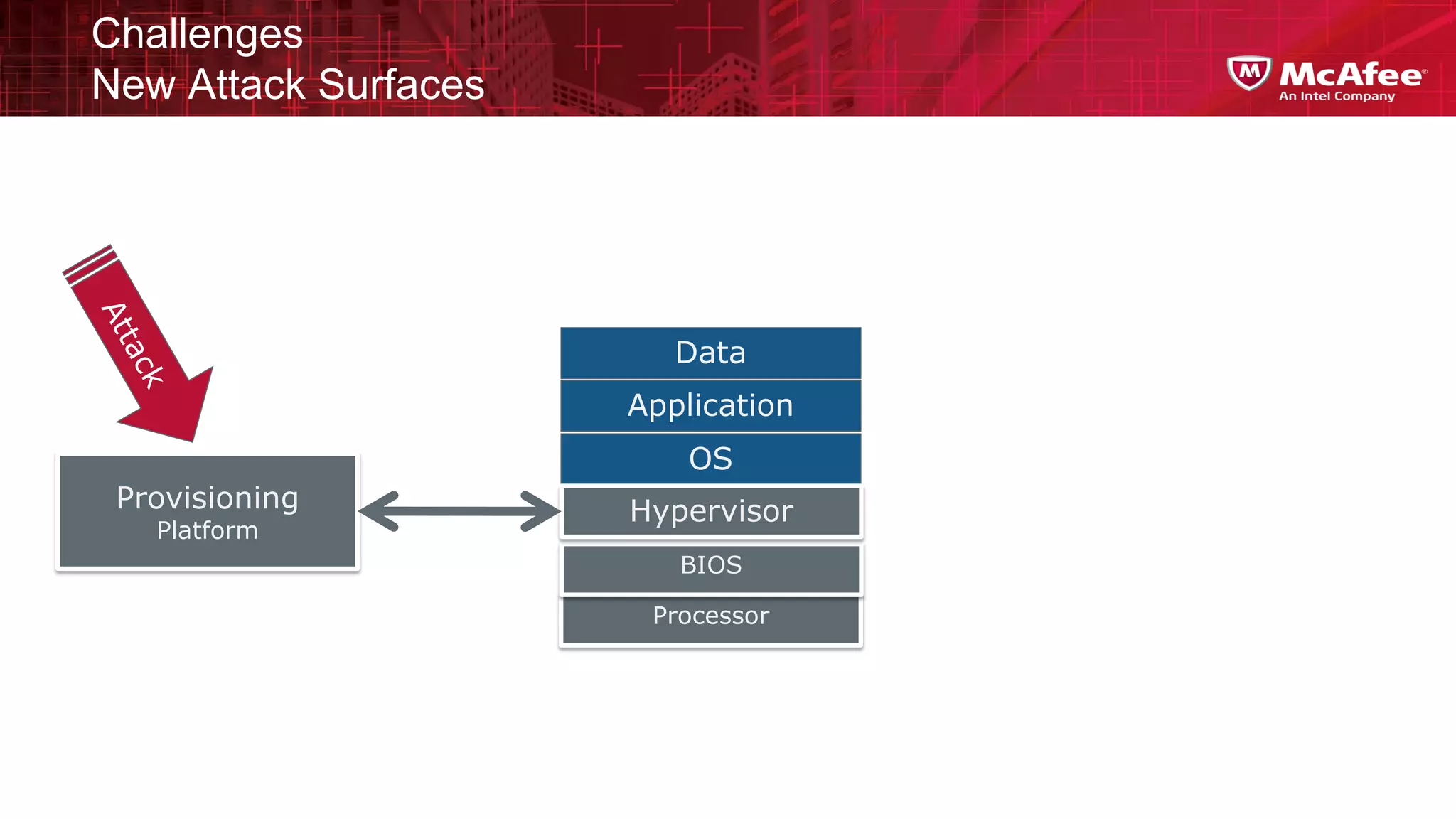
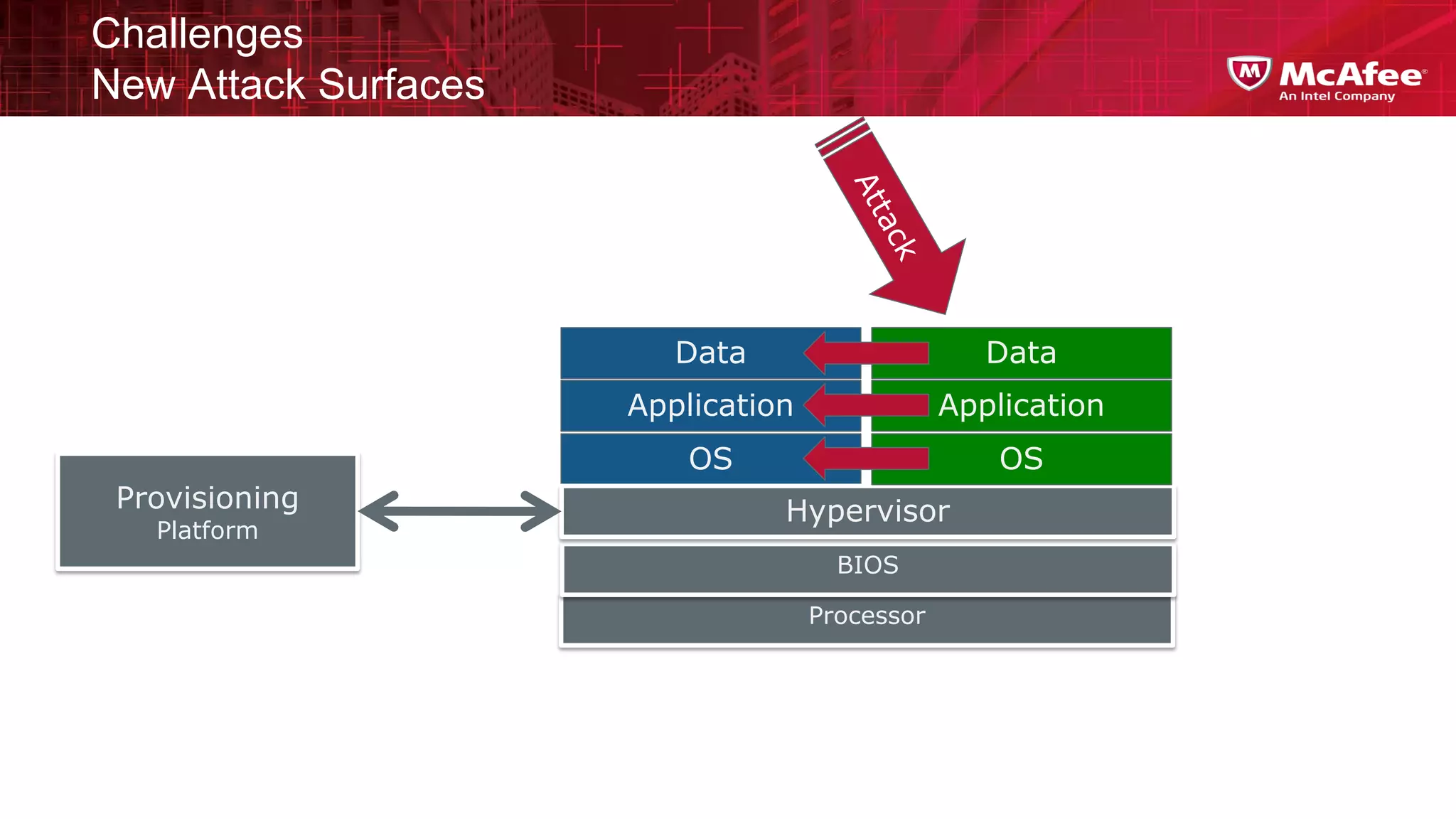
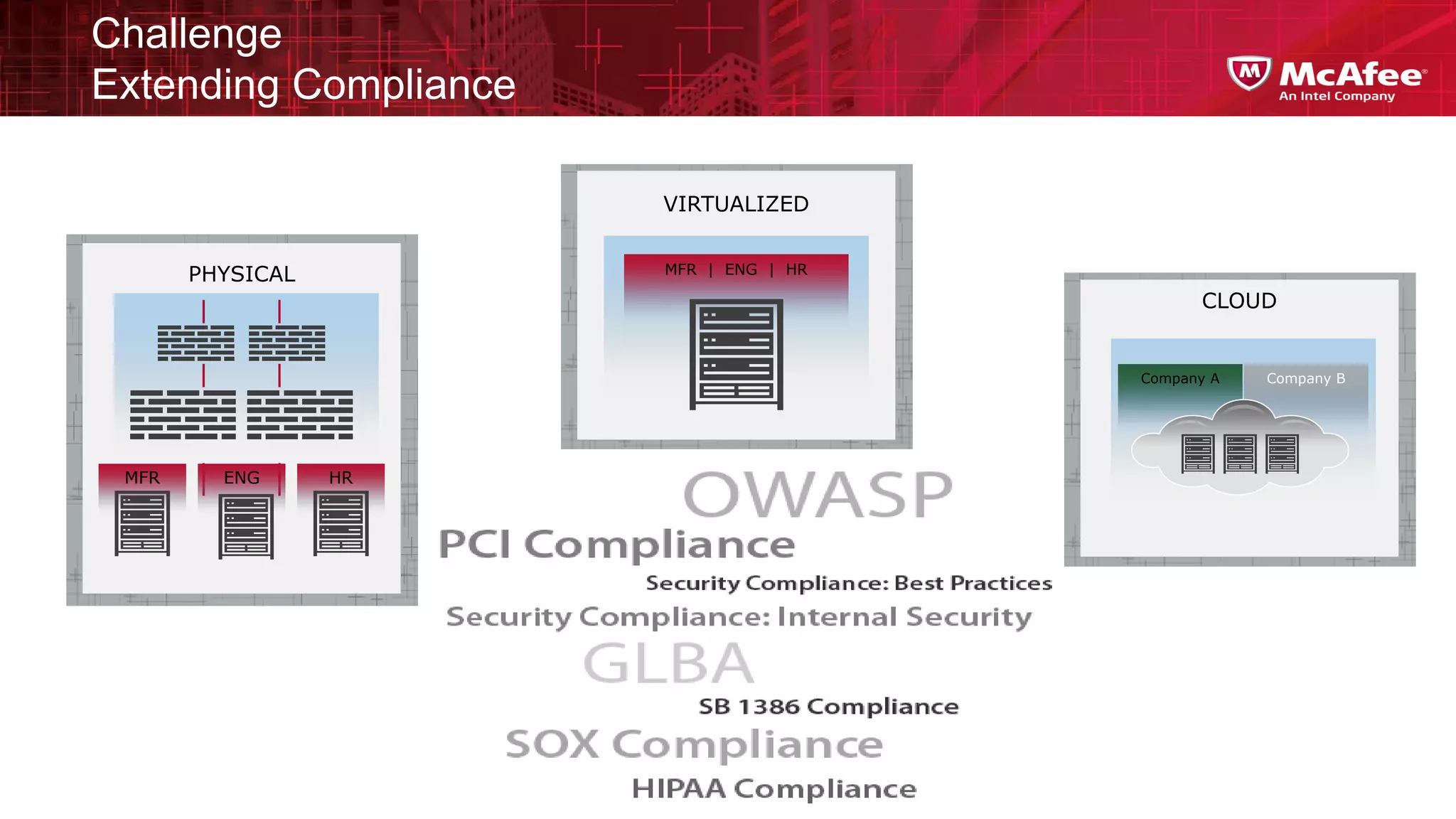
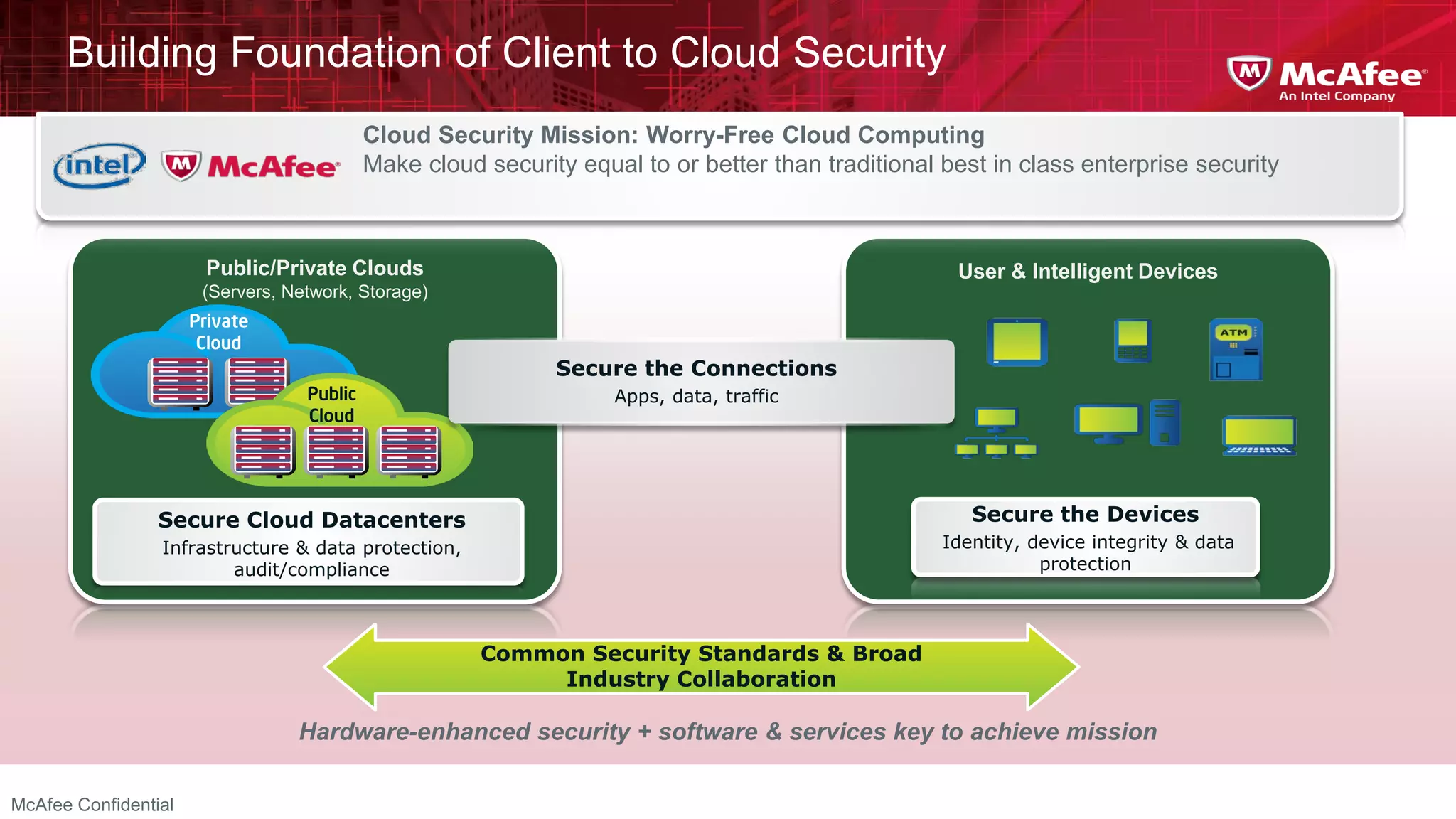
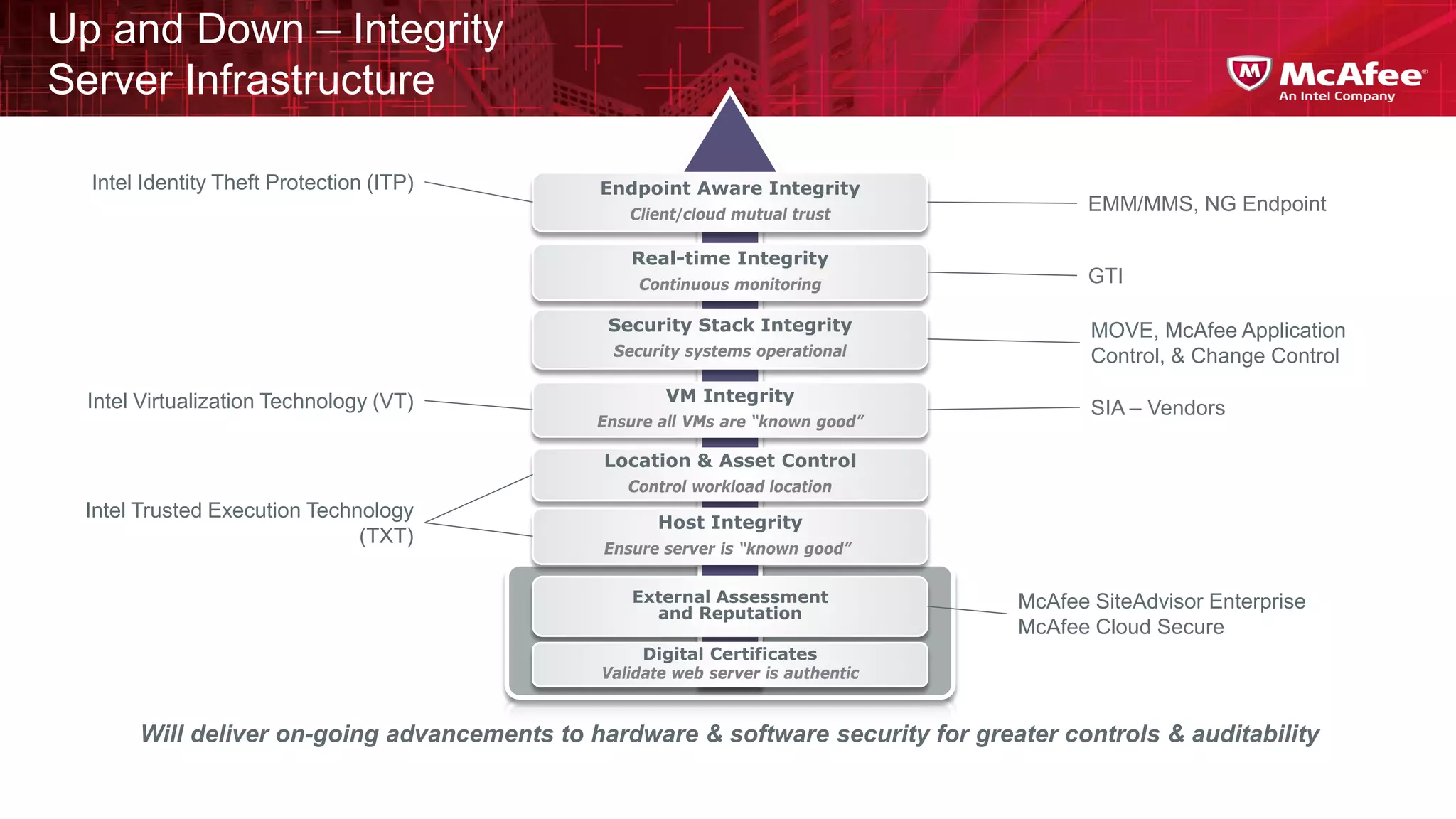
