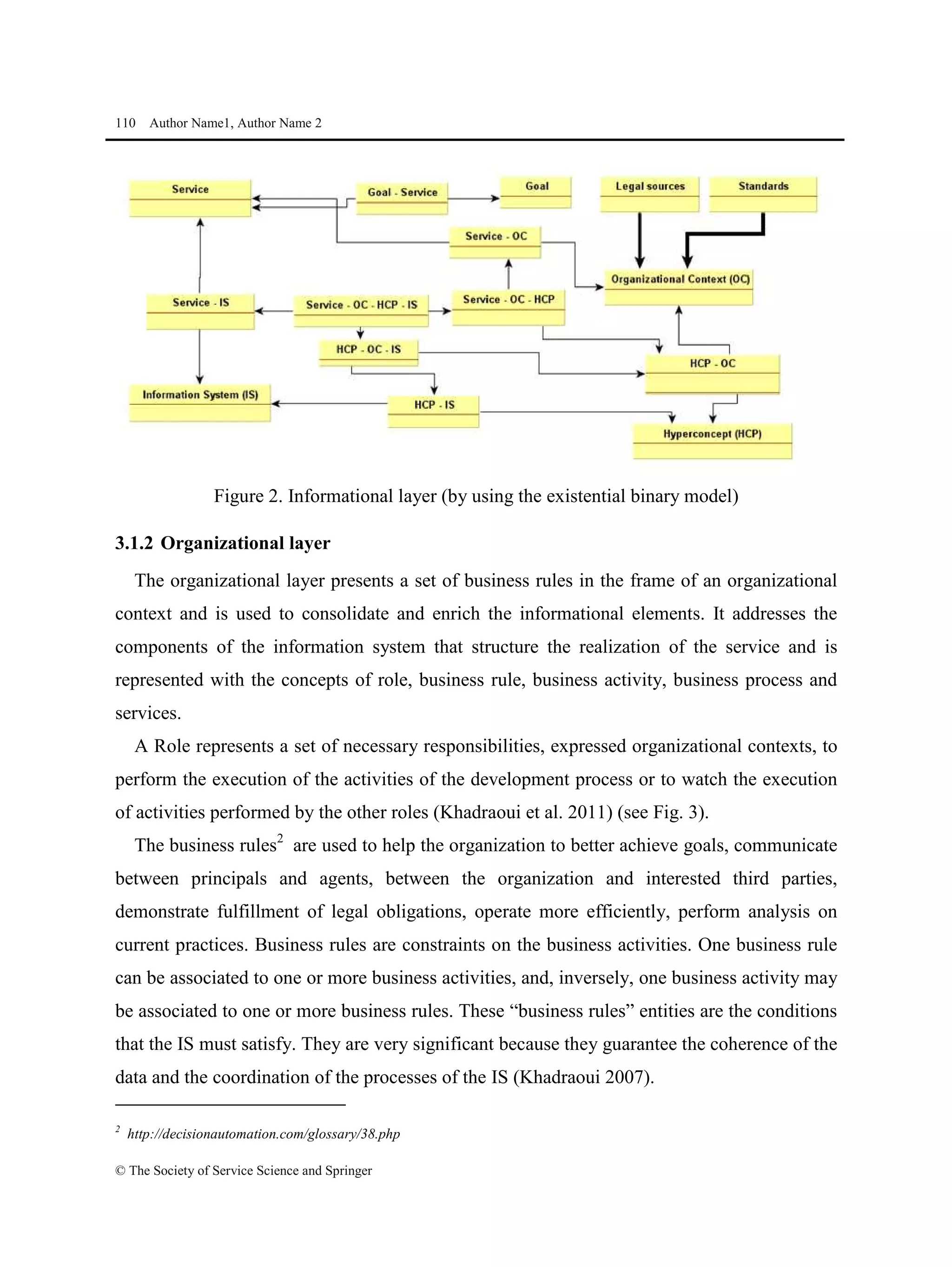
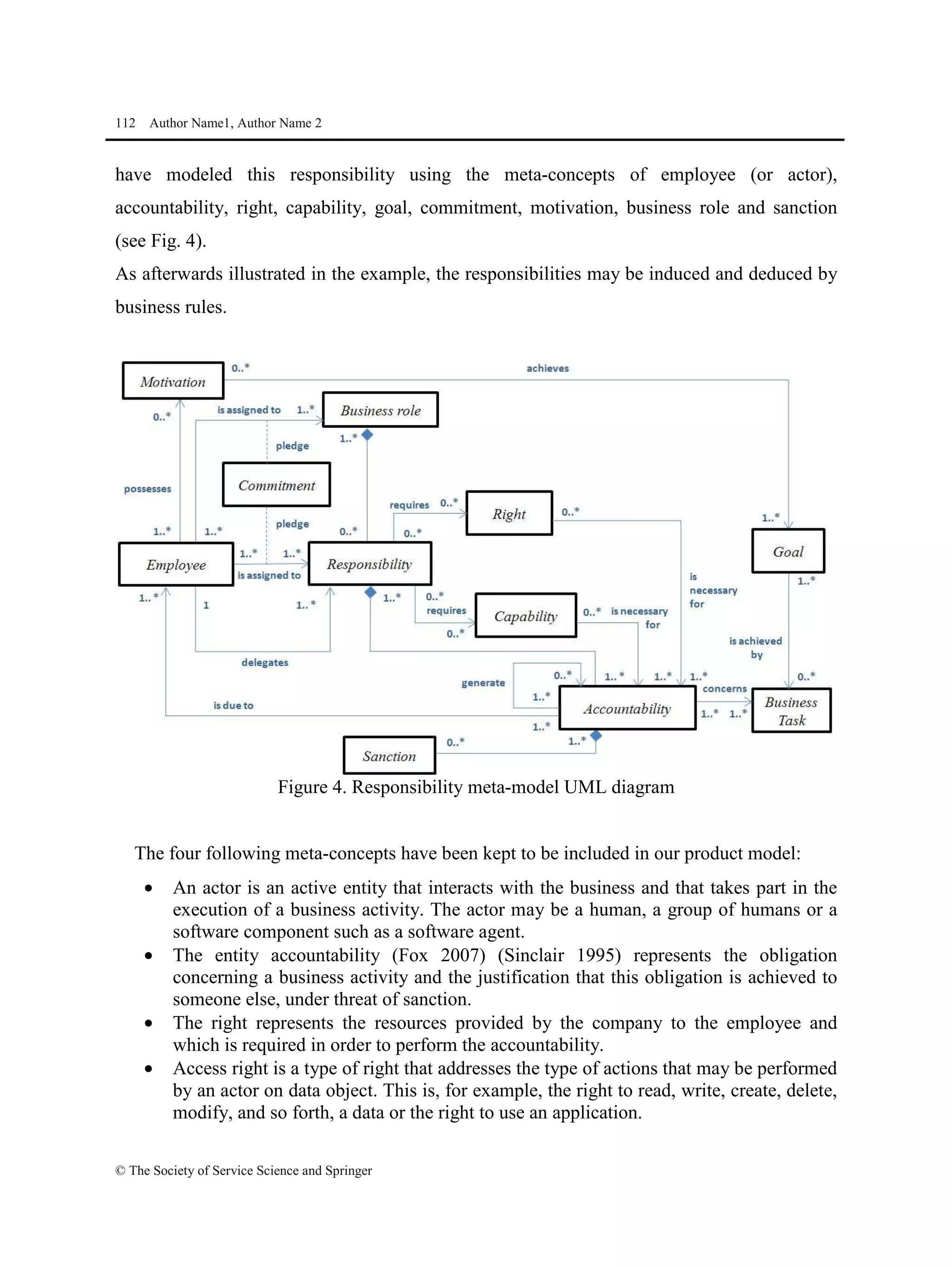
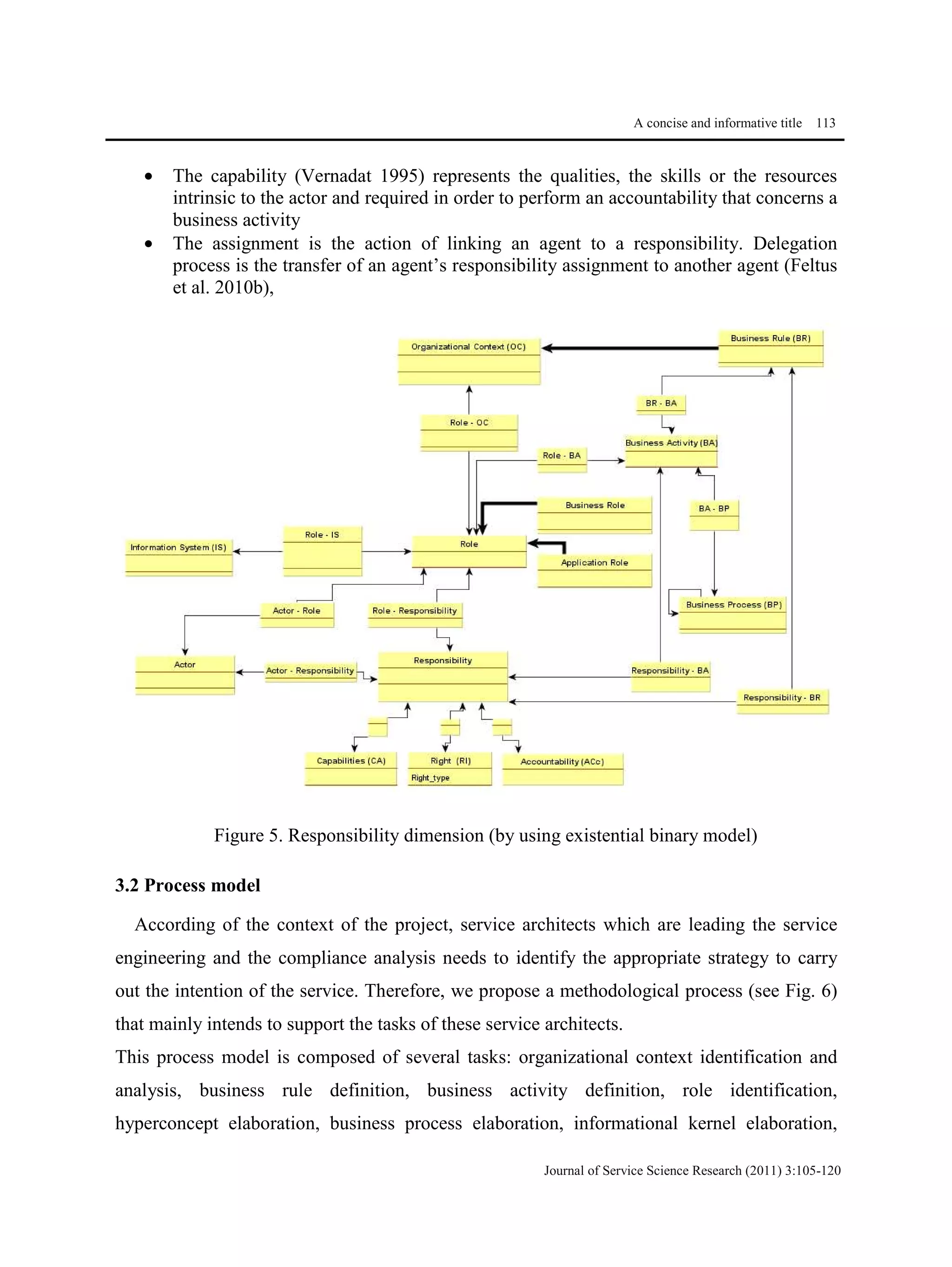
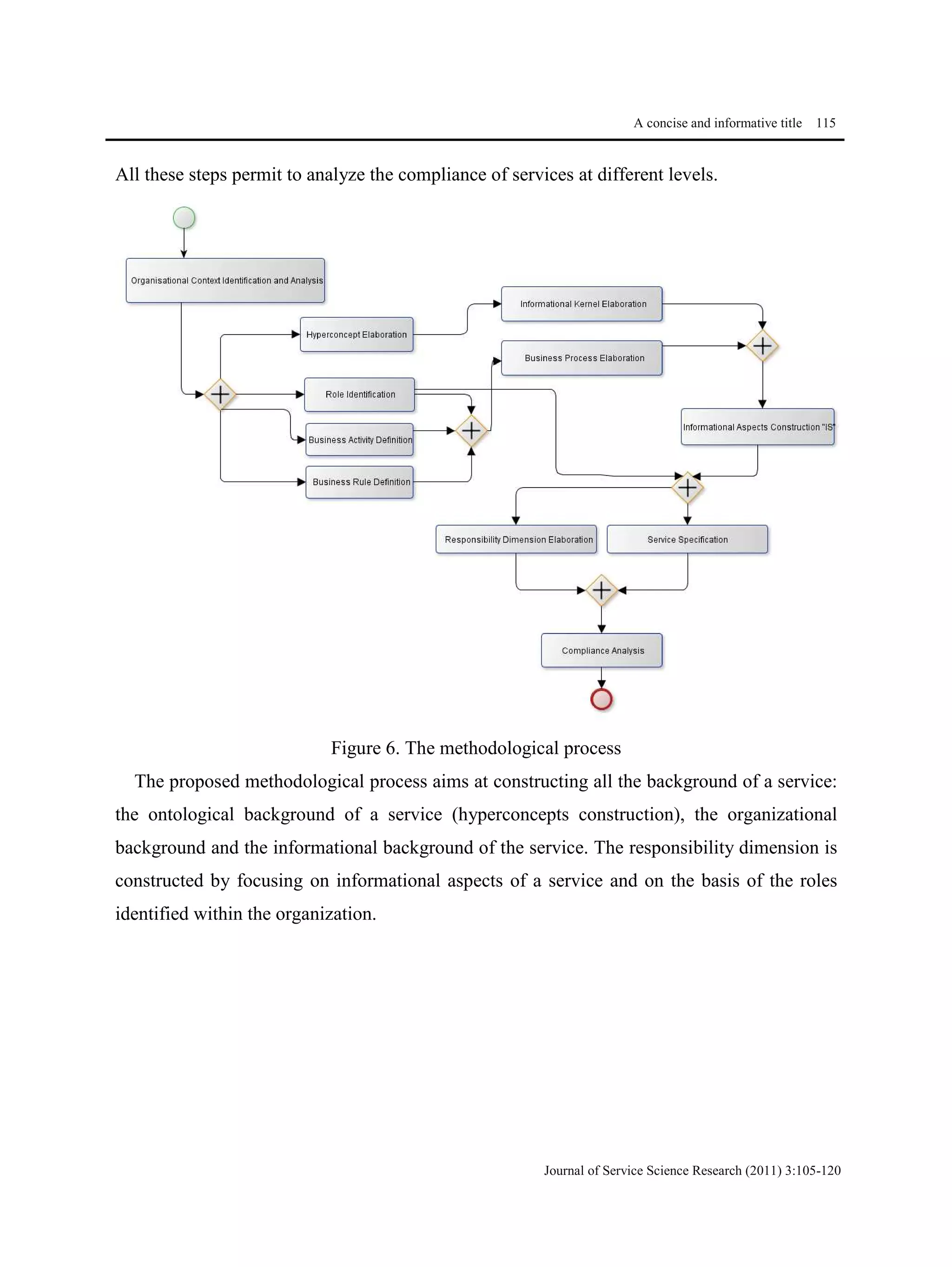
