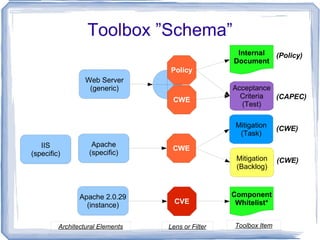
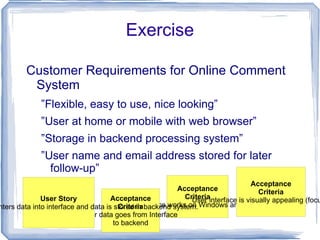
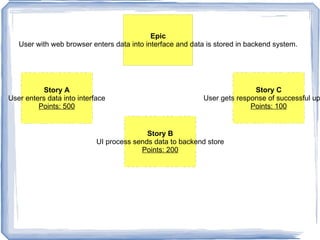
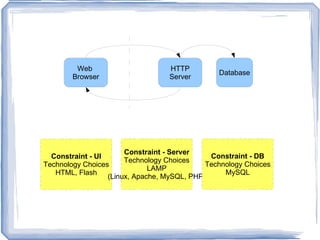
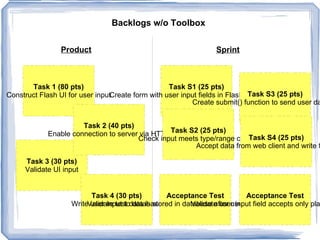
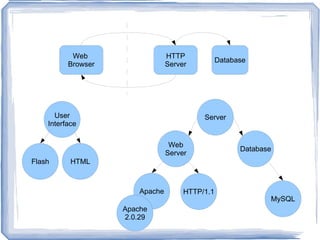
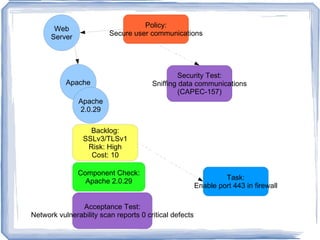
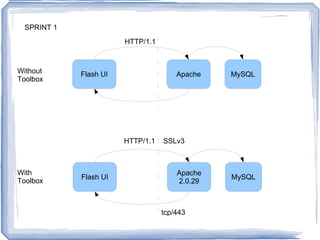
The document discusses challenges for incorporating security practices into agile development and proposes a "Security Toolbox" to help development teams identify and mitigate security risks through the use of accepted security knowledge bases and guidance mapped to specific architectural elements. The toolbox is intended to minimize "Security Debt" by predicting security issues upfront and providing acceptance tests and estimates to integrate security into sprint planning and product backlogs. An example is provided of how the toolbox could be applied to help three development teams implement a secure online comment system.