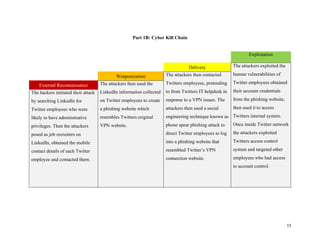
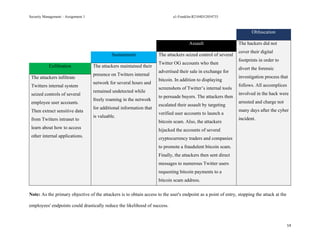
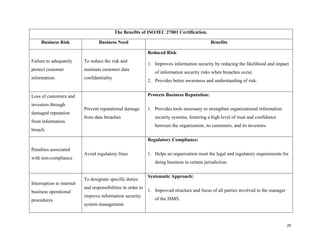
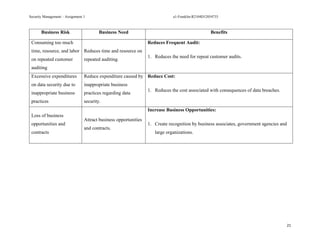
The document provides a comprehensive analysis of the July 2020 cyberattack on Twitter, where hackers utilized phone spear phishing to compromise 130 accounts and conduct a fraudulent bitcoin scam. Key lessons learned from the incident highlight the importance of leadership in cybersecurity, adequate authentication and access controls, and awareness training for staff regarding social engineering attacks. The report concludes with actions taken by Twitter to enhance its security measures post-attack.





















![Security Management – Assignment 1 a1-Franklin-R2104D12054733
26
References
BBC, 2020. Twitter hack: Staff tricked by phone spear-phishing scam. [Online]
Available at: https://www.bbc.com/news/technology-53607374
[Accessed 31 July 2023].
Calder, A., 2018. Information Security & ISO 27001: An Introduction. s.l.:s.n.
Dawson, S., 2019. The Benefits of Implementing ISO 27001. [Online]
Available at: https://www.thecoresolution.com/the-benefits-of-implementing-iso-27001
[Accessed 19 August 2023].
DFS, 2020. Twitter Investigation Report, New York: Department of Financial Services.
Fadhil, H. S., 2023. Social Engineering Attacks Techniques. International Journal of Progresive
Research in Engineering Management and Science, 03(01), pp. 18-20.
Hazout, R., 2023. Multi-CDN Strategy: Benefits And Best Practices. [Online]
Available at: https://www.ioriver.io/blog/multi-cdn-strategy
[Accessed 14 August 2023].
Iyengar, R., 2020. CNN Business. [Online]
Available at: https://edition.cnn.com/2020/07/15/tech/twitter-hack-elon-musk-bill-
gates/index.html
[Accessed 29 July 2023].](https://image.slidesharecdn.com/a1-franklin-r2104d12054733-240210180322-47a7a57b/85/Security-Management-26-320.jpg)
![Security Management – Assignment 1 a1-Franklin-R2104D12054733
27
Medina, A., 2021. Inside the Fastly Outage: Analysis and Lessons Learned. [Online]
Available at: https://www.thousandeyes.com/blog/inside-the-fastly-outage-analysis-and-lessons-
learned
[Accessed 14 August 2023].
Moon, M., 2020. Twitter's changes since the June attack include requiring security keys.
[Online]
Available at: https://www.engadget.com/twitters-security-changes-july-attack-054328827.html
[Accessed 11 August 2023].
Muneer, A., n.d. 2020 Phishing Attack on Twitter, its Analysis and Countermeasures, London:
Northumbria University.
NDCA, 2020. Three Individuals Charged For Alleged Roles In Twitter Hack. [Online]
Available at: https://www.justice.gov/usao-ndca/pr/three-individuals-charged-alleged-roles-
twitter-hack
[Accessed 31 July 2023].
Popper, N. & Conger, K., 2020. Hackers Tell the Story of the Twitter Attack From the Inside.
[Online]
Available at: https://www.nytimes.com/2020/07/17/technology/twitter-hackers-interview.html
[Accessed 10 August 2023].
Rockwell, N., 2021. Summary of June 8 outage. [Online]
Available at: https://www.fastly.com/blog/summary-of-june-8-outage
[Accessed 14 August 2023].](https://image.slidesharecdn.com/a1-franklin-r2104d12054733-240210180322-47a7a57b/85/Security-Management-27-320.jpg)
![Security Management – Assignment 1 a1-Franklin-R2104D12054733
28
Statista, 2023. Most commonly reported cyber crime categories worldwide in 2022, by number of
individuals affected. [Online]
Available at: https://www.statista.com/statistics/184083/commonly-reported-types-of-cyber-
crime-global/
[Accessed 30 July 2023].
Suciu, P., 2020. Forbes. [Online]
Available at: https://www.forbes.com/sites/petersuciu/2020/08/01/twitter-spear-phishing-attack-
highlights-security-weaknesses-of-social-media/?sh=651f9f027a29
[Accessed 29 July 2023].
Sumner, R., 2019. What is a Content Delivery Network (CDN)?. [Online]
Available at: https://www.ibm.com/topics/content-delivery-networks
[Accessed 14 August 2023].
Thompson, N. & Barrett, B., 2020. How Twitter Survived Its Biggest Hack—and Plans to Stop
the Next One. [Online]
Available at: https://www.wired.com/story/inside-twitter-hack-election-plan/
[Accessed 8 August 2023].
Twitter, 2020. An update on our security incident. [Online]
Available at: https://blog.twitter.com/en_us/topics/company/2020/an-update-on-our-security-
incident
[Accessed 8 August 2023].](https://image.slidesharecdn.com/a1-franklin-r2104d12054733-240210180322-47a7a57b/85/Security-Management-28-320.jpg)
