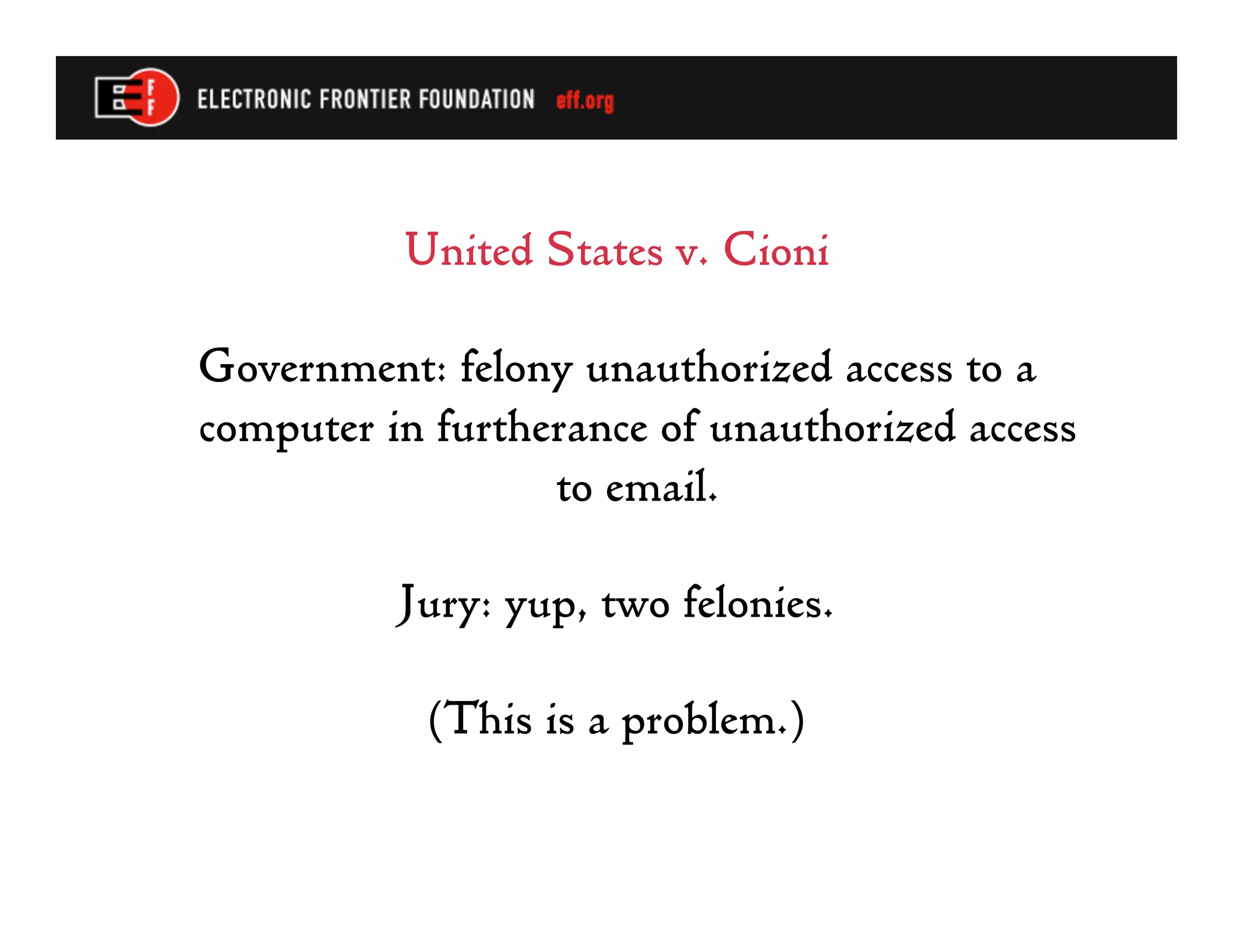
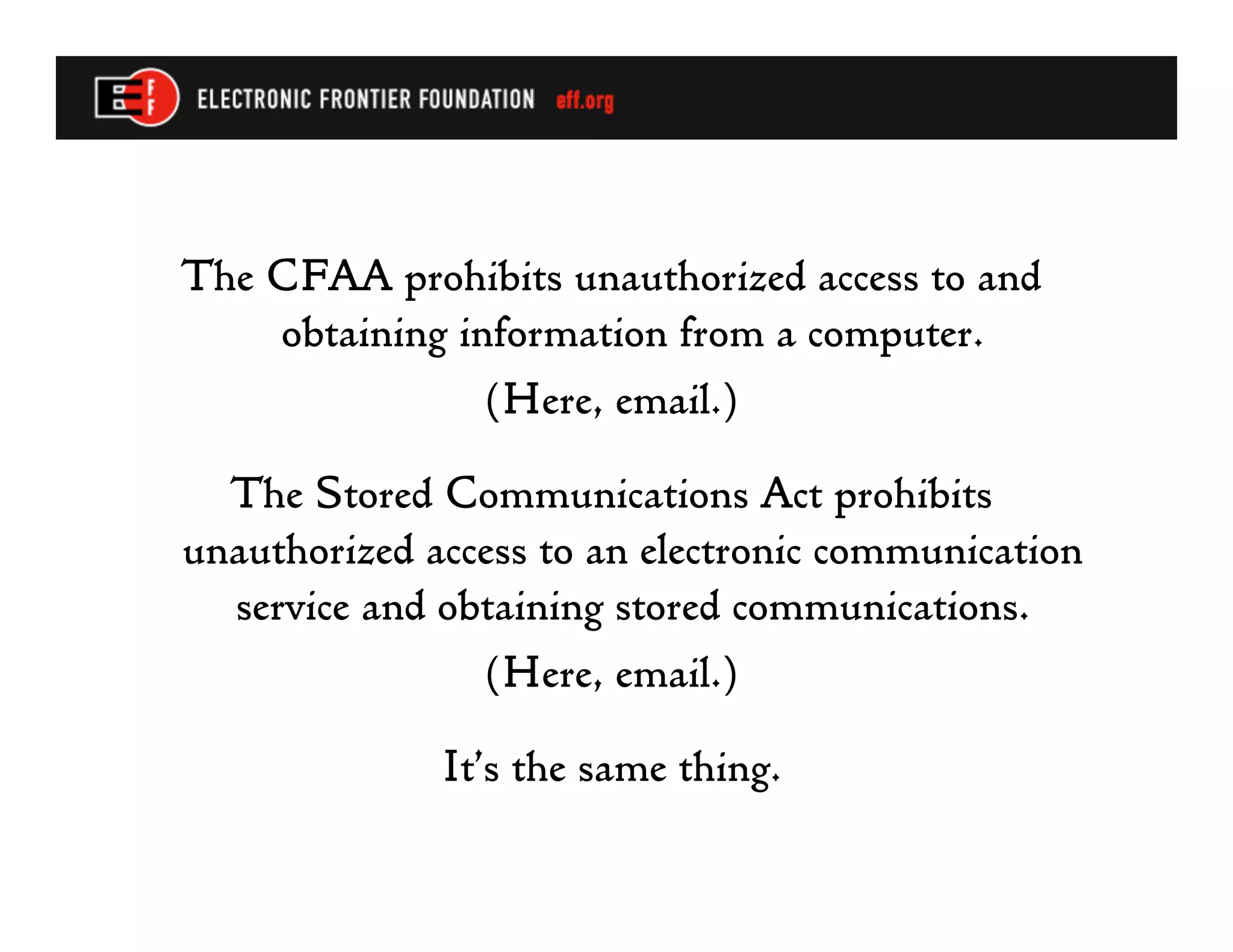
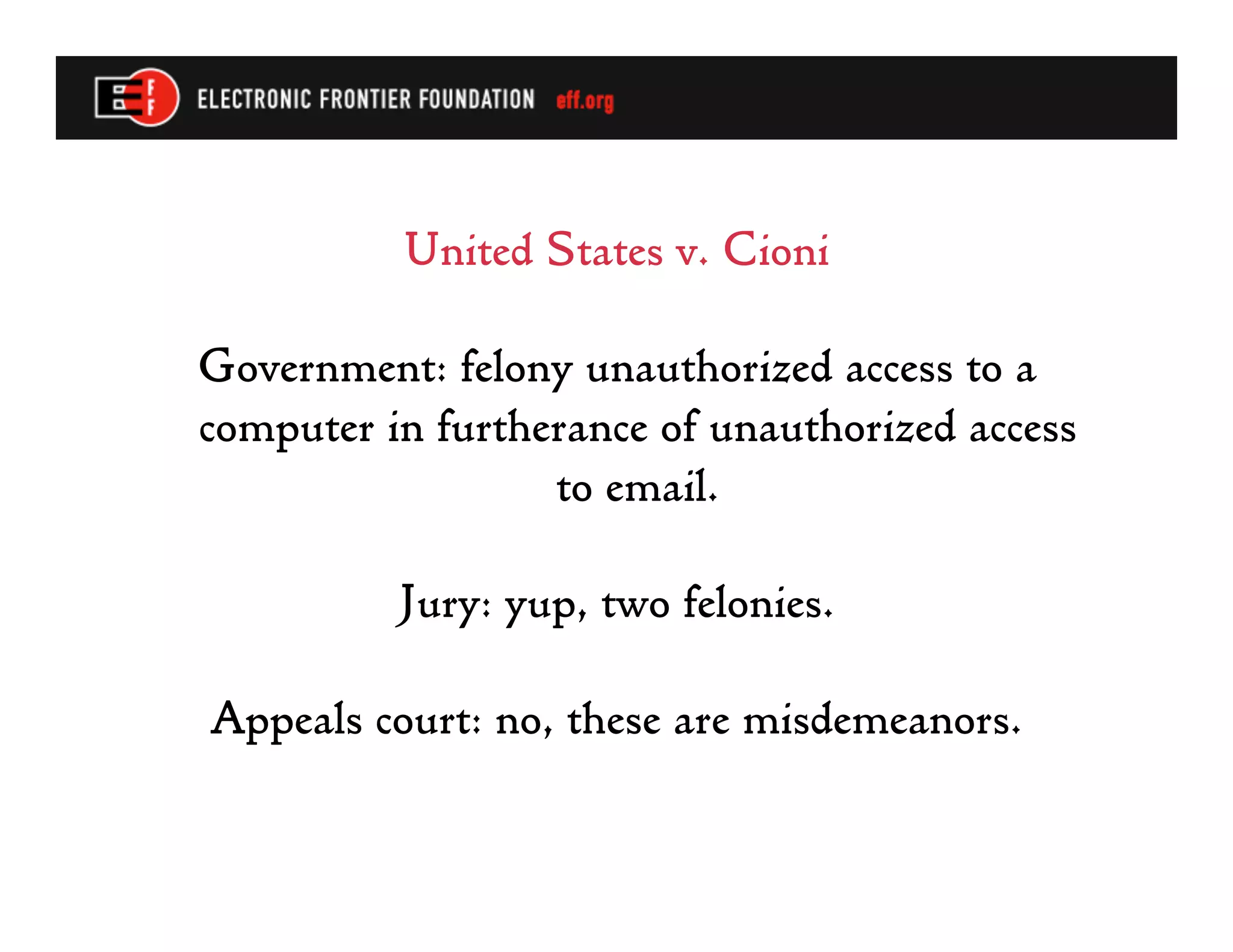
The document summarizes recent developments in computer crime law, specifically regarding interpretations of the federal Computer Fraud and Abuse Act. It discusses how courts have broadly interpreted what constitutes unauthorized access, including violating an employer's computer use policies. It also notes problems with prosecutors trying to double-count penalties for unauthorized access by charging it as a felony in furtherance of another crime when it is essentially the same conduct. The future could see legislative changes enhancing penalties for computer crimes.


![improper access
The CFAA prohibits, among other things,
“intentionally access[ing] a computer without
authorization or in excess of authorization, and
thereby obtain[ing] . . . information from any
protected computer.”
18 U.S.C. § 1030(a)(2)(C).](https://image.slidesharecdn.com/hofmannsourceslides-110619130601-phpapp01/75/The-Latest-Developments-in-Computer-Crime-Law-5-2048.jpg)