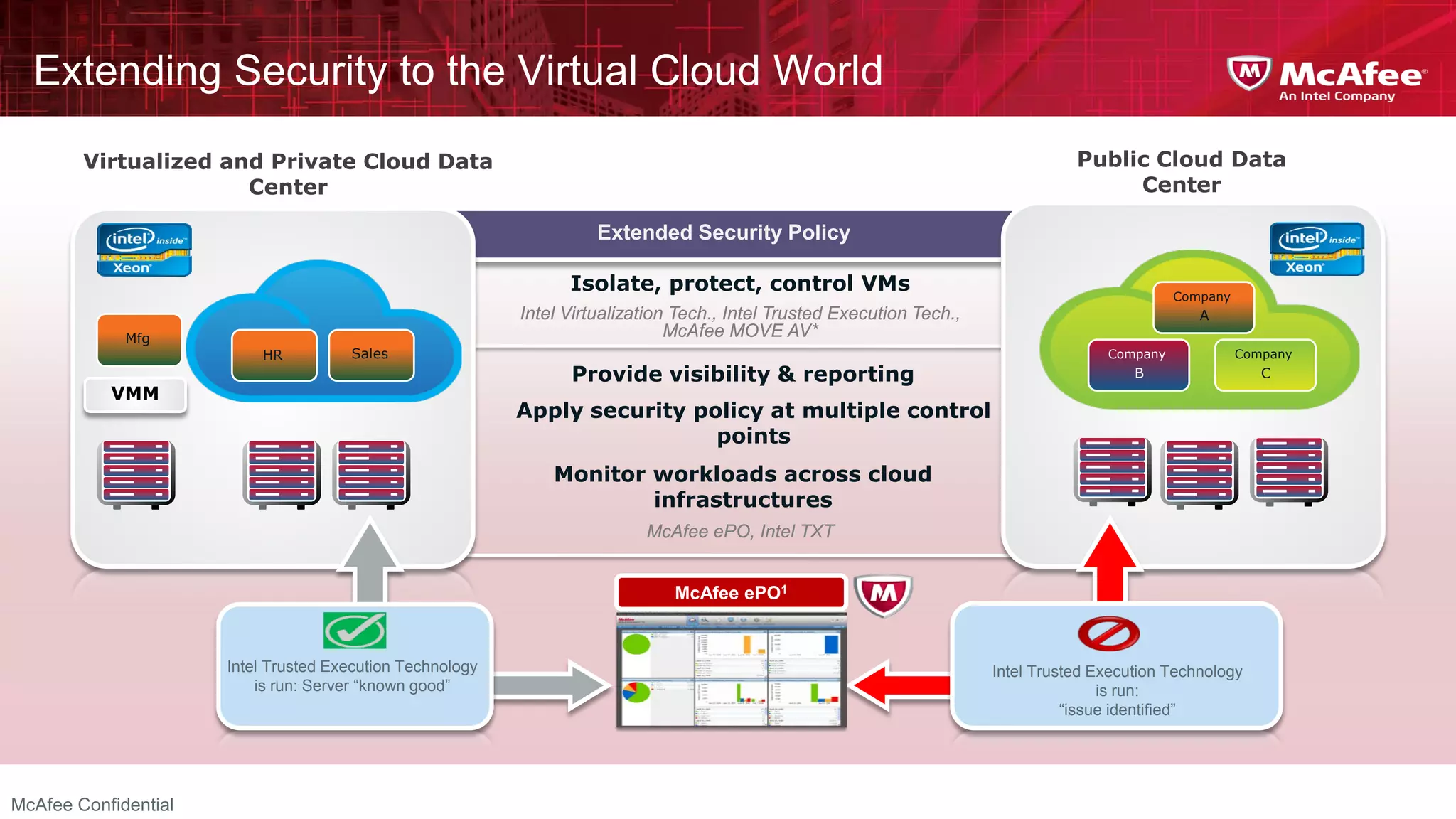
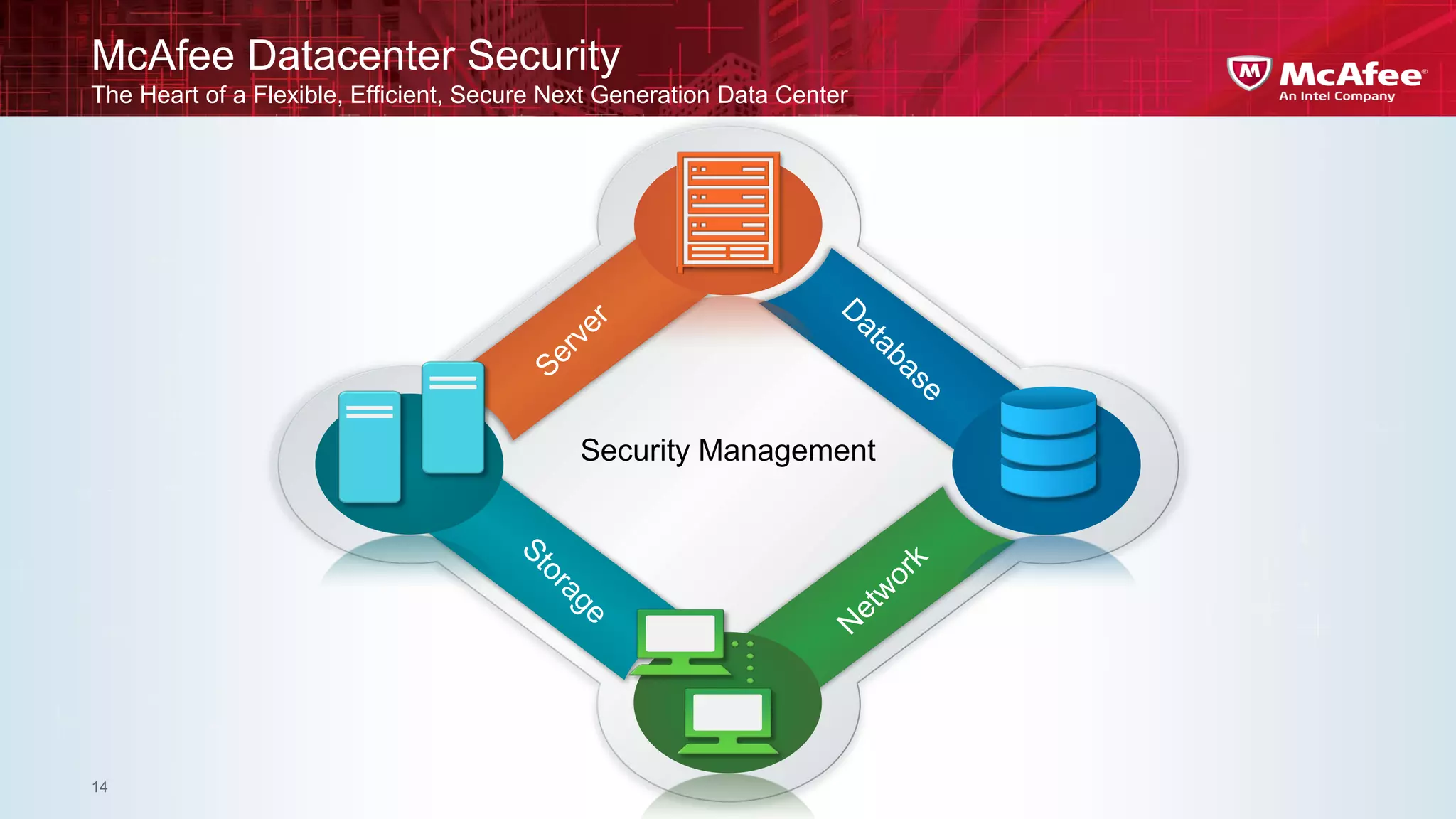
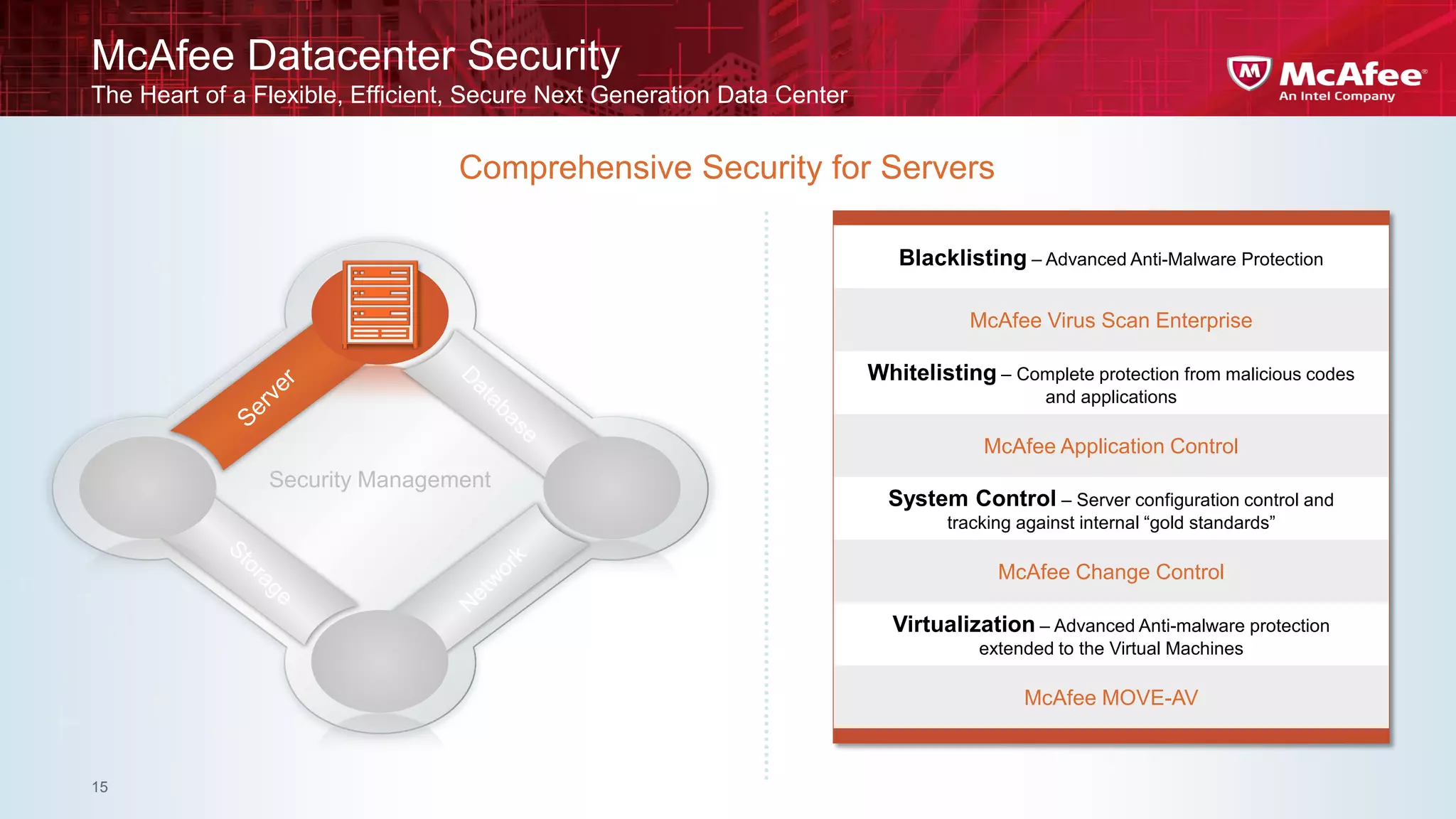
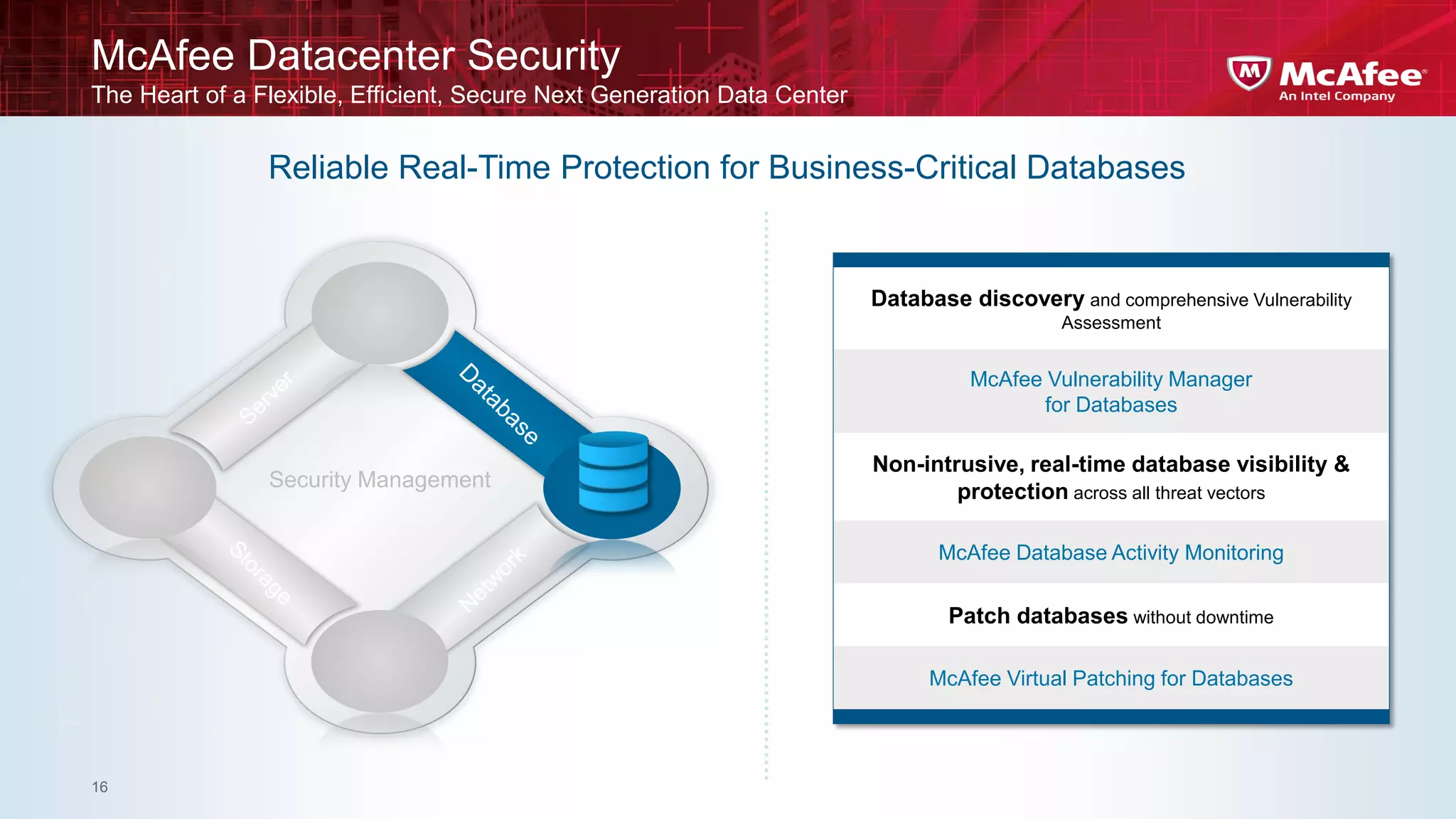
