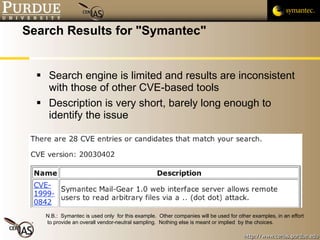
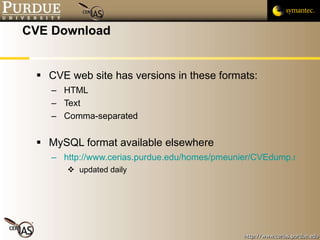
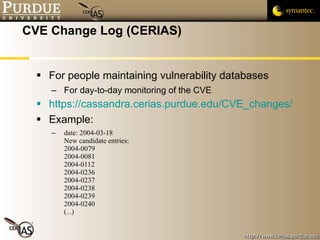
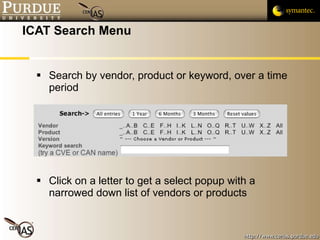
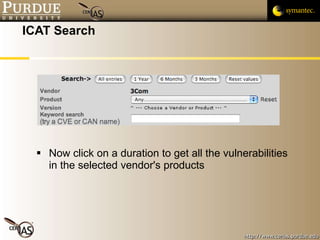
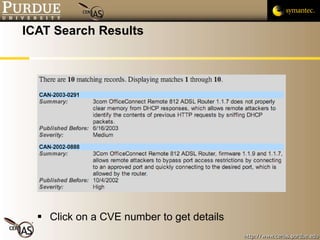
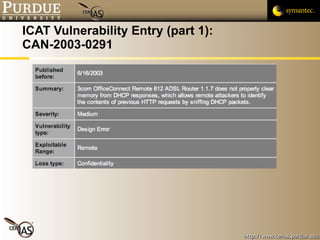
This document provides an overview of public vulnerability databases and resources that can be used by software developers. It summarizes several key resources including MITRE's CVE database, which standardizes names for known vulnerabilities, NIST's ICAT database which provides more details on vulnerabilities, and the CERT/CC and US-CERT websites which publish vulnerability advisories and notes. It encourages developers to consult these resources to stay informed about vulnerabilities in order to proactively prevent issues and learn from others' experiences.










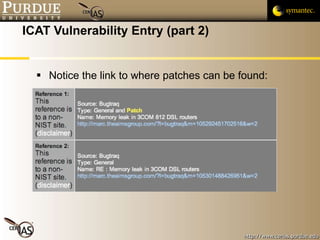


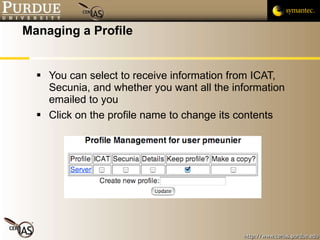
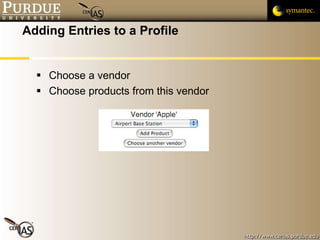
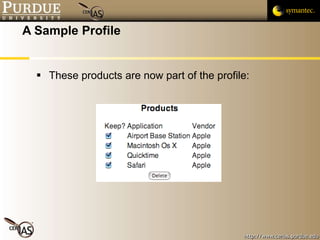
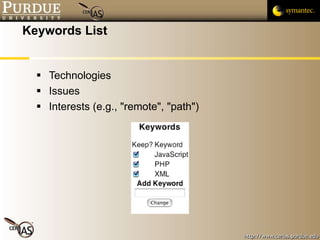
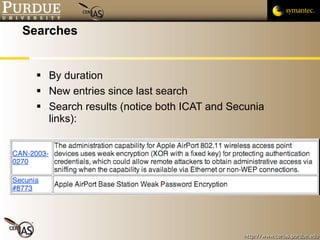







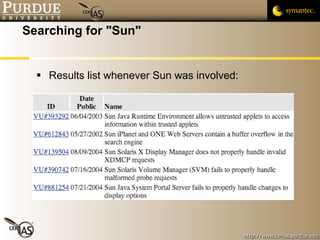








![Pascal Meunier [email_address] Contributors: Jared Robinson, Alan Krassowski, Craig Ozancin, Tim Brown, Wes Higaki, Melissa Dark, Chris Clifton, Gustavo Rodriguez-Rivera](https://image.slidesharecdn.com/2-publicvulnerabilitydatabases-091013224249-phpapp02/85/2-Public-Vulnerability-Databases-59-320.jpg)