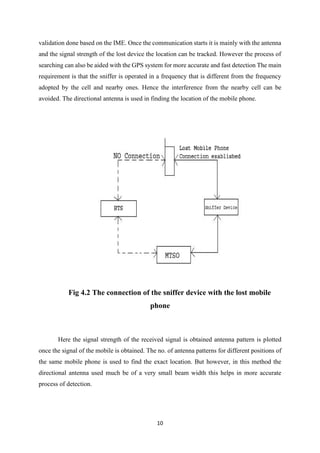
The document discusses the development of a device called the 'sniffer' designed for detecting lost mobile phones, leveraging the mobile's unique IMEI number. It details the components, such as a sniffer base station and a unidirectional antenna, necessary for the device to function effectively. The proposed solution aims to improve tracking methods by using software that interacts with the device's IMEI and facilitates communication with the lost mobile phone while avoiding interference with other cellular networks.












![14
REFERENCES
[1] Schiller, “Mobile Communication”, Pearson Education 1 Edition, 7th reprint-2003.
[2] John D Kraus, “Electromagnetics”, TMH
[3] Jordan et al, “Electromagnetic waves and radiation system”, Prentice Hall
[4] www.gsmworld.com
[5] http://ericsson.com 6. http://iec.org](https://image.slidesharecdn.com/sempart3-200616053728/85/Sniffer-for-detecting-lost-mobiles-Technical-Seminar-14-320.jpg)