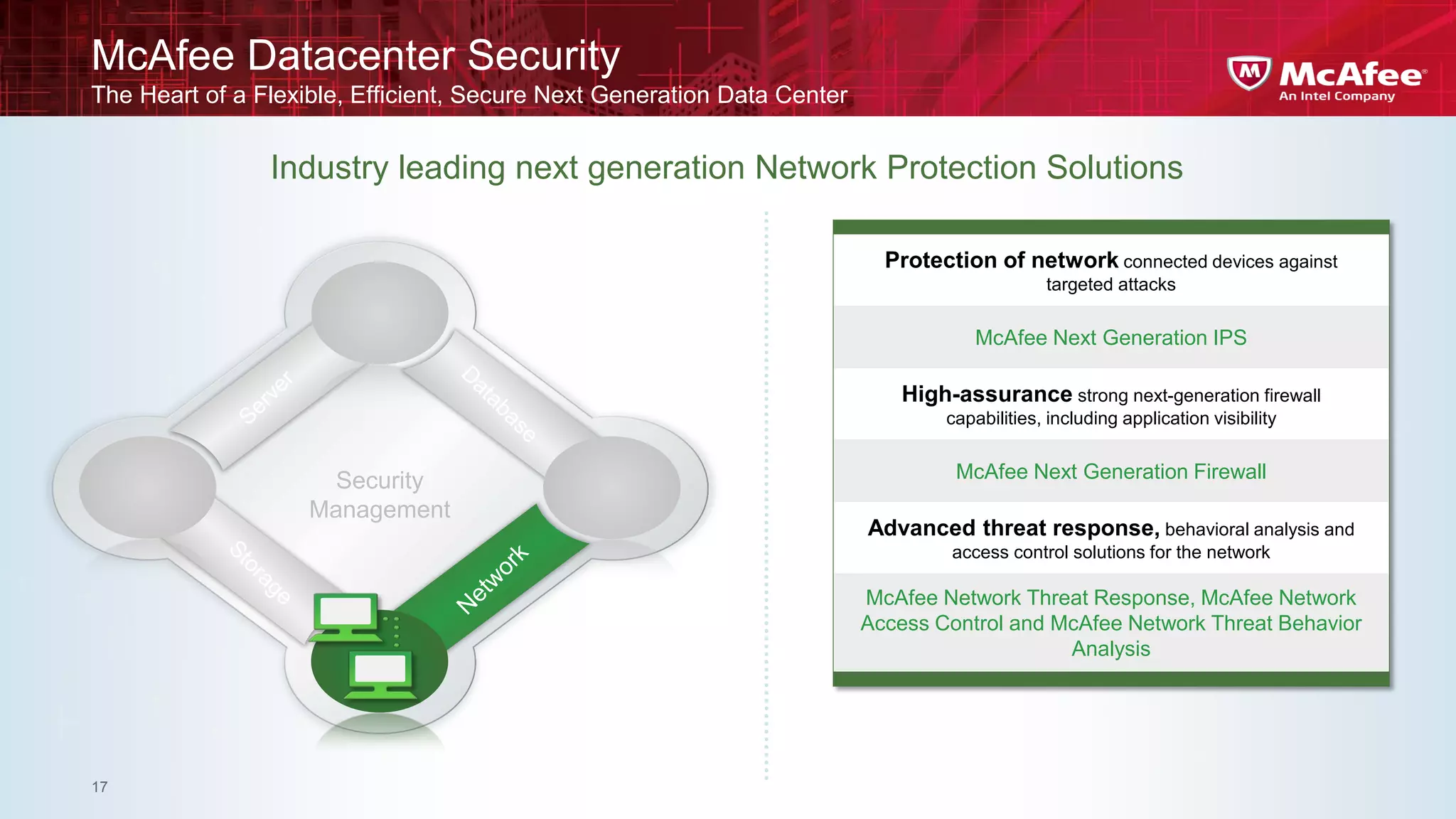
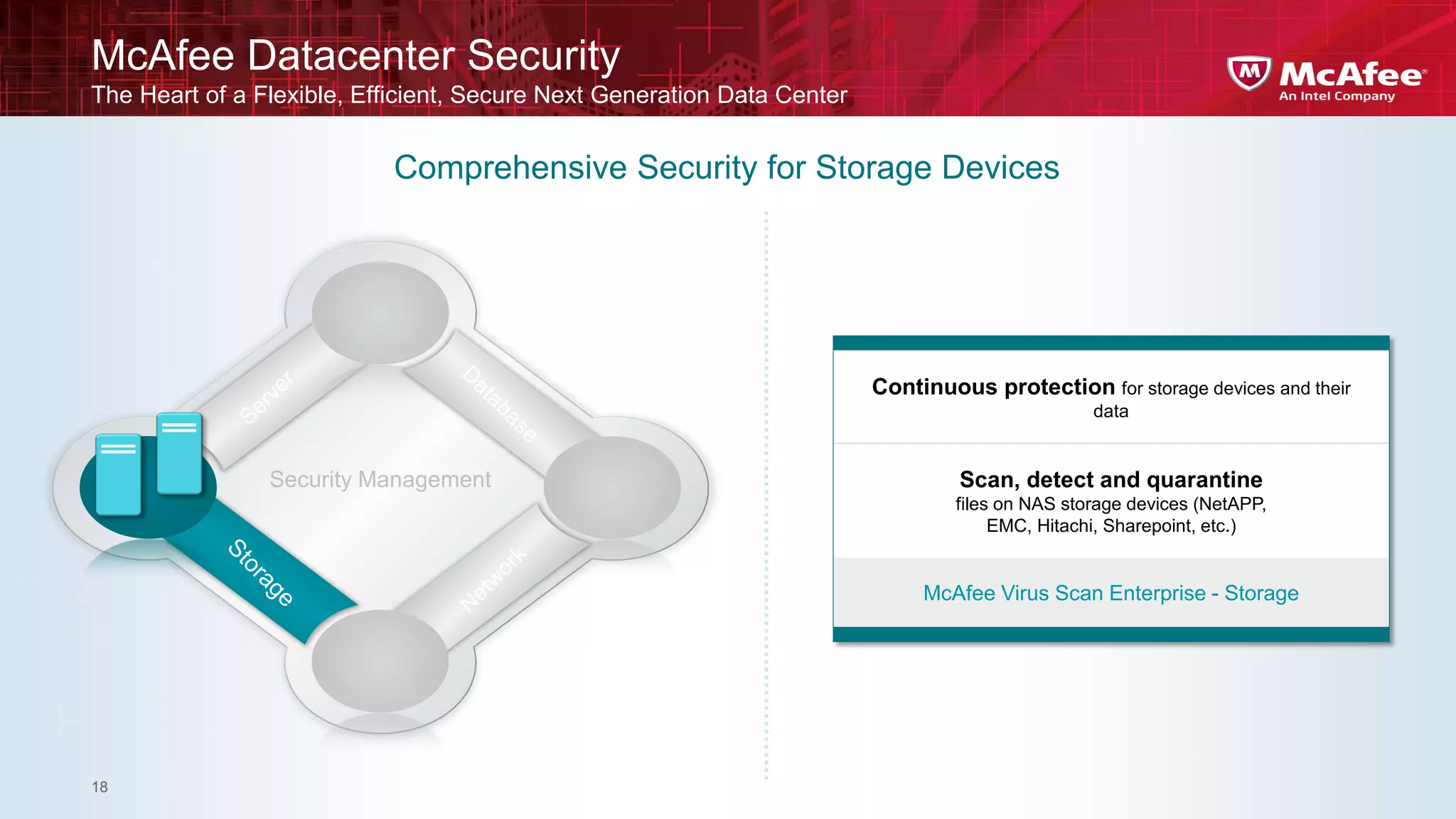
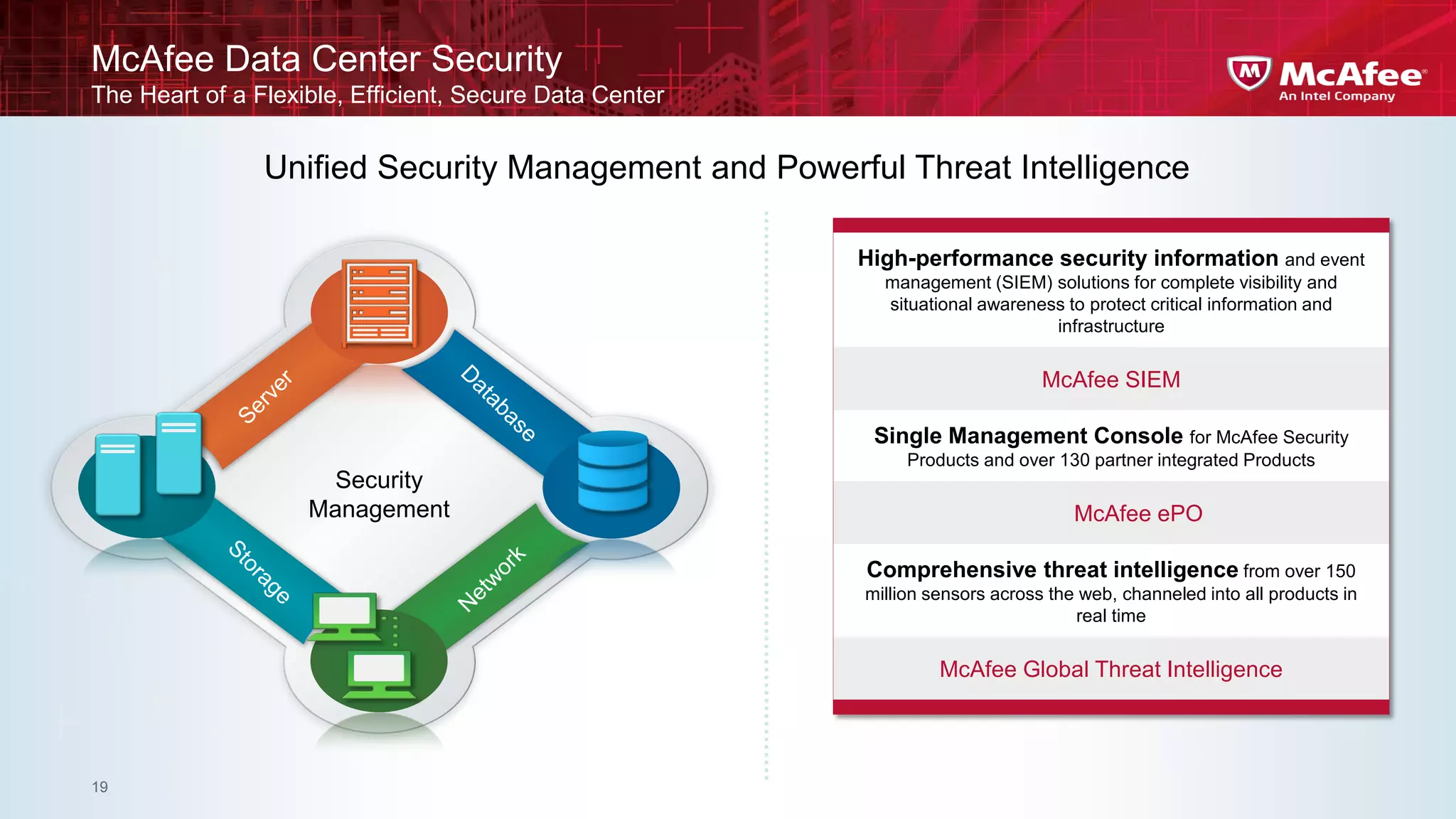
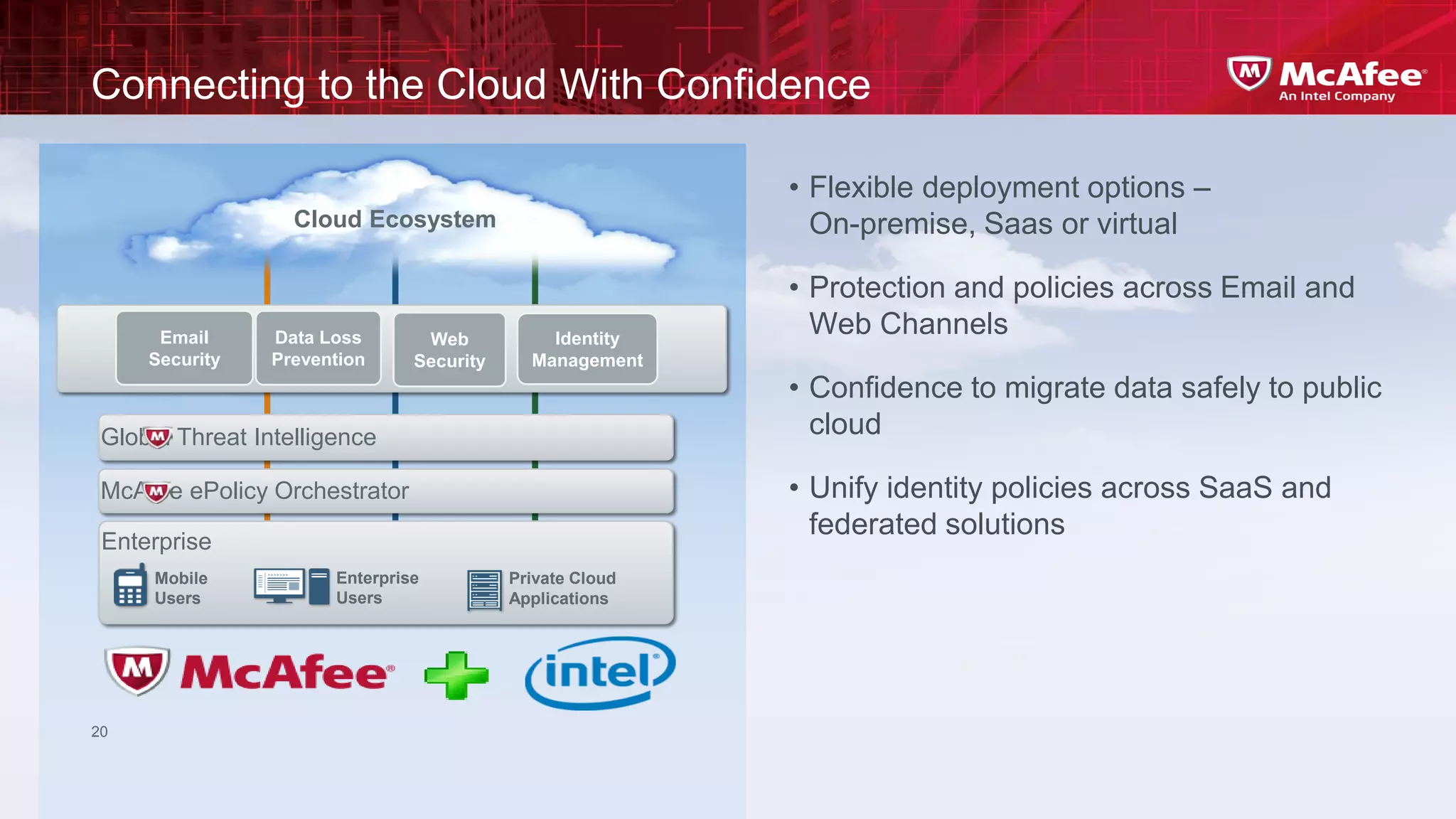
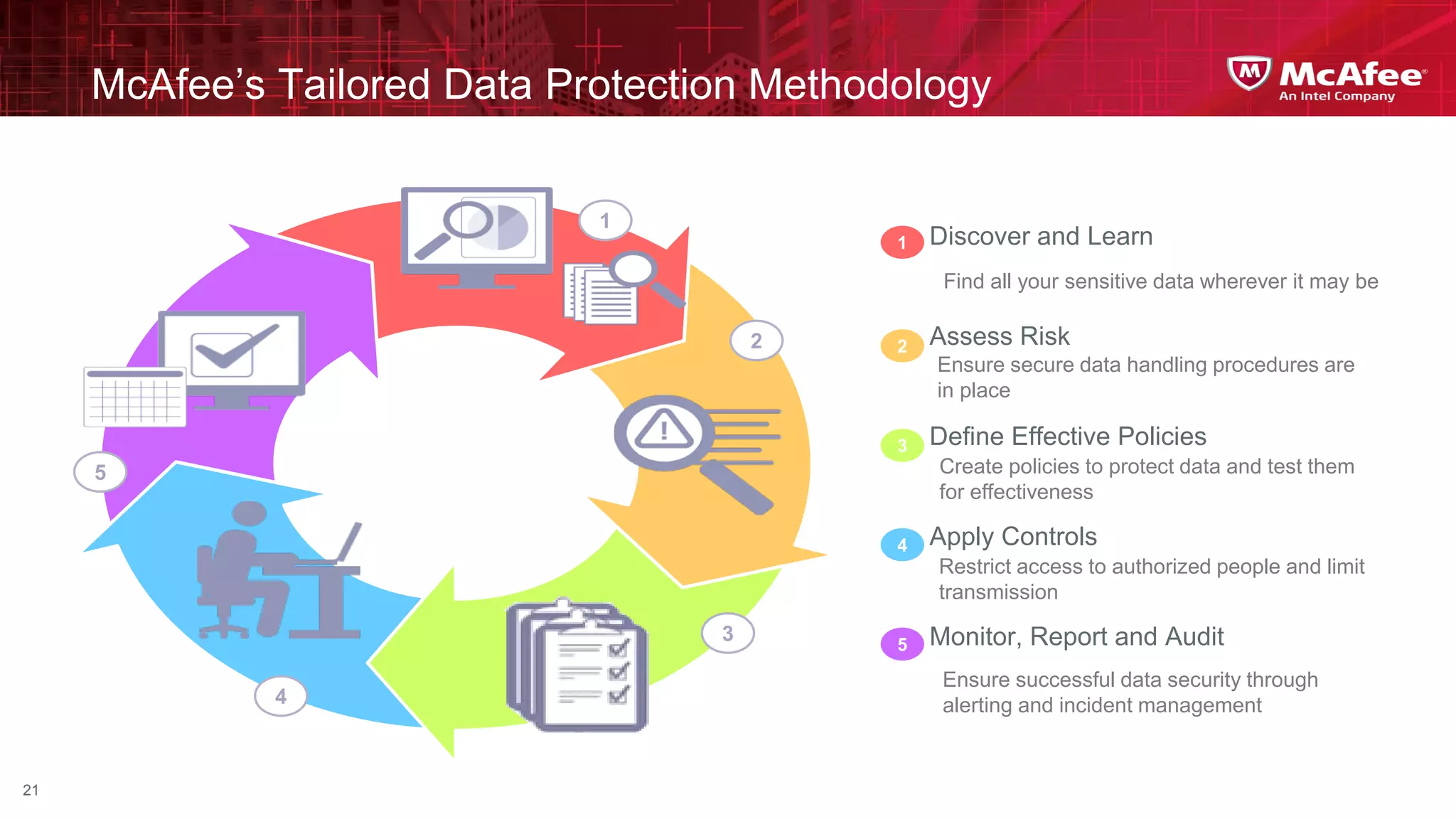
