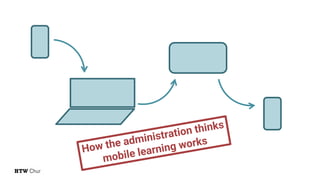
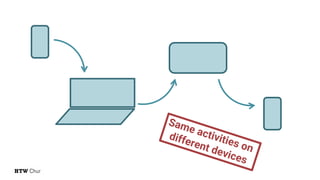
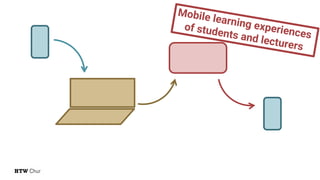
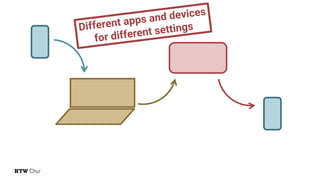
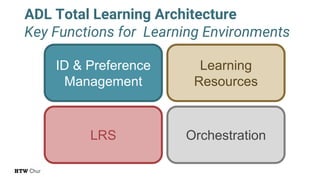
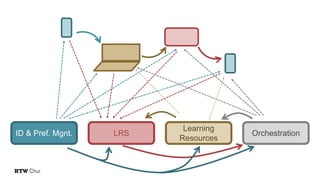
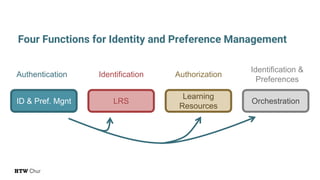
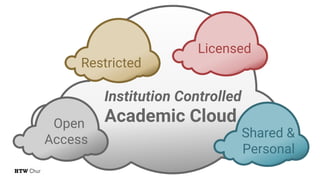
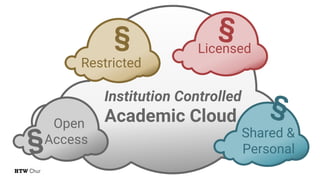
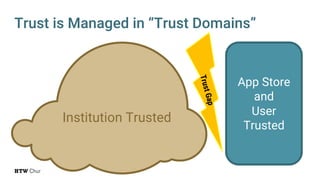
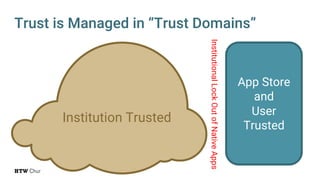
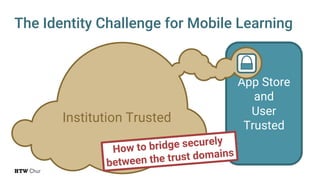
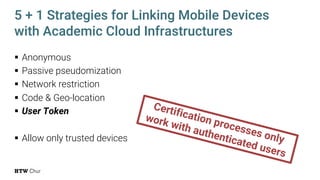
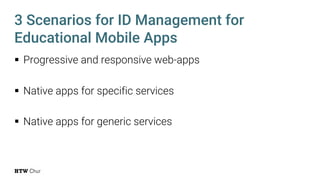
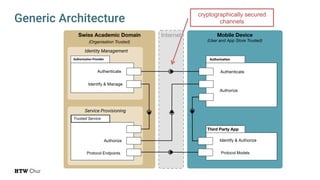
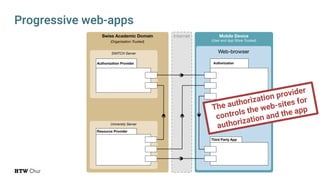
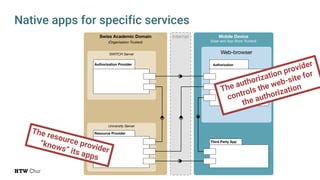
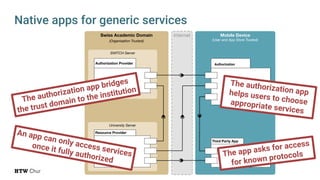
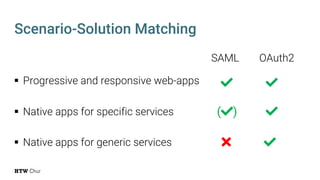
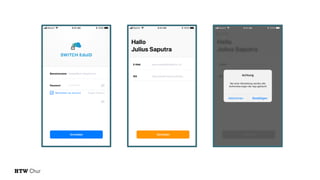
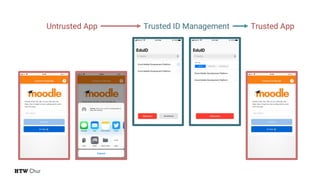
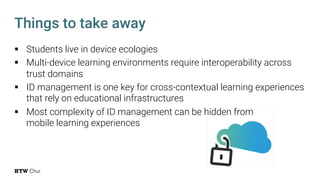
The document explores the challenges and strategies for integrating native mobile apps into educational technology ecosystems, emphasizing the low engagement of students with mobile learning. Key barriers identified include authentication difficulties, the need for multiple accounts, and poor integration with existing systems. The authors propose strategies for identity management to enhance interoperability and reduce complexity in mobile learning experiences.