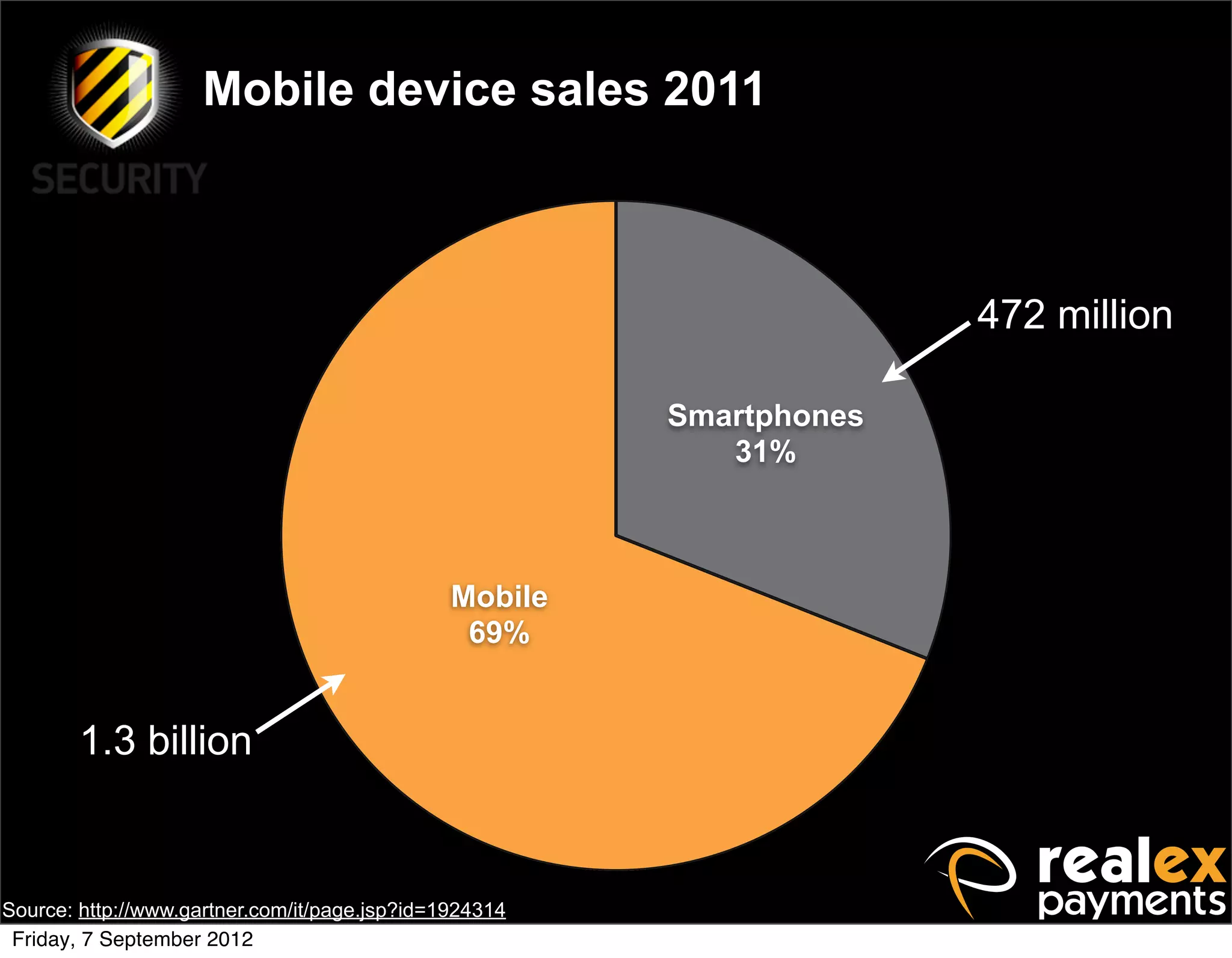
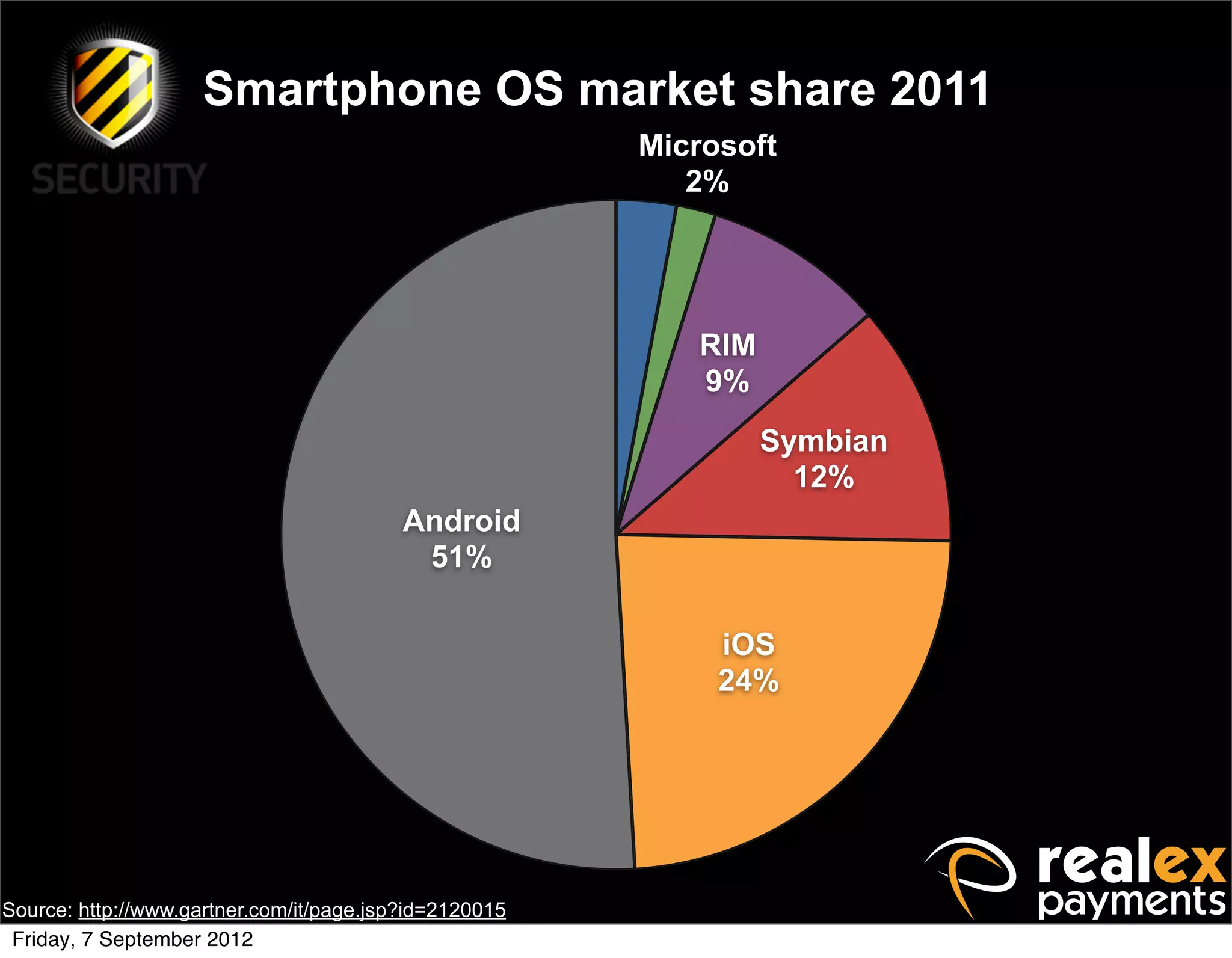
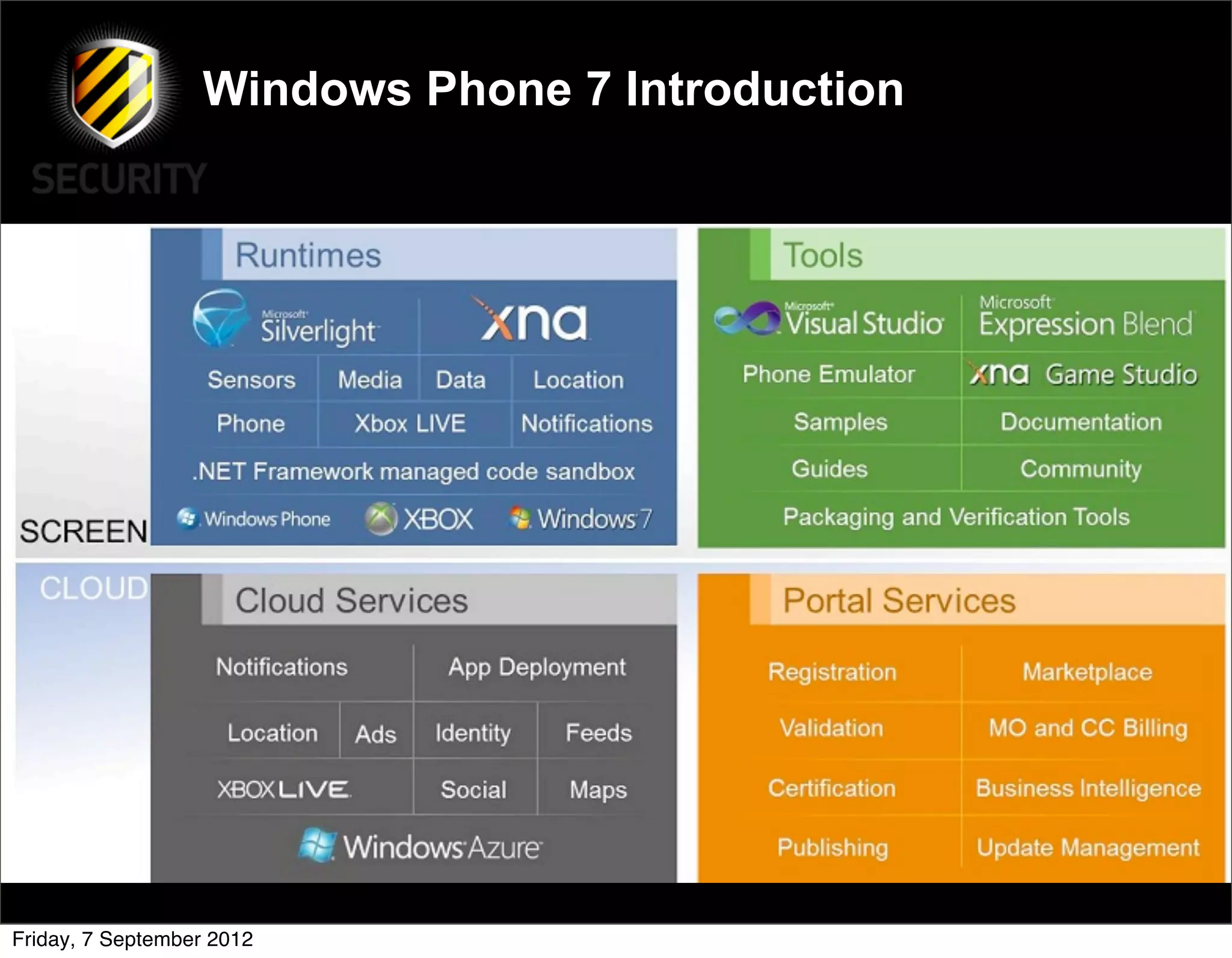
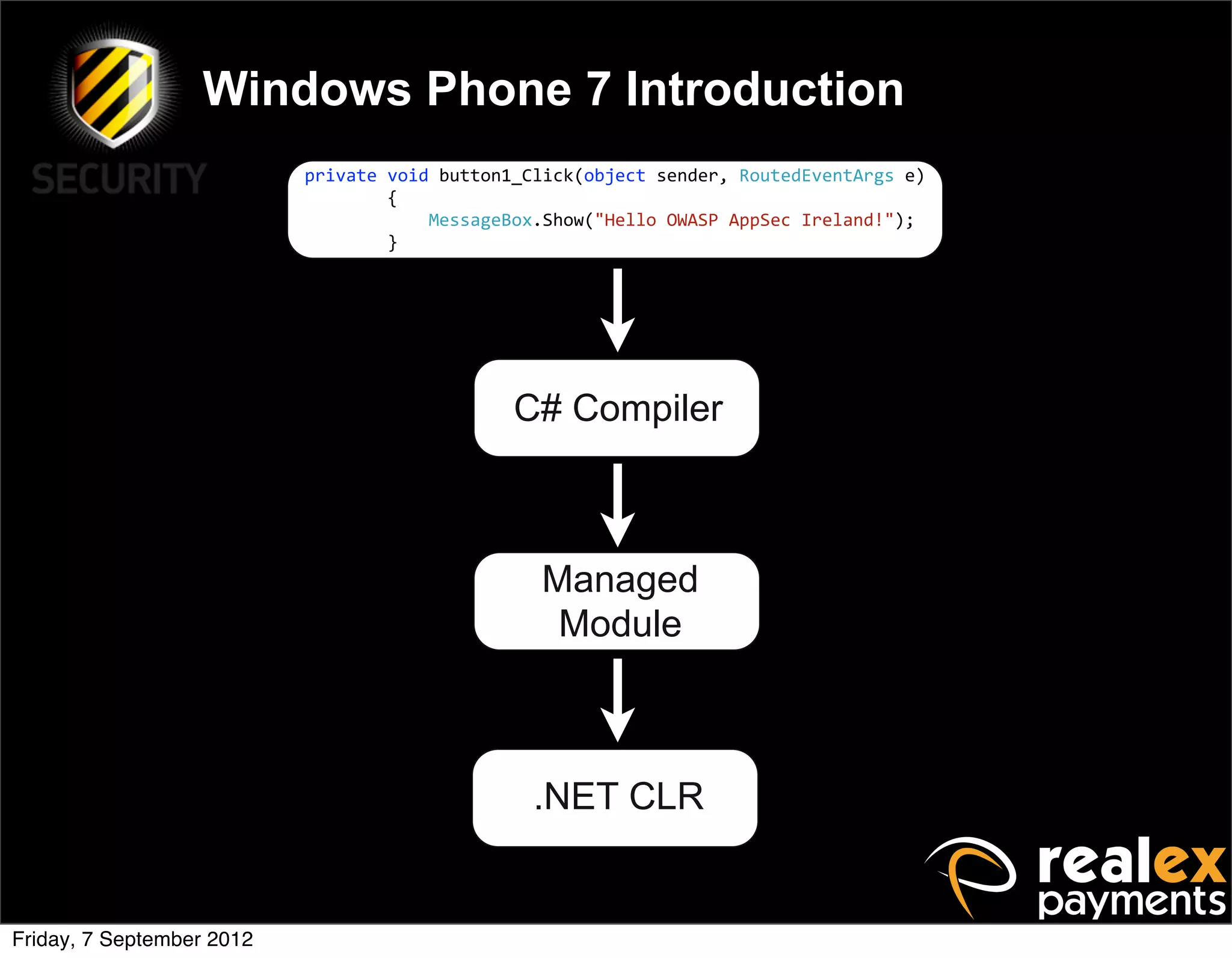
