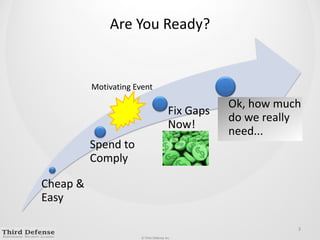
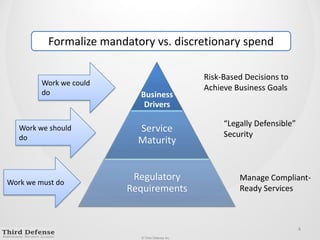
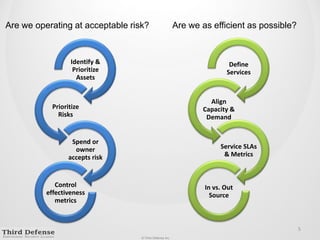
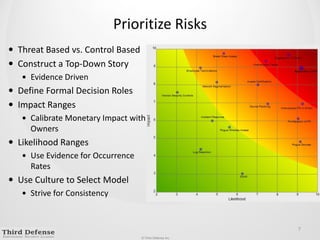
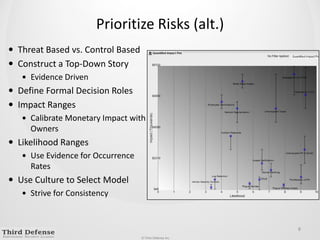
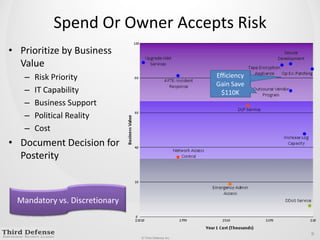
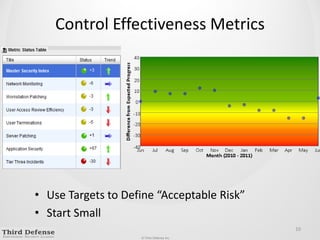
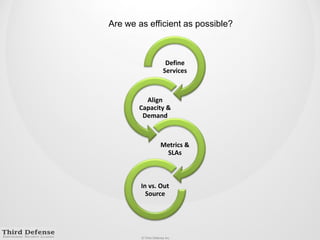
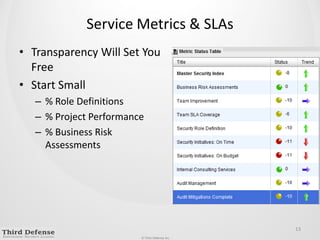
This document provides guidance on how to determine the right amount to spend on security. It recommends first formalizing mandatory, discretionary, and risk-based security spending. Prioritize assets and risks using a structured process involving business owners. Consider likelihood and impact ranges to evaluate risks. Prioritize risks based on business value and cost. Define security services and align spending with maturity targets. Start with quick wins and metrics to gain support for an ongoing process.