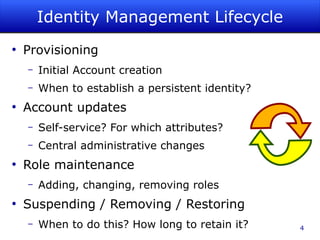
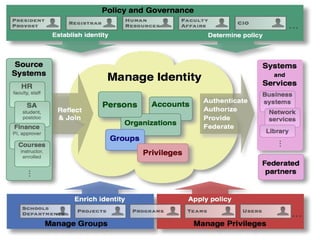
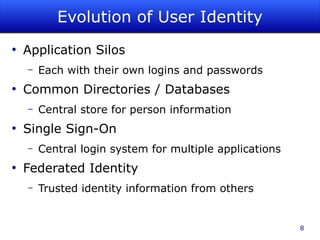
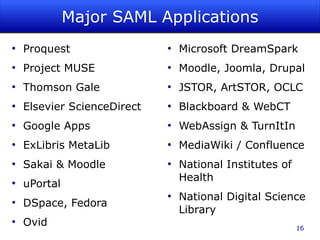
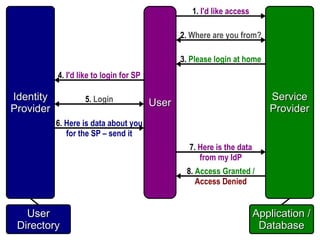
The document discusses identity management as a crucial set of processes for creating, maintaining, and using digital identities, emphasizing its importance for security, privacy, and user convenience. It outlines the identity management lifecycle, challenges in managing fragmented identities, and emerging best practices such as automation and federated identity systems. Additionally, it recommends adopting open, standards-based identity management systems to improve interoperability and usability in educational institutions.