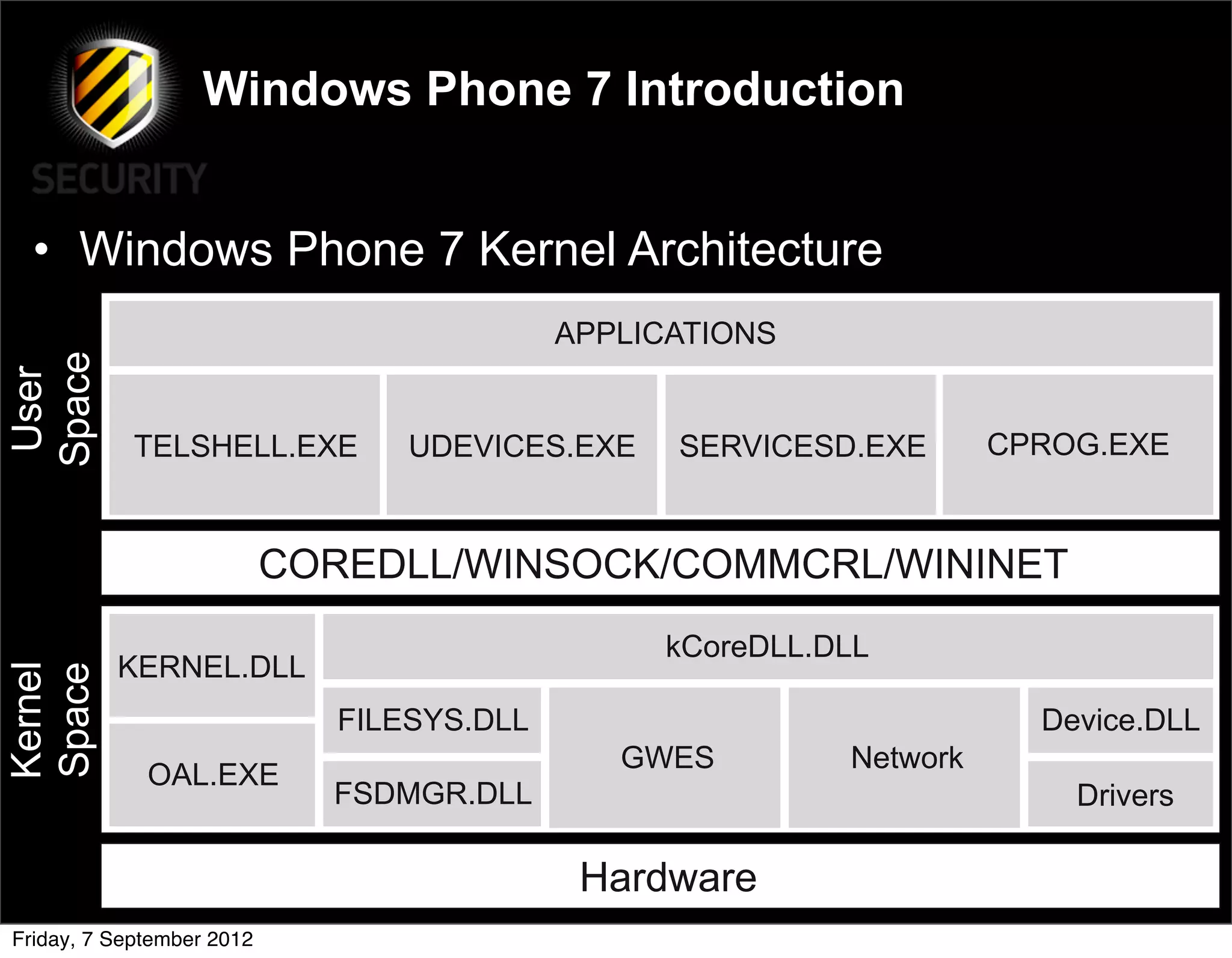
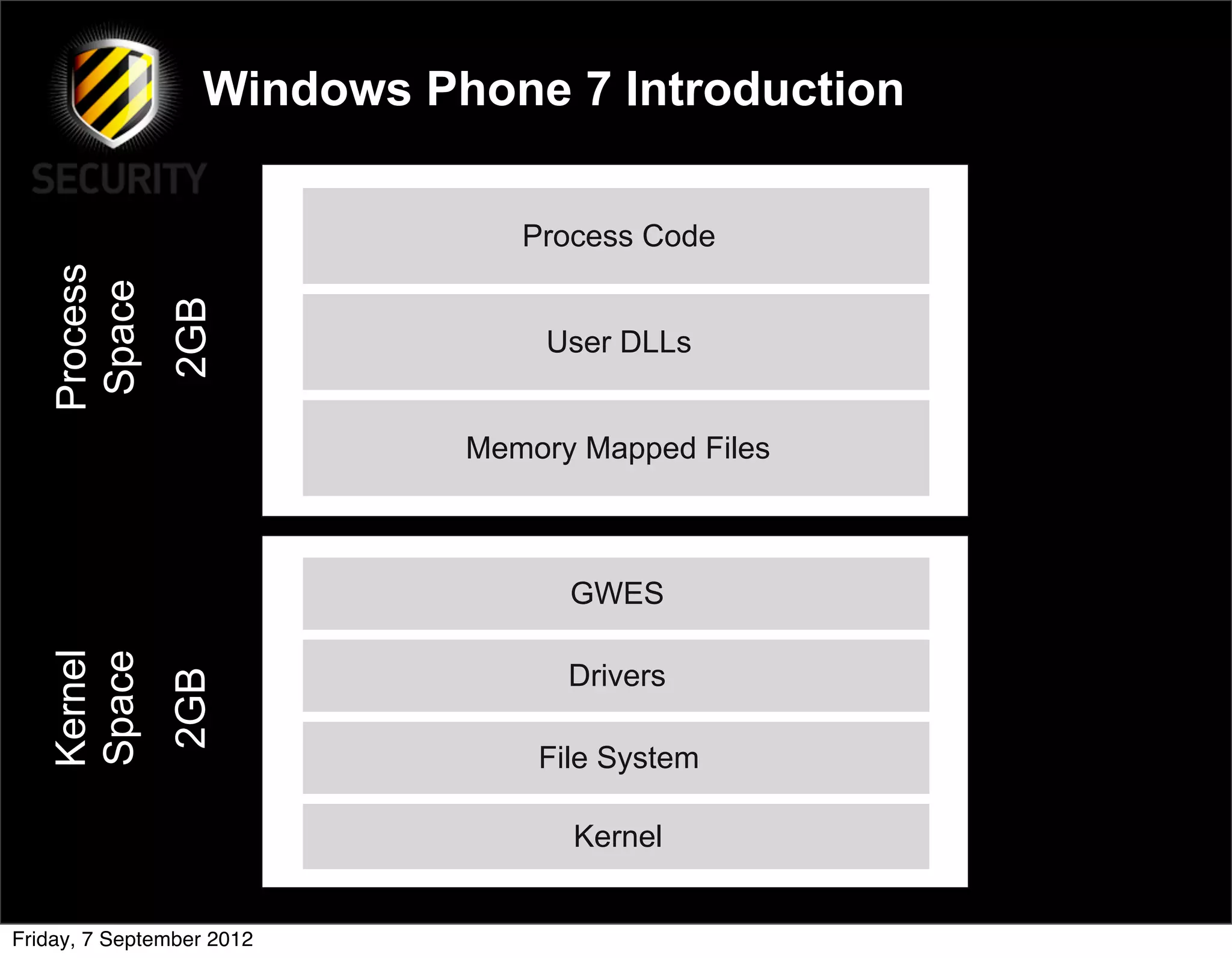
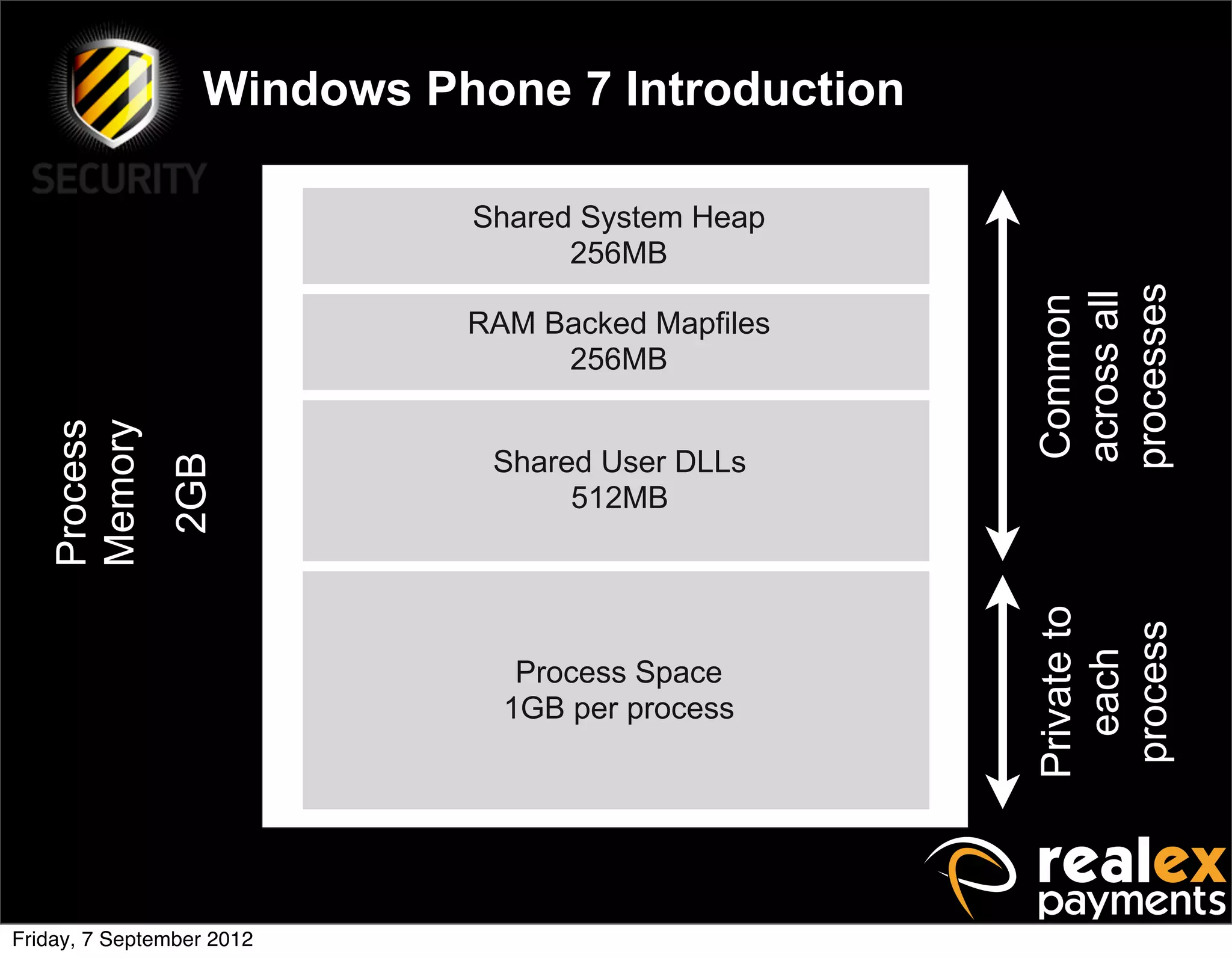
