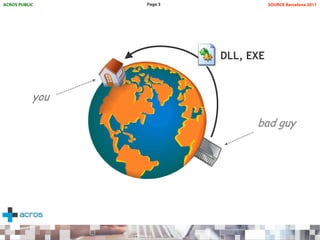
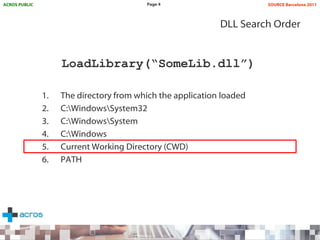
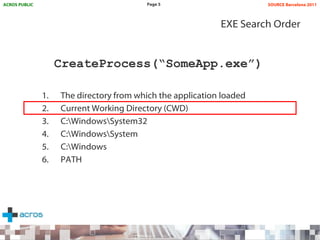
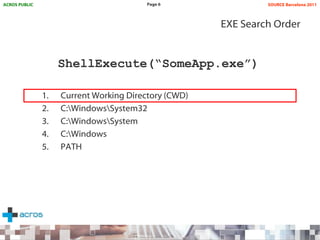
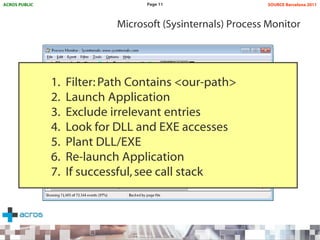
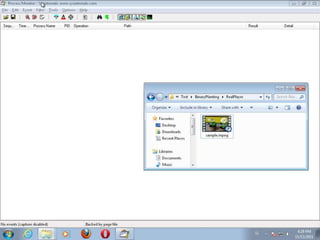
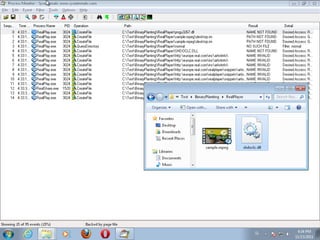
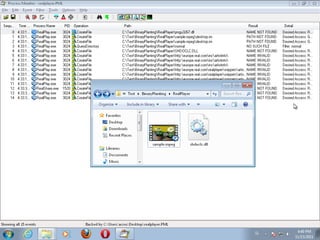
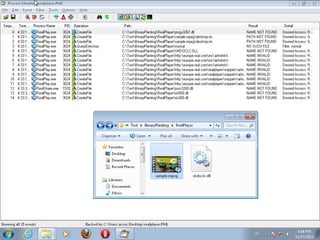
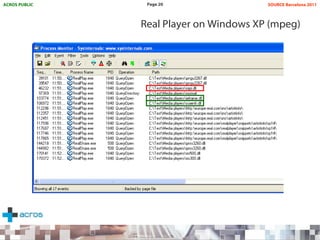
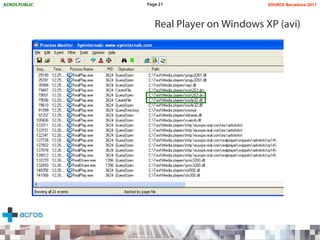
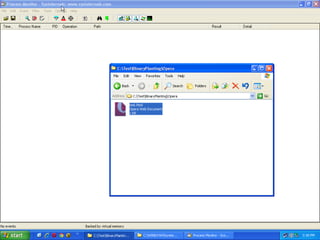
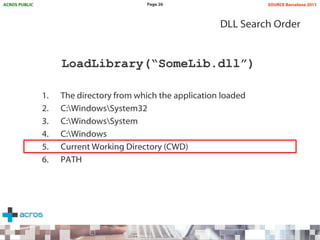
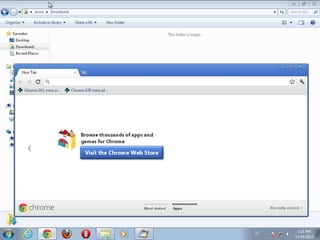
This document discusses binary planting techniques such as DLL hijacking. It provides examples of binary planting issues found in Real Player and Opera on Windows XP, where they load unexpected DLLs and EXEs during execution. It warns that downloading files can leave computers vulnerable if installers load DLLs from the Downloads folder, allowing for "persistent mines" to be planted months later when applications are launched. It provides guidelines for researchers and developers to prevent binary planting issues in their own software.