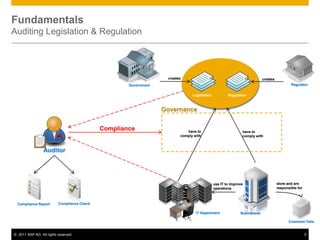
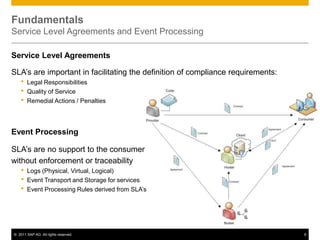
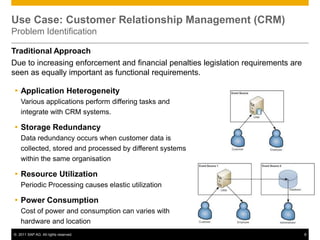
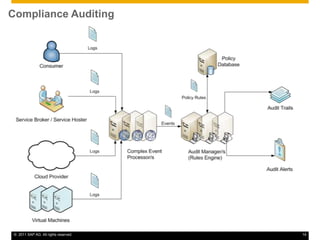
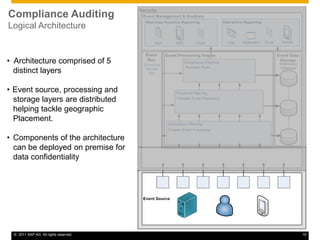
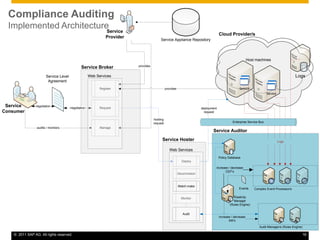
This document discusses cloud compliance auditing. It begins with definitions of cloud computing, compliance, and auditing. It discusses how legislation and regulations create compliance requirements that businesses and auditors must adhere to. Service level agreements are important for defining compliance needs. The document then examines a customer relationship management use case and challenges of ensuring compliance for data accessibility, retention, and geo-locality in cloud environments. It presents a logical architecture for cloud compliance auditing consisting of distributed event source, processing, and storage layers to help address these challenges.