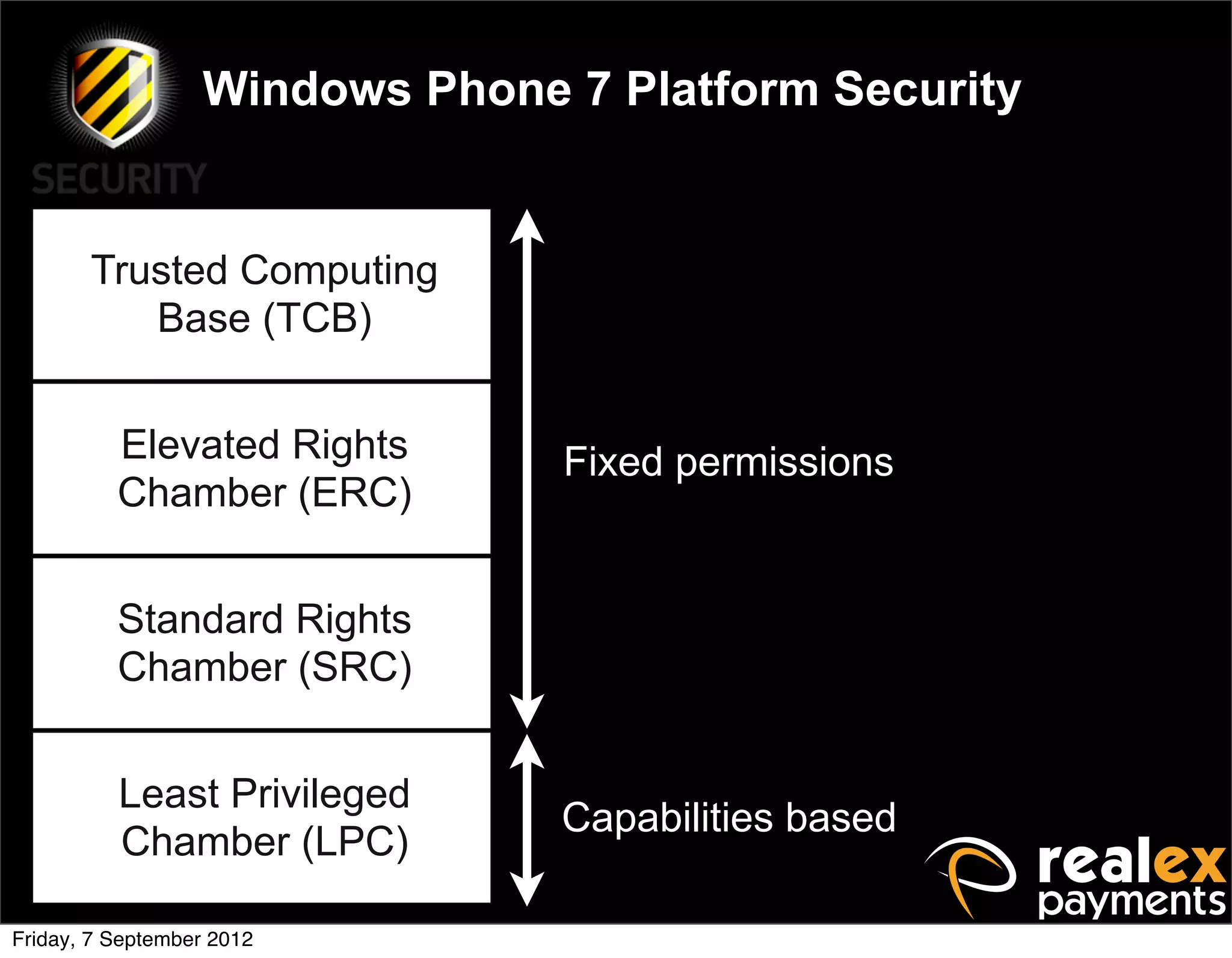
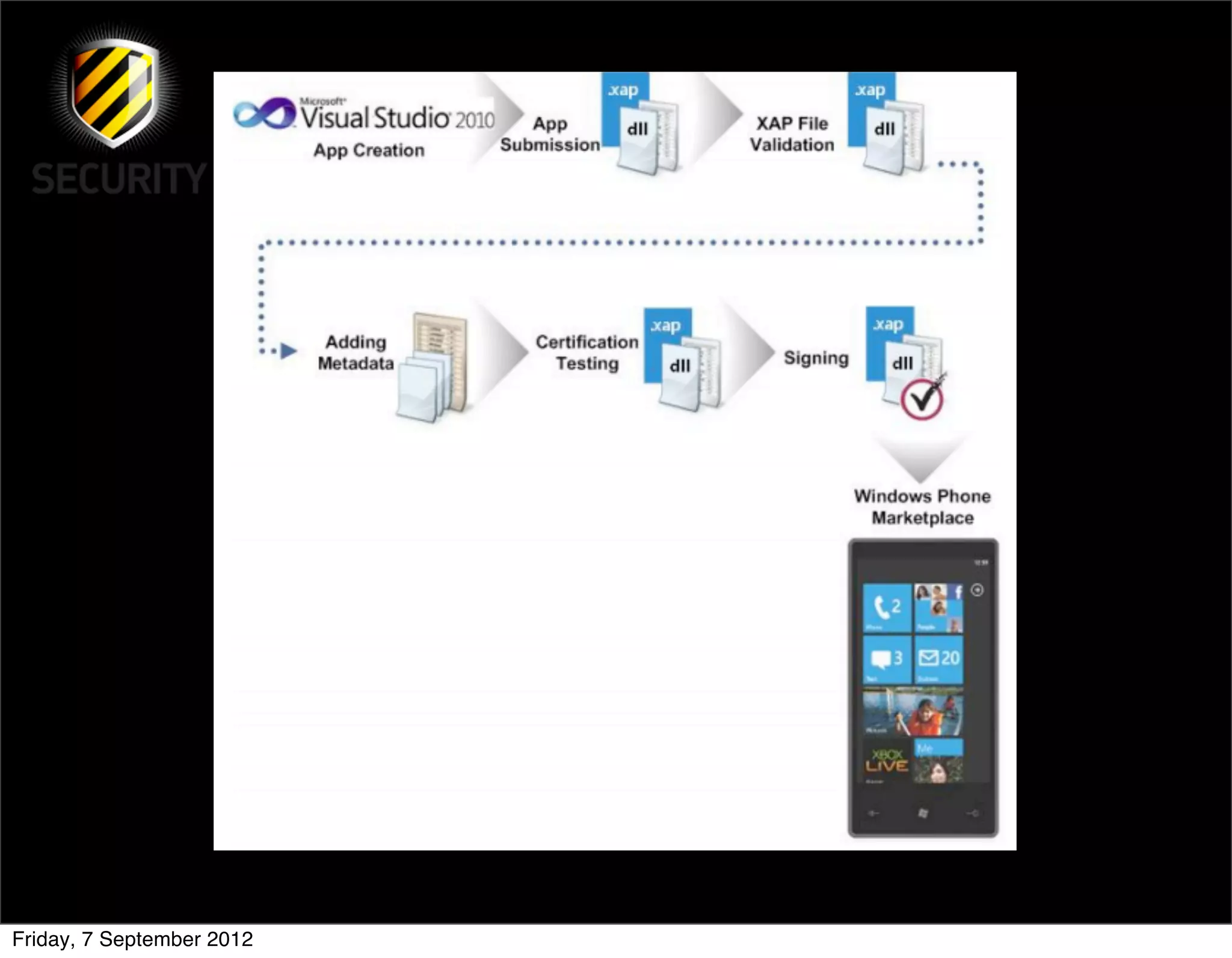
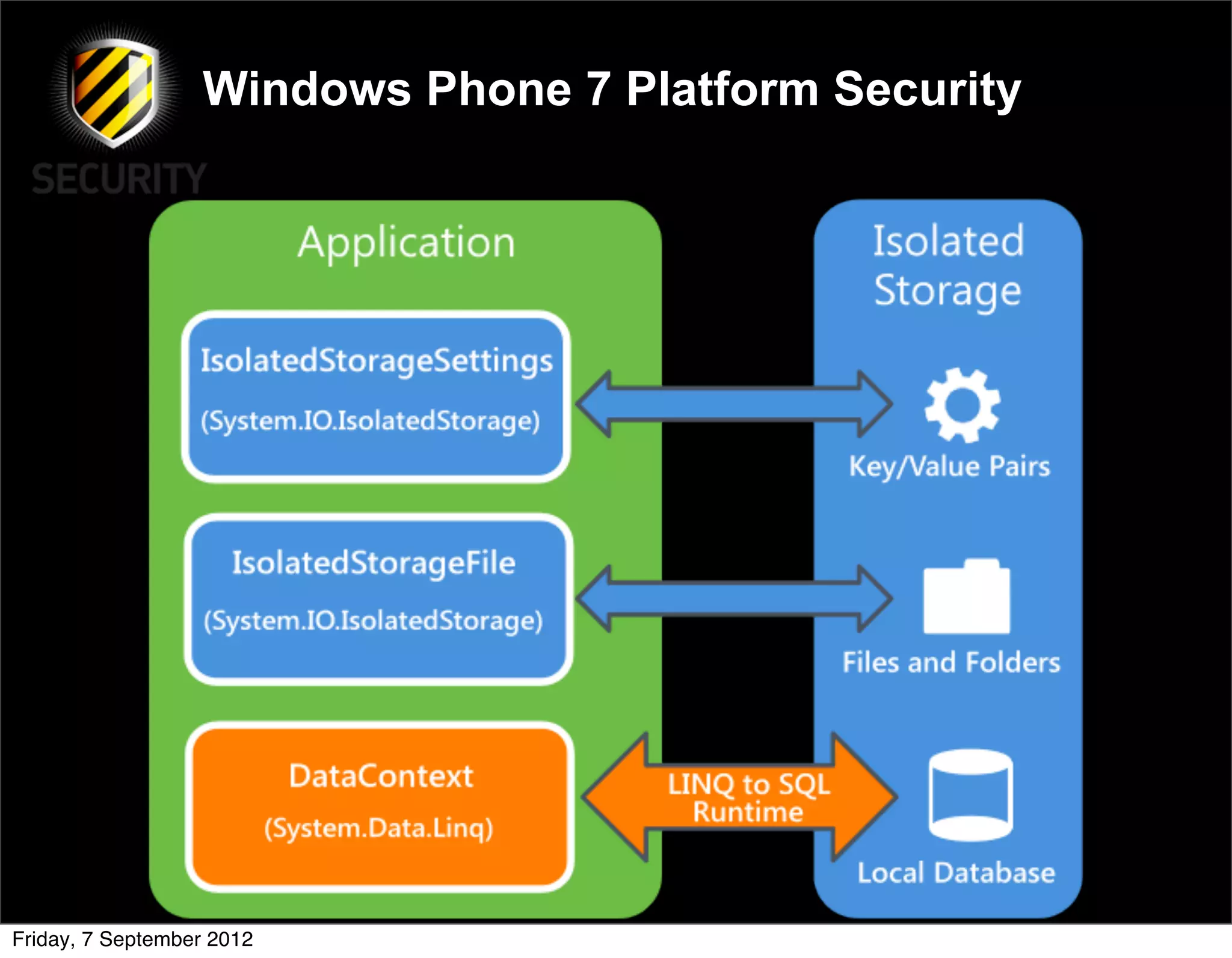
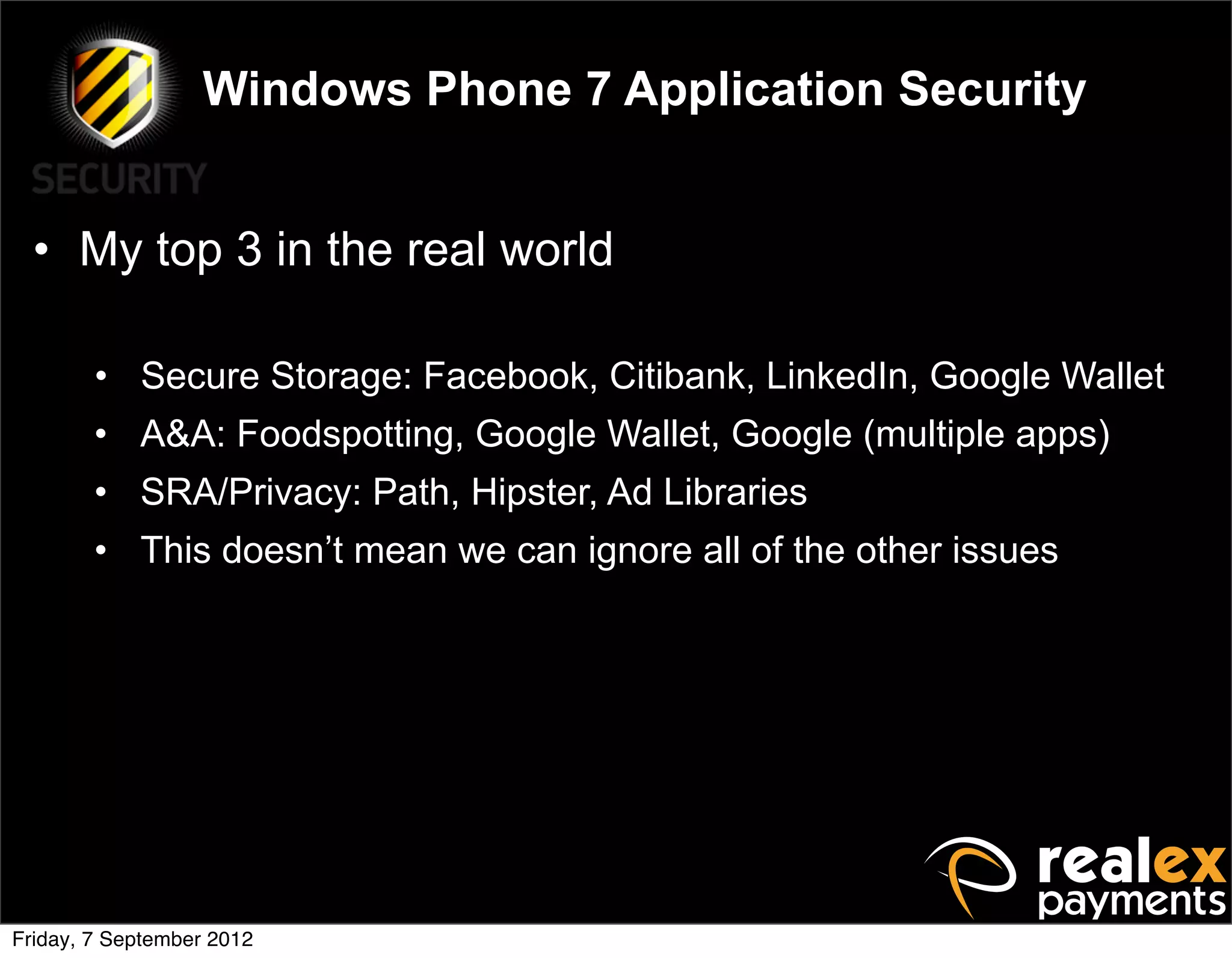