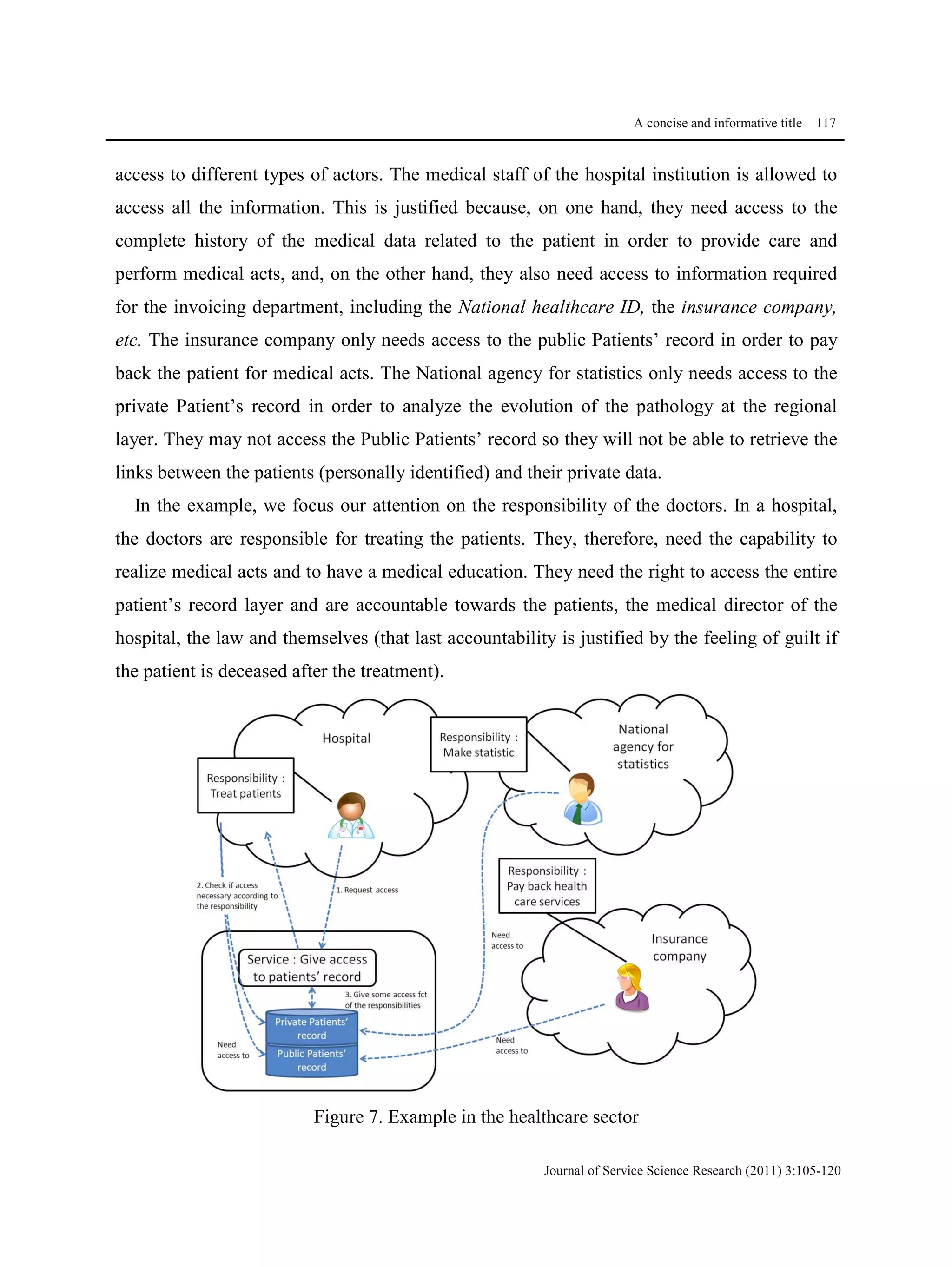
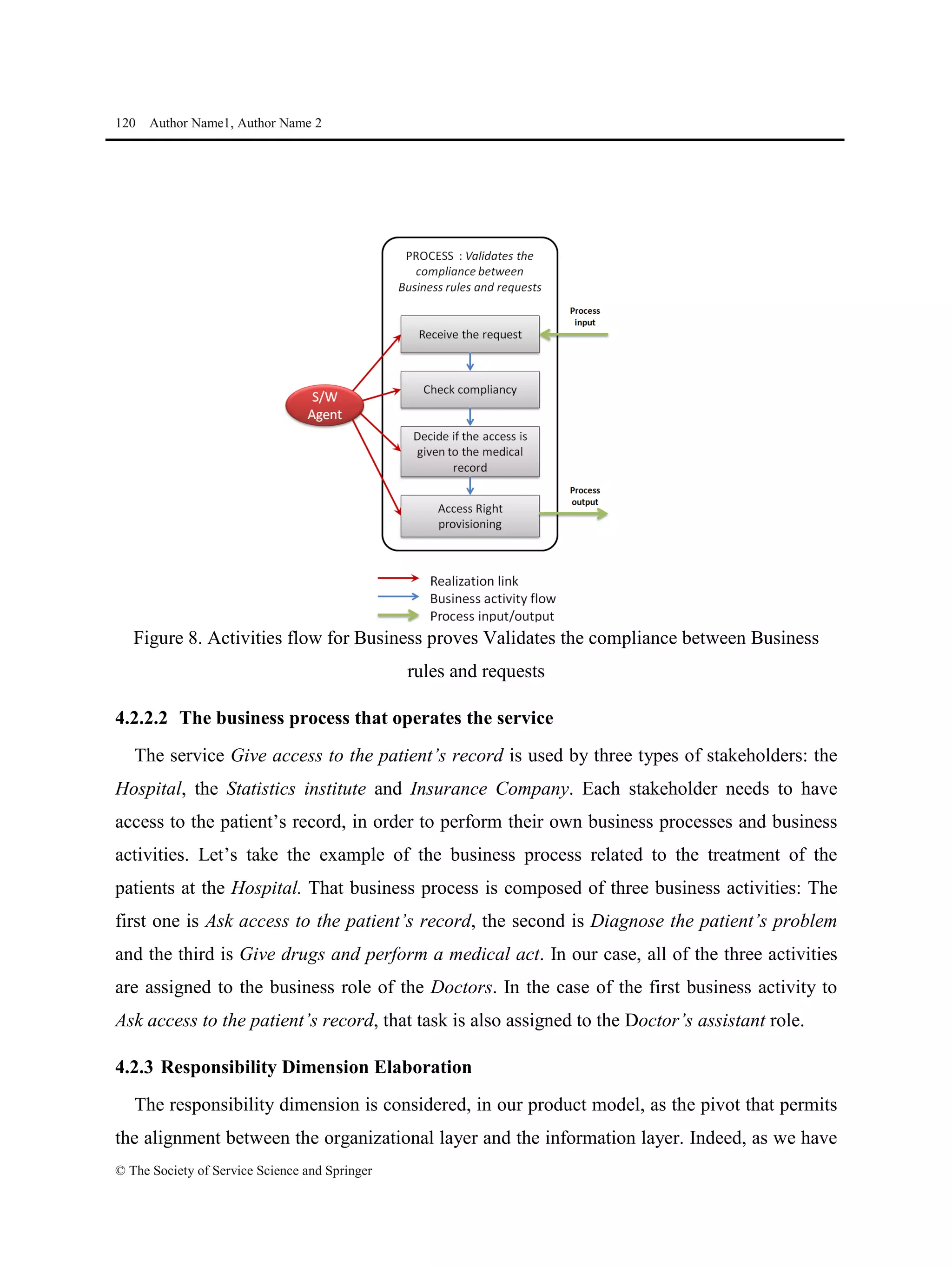
This document proposes a methodological approach for specifying services and analyzing service compliance considering the responsibility dimension of stakeholders. The approach includes a product model and process model. The product model has three layers: an informational layer describing service context and concepts, an organizational layer describing business rules and roles, and a responsibility dimension layer linking the two. The process model outlines steps for service architects to identify context, define concepts and rules, specify services, and analyze compliance. The approach is illustrated with an example of managing access rights for sensitive healthcare data exchange between organizations.