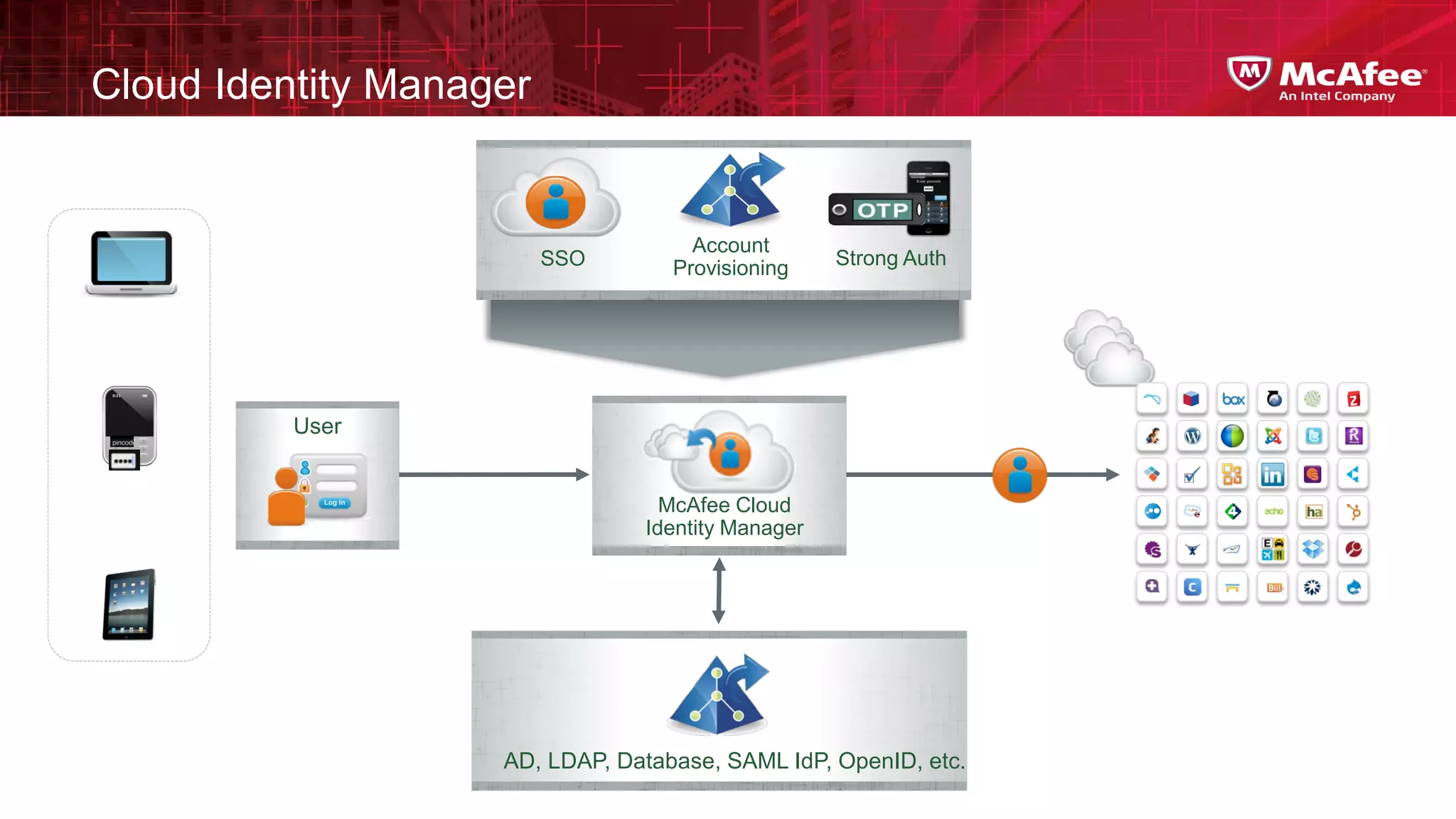
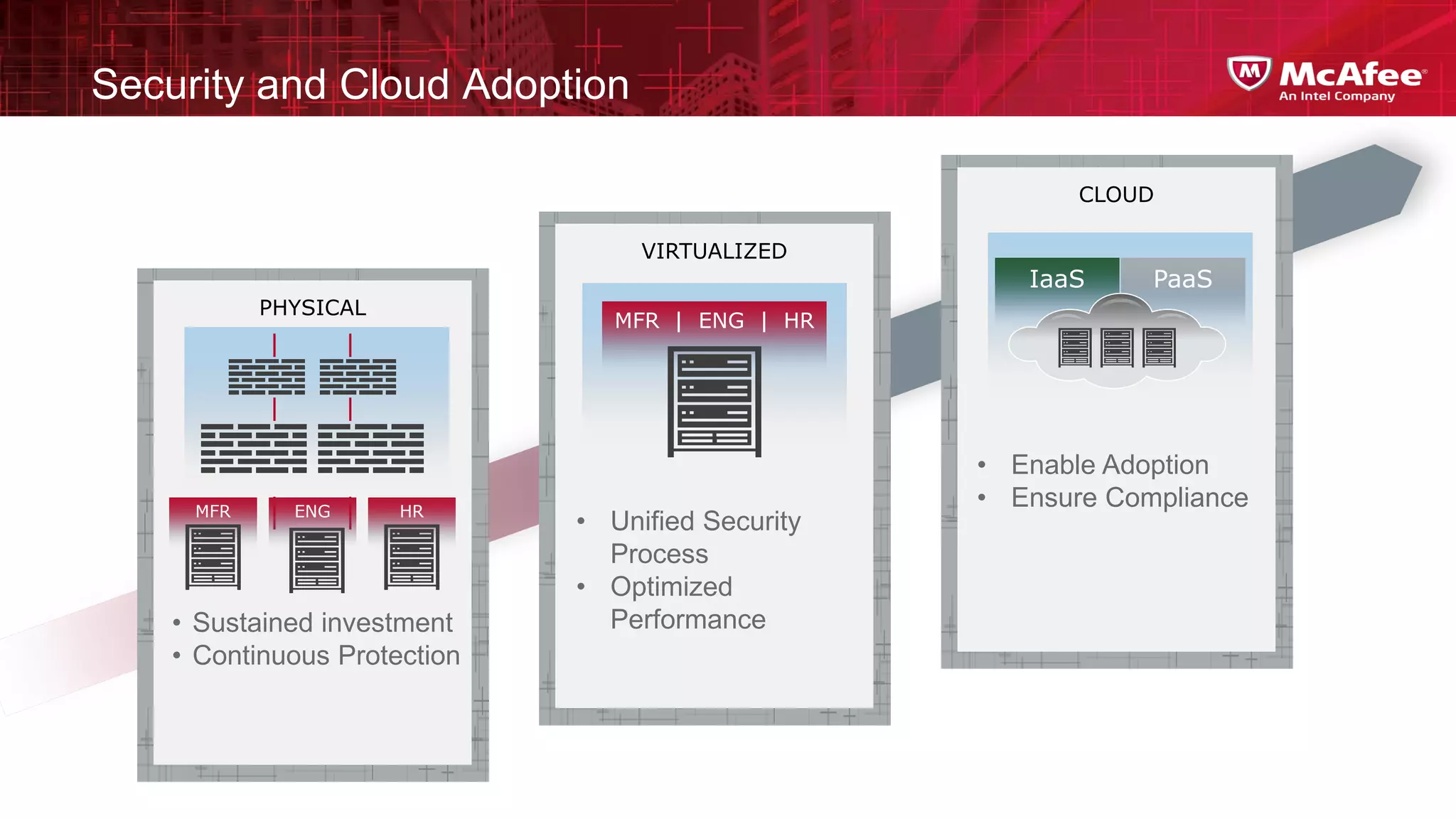
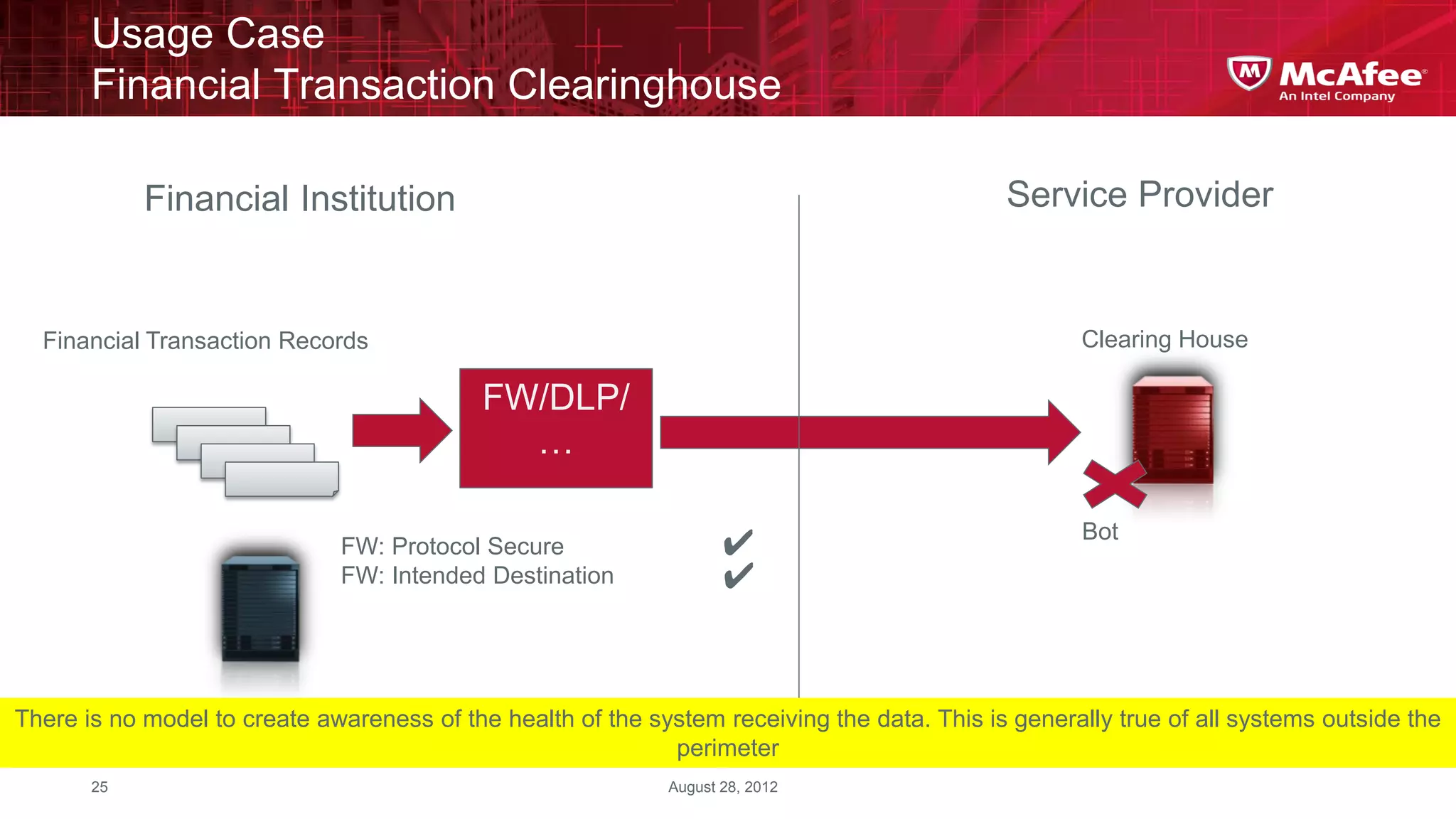
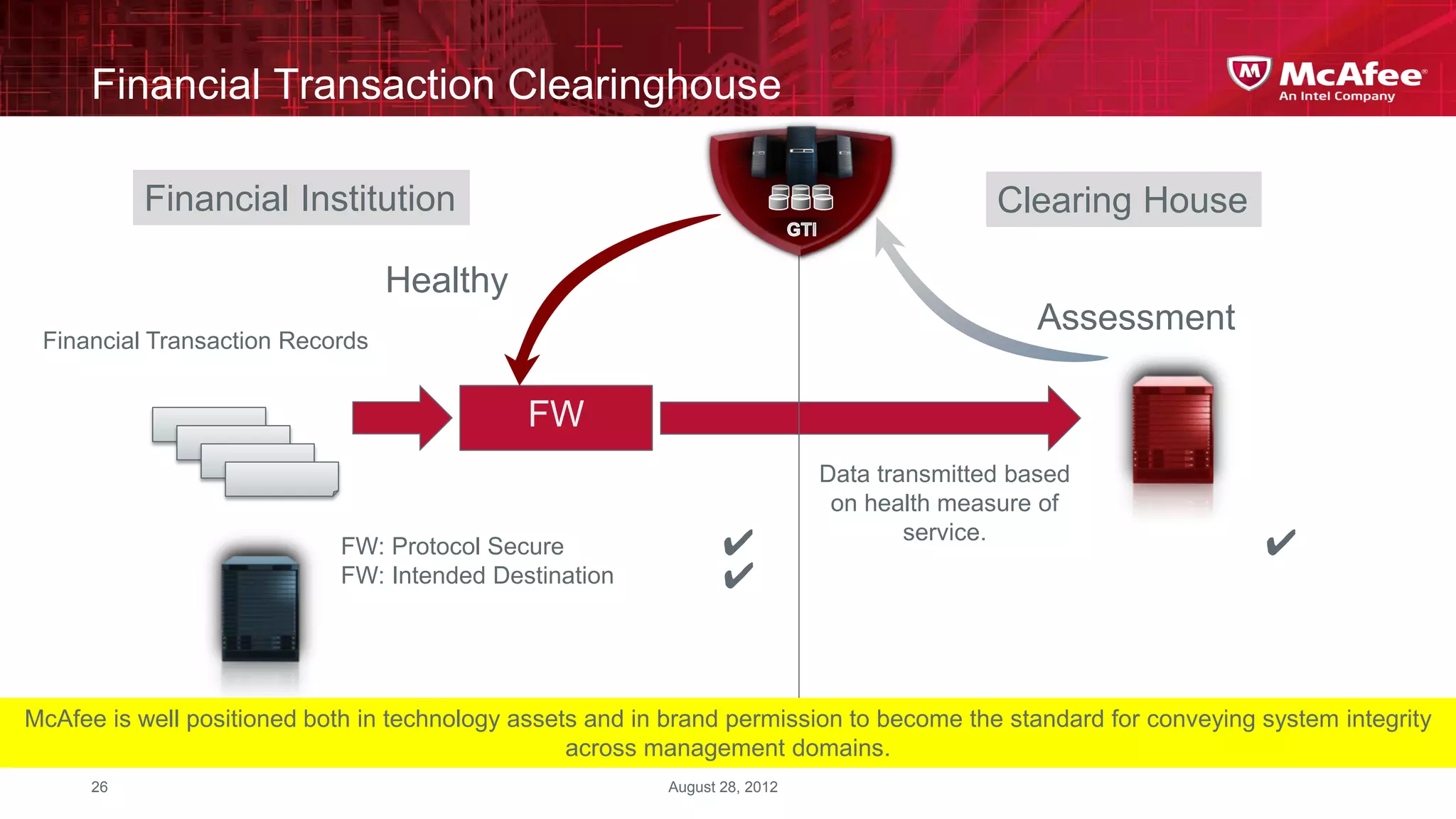
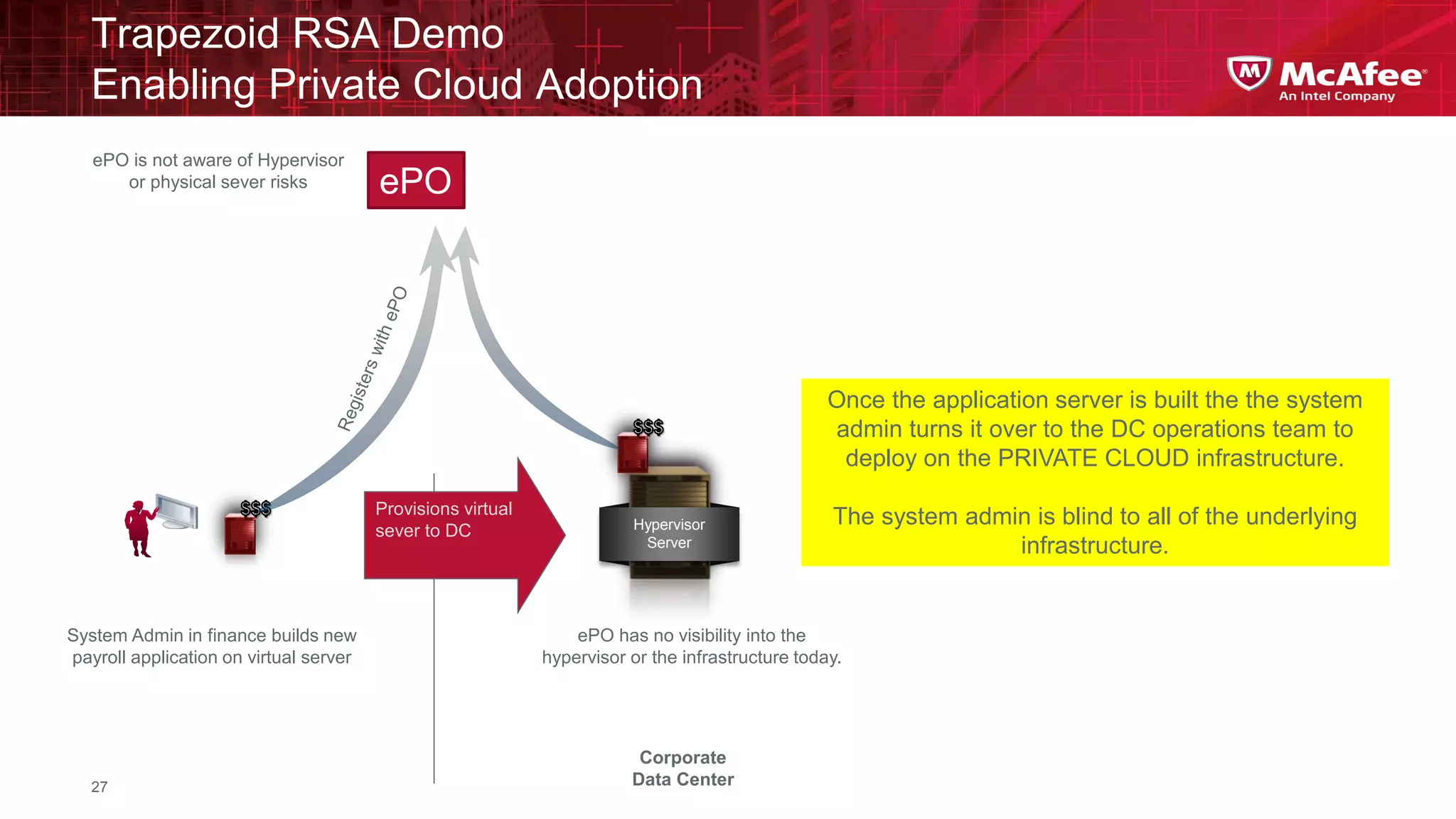