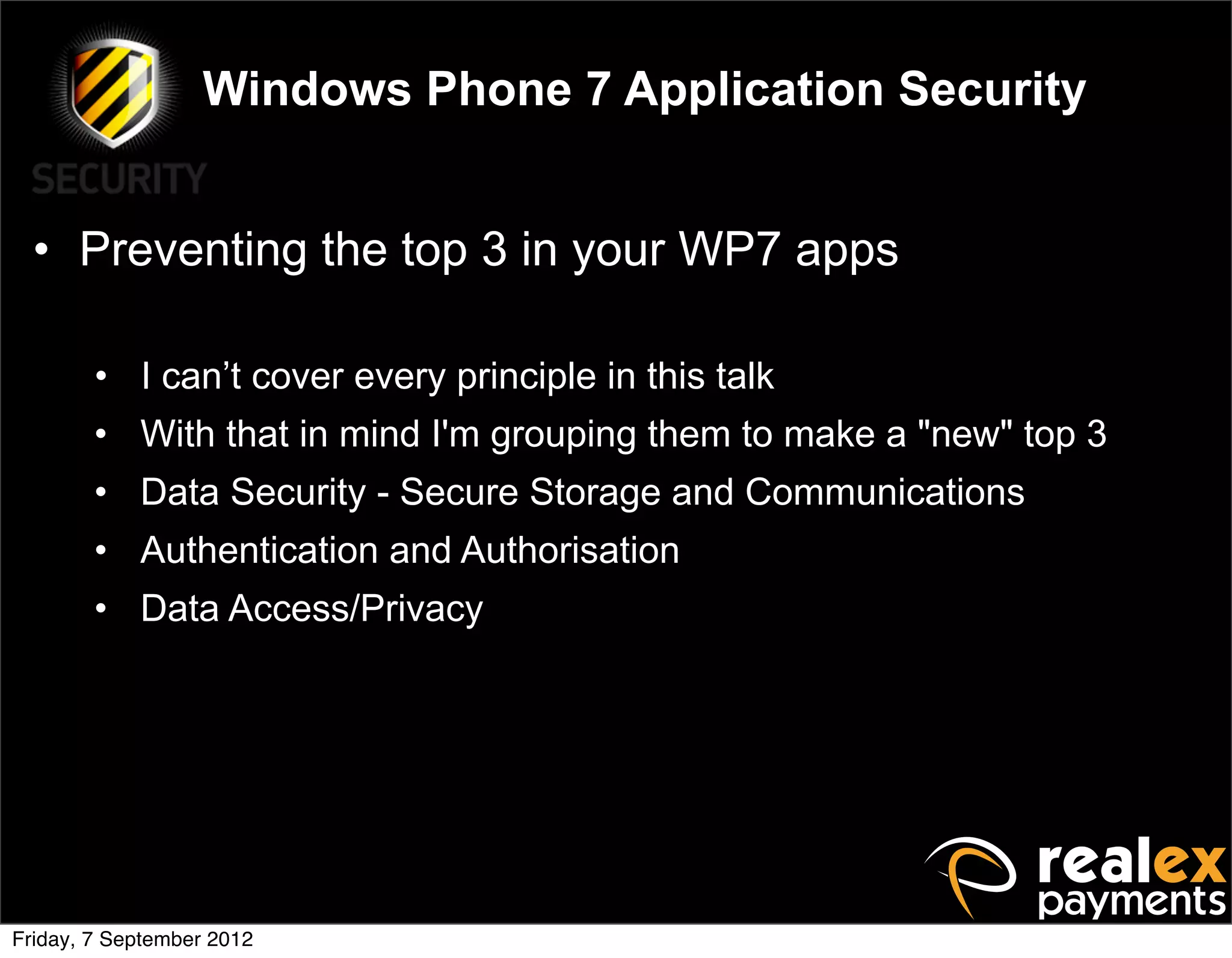
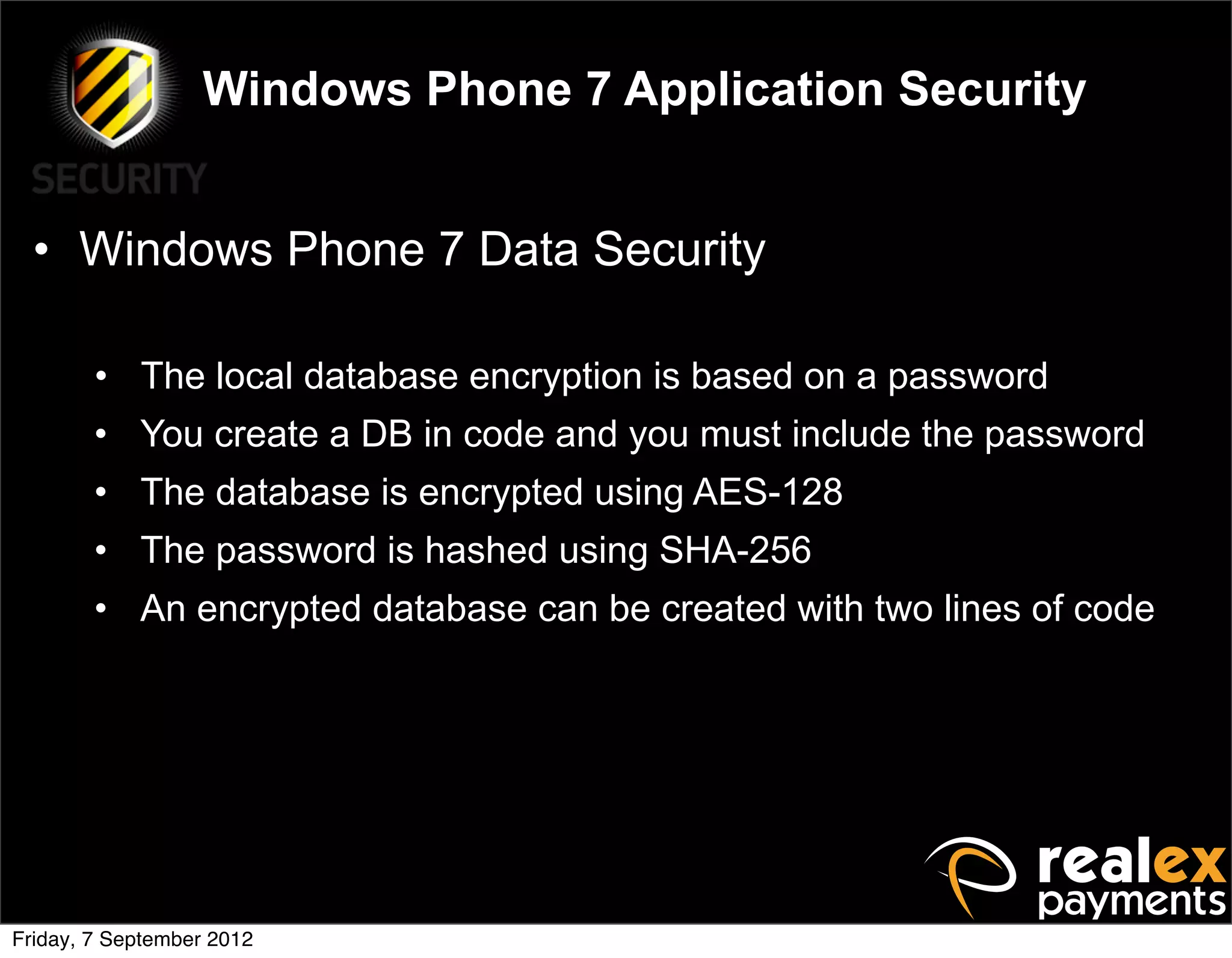
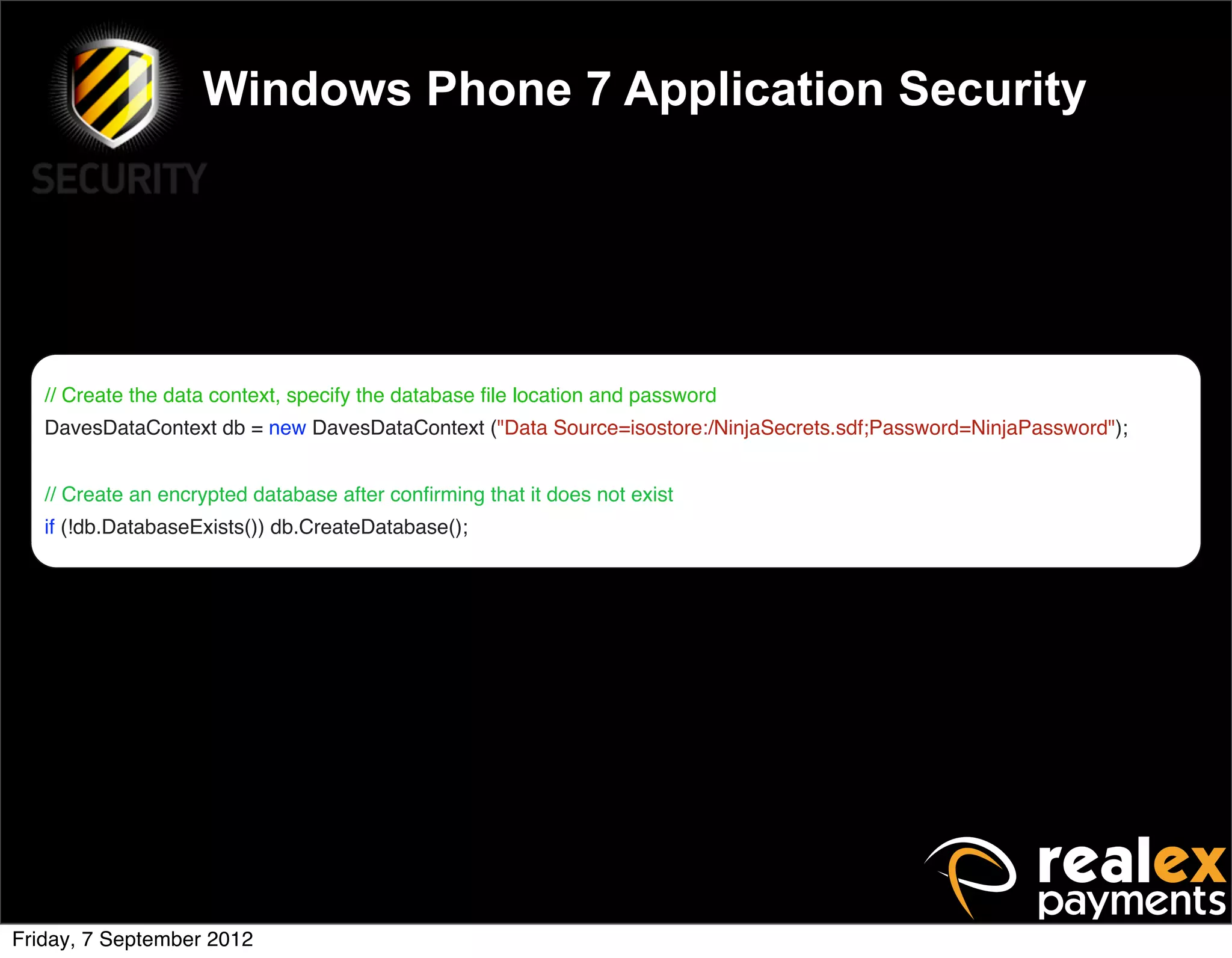
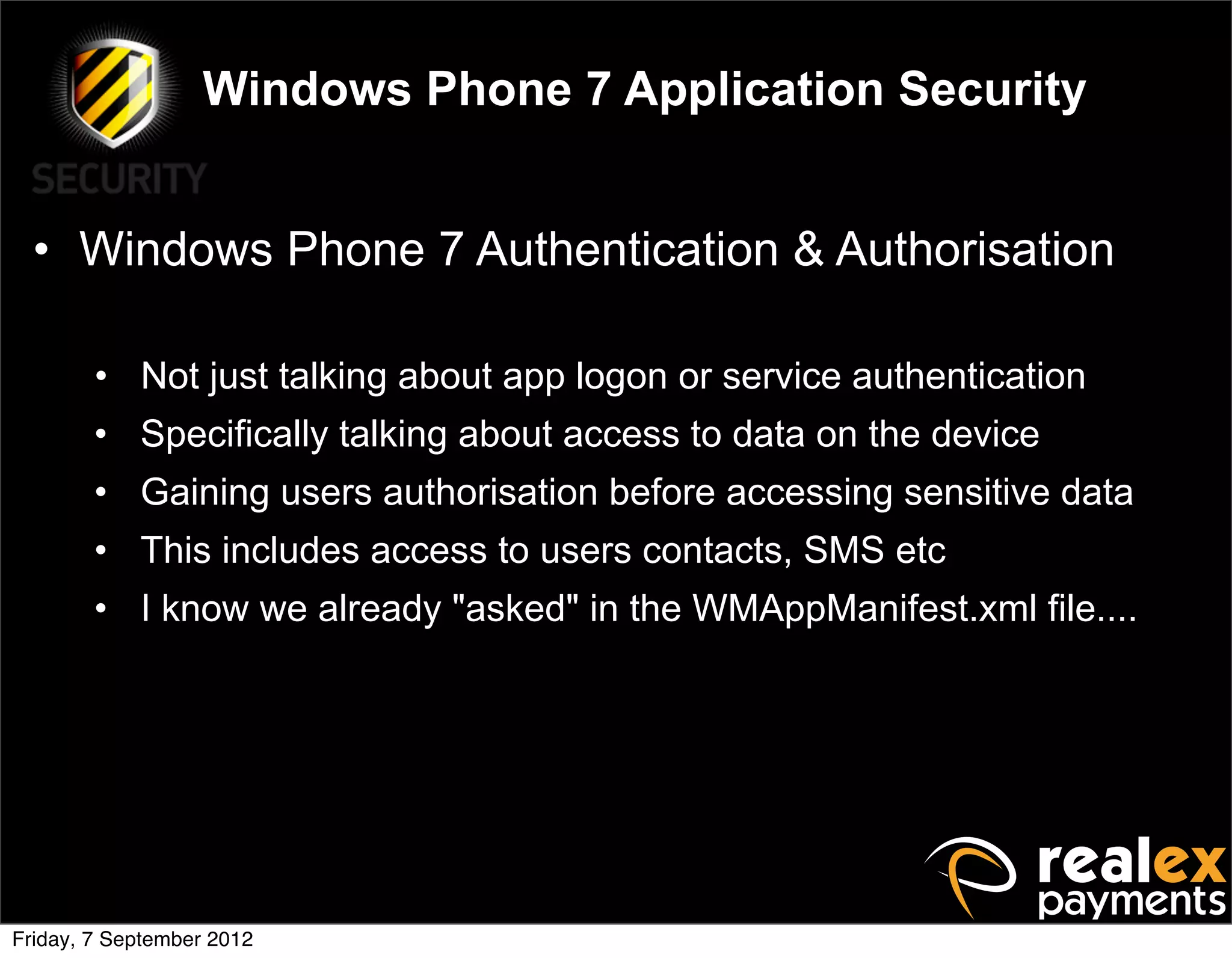
