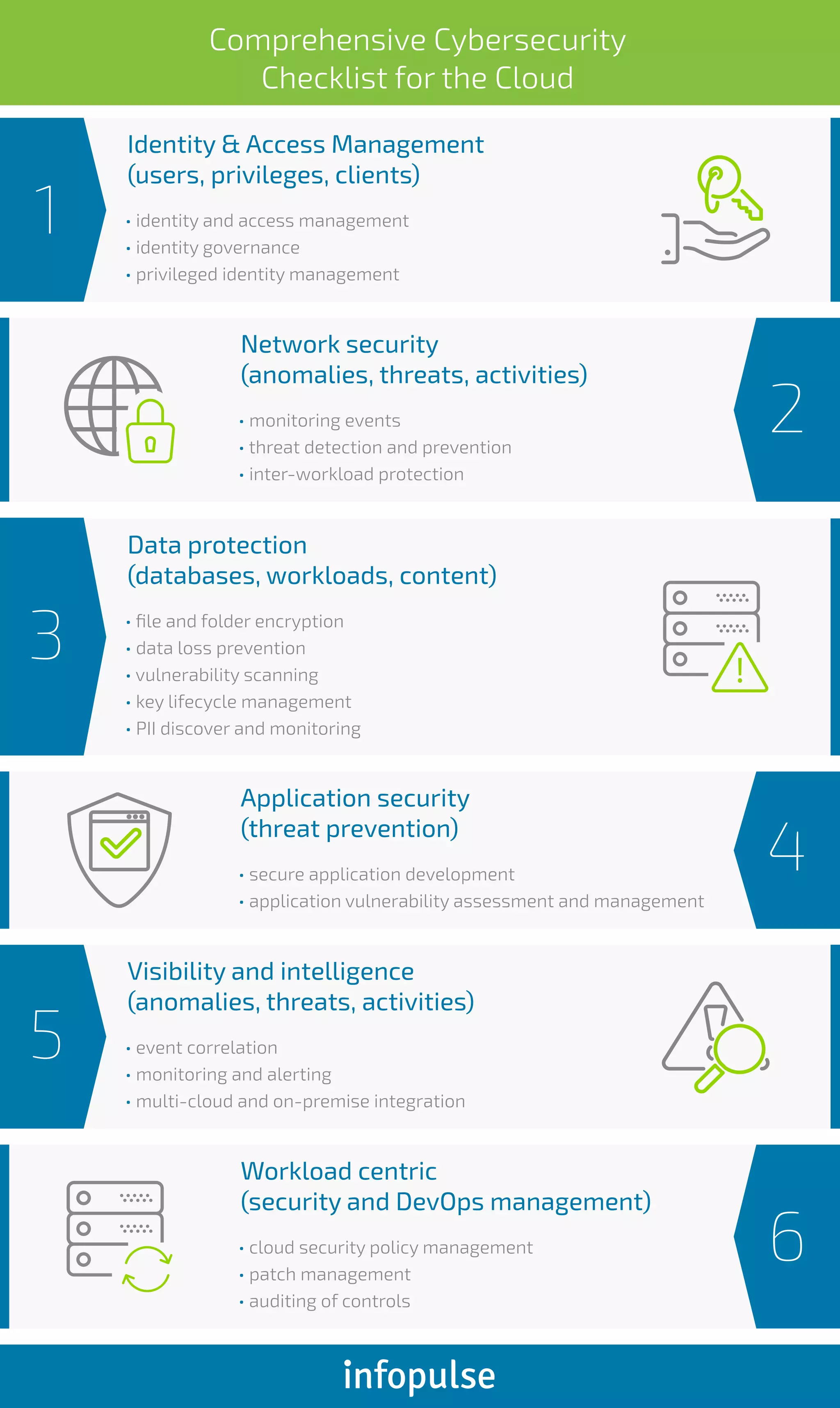

The document outlines a comprehensive cybersecurity checklist, focusing on identity and access management, data protection, visibility and intelligence, application security, and network security for cloud and on-premise workloads. Key areas include privileged identity management, file encryption, anomaly detection, secure application development, and threat prevention. The checklist is aimed at enhancing security measures in a cloud workload-centric environment.
