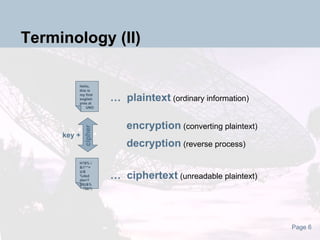
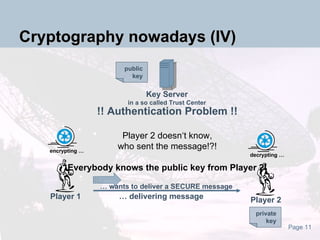
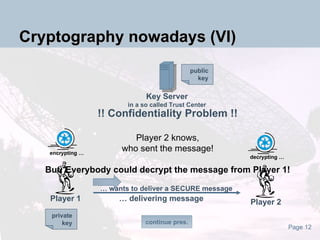
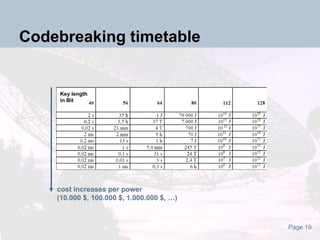
The document discusses the evolution and current state of cryptography, detailing both symmetric and asymmetric key systems and their applications in securing digital data. It emphasizes the importance of cryptography for maintaining privacy over the internet and introduces quantum cryptography as a novel approach. The document also highlights the vulnerabilities of traditional systems, particularly concerning brute force attacks.