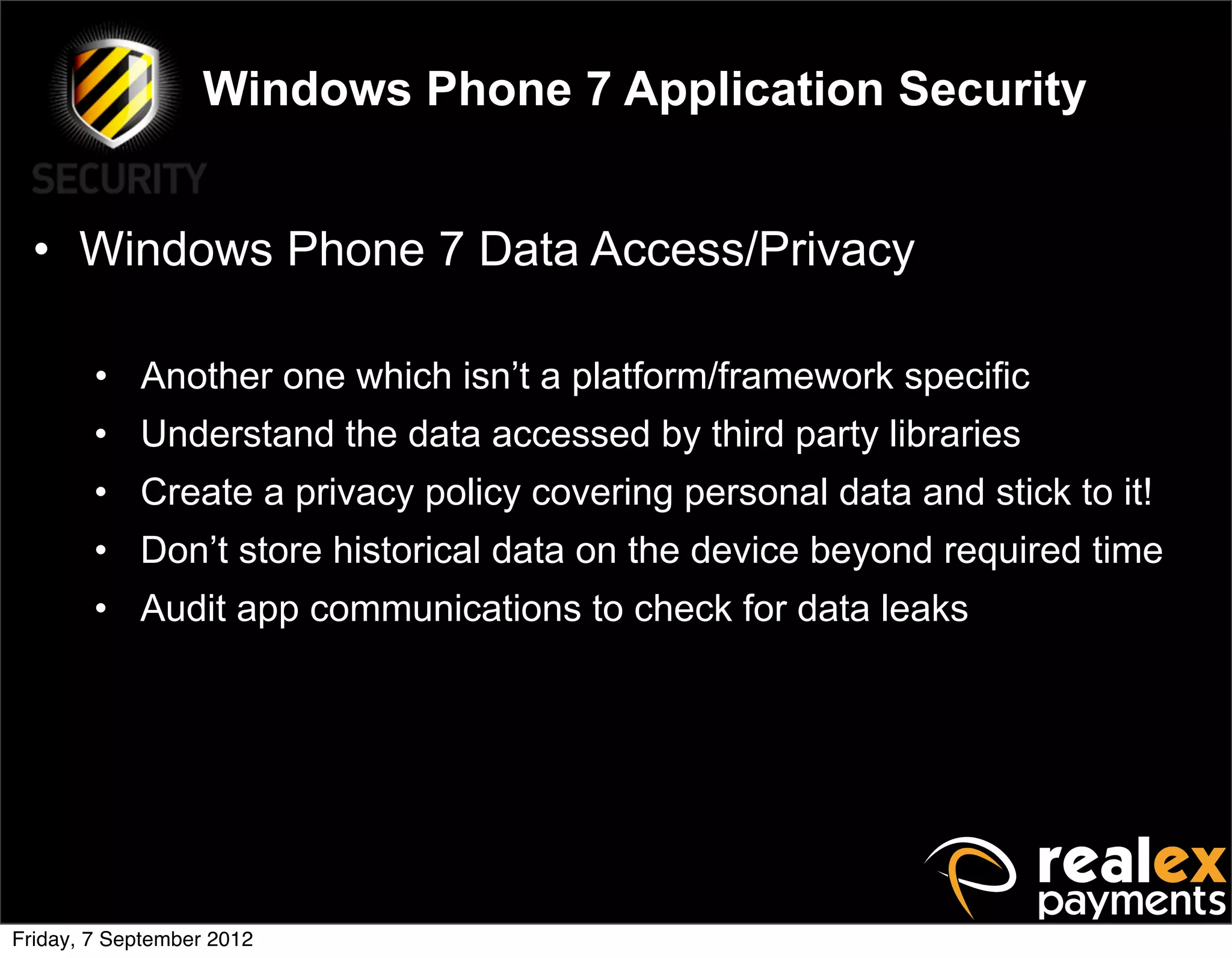
David Rook presented on Windows Phone 7 security. He began by providing context on the growing smartphone market and Microsoft's small market share. He then discussed the Windows Phone 7 platform security model, which uses chambers to enforce app isolation and least privilege. Rook also covered Windows Phone 7 application security best practices, emphasizing the importance of secure storage, authentication and authorization, and secure access to personal data. He concluded by briefly discussing new security aspects of Windows Phone 8.