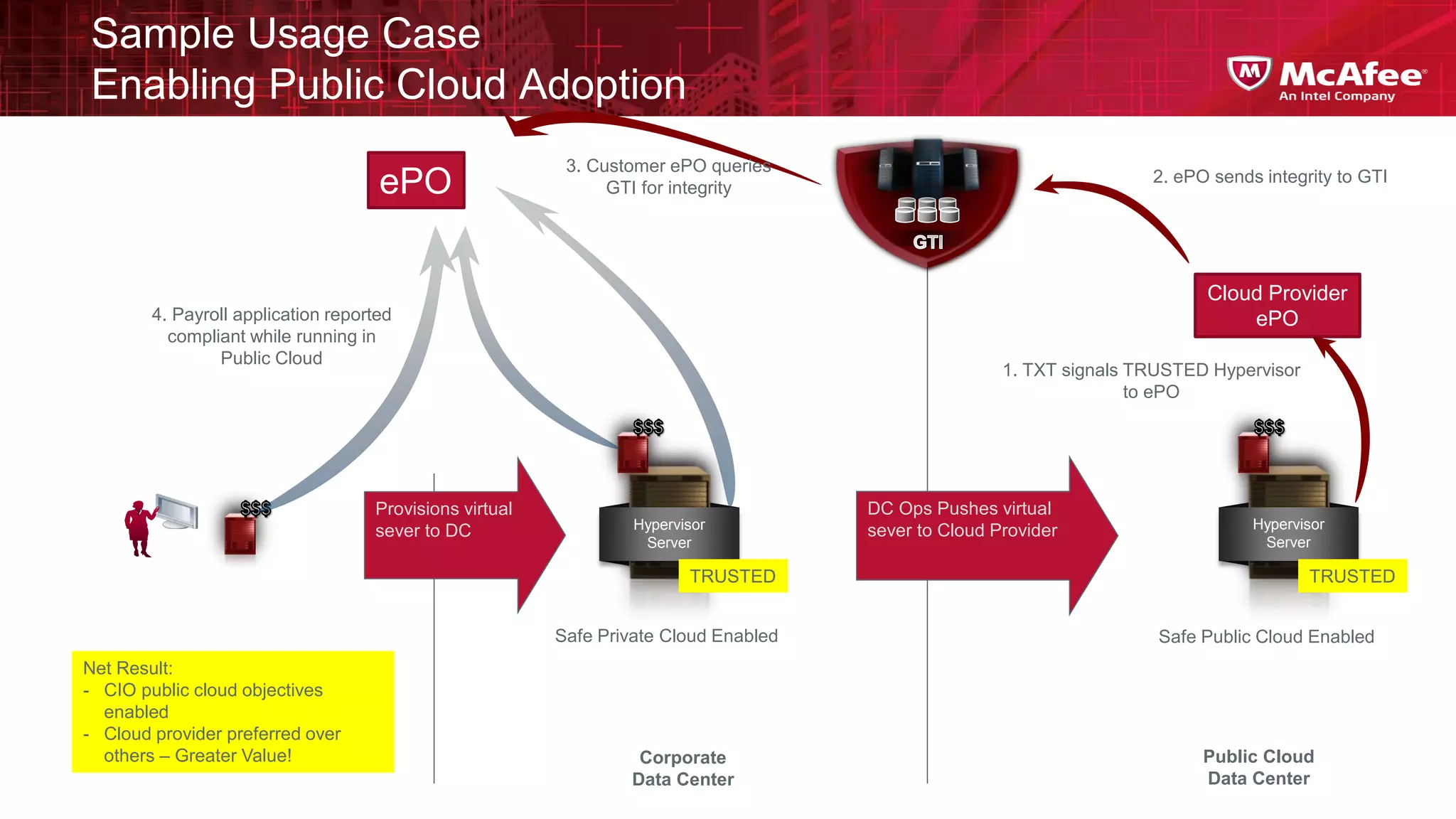
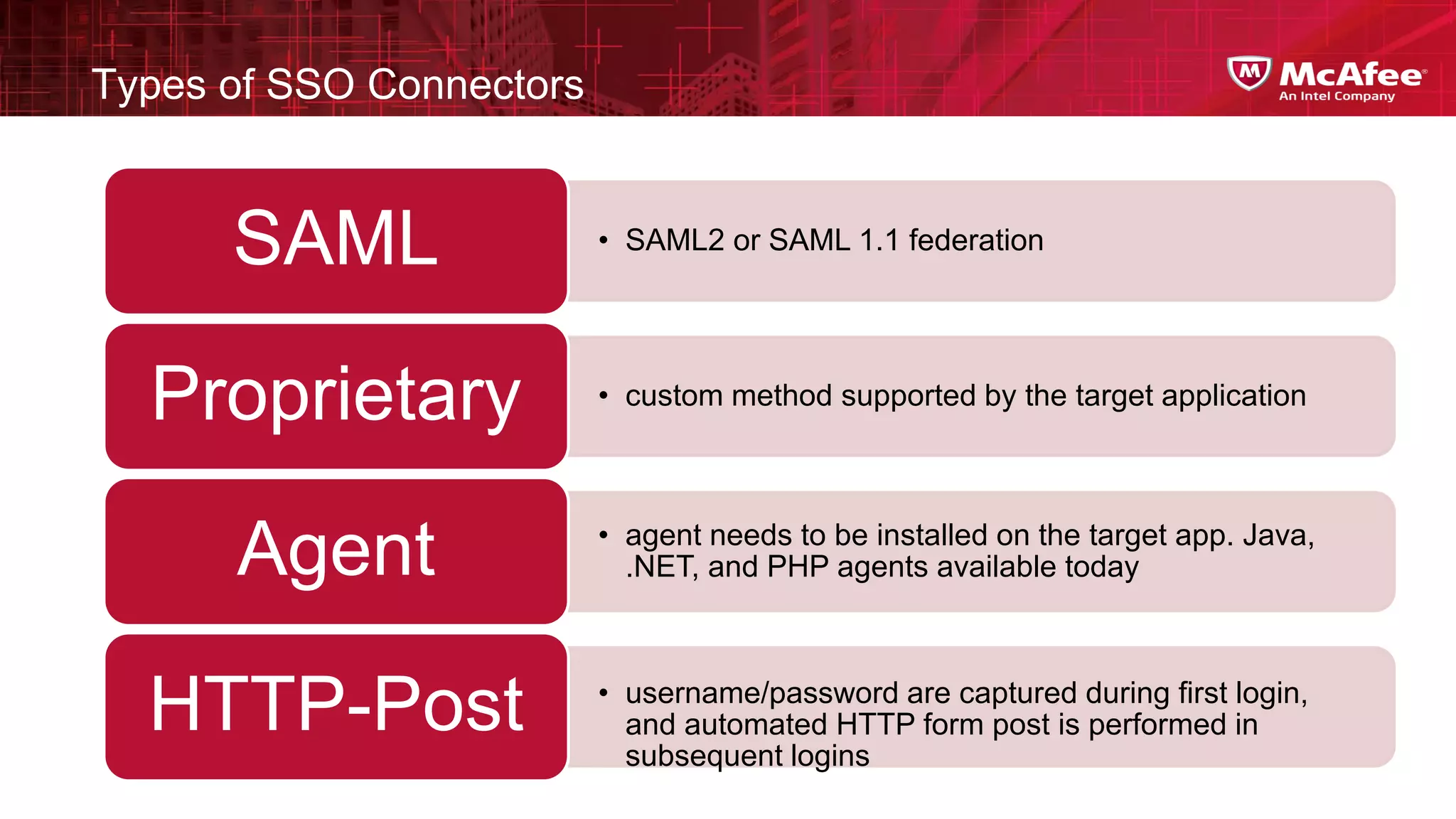
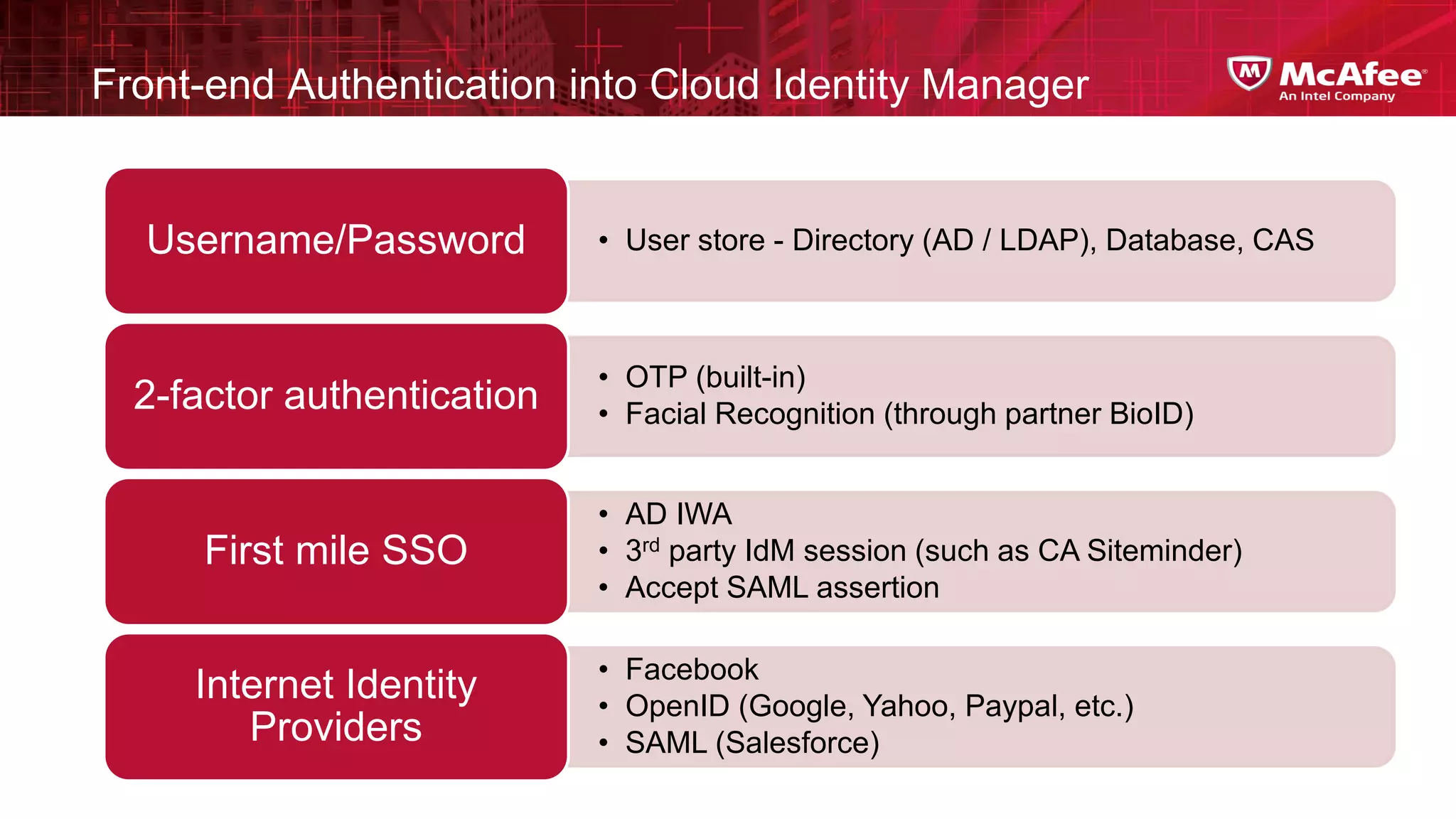
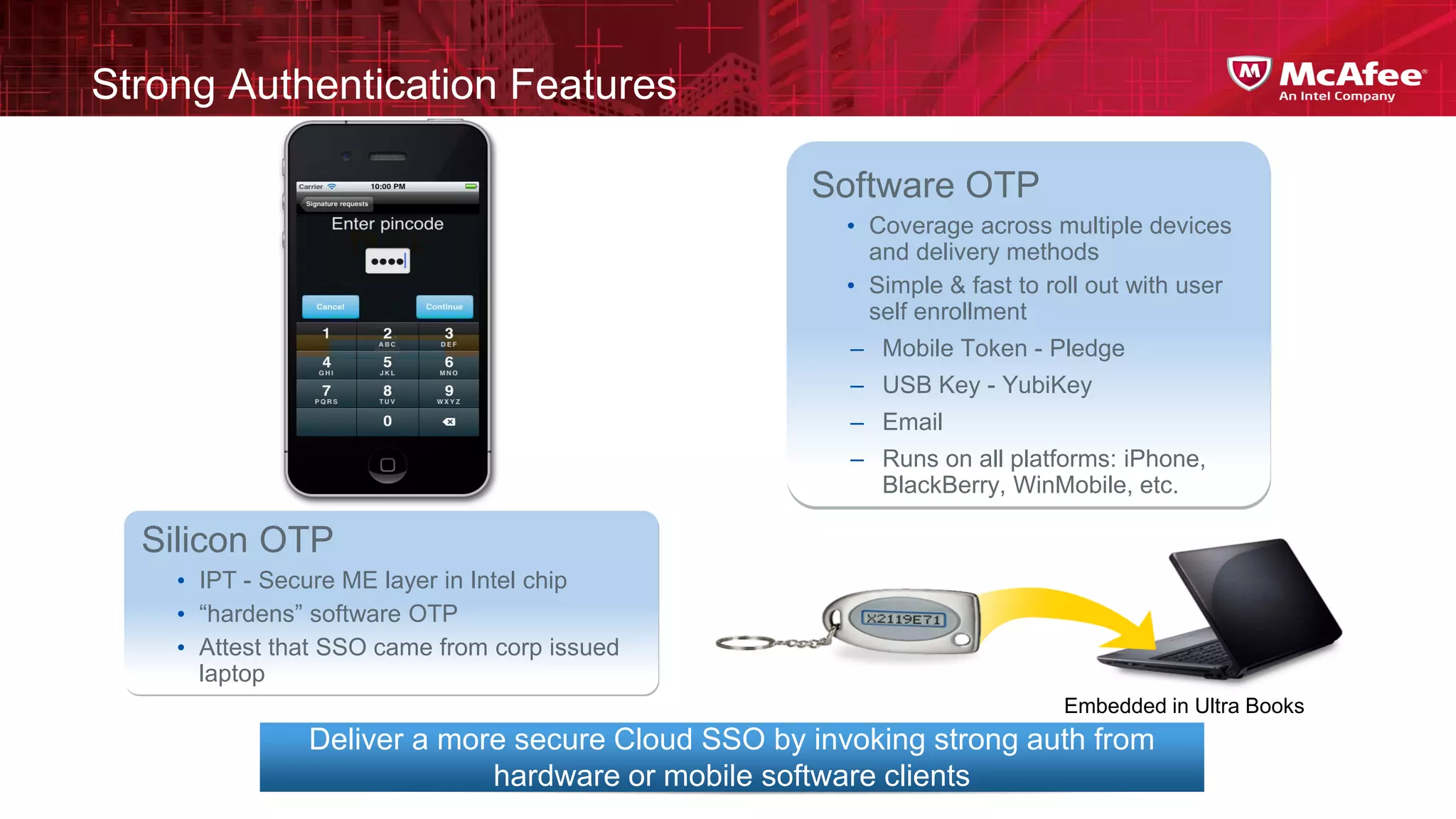
This document discusses building confidence in cloud security. It outlines challenges in cloud computing like loss of physical controls and new attack surfaces. It proposes making cloud security equal to or better than traditional enterprise security by securing connections, applications/data/traffic, and devices. The document also discusses extending security policies to virtualized and private clouds and providing visibility and control across cloud infrastructures. Finally, it discusses McAfee's datacenter security solutions for servers, virtual machines, and databases.