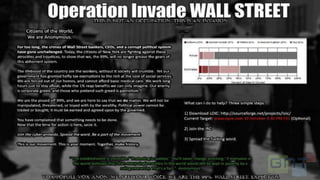
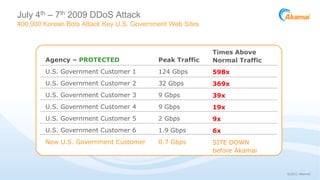
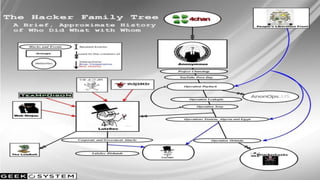
Joshua Corman gave a presentation about adapting to Anonymous in the age of chaotic actors. He began by providing background on himself and his research interests. He then discussed understanding Anonymous by deconstructing it and looking at its rise, different sects, and levels of involvement. Corman addressed adapting to Anonymous by looking at escalation risks and the need for improved security strategies. He concluded by discussing the possibility of building a better version of Anonymous that is focused on positive goals.

![About Joshua Corman
Director of Security Intelligence for Akamai Technologies
•Former Research Director, Enterprise Security [The 451 Group]
•Former Principal Security Strategist [IBM ISS]
Industry Experience
•Expert Faculty: The Institute for Applied Network Security (IANS)
•2009 NetworkWorld Top 10 Tech People to Know
•Co-Founder of “Rugged Software” www.ruggedsoftware.org
Things I’ve been researching
•Compliance vs Security
•Disruptive Security for Disruptive Innovations
•Chaotic Actors
•Espionage
•Security Metrics
2 ©2011 Akamai](https://image.slidesharecdn.com/cormansourcebcn2011compressed-111128062643-phpapp01/85/Adapting-To-The-Age-Of-Anonymous-2-320.jpg)







![Anonymous* Unmasked? [*Alleged]
©2011 Akamai](https://image.slidesharecdn.com/cormansourcebcn2011compressed-111128062643-phpapp01/85/Adapting-To-The-Age-Of-Anonymous-13-320.jpg)